漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0173684
漏洞标题:气泡网各种敏感信息泄露(服务器\数据库\后台几乎全部沦陷)
相关厂商:气泡网
漏洞作者: 路人甲
提交时间:2016-01-30 21:04
修复时间:2016-03-14 15:10
公开时间:2016-03-14 15:10
漏洞类型:重要敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-30: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-03-14: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
...
详细说明:
Index topic:
http://qipaobbs.91qipao.com/api/app/index_api.php?page='+topic_page;
svn: 账号/密码:xiebc/xbc@gqc502
svn://120.131.81.217/qipao_bbs
svn://120.131.81.217/qipao_shop
svn://120.131.81.217/www_neng123_com/trunk
svn://120.131.81.217/qipao_tools/trunk
友盟的统计: http://www.umeng.com/
账号:[email protected]
密码:gaoqian1234
论坛管理 http://shuangbbs.xingkec.com/forum.php
账号:admin 密码: Goq!an@3s*7GD
商城管理 http://shuang.xingkec.com/admin/index.php
账号:admin 密码: admin123456
数据采集:
http://we.onexin.com/?mod=bigdata
云梯vpn:
账号是:[email protected]
登陆账号:YING 密码: qiang1989
论坛管理 http://qipaobbs.91qipao.com/forum.php
账号:admin 密码: .WZR1vsLL.2#@Cao.
商城管理 http://adshop.91qipao.com/admin/privilege.php?act=login
账号:admin 密码: .WZR1vsLL.2#@Cao.
数据采集:
http://we.onexin.com/?mod=bigdata
账号:260296 密码: a1234567890b!@#
云主机1配置: mstsc
ip:120.131.81.41 4cpu_4gram 100g硬盘 win2008x64
账号:administrator/Gq502#c!91
云主机2配置(数据库):
ip:120.131.81.42 2cpu_4gram 100g硬盘 win2008x64
账号:administrator/Gq502@x!91
云主机4配置:
名称: gaoqian_91qipao_db
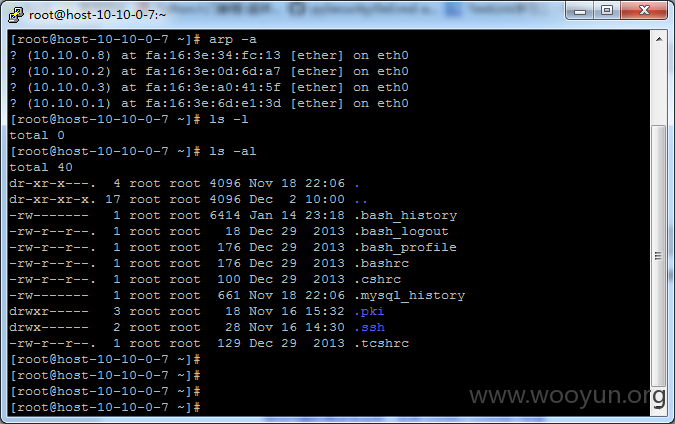
ip:120.131.84.112/10.10.0.7 8cpu_16gram 5M 400g硬盘 centos6.5x64
账号:root / syscloud.cn$#@!1234
mysql: root / Gq@qi502c (port:3386)
云主机5配置:
名称: gaoqian_91qipao_www
ip:120.131.84.113/10.10.0.8 8cpu_16gram 5M 400g硬盘 centos6.5x64
账号:root / Gq@paoc502
数据库:mysql: 端口:3307 root / Gq3502@c91
http://tongji.baidu.com/web/welcome/login
验证邮箱:
邮箱:[email protected]
密码:qipao123
百度统计账号密码:
账号:91qipao
密码:qipao123
企业账号:[email protected]/gaoqian1234
v2//////////////////////////////////////////////////////////////v2//////////////////////////////
Index topic:
http://qipaobbs.91qipao.com/api/app/index_api.php?page='+topic_page;
我的邮箱:[email protected]/gaoqian1234
公司QQ号3183317032,密码改成qipao1234
Qq企业账号:
svn: 账号/密码:xiebc/xbc@gqc502
svn://120.131.81.217/qipao_bbs
svn://120.131.81.217/qipao_shop
友盟的统计: http://www.umeng.com/
账号:[email protected]
密码:gaoqian1234
论坛管理 http://shuangbbs.xingkec.com/forum.php
账号:admin 密码: Goq!an@3s*7GD
商城管理 http://shuang.xingkec.com/admin/index.php
账号:admin 密码: admin123456
数据采集:
http://we.onexin.com/?mod=bigdata
论坛管理 http://qipaobbs.91qipao.com/forum.php
账号:admin 密码: .WZR1vsLL.2#@Caoyyy.
