http://bbs.anzhuo.cn/config/config_ucenter.php.bak
http://bbs.anzhuo.cn/config/config_global.php.bak
没找到数据库外网ip 而且也很可能不可外连
那么这里我们利用uc_key
有了uc_key 我们可以直接获取getshell的
参考: WooYun: 敏感信息泄露#动漫东东敏感信息泄露导致100万+用户信息可被脱裤
可惜简单的getshell方法失败,另一个getshell方法比较麻烦
那我们来试试利用uc_key进任意用户账号吧
文件:/api/uc.php
我们利用这里的接口:synlogin
代码片段:
利用脚本略过
利用api进入任意用户:
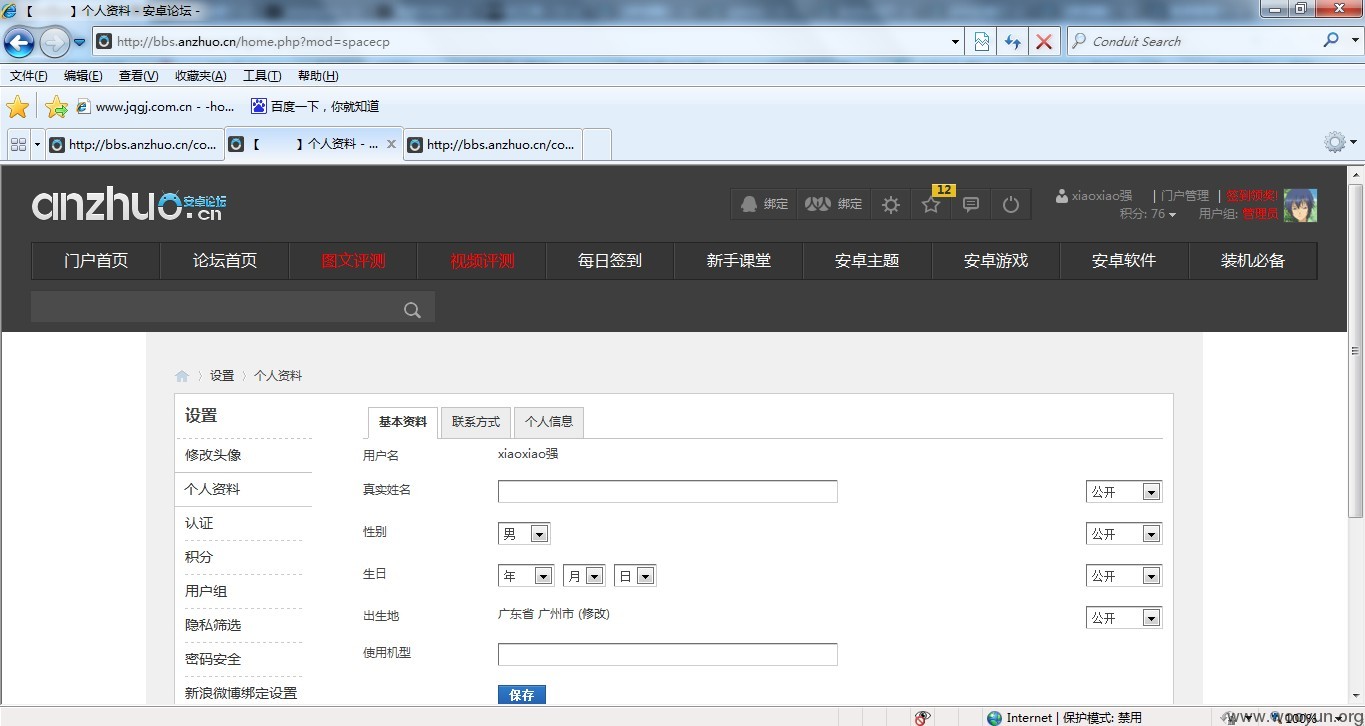
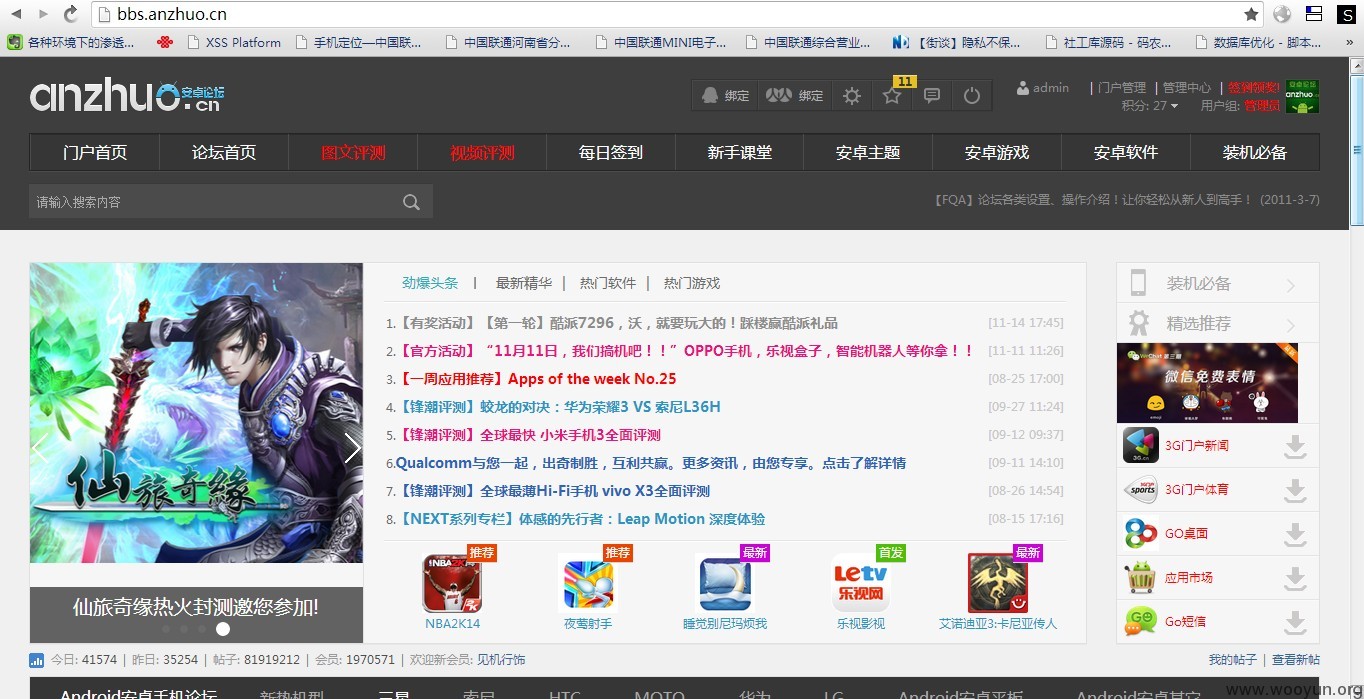
还可以利用uc_key拿webshell
方法:改管理员密码(本地搭建个discuz,利用uc_key修改anzhuo.cn管理员的密码) 进后台拿webshell
安卓中国有197万+用户