漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2012-07165
漏洞标题:美国白宫主站XSS,求跨Obama
相关厂商:美国白宫
漏洞作者: gainover
提交时间:2012-05-15 23:07
修复时间:2012-05-15 23:07
公开时间:2012-05-15 23:07
漏洞类型:xss跨站脚本攻击
危害等级:高
自评Rank:12
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2012-05-15: 积极联系厂商并且等待厂商认领中,细节不对外公开
2012-05-15: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
这个这个,没上下文,白宫人不多吧,我跨谁呢,跨谁呢!!
详细说明:
I hope my Chinese-Wind-English can be understood.
First, The Website of the WhiteHouse use a JWPlayer (a video player based on flash from longtailvideo, www.longtailvideo.com), and this player have a xss vulnerability.
Next, we could use this vulnerability to construct an evil link to attack potential victims. The codes are listed below!
The evil code can be run in both IE and Firefox, but crashed in Chrome (:( unkown reason).
The attack flow:
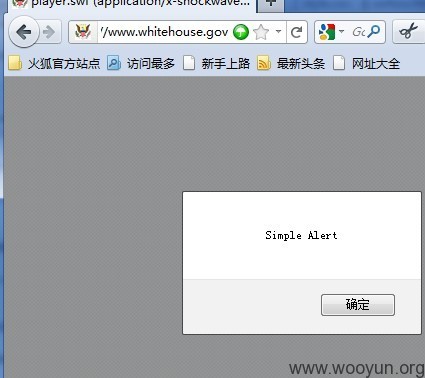
1. Simple Alert, However, we got a "Access Denied Error". The server seems to have some strange filter rules? Luckily, We can bypass this limitation.
Failed Code
Success Code
2. We found some other sensetive words are also banned, such as <script></script>.
3. The code used above is runable but harmless. A more harmful code :
4. Run it then known it. (in Chinese: 试试看你就知道了!)
漏洞证明:
1. Simple alert example
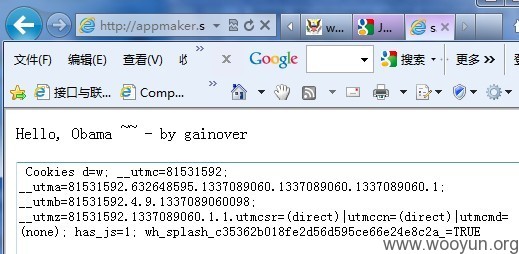
2. Cookies got from whitehouse and sent to our own page.
3. Firefox can also run evil codes.
修复方案:
Delete unused JWPlayer or wait for JWPlayer update.
版权声明:转载请注明来源 gainover@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:3 (WooYun评价)