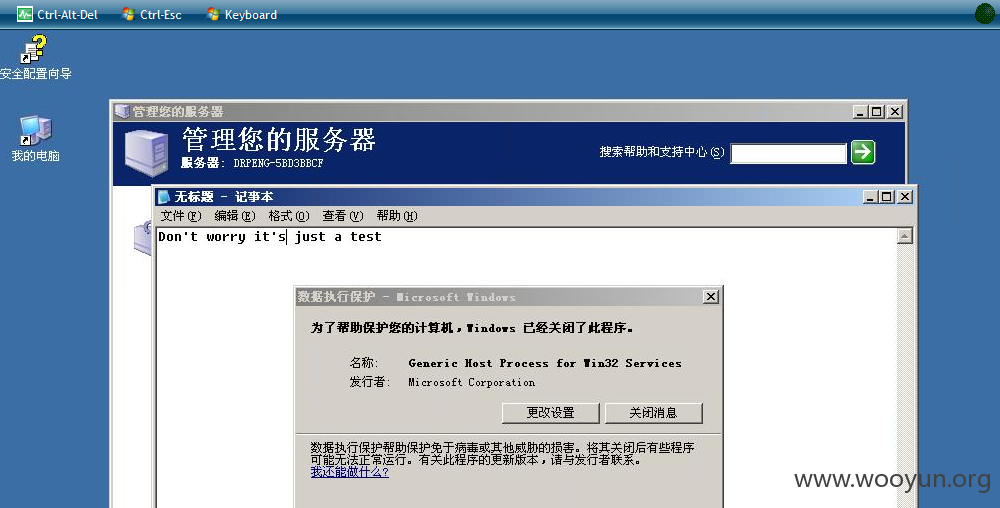
是的,先看到这里
http://**.**.**.**/bugs/wooyun-2015-098853
在我今天早上发现了漏洞之后,就去网上搜索了一下,没想到还真的有过。
不过,既然已经公开了,那么应该已经修复了吧?
然而,我测试过程中,发现,还是没有,下面我就结合我的发现,来报告一下这个漏洞。
首先,是进入到这个管理面板。
http://**.**.**.**/index.asp
然后登陆,
开始抓包。
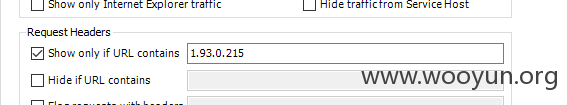
在登陆之后,可以看到抓到这样一个包,我们从这里入手
这个,最后面的 ownUserId 大有玄机,我们随机改改试试
然后我们看看返回了什么吧
哈哈就得到这个账户的信息了。
