URL: http://libao.g.letv.com/?gid=116
注入参数sid
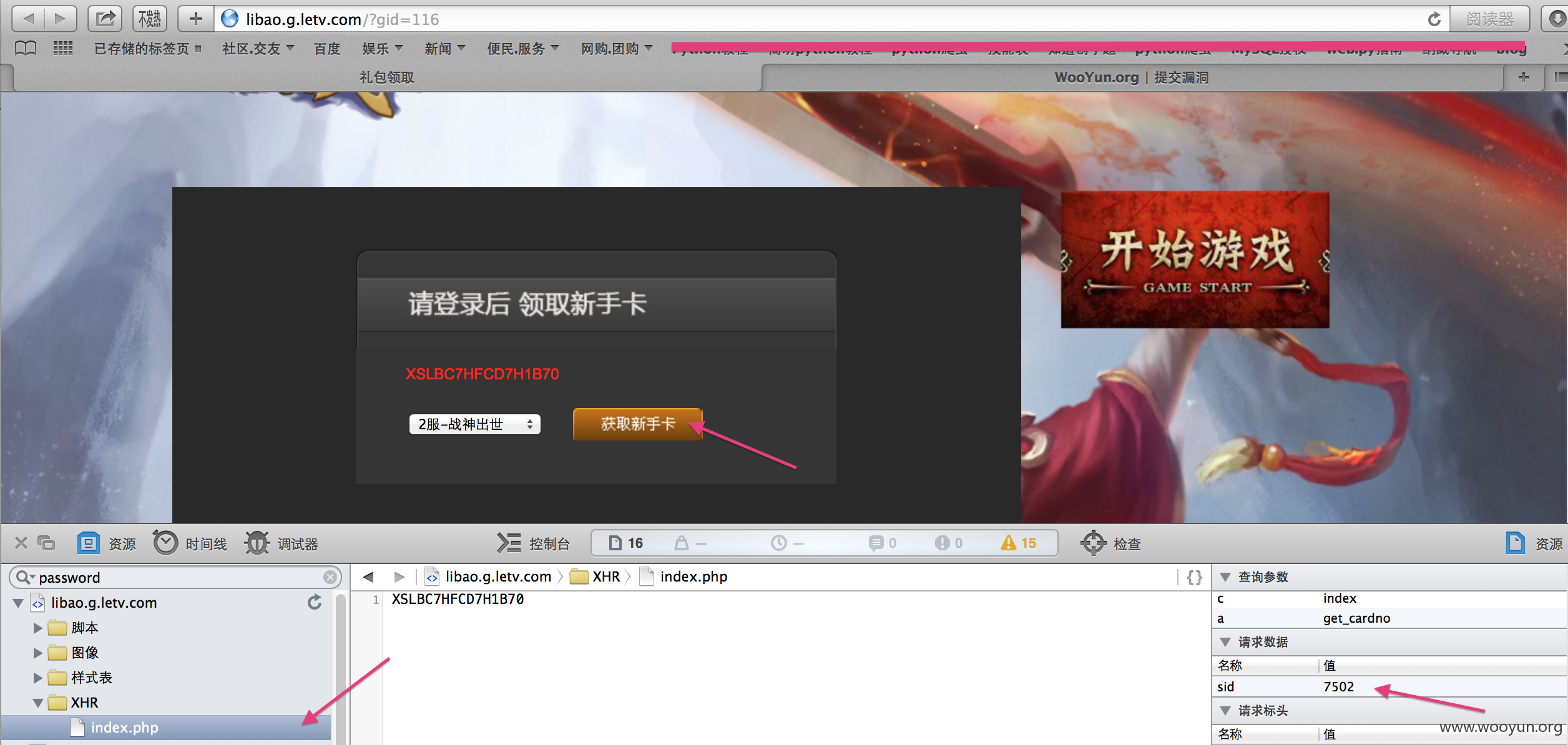
刚开始简单手工测试后直接仍SQLMAP 结果测试到time注入的时候网站挂掉了 应该是新手卡返回过多导致延迟时间成倍的增加 然后就崩掉了 后来修改一下SQLMAP的参数
这样就只测试布尔盲注了 tamper=between 是因为过滤了大于小于符号
game_bbs就是游戏论坛了 注出uckey
有了uckey 就可以getshell了 不过发现论坛貌似在维护中?什么功能都用不了 访问任意php文件都是403错误
下面的是web_admin库 应该是有关游戏的



