漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0161833
漏洞标题:KesionCMS ASP版一处SQL注入
相关厂商:厦门科汛软件有限公司
漏洞作者: 路人甲
提交时间:2015-12-17 10:24
修复时间:2016-01-28 17:10
公开时间:2016-01-28 17:10
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-17: 积极联系厂商并且等待厂商认领中,细节不对外公开
2016-01-28: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
搜索型注入
详细说明:
很明显的一处注入;但是好像需要闭合,先提交了证明下注入,闭合就交给大牛完成了
漏洞证明:
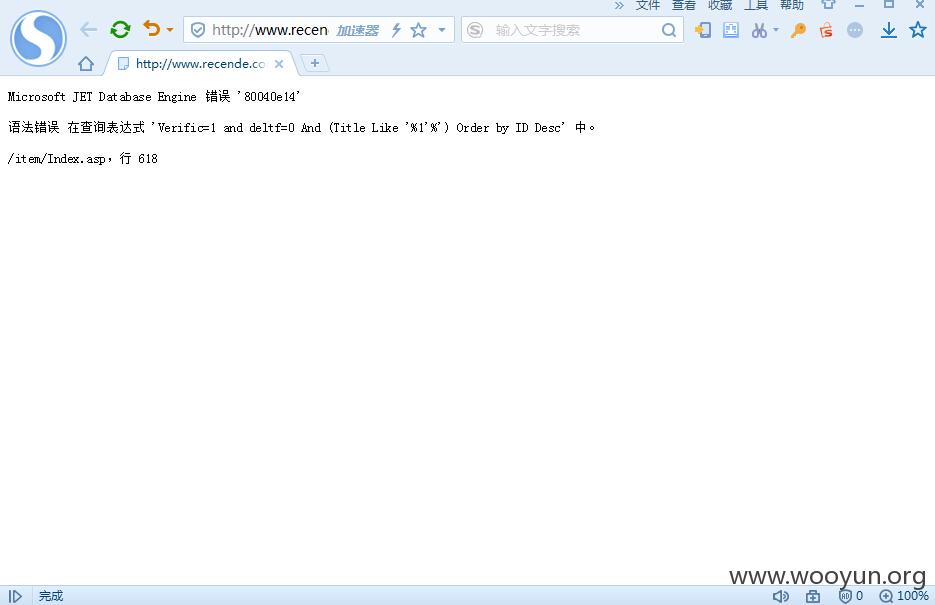
http://www.recende.com/item/?c-5,key-1%27.html
Microsoft JET Database Engine 错误 '80040e14'
语法错误 在查询表达式 'Verific=1 and deltf=0 And (Title Like '%1'%') Order by ID Desc' 中。
/item/Index.asp,行 618
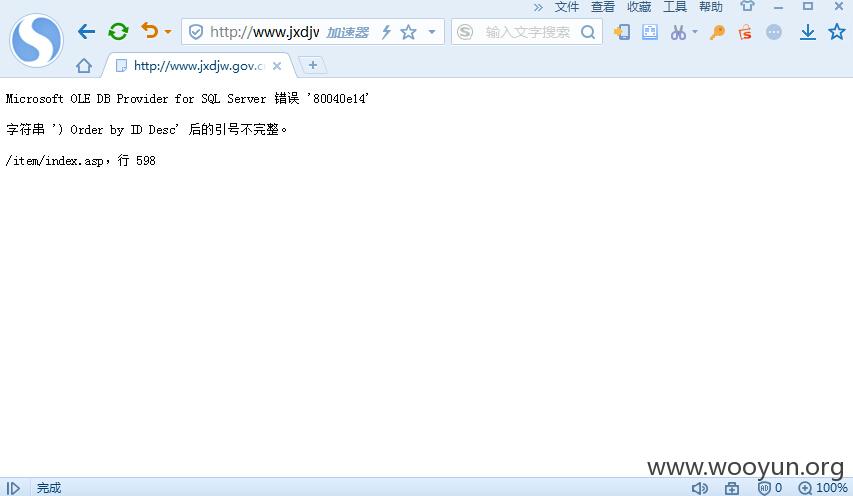
http://www.jxdjw.gov.cn//item/?c-5,key-1%27.html
Microsoft OLE DB Provider for SQL Server 错误 '80040e14'
字符串 ') Order by ID Desc' 后的引号不完整。
/item/index.asp,行 598
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)