然后我们这里需要的是 instanceId 这个参数 可以看到我们目标攻击的主机是 434522,记下。
然后我们继续看,先到自己的主机里,查看密码,抓到一个格式,作为模板。
把 URL 里的地址 替换成 上面获取的实例ID,
比如 刚刚的,
然后就可以看到了
然后继续来,获取一下远程桌面的连接地址吧。
同样的,点击自己的主机,抓个模板。
如法炮制,获取我们目标主机的 URL。
获取到了~
我们访问看看~
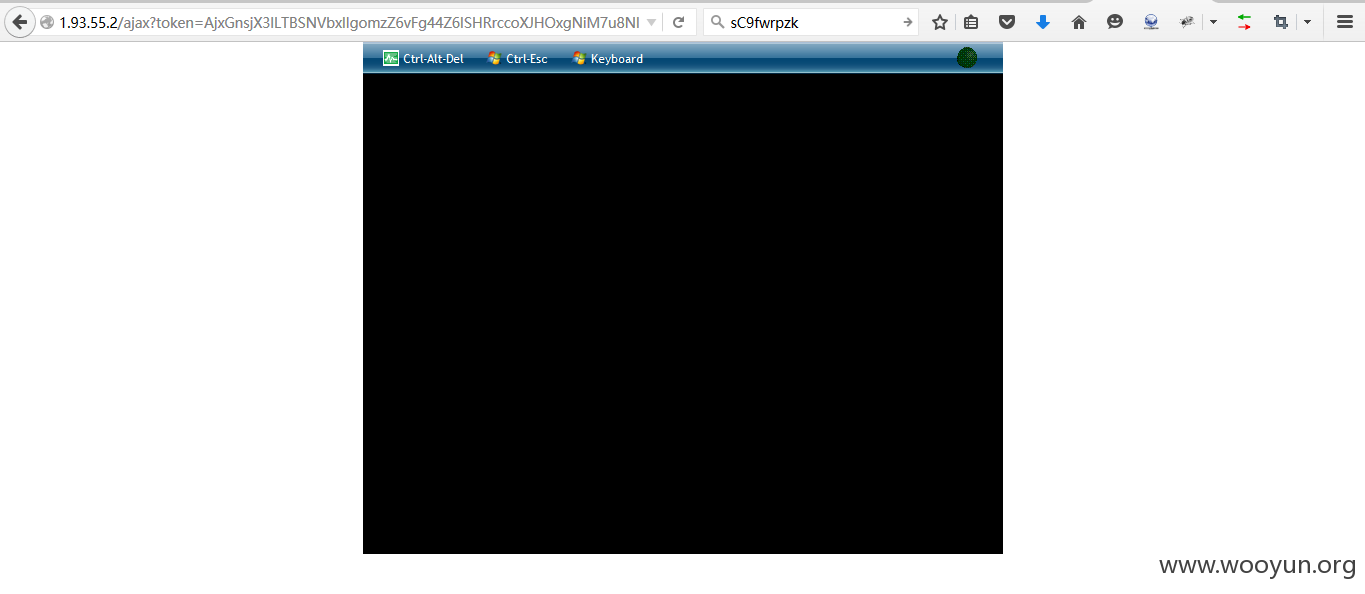
http://**.**.**.**/ajax?token=AjxGnsjX3lLTBSNVbxlIgomzZ6vFg44Z6ISHRrccoXJHOxgNiM7u8NI1bmcP_OT2Uw38McVMk51y_-0DMk09FE7dWam1ojWD7v1IN9-BlNXz7-k9Z80mbO81dHb-My_scv_tAzJNPRTwT0gI