漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0150603
漏洞标题:香港航空官网APP存在SQL注入(可跨68个库)
相关厂商:香港航空
漏洞作者: 路人甲
提交时间:2015-10-30 13:37
修复时间:2015-12-14 15:36
公开时间:2015-12-14 15:36
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-30: 细节已通知厂商并且等待厂商处理中
2015-10-30: 厂商已经确认,细节仅向厂商公开
2015-11-09: 细节向核心白帽子及相关领域专家公开
2015-11-19: 细节向普通白帽子公开
2015-11-29: 细节向实习白帽子公开
2015-12-14: 细节向公众公开
简要描述:
航空安全之香港航空APP注入
详细说明:
目标:香港航空APP
检测发现以下地方存在SQL注入:(注入参数为app_id和uid,皆为时间盲注)
估计是SQLMap对json语法支持不好,而且程序对sleep()睡眠时间不定,所以用SQLMap没跑出来;于是改用了BENCHMARK。Payload如下,直接加在注入参数之后即可,替换注入语句2>1为查询语句:
漏洞证明:
按照以上原理,写了个Python批量执行,从而取得数据:
1、当前数据库用户
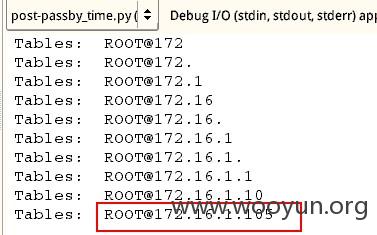
2、当前数据库
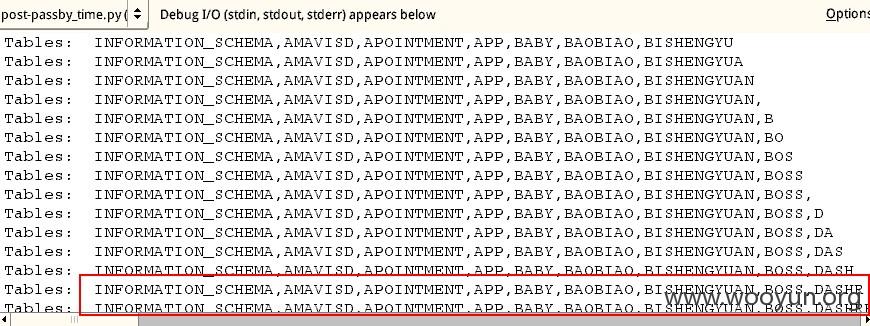
3、所有数据库,共68个,可跨库,此处只列出前55个
==============================
AMAVISD
APOINTMENT
APP
BABY
BAOBIAO
BISHENGYUAN
BOSS
DASHREPORTS
DATABURGER_CMS
ECOMMERCE
GROUPBUY
HEALTHCHANNEL
HKSHARES
HUASHI
HUAZHUANG
HUAZHUANG_BAOBIAO
HUAZHUANG_DASHREPORTS
HUAZHUANG_DW
IMAGE_CUT
IMSERVER
INTERFACE
IWEBMALL
IWEBSHO_
MADSERVER
MADSERVER_YSZJ
MADSERVER_ZSYD
MEDICINE
MEDICINESHOP
MUYINGBAOBIAO
MY_WIKI
MYSQL
OPENFIRE
OPENFIRE2
OPENSIPS
OPENX
ORDERSYSTEM
OUT_ADD_PUSH
PHARMACIES
PIWIK
POLICEMAN
POLICYD
POSTFIX
PROTAL
PUBLICINFO
RADIUS
ROUNDCUBEMAIL
SEARCH
SEARCH_BUS
SERVLETS
SHOP_ITEM
SIP_JAB
SMS
SNSWEBBUS
SOLRDATA
SPAMASSASSIN
==================================
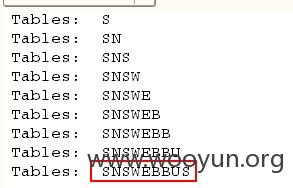
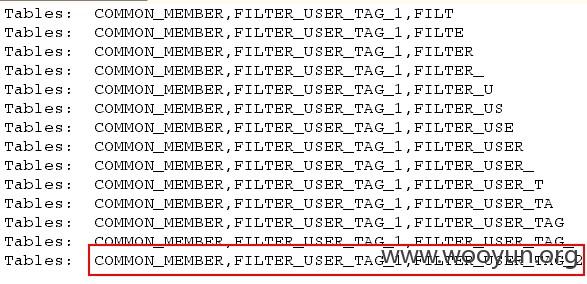
4、跑下当前库SNSWEBBUS的表吧,只跑前三个~
以此可跑出所有数据,不深入了~
修复方案:
请多指教~
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2015-10-30 15:35
厂商回复:
谢谢,我们将对漏洞进行修复
最新状态:
暂无