漏洞概要
关注数(24)
关注此漏洞
漏洞标题:暴力破解深澜网关计费系统用户密码
提交时间:2013-11-05 10:19
修复时间:2013-12-20 10:20
公开时间:2013-12-20 10:20
漏洞类型:网络设计缺陷/逻辑错误
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2013-11-05: 细节已通知厂商并且等待厂商处理中
2013-11-09: 厂商已经确认,细节仅向厂商公开
2013-11-19: 细节向核心白帽子及相关领域专家公开
2013-11-29: 细节向普通白帽子公开
2013-12-09: 细节向实习白帽子公开
2013-12-20: 细节向公众公开
简要描述:
可以通过判断服务器返回值的方式,暴力破解深澜网关
详细说明:
post到服务器的数据username=xxx&password={TEXT}xxxxx&drop=0&type=1&n=100
然后服务器会返回user_tab_error username_error password_error ername_error等返回值,这时候可以通过判断返回值对用户的密码进行暴力破解
漏洞证明:
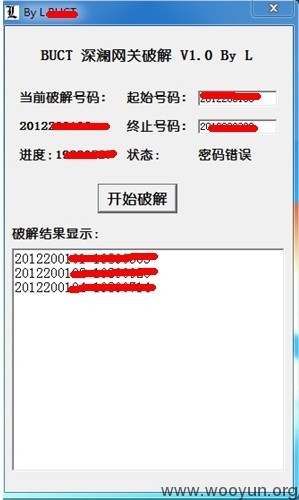
核心代码
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2013-11-09 19:35
厂商回复:
CNVD未能直接复现所述情况,所述系统多部署于内部网关,根据图片以及所述代码情况进行确认,rank 15
最新状态:
暂无