商城管理 http://adshop.91qipao.com/admin/privilege.php?act=login
账号:admin 密码: .WZR1vsLL.2#@Caoyyy.
数据采集:
http://we.onexin.com/?mod=bigdata
账号:260296 密码: a1234567890b!@#
云主机1配置: mstsc
ip:120.131.81.41 4cpu_4gram 100g硬盘 win2008x64
账号:administrator/Gq502#c!91
云主机2配置(数据库):
ip:120.131.81.42 2cpu_4gram 100g硬盘 win2008x64
账号:administrator/Gq502@x!91
数据库:mysql: 端口:3307 root / Gq3502@c91
高能广告:[email protected] / admin
云主机4配置:
名称: gaoqian_91qipao_db
ip:120.131.84.112/10.10.0.7 8cpu_16gram 5M 400g硬盘 centos6.5x64
账号:root / syscloud.cn$#@!1234
mysql: root / Gq@qi502c (port:3386)
云主机5配置:
名称: gaoqian_91qipao_www
ip:120.131.84.113/10.10.0.8 8cpu_16gram 5M 400g硬盘 centos6.5x64
账号:root / Gq@paoc502
云主机3配置:
ip:120.131.81.217 8cpu_32gram 5M 200g硬盘 centos6.5x64
账号:root / Gq@paoc502
$_config['db']['1']['dbhost'] = '10.10.0.7:3386';
$_config['db']['1']['dbuser'] = 'root';
$_config['db']['1']['dbpw'] = 'Gq@qi502c';
$_config['db']['1']['dbcharset'] = 'utf8';
$_config['db']['1']['pconnect'] = '0';
$_config['db']['1']['dbname'] = '91qipao_bbs';
$_config['db']['1']['tablepre'] = 'pre_';
$_config['db']['slave'] = '';
$_config['db']['common']['slave_except_table'] = '';
重启服务器
service php-fpm restart
service nginx restart
分享页:http://qipaobbs.91qipao.com/forum.php?mod=viewthread&mobile=2&tid=6635
广告状态: 未审核、审核未通过、激活、暂停、余额不足
老 2015/9/22 15:03:03
按钮(广告主): 报表、编辑、启用、暂停
采集系统: http://we.onexin.com
之前外包的:
OID账号:260296
PWD密码:a1234567890b!@#
---------ONEXIN--------
新注册的:
OID: 261424
Pwd: 6b26da34
http://tongji.baidu.com/web/welcome/login
验证邮箱:
邮箱:[email protected]
密码:qipao123
百度统计账号密码:
账号:91qipao
密码:qipao123
微信/qq/微博开放平台账号密码
https://open.weixin.qq.com/
登录,分享
账号:[email protected]
密码:gaoqian1234
http://open.qq.com/
账号:3183317032
密码:qipao1234.
http://open.weibo.com/
微博认证: [email protected] qipao1234.
/home/www/qipaobbs/data/image_tmp
老刘 2015/12/15 18:12:06
http://qipaobbs.91qipao.com/data/image_tmp/
19:43:55
老刘 2015/12/15 19:43:55
ftp服务器: 120.131.84.113 port:21
老刘 2015/12/15 19:44:31
账号/密码: ftp1 / Gq@1#502
老刘 2015/12/15 19:45:07
账号 ftp1的根目录 即为: /home/www/qipaobbs/data/image_tmp
这,不能再详细了有木有。多的我都措手不及,不知道该做点什么了
漏洞证明:
修复方案:
...
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)