漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0153256
漏洞标题:phpwind < v6 版本命令执行漏洞
相关厂商:phpwind
漏洞作者: 猪猪侠
提交时间:2015-11-10 12:06
修复时间:2016-02-08 15:10
公开时间:2016-02-08 15:10
漏洞类型:命令执行
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-10: 细节已通知厂商并且等待厂商处理中
2015-11-10: 厂商主动忽略漏洞,细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航)
2016-01-04: 细节向核心白帽子及相关领域专家公开
2016-01-14: 细节向普通白帽子公开
2016-01-24: 细节向实习白帽子公开
2016-02-08: 细节向公众公开
简要描述:
07年的漏洞,一个轻松简单就能利用的漏洞
详细说明:
phpwind/sort.php 会定期每天处理一次帖子的浏览量、回复量、精华版排序
代码直接使用savearray将数据库查询出来的内容写入php文件,savearray出来的参数,都使用"双引号来包含,所以可以利用变量来执行任意命令
发表一个帖子:标题如下
再开一个多线程(100线程,几分钟就可以了),请求访问那个帖子,直到帖子的访问量排入前20
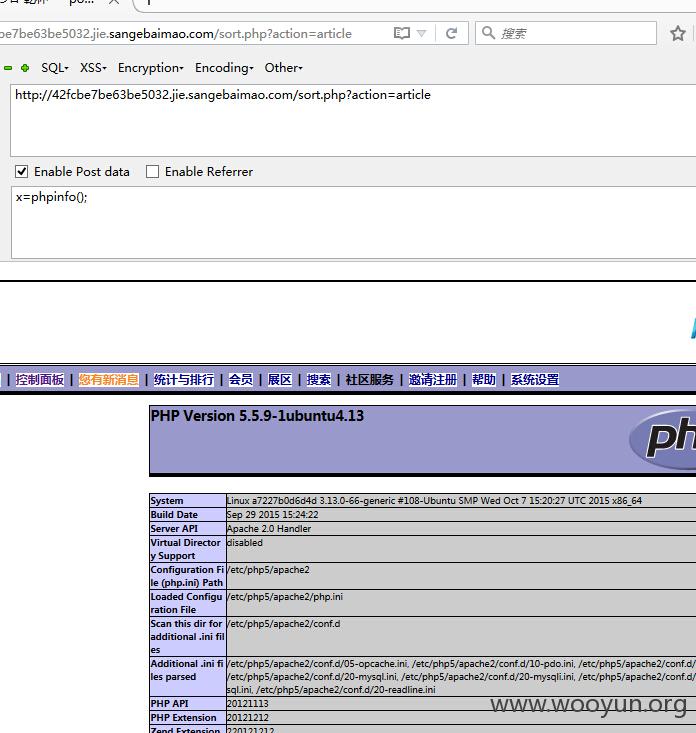
第二天,生成统计排行的时候,shell就躺在了 /data/bbscache/article_sort.php
三个白帽实际演示:http://**.**.**.**/data/bbscache/article_sort.php
漏洞证明:
/data/bbscache/article_sort.php
修复方案:
使用单引号处理来自客户端可控的变量
版权声明:转载请注明来源 猪猪侠@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2016-02-08 15:10
厂商回复:
您好,由于phpwind目前仅维护phpwind8.7及以上版本,其他低版本已不再维护更新。该问题暂不会影响到新版本的用户,建议仍在使用低版本的用户尽快升级到最新版。
漏洞Rank:15 (WooYun评价)
最新状态:
暂无