5KgWNl2tIQwVjgrLFyWl7E_-WslM2hgI56rYO-oPXqbWJJmm5hTQmmlVX-lJTTSOIBLfcnlCGsZKmYN1qIGKbT5b-JXfDaRfFuCMIZJlnppEufsM&guest=windows&title=i-2-22462-VM
看到没,登陆了。
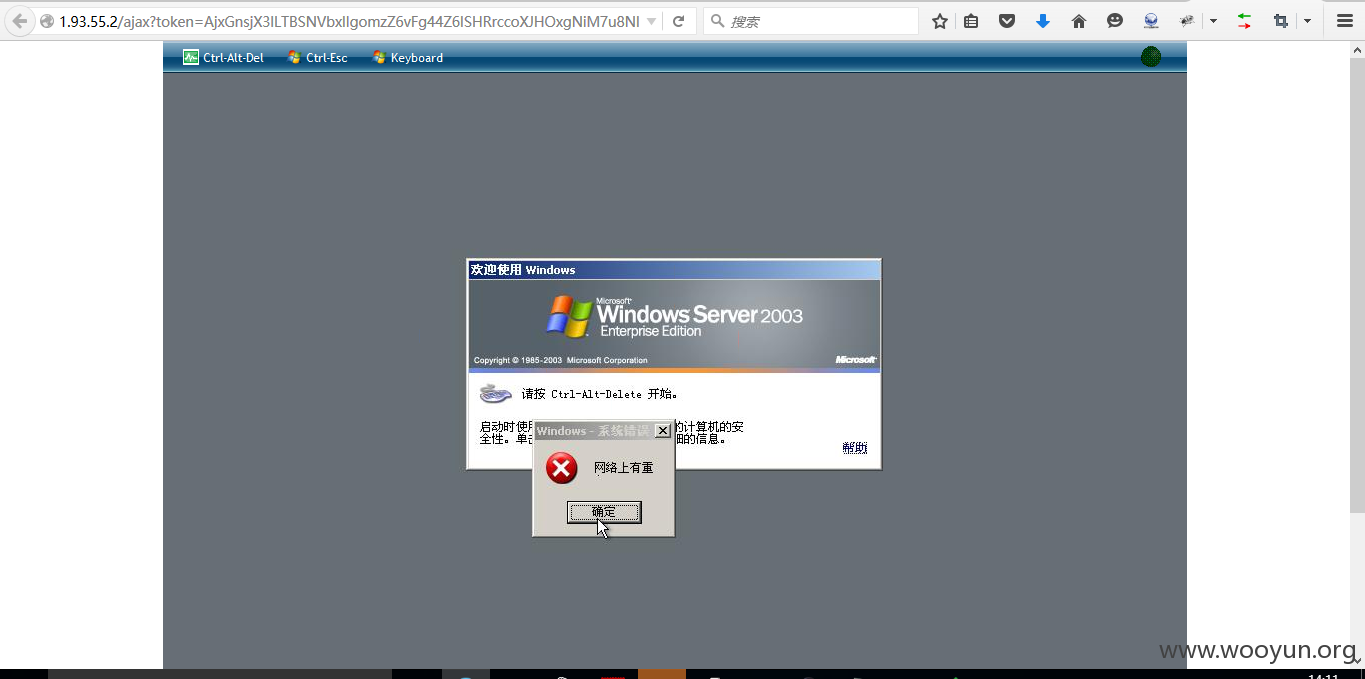
我用刚才得到的密码 sC9fwrpzk 试试。
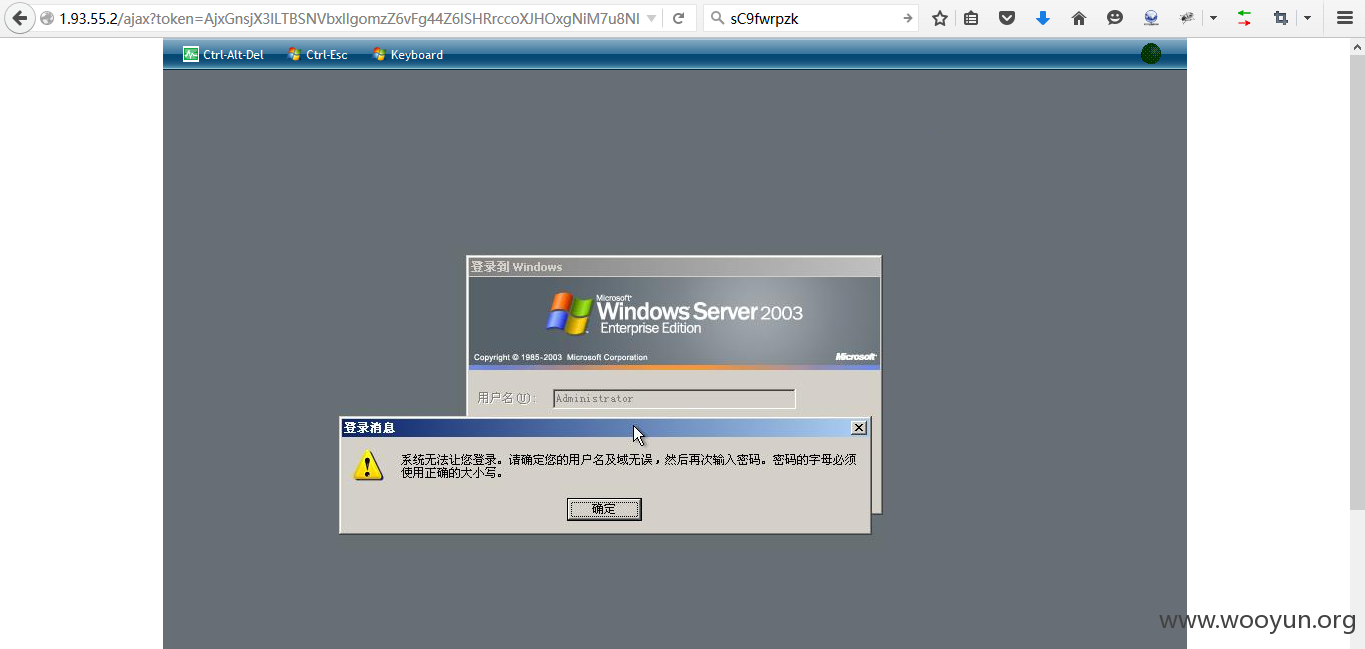
似乎是修改了默认密码
不要紧,我们可以重置
在自己的面板上,先关机,然后尝试重置密码,这里我抓模板。
这个是关机的
这个是重置密码的
然后这个是开机指令。
OK ,我们来试试
发送停机指令
然后继续
重置密码了
然后启动看看
看看能登陆没= =
然后,接着看下面的验证。