漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0153827
漏洞标题:P2P金融安全之钱爸爸sql注入漏洞(66W会员信息泄露)
相关厂商:深圳市钱爸爸电子商务有限公司
漏洞作者: Nelion
提交时间:2015-11-17 09:43
修复时间:2016-01-11 15:32
公开时间:2016-01-11 15:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-17: 细节已通知厂商并且等待厂商处理中
2015-11-20: 厂商已经确认,细节仅向厂商公开
2015-11-30: 细节向核心白帽子及相关领域专家公开
2015-12-10: 细节向普通白帽子公开
2015-12-20: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
p2p金融钱爸爸(https://www.qian88.com/)存在sql注入漏洞。
详细说明:
1、注入点:
漏洞证明:
2、所有的数据库:
3、当前库qianbaba的表(表太多就截些数据多的):
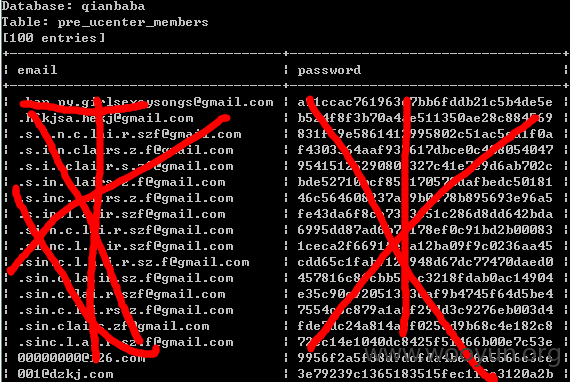
4、表pre_ucenter_members的字段:
Database: qianbaba
Table: pre_ucenter_members
[12 columns]
+---------------+-----------------------+
| Column | Type |
+---------------+-----------------------+
| email | char(32) |
| lastloginip | int(10) |
| lastlogintime | int(10) unsigned |
| myid | char(30) |
| myidkey | char(16) |
| password | char(32) |
| regdate | int(10) unsigned |
| regip | char(15) |
| salt | char(6) |
| secques | char(8) |
| uid | mediumint(8) unsigned |
| username | char(15) |
+---------------+-----------------------+
5、再dump点数据看看:
修复方案:
参数过滤
版权声明:转载请注明来源 Nelion@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:3
确认时间:2015-11-20 16:41
厂商回复:
感谢白帽子Nelion提交的漏洞,已转交技术人员处理。
最新状态:
暂无